信息网络安全 ›› 2026, Vol. 26 ›› Issue (1): 102-114.doi: 10.3969/j.issn.1671-1122.2026.01.009
支持属性更新的轻量级联邦学习节点动态参与方案
郑开发1, 骆振鹏2, 刘嘉奕2, 刘志全2, 王赜3, 吴云坤4( )
)
- 1.浙江大学计算机科学与技术学院,杭州 310027
2.暨南大学网络空间安全学院,广州 511443
3.天津工业大学软件学院,天津 300387
4.奇安信科技集团股份有限公司,北京 100084
-
收稿日期:2025-08-20出版日期:2026-01-10发布日期:2026-02-13 -
通讯作者:吴云坤wuyunkun@qianxin.com -
作者简介:郑开发(1989—),男,湖北,高级工程师,博士,CCF会员,主要研究方向为隐私计算、隐私保护和信息安全|骆振鹏(2003—),男,广东,本科,主要研究方向为数据安全、云安全、可搜索加密和隐私保护|刘嘉奕(2005—),男,江苏,本科,主要研究方向为密码学、数据安全和云计算安全|刘志全(1989—),男,山西,教授,博士,CCF会员,主要研究方向为车联网安全、数据安全、隐私计算|王赜(1976—),男,吉林,教授,博士,CCF高级会员,主要研究方向为数据智能分析、数据安全与隐私计算、工业智能软件|吴云坤(1975—),男,江苏,正高级工程师,博士,主要研究方向为关键信息基础设施安全、网络安全 -
基金资助:国家自然科学基金(62272195);国家重点研发计划(2022YFB3104900);北京市高层次创新创业人才支持计划科技新星计划(20250484975)
A Lightweight Dynamic Node Participation Scheme for Federated Learning Nodes Supporting Attribute Update
