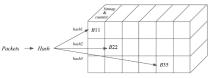
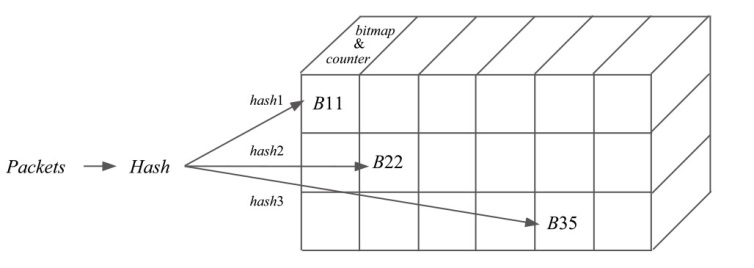
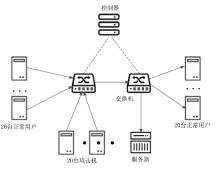
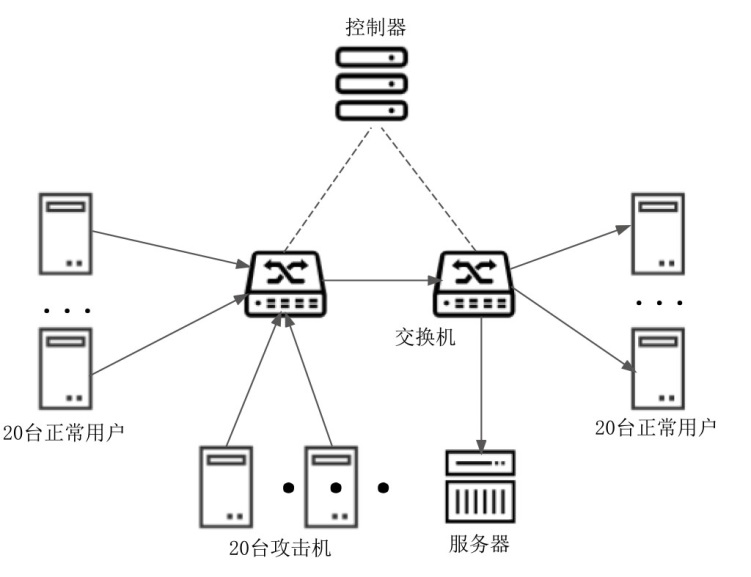
信息网络安全 ›› 2026, Vol. 26 ›› Issue (1): 79-90.doi: 10.3969/j.issn.1671-1122.2026.01.007
抽样情况下复杂LDoS攻击检测方法研究
- 东南大学网络空间安全学院,南京 214000
-
收稿日期:2025-10-30出版日期:2026-01-10发布日期:2026-02-13 -
通讯作者:程光gcheng@njnet.edu.cn -
作者简介:徐一凡(2000—),男,山西,硕士研究生,主要研究方向为网络与信息安全|程光(1973—),男,安徽,教授,博士,CCF杰出会员,主要研究方向为网络空间安全监测和防护、网络大数据分析|周余阳(1994—),男,江苏,助理研究员,博士,CCF会员,主要研究方向为网络安全、移动目标防御 -
基金资助:国家自然科学基金(U22B2025);国家自然科学基金(62202097)
Research on Complex LDoS Attack Detection Methods under Sampling Conditions
XU Yifan, CHENG Guang( ), ZHOU Yuyang
), ZHOU Yuyang
- School of Cyber Science and Engineering, SouthEast University, Nanjing 214000, China
-
Received:2025-10-30Online:2026-01-10Published:2026-02-13
摘要:
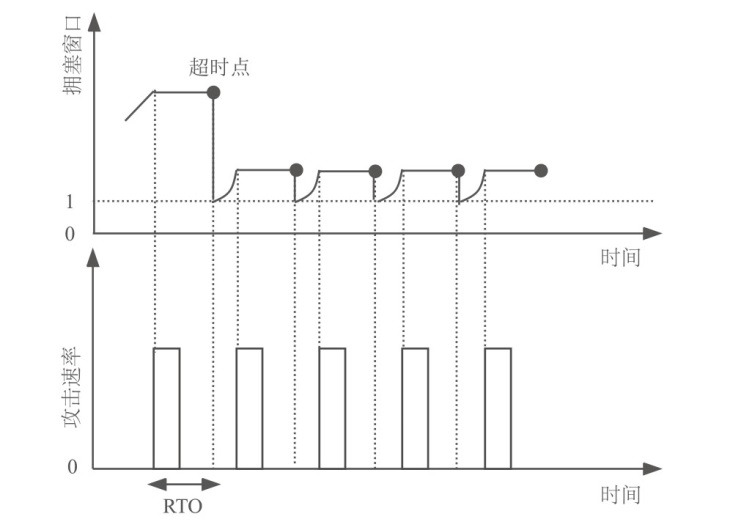
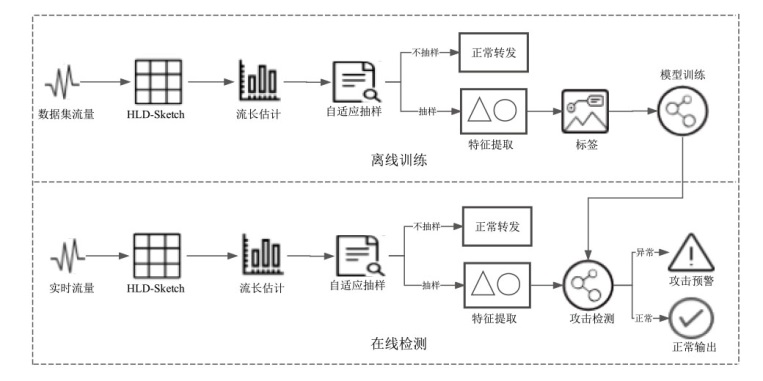
低速率拒绝服务(LDoS)攻击借助网络协议的自适应机制缺陷,以合法方式致使网络自适应机制失效,显著降低带宽利用率和服务质量。因此,LDoS攻击的高隐蔽性和强破坏性使其成为网络安全领域的重要研究课题。针对复杂LDoS攻击在多网络层次中的隐蔽性及传统检测方法在抽样场景下的局限性,文章提出一种基于HLD-Sketch的LDoS攻击检测方法。文章涵盖在抽样情况下传输层LDoS攻击、应用层LDoS攻击及混合层次攻击场景。首先,通过改进的CM-Sketch结构实现动态流长估计,基于流长自适应调整抽样概率,优先对短流实施细粒度采样,减少长流背景噪声对攻击特征提取的干扰;其次,利用CM-Sketch的轻量级特性,在抽样流量中高效提取多维时序统计特征,包括流速率、上下行数据包个数及端口散布值等特征;最后,采用机器学习分类器对传输层、应用层及混合攻击进行层次化检测。实验结果表明,文章方法在3%的抽样率以及在混合攻击场景中,6 s内的检测准确率可以达到99.94%。该方法为高速网络环境下多维度LDoS攻击的实时检测提供了轻量化解决方案,尤其适用于大规模流量环境中的资源受限场景。
中图分类号:
引用本文
徐一凡, 程光, 周余阳. 抽样情况下复杂LDoS攻击检测方法研究[J]. 信息网络安全, 2026, 26(1): 79-90.
XU Yifan, CHENG Guang, ZHOU Yuyang. Research on Complex LDoS Attack Detection Methods under Sampling Conditions[J]. Netinfo Security, 2026, 26(1): 79-90.
表7
滑动时间窗口对检测性能的影响
| 时间/s | Accuracy | Recall | FPR | F1 |
|---|---|---|---|---|
| 1 | 98.01% | 98.51% | 12.62% | 98.97% |
| 2 | 98.27% | 98.64% | 11.83% | 99.11% |
