信息网络安全 ›› 2022, Vol. 22 ›› Issue (5): 84-93.doi: 10.3969/j.issn.1671-1122.2022.05.010
基于区块链的属性加密多授权机构安全模型研究
- 1.北京信息科技大学网络文化与数字传播北京市重点实验室,北京 100101
2.北京信息科技大学计算机学院,北京 100101
3.国家信息中心信息与网络安全部,北京 100045
-
收稿日期:2022-03-09出版日期:2022-05-10发布日期:2022-06-02 -
通讯作者:张伟 E-mail:zhwei@bistu.edu.cn -
作者简介:崔皓宇(1996—),男,河北,硕士研究生,主要研究方向为密码应用、区块链|马利民(1983—),男,山东,副教授,博士,主要研究方向为网络安全协议、信息隐藏技术、大数据安全|王佳慧(1983—),女,山西,研究员,博士,主要研究方向为云计算安全、大数据安全、云取证安全|张伟(1980—),男,山东,教授,博士,主要研究方向为大数据存储与安全、软硬件协同设计 -
基金资助:国家重点研发计划(2020YFC1522702)
Research on the Security Model of Multi-Authority for Attribute Encryption Based on Blockchain
CUI Haoyu1,2, MA Limin1,2, WANG Jiahui3, ZHANG Wei2( )
)
- 1. Beijing Key Laboratory of Internet Culture and Digital Dissemination Research, Beijing Information Science & Technology University, Beijing 100101, China
2. School of Computer, Beijing Information Science & Technology University, Beijing 100101, China