ZHENG Kaifa1, LUO Zhenpeng2, LIU Jiayi2, LIU Zhiquan2, WANG Ze3, WU Yunkun4( )
)
- 1. College of Computer Science and Technology, Zhejiang University, Hangzhou 310027, China
2. School of Cyber Security, Jinan University, Guangzhou 511443, China
3. School of Software, Tiangong University, Tianjin 300387, China
4. Qi An Xin Technology Group Inc., Beijing 100084, China
-
Received:2025-08-20Online:2026-01-10Published:2026-02-13
摘要:
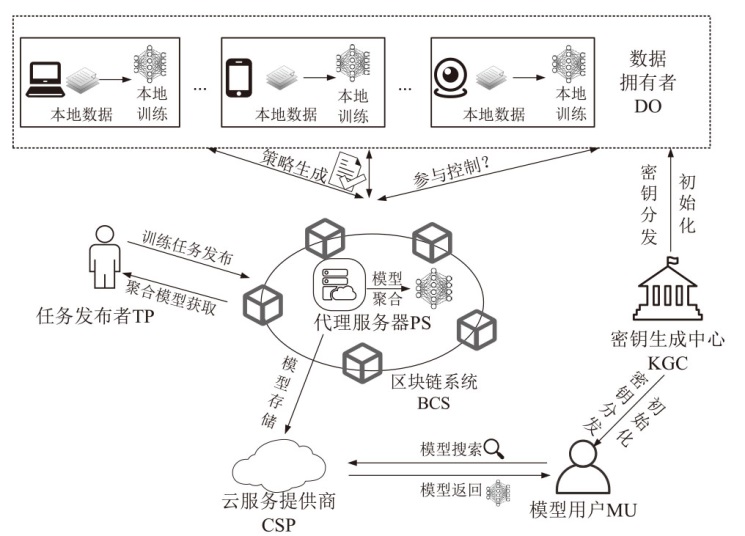
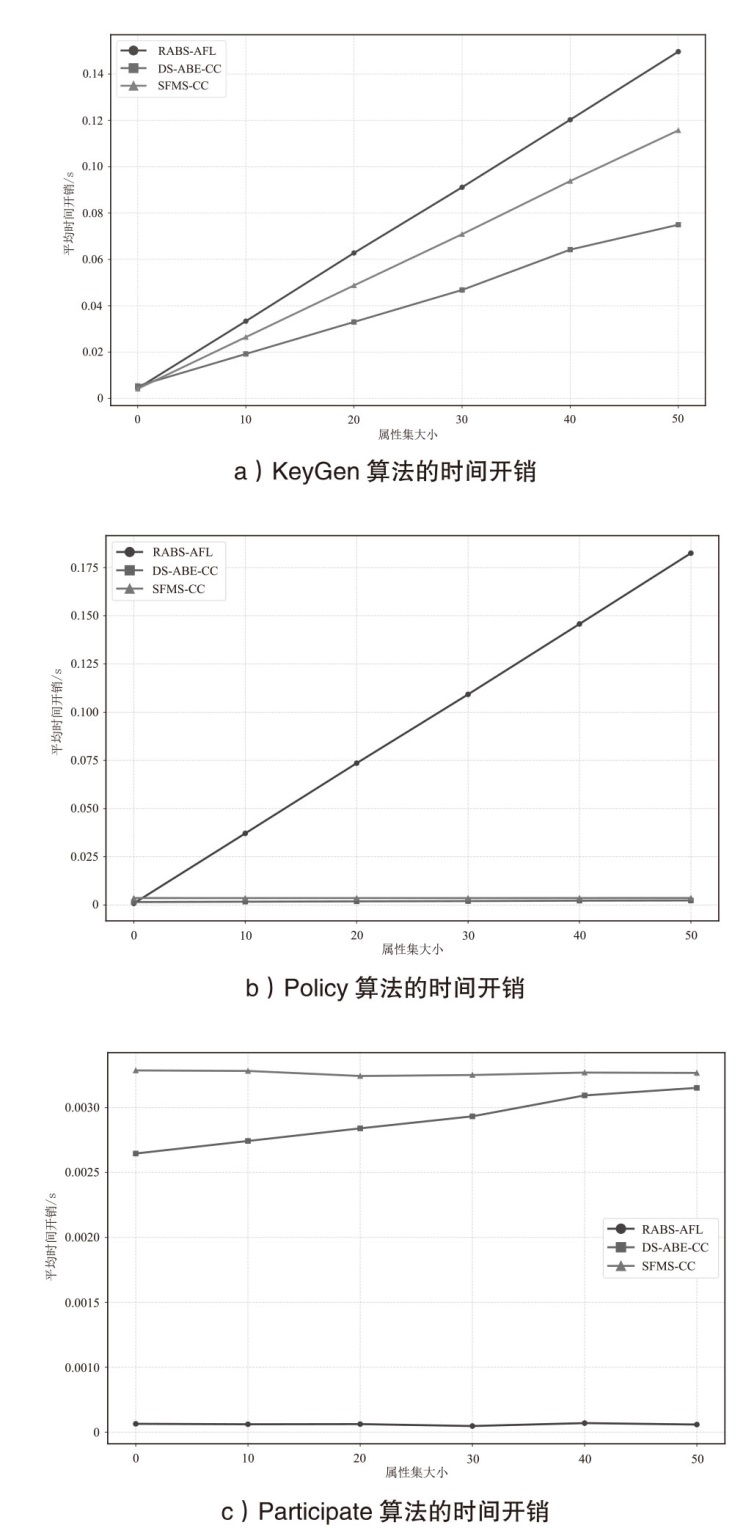
动态的节点参与和退出机制在异步联邦学习环境中可以有效提高学习的灵活性,因此,在涉及数据隐私与安全的场景下,保障参与节点的合法性和安全退出十分关键。文章提出一种支持属性更新的轻量级联邦学习节点动态参与方案。首先,通过引入属性加密和撤销机制,设计一种安全、灵活的参与机制,能够支持节点在参与过程中根据预定的安全策略动态加入或退出,且能够有效应对节点属性的变化,确保数据隐私性。然后,该方案结合区块链技术,使用其智能合约机制记录操作内容,实现了系统操作过程的公开透明,提高了属性撤销的安全性。通过方案分析,验证了算法生成的密文具有良好的不可区分性,性能分析则进一步验证了文章所提方案的优势。
中图分类号:
引用本文
郑开发, 骆振鹏, 刘嘉奕, 刘志全, 王赜, 吴云坤. 支持属性更新的轻量级联邦学习节点动态参与方案[J]. 信息网络安全, 2026, 26(1): 102-114.