| 3 | 99.52% | 99.87% | 15.61% | 99.75% |
| 4 | 99.68% | 99.88% | 13.28% | 99.83% |
| 5 | 99.46% | 99.76% | 9.55% | 99.73% |
| 6 | 99.73% | 99.88% | 7.97% | 99.86% |
| 7 | 99.79% | 99.92% | 6.74% | 99.90% |
| 8 | 99.88% | 99.96% | 7.48% | 99.94% |
| 9 | 99.92% | 99.98% | 4.63% | 99.95% |
| 10 | 99.91% | 99.98% | 5.79% | 99.95% |
表8
与随机抽样对比实验
| 时间/s | Accuracy | Recall | FPR | F1 |
|---|---|---|---|---|
| 1 | 95.33% | 96.82% | 13.93% | 97.27% |
| 2 | 96.89% | 98.65% | 16.04% | 98.24% |
| 3 | 97.34% | 98.27% | 13.00% | 98.54% |
| 4 | 97.71% | 99.06% | 15.04% | 98.73% |
| 5 | 98.91% | 99.80% | 12.50% | 99.41% |
| 6 | 99.09% | 99.56% | 7.93% | 99.51% |
| 7 | 99.59% | 100.00% | 4.87% | 99.77% |
| 8 | 99.47% | 99.88% | 6.15% | 99.72% |
| 9 | 99.69% | 100.00% | 8.88% | 99.78% |
| 10 | 99.00% | 99.89% | 14.51% | 99.47% |
表9
滑动时间窗口对检测性能的影响
| 时间/s | Accuracy | Recall | FPR | F1 |
|---|---|---|---|---|
| 1 | 97.82% | 90.20% | 4.10% | 79.96% |
| 2 | 99.82% | 95.08% | 1.99% | 95.46% |
| 3 | 99.74% | 90.18% | 4.39% | 92.18% |
| 4 | 99.83% | 90.89% | 3.46% | 93.20% |
| 5 | 99.83% | 85.49% | 5.32% | 89.23% |
| 6 | 99.94% | 90.09% | 2.87% | 93.65% |
| 7 | 99.93% | 89.58% | 3.40% | 93.81% |
| 8 | 99.94% | 94.11% | 1.85% | 95.82% |
| 9 | 99.90% | 90.35% | 3.50% | 94.48% |
| 10 | 99.92% | 90.27% | 4.16% | 94.51% |
表10
Chen等人方法对比实验
| 时间/s | Accuracy | Recall | FPR | F1 |
|---|---|---|---|---|
| 1 | 90.12% | 85.47% | 10.07% | 87.73% |
| 2 | 94.33% | 91.25% | 8.31% | 90.68% |
| 3 | 89.56% | 87.71% | 9.92% | 88.18% |
| 4 | 95.67% | 93.08% | 7.21% | 94.36% |
| 5 | 94.96% | 91.33% | 8.03% | 91.93% |
| 6 | 96.81% | 92.84% | 6.12% | 91.89% |
| 7 | 96.56% | 92.58% | 6.47% | 92.06% |
| 8 | 98.11% | 94.41% | 5.44% | 95.71% |
| 9 | 99.03% | 95.35% | 3.58% | 95.11% |
| 10 | 98.72% | 93.67% | 6.16% | 94.97% |
表11
HU等人方法对比实验