3. Department of Information and Security,The State Information Center, Beijing 100045, China
-
Received:2022-03-09Online:2022-05-10Published:2022-06-02 -
Contact:ZHANG Wei E-mail:zhwei@bistu.edu.cn
摘要:
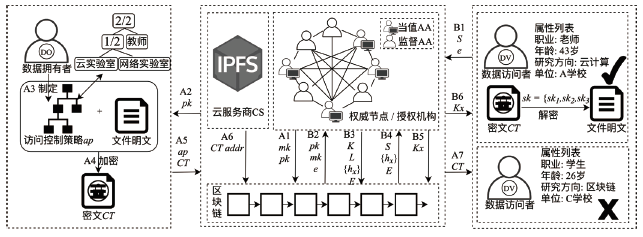
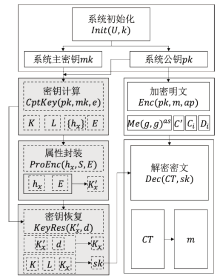
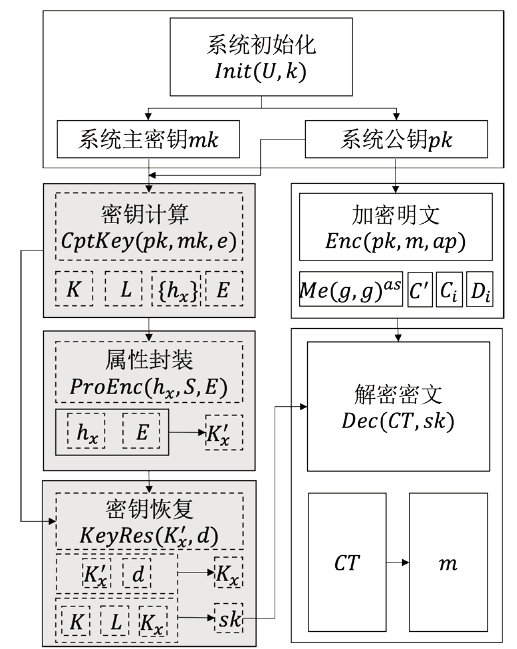
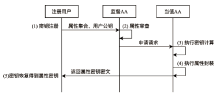
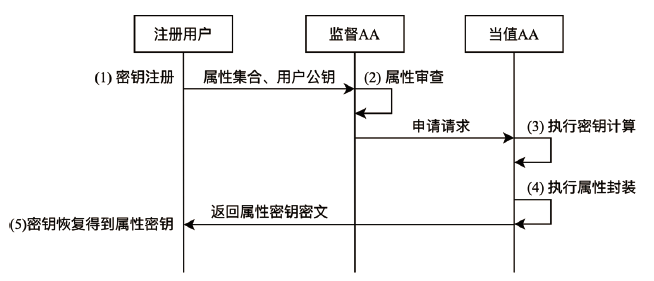
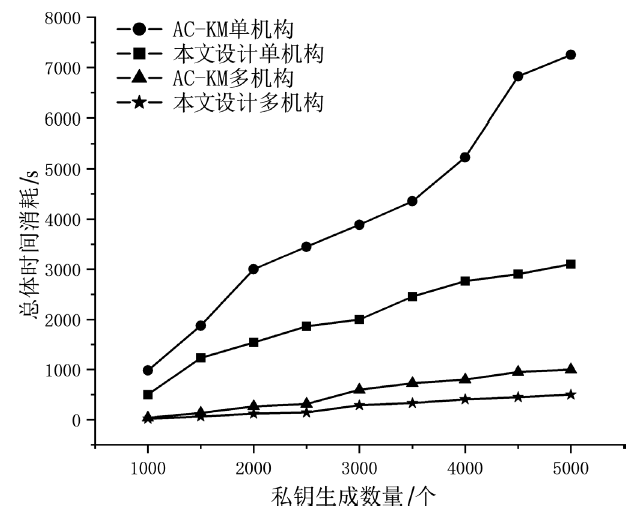
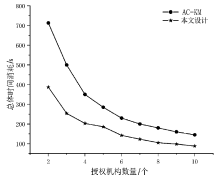
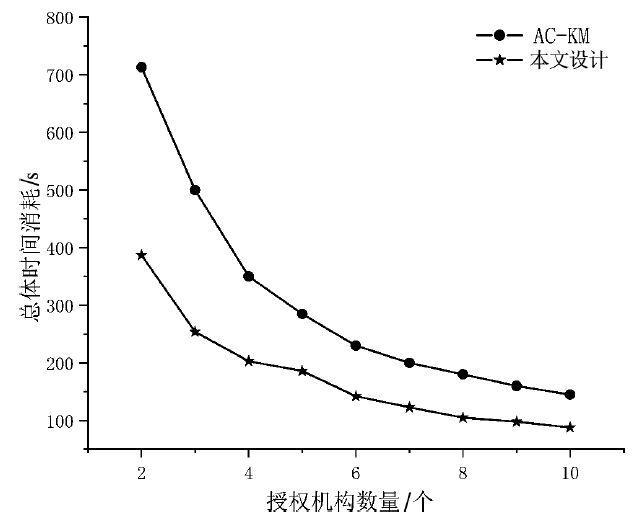
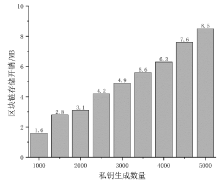
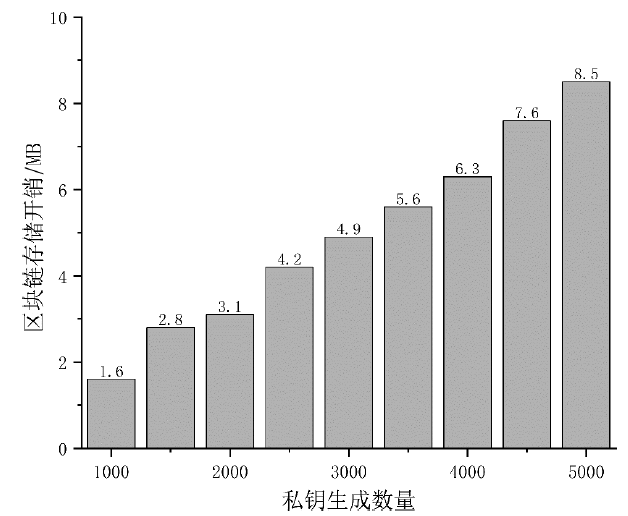
云环境中属性加密算法可以有效实现数据云存储的细粒度访问控制,基于单授权机构的属性加密算法可能存在单点故障、密钥分发困难等问题,基于多授权机构的属性加密算法则存在通信开销大、授权机构不可信等问题。针对上述问题,文章提出一种基于区块链的属性加密多授权机构安全访问控制模型。首先,多个授权机构联合参与属性密钥生成和安全传输,避免了密钥关键信息的泄露;其次,通过共识机制和滑动窗口机制动态调节授权机构数量,防止单点故障,实现负载均衡。理论分析和实验数据表明,文章所提的方案能够有效保障数据安全,提高授权机构可信性、可靠性以及可审计性。
中图分类号:
引用本文
崔皓宇, 马利民, 王佳慧, 张伟. 基于区块链的属性加密多授权机构安全模型研究[J]. 信息网络安全, 2022, 22(5): 84-93.