ZHENG Kaifa, LUO Zhenpeng, LIU Jiayi, LIU Zhiquan, WANG Ze, WU Yunkun. A Lightweight Dynamic Node Participation Scheme for Federated Learning Nodes Supporting Attribute Update[J]. Netinfo Security, 2026, 26(1): 102-114.
表2
计算开销对比
| 方案 | DO加密开销 | DO解密开销 | PS解密开销 |
|---|---|---|---|
| 本文方案 | |||
| 文献[ | |||
| 文献[ | |||
| 文献[ | |||
| 文献[ | — | ||
| 文献[ | |||
| 文献[ | |||
| 文献[ |
表3
存储开销对比
| 方案 | DO密钥 | DO密文 | CSP密文 |
|---|---|---|---|
| 本文方案 | |||
| 文献[ | — | ||
| 文献[ | |||
| 文献[ | |||
| 文献[ | — | ||
| 文献[ | — | ||
| 文献[ | — | ||
| 文献[ | — |
| [1] | ZHENG Wenbo, YAN Lang, GOU Chao, et al. Federated Meta-Learning for Fraudulent Credit Card Detection[C]// IEEE. The Twenty-Ninth International Joint Conference on Artificial Intelligence. New York: IEEE, 2021: 4654-4660. |
| [2] |
BRISIMI T S, CHEN Ruidi, MELA T, et al. Federated Learning of Predictive Models from Federated Electronic Health Records[J]. International Journal of Medical Informatics, 2018, 112: 59-67.
doi: S1386-5056(18)30008-X pmid: 29500022 |
| [3] |
POKHREL S R, CHOI J. Federated Learning with Blockchain for Autonomous Vehicles: Analysis and Design Challenges[J]. IEEE Transactions on Communications, 2020, 68(8): 4734-4746.
doi: 10.1109/TCOMM.26 URL |
| [4] | NIKNAM S, DHILLON H S, REED J H. Federated Learning for Wireless Communications: Motivation, Opportunities, and Challenges[J]. IEEE Communications Magazine, 2020, 58(6): 46-51. |
| [5] | LIU Yang, HUANG Anbu, LUO Yun, et al. FedVision: An Online Visual Object Detection Platform Powered by Federated Learning[C]// AAAI. The AAAI Conference on Artificial Intelligence. New York: AAAI Press, 2020: 13172-13179. |
| [6] | LI Li, FAN Yuxi, TSE M, et al. A Review of Applications in Federated Learning[EB/OL]. (2020-11-01)[2025-02-20]. https://doi.org/10.1016/j.cie.2020.106854. |
| [7] | MCMAHAN B, MOORE E, RAMAGE D, et al. Communication-Efficient Learning of Deep Networks from Decentralized Data[C]// AISTATS. The 20th International Conference on Artificial Intelligence and Statistics. New York: PMLR, 2017: 1273-1282. |
| [8] | XIE Cong, KOYEJO S, GUPTA I. Asynchronous Federated Optimization[EB/OL]. (2020-01-01)[2025-02-20]. https://arxiv.org/abs/1903.03934. |
| [9] | SAHAI A, WATERS B. Fuzzy Identity-Based Encryption[C]// EUROCRYPT. Advances in Cryptology- EUROCRYPT 2005. Heidelberg: Springer, 2005: 457-473. |
| [10] |
KIM H, PARK J, BENNIS M, et al. Blockchained on-Device Federated Learning[J]. IEEE Communications Letters, 2019, 24(6): 1279-1283.