| 时间/s | Accuracy | Recall | FPR | F1 |
|---|---|---|---|---|
| 1 | - | - | - | - |
| 2 | - | - | - | - |
| 3 | 72.15% | 68.33% | 19.87% | 70.18% |
| 4 | 75.62% | 71.84% | 17.45% | 73.68% |
| 5 | 84.72% | 82.15% | 13.32% | 83.41% |
| 6 | 91.42% | 90.98% | 10.28% | 91.96% |
| 7 | 87.93% | 84.52% | 8.40% | 85.21% |
| 8 | 93.13% | 90.61% | 6.35% | 91.28% |
| 9 | 93.71% | 89.94% | 6.50% | 90.55% |
| 10 | 92.37% | 90.91% | 7.21% | 91.84% |
| [1] | NEEDHAM R M. Denial of Service: An Example[J]. Communications of the ACM, 1994, 37(11): 42-46. |
| [2] | KUZMANOVIC A, KNIGHTLY E W. Low-Rate TCP-Targeted Denial of Service Attacks:the Shrew vs. The Mice and Elephants[C]// ACM. The 2003 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications. New York: ACM, 2003: 75-86. |
| [3] |
MACIÁ-FERNÁNDEZ G, DÍAZ-VERDEJO J E, GARCÍA-TEODORO P. Evaluation of a Low-Rate DoS Attack Against Iterative Servers[J]. Computer Networks, 2007, 51(4): 1013-1030.
doi: 10.1016/j.comnet.2006.07.002 URL |
| [4] | OKTA. Slowloris DDoS Attack: Definition, Damage&Deffense[EB/OL]. (2024-09-01)[2025-10-12]. https://www.okta.com/identity-101/slowloris/. |
| [5] | TOULAS B. Italian CERT: Hacktivists Hit Govt Sites in ‘Slow HTTP’ DDoS Attacks[EB/OL]. (2020-05-13)[2025-10-12]. https://www.bleepingcomputer.com/news/security/italian-cert-hacktivists-hit-govt-sites-in-slow-http-ddos-attacks/. |
| [6] | SUN Haibin, LUI J C S, YAU D K Y. Defending Against Low-Rate TCP Attacks: Dynamic Detection and Protection[C]// IEEE. The 12th IEEE International Conference on Network Protocols (ICNP 2004). New York: IEEE, 2004: 196-205. |
| [7] |
TANG Dan, WANG Xiyin, LI Xiong, et al. AKN-FGD: Adaptive Kohonen Network Based Fine-Grained Detection of LDoS Attacks[J]. IEEE Transactions on Dependable and Secure Computing, 2023, 20(1): 273-287.