CUI Haoyu, MA Limin, WANG Jiahui, ZHANG Wei. Research on the Security Model of Multi-Authority for Attribute Encryption Based on Blockchain[J]. Netinfo Security, 2022, 22(5): 84-93.
| [1] |
LIU Chilun. Cloud Service Access Control System Based on Ontologies[J]. Advances in Engineering Software, 2014, 69: 26-36.
doi: 10.1016/j.advengsoft.2013.12.006 URL |
| [2] | CHEN Danwei, HUANG Xiuli, REN Xunyi. Access Control of Cloud Service Based on UCON[C]// Springer. Proceedings of the 1st International Conference on Cloud Computing. Heidelberg: Springer, 2009: 559-564. |
| [3] | BELLARE M, DESAI A, JOKIPII E, et al. A Concrete Security Treatment of Symmetric Encryption[C]// IEEE. Proceedings of the 38th Annual Symposium on Foundations of Computer Science. Washington, DC: IEEE, 1997: 394-403. |
| [4] | CURTMOLA R, GARAY J, KAMARA S, et al. Searchable Symmetric Encryption: Improved Definitions and Efficient Constructions[C]// ACM. Proceedings of the 13th ACM Conference on Computer and Communications Security. New York: ACM, 2006: 79-88. |
| [5] |
CRAMER R, SHOUP V. Design and Analysis of Practical Public-Key Encryption Schemes Secure Against Adaptive Chosen Ciphertext Attack[J]. Siam Journal on Computing, 2004, 33(1): 167-226.
doi: 10.1137/S0097539702403773 URL |
| [6] |
BALDI M, BIANCHI M, CHIARALUCE F, et al. Enhanced Public Key Security for the McEliece Cryptosystem[J]. Journal of Cryptology, 2016, 29(1): 1-27.
doi: 10.1007/s00145-014-9187-8 URL |
| [7] | SAHAI A, WATERS B. Fuzzy Identity-Based Encryption[C]// Springer. Proceedings of the 24th Annual International Conference on Theory and Applications of Cryptographic Techniques. Heidelberg: Springer, 2005: 457-473. |
| [8] | DAN B, FRANKLIN M. Identity-Based Encryption from the Weil Pairing[C]// Springer. Proceedings of the 21st Annual International Cryptology Conference on Advances in Cryptology. Heidelberg: Springer, 2001: 213-229. |
| [9] | SUN Li. Research and Application of Information Protection Mechanism for Online Education Resource Alliance[J]. Netinfo Security, 2021, 21(9): 32-39. |
| 孙力. 区块链+在线教育资源联盟信息保护机制研究与应用[J]. 信息网络安全, 2021, 21(9):32-39. | |
| [10] | CAO Lei. Cloud Outsourcing Attribute Base Encryption for Hidden Structure in Mobile Medical Service[D]. Xi'an: Xidian University, 2015. |
| [11] | CHASE M. Multi-Authority Attribute Based Encryption[C]// Springer. Proceedings of the 4th Theory of Cryptography Conference Amsterdam. Heidelberg: Springer, 2007: 515-534. |
| [12] | CHASE M, CHOW S. Improving Privacy and Security in Multi-Authority Attribute-Based Encryption[C]// ACM. Proceedings of the 16th ACM conference onComputer and communications security. New York: ACM, 2009: 121-130. |
| [13] | LEWKO A, WATERS B. Decentralizing Attribute-Based Encryption[C]// Springer. Proceedings of the 30th Annual International Conference on the Theory and Applications of Cryptographic Techniques. Heidelberg: Springer, 2011: 568-588. |
| [14] | YUAN Chao, XU Mixue, SI Xueming, et al. Blockchain with Accountable CP-ABE: How to Effectively Protect the Electronic Documents[C]// IEEE. Proceedings of the 2017 IEEE 23rd International Conference on Parallel and Distributed Systems. Washington: IEEE, 2017: 800-803. |
| [15] | ZHENG Lianghan, HE Heng, TONG Qian, et al. Multi-Authority Access Control Scheme in Cloud Environment[J]. Journal of Frontiers of Computer Science and Technology, 2020, 14(11): 1865-1878. |