doi: 10.1109/COML.4234 URL |
| [11] | WANG Rong, TSAI W T. Asynchronous Federated Learning System Based on Permissioned Blockchains[EB/OL]. (2022-02-21)[2025-02-20]. https://doi.org/10.3390/s22041672. |
| [12] | KHAN L U, SAAD W, HAN Zhu, et al. Federated Learning for Internet of Things: Recent Advances, Taxonomy, and Open Challenges[J]. IEEE Communications Surveys & Tutorials, 2021, 23(3): 1759-1799. |
| [13] | GUO Shaoyong, XIANG Baoyu, XIA Xuwei, et al. Blockchain and Federated Learning Based Data Security Sharing Mechanism over Smart City[EB/OL]. (2020-11-12)[2025-02-20]. https://doi.org/10.21203/rs.3.rs-104012/v1. |
| [14] |
LU Yunlong, HUANG Xiaohong, DAI Yueyue, et al. Blockchain and Federated Learning for Privacy-Preserved Data Sharing in Industrial IoT[J]. IEEE Transactions on Industrial Informatics, 2019, 16(6): 4177-4186.
doi: 10.1109/TII.9424 URL |
| [15] | ALBOGAMI N N. Intelligent Deep Federated Learning Model for Enhancing Security in Internet of Things Enabled Edge Computing Environment[EB/OL]. (2025-02-03)[2025-02-20]. https://doi.org/10.1038/s41598-025-88163-5. |
| [16] |
WANG Pengpian, FENG Dengguo, ZHANG Liwu. CP-ABE Scheme Supporting Fully Fine-Grained Attribute Revocation[J]. Journal of Software, 2012, 23(10): 2805-2816.
doi: 10.3724/SP.J.1001.2012.04184 URL |
| 王鹏翩, 冯登国, 张立武. 一种支持完全细粒度属性撤销的CP-ABE方案[J]. 软件学报, 2012, 23(10): 2805-2816. | |
| [17] | WU Xia, XU Lei, ZHU Liehuang. Local Differential Privacy-Based Federated Learning under Personalized Settings[EB/OL]. (2023-03-24)[2025-02-20]. https://doi.org/10.3390/app13074168. |
| [18] | PANG Bo, LIANG Huihui, ZHANG Linghao, et al. An Improved Federated Learning-Assisted Data Aggregation Scheme for Smart Grids[EB/OL]. (2023-08-22)[2025-02-20]. https://doi.org/10.3390/app13179813. |
| [19] | WANG Pengfei, WEI Zongzheng, ZHOU Dongsheng, et al. Survey on Federated Forgetting Learning[J]. Chinese Journal of Computers, 2024, 47(2): 396-422. |
| 王鹏飞, 魏宗正, 周东生, 等. 联邦忘却学习研究综述[J]. 计算机学报, 2024, 47(2): 396-422. | |
| [20] |
BAUCAS M J, SPACHOS P, PLATANIOTIS K N. Federated Learning and Blockchain-Enabled Fog-IoT Platform for Wearables in Predictive Healthcare[J]. IEEE Transactions on Computational Social Systems, 2023, 10(4): 1732-1741.
doi: 10.1109/TCSS.2023.3235950 URL |
| [21] |
SAVAZZI S, NICOLI M, RAMPA V. Federated Learning with Cooperating Devices: A Consensus Approach for Massive IoT Networks[J]. IEEE Internet of Things Journal, 2020, 7(5): 4641-4654.
doi: 10.1109/JIoT.6488907 URL |
| [22] |
LIU Jingwei, LI Yating, SUN Rong, et al. EMK-ABSE: Efficient Multikeyword Attribute-Based Searchable Encryption Scheme through Cloud-Edge Coordination[J]. IEEE Internet of Things Journal, 2022, 9(19): 18650-18662.
doi: 10.1109/JIOT.2022.3163340 URL |
| [23] | ZHENG Kaifa, DING Caiyang, WANG Jinchen. A Secure Data-Sharing Scheme for Privacy-Preserving Supporting Node-Edge-Cloud Collaborative Computation[EB/OL]. (2023-06-15)[2025-02-20]. https://doi.org/10.3390/electronics12122737. |
| [24] |
ZHENG Kaifa, ZHOU Ziyu, LIU Jianwei, et al. Secure Fine-Grained Multi-Keyword Ciphertext Search Supporting Cloud-Edge-End Collaboration in IoT[J]. Chinese Journal of Electronics, 2025, 34(1): 266-281.