doi: 10.1109/TDSC.2021.3131531 URL |
| [8] |
XIANG Yang, LI Ke, ZHOU Wanlei. Low-Rate DDoS Attacks Detection and Traceback by Using New Information Metrics[J]. IEEE Transactions on Information Forensics and Security, 2011, 6(2): 426-437.
doi: 10.1109/TIFS.2011.2107320 URL |
| [9] |
YUE Meng, WU Zhijun, WANG Jingjie. Detecting LDoS Attack Bursts Based on Queue Distribution[J]. IET Information Security, 2019, 13(3): 285-292.
doi: 10.1049/iet-ifs.2018.5097 |
| [10] |
TANG Dan, TANG Liu, DAI Rui, et al. MF-Adaboost: LDoS Attack Detection Based on Multi-Features and Improved Adaboost[J]. Future Generation Computer Systems, 2020, 106: 347-359.
doi: 10.1016/j.future.2019.12.034 URL |
| [11] | LUO Xiapu, CHANG R K C. On A New Class of Pulsing Denial-of-Service Attacks and the Defense[C]// NDSS. NDSS Symposium 2005. SanDiego: NDSS, 2005: 67-85. |
| [12] |
CHEN Zhaomin, YEO C K, LEE B S, et al. Power Spectrum Entropy Based Detection and Mitigation of Low-Rate DoS Attacks[J]. Computer Networks, 2018, 136: 80-94.
doi: 10.1016/j.comnet.2018.02.029 URL |
| [13] | ZHANG Naiji, JAAFAR F, MALIK Y. Low-Rate DoS Attack Detection Using PSD Based Entropy and Machine Learning[C]// IEEE. 2019 6th IEEE International Conference on Cyber Security and Cloud Computing (CSCloud)/ 2019 5th IEEE International Conference on Edge Computing and Scalable Cloud (EdgeCom). New York: IEEE, 2019: 59-62. |
| [14] |
WU Zhijun, ZHANG Liyuan, YUE Meng. Low-Rate DoS Attacks Detection Based on Network Multifractal[J]. IEEE Transactions on Dependable and Secure Computing, 2016, 13(5): 559-567.
doi: 10.1109/TDSC.2015.2443807 URL |
| [15] |
CHEN Hongsong, MENG Caixia, SHAN Zhiguang, et al. A Novel Low-Rate Denial of Service Attack Detection Approach in ZigBee Wireless Sensor Network by Combining Hilbert-Huang Transformation and Trust Evaluation[J]. IEEE Access, 2019, 7: 32853-32866.
doi: 10.1109/ACCESS.2019.2903816 |
| [16] |
JAZI H H, GONZALEZ H, STAKHANOVA N, et al. Detecting HTTP-Based Application Layer DoS Attacks on Web Servers in the Presence of Sampling[J]. Computer Networks, 2017, 121: 25-36.
doi: 10.1016/j.comnet.2017.03.018 URL |
| [17] | REED A, DOOLEY L S, MOSTEFAOUI S K. A Reliable Real-Time Slow DoS Detection Framework for Resource-Constrained IoT Networks[C]// IEEE. 2021 IEEE Global Communications Conference (GLOBECOM). New York: IEEE, 2022: 1-6. |
| [18] | XU Congyuan, SHEN Jizhong, DU Xin. Low-Rate DoS Attack Detection Method Based on Hybrid Deep Neural Networks[EB/OL]. [2025-10-30]. https://doi.org/10.1016/j.jisa.2021.102879. |
| [19] |
JANSI RANI S V, IOANNOU I, NAGARADJANE P, et al. Detection of DDoS Attacks in D2D Communications Using Machine Learning Approach[J]. Computer Communications, 2023, 198: 32-51.