| 郑良汉, 何亨, 童潜, 等. 云环境中的多授权机构访问控制方案[J]. 计算机科学与探索, 2020, 14(11):1865-1878. | |
| [16] | BEIMEL A. Secure Schemes for Secret Sharing and Key Distribution[D]. Haifa: Israel Institute of Technology, 1996. |
| [17] | WANG Jinmiao, XIE Yongheng, WANG Guowei, et al. A Method of Privacy Preserving and Access Control in Blockchain Based on Attribute-Based Encryption[J]. Netinfo Security, 2020, 20(9): 47-51. |
| 汪金苗, 谢永恒, 王国威, 等. 基于属性基加密的区块链隐私保护与访问控制方法[J]. 信息网络安全, 2020, 20(9):47-51. | |
| [18] | YU Shucheng, WANG Cong, REN Kui, et al. Achieving Secure, Scalable, and Fine-Grained Data Access Control in Cloud Computing[C]// IEEE. Proceedings of the Infocom 2010. New York: IEEE, 2010: 1-9. |
| [19] | YU Jingang, ZHANG Hong, LI Shu, et al. Data Sharing Model for Internet of Things Based on Blockchain[J]. Journal of Chinese Mini-Micro Computer Systems, 2019, 40 (11): 2324-2329. |
| [20] | LI Jiguo, SHI Yuerong, ZHANG Yichen. Searchable Ciphertext-Policy Attribute-Based Encryption with Revocation in Cloud Storage[J]. International Journal of Communication Systems, 2017, 30(1): 2942-2955. |
| [21] | TIAN Youliang, YANG Kedi, WANG Zuan, et al. Algorithm of Blockchain Data Provenance Based on ABE[J]. Journal on Communications, 2019, 40 (11): 101-111. |
| 田有亮, 杨科迪, 王缵, 等. 基于属性加密的区块链数据溯源算法[J]. 通信学报, 2019, 40(11):101-111. | |
| [22] | YAN Xixi, YUAN Xiaohan, TANG Yongli, et al. Verifiable Attribute-Based Searchable Encryption Scheme Based on Blockchain[J]. Journal on Communications, 2020, 41(2): 187-198. |
| 闫玺玺, 原笑含, 汤永利, 等. 基于区块链且支持验证的属性基搜索加密方案[J]. 通信学报, 2020, 41(2):187-198. | |
| [23] | WATERS B. Ciphertext-Policy Attribute-Based Encryption: An Expressive, Efficient, and Provably Secure Realization[C]// Springer. Proceedings of the 14th International Conference on Practice and Theory in Public Key Cryptography Conference on Public Key Cryptography. Heidelberg: Springer, 2011: 53-70. |
| [24] | JUNG T, LI Xiangyang, WAN Zhiguo, et al. Privacy Preserving Cloud Data Access with Multi-Authorities[C]// IEEE. Proceedings of the Infocom 2013. New York: IEEE, 2013: 2625-2633. |
| [1] | 冯景瑜, 张琪, 黄文华, 韩刚. 基于跨链交互的网络安全威胁情报共享方案[J]. 信息网络安全, 2022, 22(5): 21-29. |
| [2] | 刘嘉微, 马兆丰, 王姝爽, 罗守山. 基于区块链的隐私信用数据受限共享技术研究[J]. 信息网络安全, 2022, 22(5): 54-63. |
| [3] | 石润华, 王树豪, 李坤昌. V2G中一种轻量级的跨域双向认证方案[J]. 信息网络安全, 2022, 23(3): 20-28. |
| [4] | 陈彬杰, 魏福山, 顾纯祥. 基于KNN的具有隐私保护功能的区块链异常交易检测[J]. 信息网络安全, 2022, 23(3): 78-84. |
| [5] | 王健, 张蕴嘉, 刘吉强, 陈志浩. 基于区块链的司法数据管理及电子证据存储机制[J]. 信息网络安全, 2022, 22(2): 21-31. |
| [6] | 刘峰, 杨成意, 於欣澄, 齐佳音. 面向去中心化双重差分隐私的谱图卷积神经网络[J]. 信息网络安全, 2022, 22(2): 39-46. |
| [7] | 侯雨桐, 马兆丰, 罗守山. 基于区块链的数据安全共享与受控分发技术研究与实现[J]. 信息网络安全, 2022, 22(2): 55-63. |
| [8] | 刘忻, 王家寅, 杨浩睿, 张瑞生. 一种基于区块链和secGear框架的车联网认证协议[J]. 信息网络安全, 2022, 22(1): 27-36. |
| [9] | 冯景瑜, 汪涛, 于婷婷, 张文波. 基于多云多链协同的医疗数据安全共享机制[J]. 信息网络安全, 2022, 22(1): 9-18. |
| [10] | 孙力. 区块链+在线教育资源联盟信息保护机制研究与应用[J]. 信息网络安全, 2021, 21(9): 32-39. |
| [11] | 陈凯杰, 熊焰, 黄文超, 武建双. 一种基于拜占庭容错的PoS共识协议形式化分析方法[J]. 信息网络安全, 2021, 21(8): 35-42. |
| [12] | 任涛, 金若辰, 罗咏梅. 融合区块链与联邦学习的网络入侵检测算法[J]. 信息网络安全, 2021, 21(7): 27-34. |
| [13] | 吴奕, 仲盛. 区块链共识算法Raft研究[J]. 信息网络安全, 2021, 21(6): 36-44. |
| [14] | 李鹏, 郑田甜, 徐鹤, 朱枫. 基于区块链技术的RFID安全认证协议[J]. 信息网络安全, 2021, 21(5): 1-11. |
| [15] | 周由胜, 钟天琦. 基于区块链的公平交换方案[J]. 信息网络安全, 2021, 21(5): 19-30. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||