doi: 10.23919/cje.2023.00.244 URL |
| [25] | WATERS B. Ciphertext-Policy Attribute-Based Encryption:An Expressive, Efficient, and Provably Secure Realization[C]// Springer. International Workshop on Public Key Cryptography. Heidelberg: Springer, 2011: 53-70. |
| [26] | LI Yanfeng, ZHANG Guipeng, LIN Lubin, et al. Accountable and Verifiable Outsourced Decryption for Ciphertext-Policy Attribute-Based Encryption[J]. Journal of Guangdong University of Technology, 2024, 41(4): 106-113. |
| 李彦锋, 张桂鹏, 林禄滨, 等. 一种支持追责和可验证外包解密的属性基加密方案[J]. 广东工业大学学报, 2024, 41(4): 106-113. | |
| [27] |
QIN Baodong, DENG R H, LIU Shengli, et al. Attribute-Based Encryption with Efficient Verifiable Outsourced Decryption[J]. IEEE Transactions on Information Forensics and Security, 2015, 10(7): 1384-1393.
doi: 10.1109/TIFS.2015.2410137 URL |
| [28] | LI Qi, ZHU Hongbo, YING Zuobin, et al. Traceable Ciphertext-Policy Attribute-Based Encryption with Verifiable Outsourced Decryption in eHealth Cloud[EB/OL]. (2018-06-06)[2025-02-20]. https://doi.org/10.1155/2018/1701675. |
| [1] | 郭瑞, 杨鑫, 王俊茗. 基于区块链的可验证可撤销属性加密方案[J]. 信息网络安全, 2024, 24(6): 863-878. |
| [2] | 吴立钊, 汪晓丁, 徐恬, 阙友雄, 林晖. 面向半异步联邦学习的防御投毒攻击方法研究[J]. 信息网络安全, 2024, 24(10): 1578-1585. |
| [3] | 周权, 陈民辉, 卫凯俊, 郑玉龙. 基于SM9的属性加密的区块链访问控制方案[J]. 信息网络安全, 2023, 23(9): 37-46. |
| [4] | 张雪锋, 胡奕秀. 一种基于SM9的可撤销标识广播加密方案[J]. 信息网络安全, 2023, 23(1): 28-35. |
| [5] | 崔皓宇, 马利民, 王佳慧, 张伟. 基于区块链的属性加密多授权机构安全模型研究[J]. 信息网络安全, 2022, 22(5): 84-93. |
| [6] | 张淑清, 蔡志文. 云数据下基于可问责属性即可撤销的加密方案[J]. 信息网络安全, 2021, 21(12): 70-77. |
| [7] | 汪金苗, 王国威, 王梅, 朱瑞瑾. 面向雾计算的隐私保护与访问控制方法[J]. 信息网络安全, 2019, 19(9): 41-45. |
| [8] | 王生玉, 汪金苗, 董清风, 朱瑞瑾. 基于属性加密技术研究综述[J]. 信息网络安全, 2019, 19(9): 76-80. |
| [9] | 刘建华, 郑晓坤, 郑东, 敖章衡. 基于属性加密且支持密文检索的安全云存储系统[J]. 信息网络安全, 2019, 19(7): 50-58. |
| [10] | 王乐, 杨哲荣, 刘容京, 王祥. 基于属性加密算法的可穿戴设备系统隐私保护方法研究[J]. 信息网络安全, 2018, 18(6): 77-84. |
| [11] | 陈飞, 司一帆, 韩益亮. 适用于PHR系统的混合属性加密签名方案[J]. 信息网络安全, 2016, 16(12): 46-50. |
| [12] | 赵洋, 陈阳, 熊虎, 任化强. 云环境下一种可撤销授权的数据拥有性证明方案[J]. 信息网络安全, 2015, 15(8): 1-7. |
| [13] | 唐宇, 刘嘉勇, 汤殿华. 一种可撤销的指纹模板保护方案[J]. 信息网络安全, 2015, 15(1): 72-75. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||