doi: 10.1016/j.comcom.2022.11.013 URL |
| [20] | GARCIA N, ALCANIZ T, GONZÁLEZ-VIDAL A, et al. Distributed Real-Time SlowDoS Attacks Detection over Encrypted Traffic Using Artificial Intelligence[EB/OL]. (2021-01-01)[2025-10-30]. https://doi.org/10.1016/j.jnca.2020.102871. |
| [21] | WEN Kun, YANG Jiahai, ZHANG Bin. Survey on Research and Progress of Low-Rate Denial of Service Attacks[J]. Journal of Software, 2014, 25(3): 591-605. |
| 文坤, 杨家海, 张宾. 低速率拒绝服务攻击研究与进展综述[J]. 软件学报, 2014, 25(3): 591-605. | |
| [22] | RFC 2988. Computing TCP’s Retransmission Timer[EB/OL]. [2025-10-12]. https://www.rfc-editor.org/rfc/pdfrfc/rfc2988.txt.pdf. |
| [23] | LI D C, TU H H, CHOU L D. Cross-Layer Detection and Defence Mechanism Against DDoS and DRDoS Attacks in Software-Defined Networks Using P4 Switches[EB/OL]. (2021-01-01)[2025-10-30]. https://doi.org/10.1016/j.compeleceng.2024.10930. |
| [24] | WANG Zhi, ZHANG Hao, GU Jianjun. A Hybrid Method of Joint Entropy and Multiple Clustering Based DDoS Detection in SDN[J]. Netinfo Security, 2023, 23(10): 1-7. |
| 王智, 张浩, 顾建军. SDN网络中基于联合熵与多重聚类的DDoS攻击检测[J]. 信息网络安全, 2023, 23(10): 1-7. | |
| [25] | CHEN Jinfeng, WU Hua, WANG Suyue, et al. An Accurate and Real-Time Detection Method for Concealed Slow HTTP DoS in Backbone Network[C]// Springer. ICT Systems Security and Privacy Protection. Heidelberg: Springer, 2024: 207-221. |
| [26] |
HU Xiaoyan, GAO Wenjie, CHENG Guang, et al. Toward Early and Accurate Network Intrusion Detection Using Graph Embedding[J]. IEEE Transactions on Information Forensics and Security, 2023, 18: 5817-5831.
doi: 10.1109/TIFS.2023.3318960 URL |
| [1] | 郭毅, 李旭青, 张子蛟, 张宏涛, 张连成, 张香丽. 基于区块链的数据安全共享研究[J]. 信息网络安全, 2026, 26(1): 1-23. |
| [2] | 郑开发, 骆振鹏, 刘嘉奕, 刘志全, 王赜, 吴云坤. 支持属性更新的轻量级联邦学习节点动态参与方案[J]. 信息网络安全, 2026, 26(1): 102-114. |
| [3] | 李冬, 高源, 于俊清, 曾木虹, 陈俊鑫. 一种基于P4的多模态网络控制与安全检测方案[J]. 信息网络安全, 2026, 26(1): 115-124. |
| [4] | 董佳瑜, 高宏民, 马兆丰, 赖冠辉. 多重签名机制在区块链中的研究及实现[J]. 信息网络安全, 2026, 26(1): 125-138. |
| [5] | 钮可, 胡方锰, 李军. 基于非局部机制的可逆神经网络视频隐写研究[J]. 信息网络安全, 2026, 26(1): 139-149. |
| [6] | 邓钰洋, 芦天亮, 李知皓, 孟昊阳, 马远声. 融合GAT与可解释DQN的SQL注入攻击检测模型[J]. 信息网络安全, 2026, 26(1): 150-167. |
| [7] | 仝鑫, 焦强, 王靖亚, 袁得嵛, 金波. 公共安全领域大语言模型的可信性研究综述:风险、对策与挑战[J]. 信息网络安全, 2026, 26(1): 24-37. |
| [8] | 王亚杰, 陆锦标, 谭冬黎, 范青, 祝烈煌. 面向胶囊网络的成员推理风险评估[J]. 信息网络安全, 2026, 26(1): 38-48. |
| [9] | 施寅生, 包阳, 庞晶晶. 一种对抗GAN攻击的联邦隐私增强方法研究[J]. 信息网络安全, 2026, 26(1): 49-58. |
| [10] | 吴越, 张雅雯, 程相然. 基于动态安全管理模式的信息系统安全防御策略研究[J]. 信息网络安全, 2026, 26(1): 59-68. |
| [11] | 张慎明, 梁金洁, 许新桥, 冯戈, 邹添华, 胡志林. 基于博弈论的地址跳变系统时间策略研究[J]. 信息网络安全, 2026, 26(1): 69-78. |
| [12] | 王焕臻, 徐洪平, 李旷代, 刘洋, 姚琳元. 一种基于分层强化学习的网络防御自主决策研究[J]. 信息网络安全, 2026, 26(1): 91-101. |
| [13] | 韩益亮, 彭一轩, 吴旭光, 李鱼. 基于图变分自编码器的多模态特征融合加密流量分类模型[J]. 信息网络安全, 2025, 25(12): 1914-1926. |
| [14] | 张雪锋, 王柯航. 一种基于SM9的代理环签名方案[J]. 信息网络安全, 2025, 25(12): 1901-1913. |
| [15] | 解相朋, 邵邢晨. 基于双域多项式框架的随机非线性CPS安全增益调度方法[J]. 信息网络安全, 2025, 25(12): 1889-1900. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||