信息网络安全 ›› 2022, Vol. 22 ›› Issue (5): 21-29.doi: 10.3969/j.issn.1671-1122.2022.05.003
基于跨链交互的网络安全威胁情报共享方案
- 西安邮电大学无线网络安全技术国家工程实验室,西安 710121
-
收稿日期:2021-11-04出版日期:2022-05-10发布日期:2022-06-02 -
通讯作者:冯景瑜 E-mail:fengjy@xupt.edu.cn -
作者简介:冯景瑜(1984—),男,甘肃,副教授,博士,主要研究方向为物联网安全、区块链、网络攻防|张琪(1997—),男,甘肃,硕士研究生,主要研究方向为物联网安全、区块链|黄文华(1980—),女,江苏,副教授,博士,主要研究方向为隐私保护、网络安全风险评估|韩刚(1990—),男,陕西,讲师,博士,主要研究方向为公钥密码学、属性基加密 -
基金资助:国家自然科学基金(62102312);陕西省高校科协青年人才托举计划(20210119)
A Cyber Threat Intelligence Sharing Scheme Based on Cross-Chain Interaction
FENG Jingyu( ), ZHANG Qi, HUANG Wenhua, HAN Gang
), ZHANG Qi, HUANG Wenhua, HAN Gang
- National Engineering Laboratory for Wireless Security, Xi'an University of Posts and Telecommunications, Xi'an 710121, China
-
Received:2021-11-04Online:2022-05-10Published:2022-06-02 -
Contact:FENG Jingyu E-mail:fengjy@xupt.edu.cn
摘要:
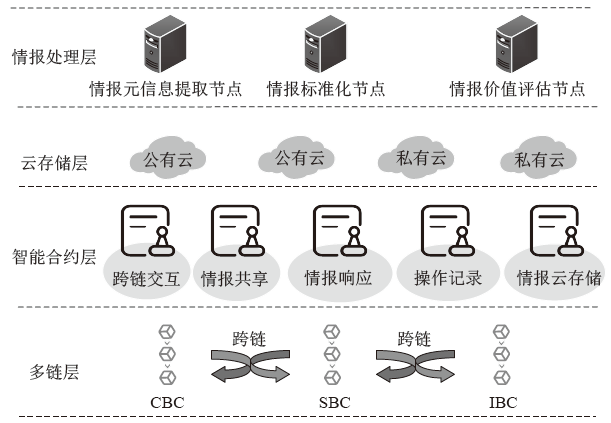
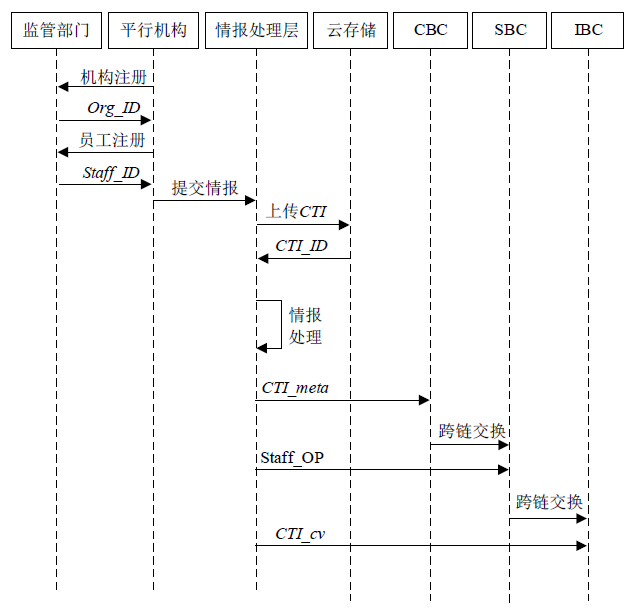
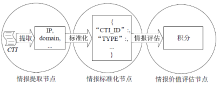
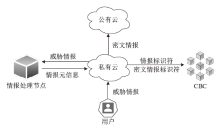
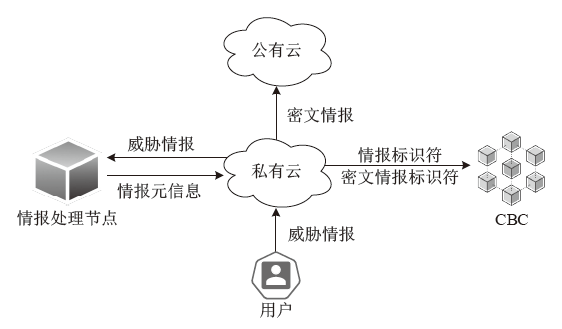
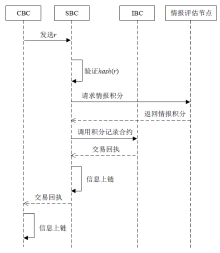
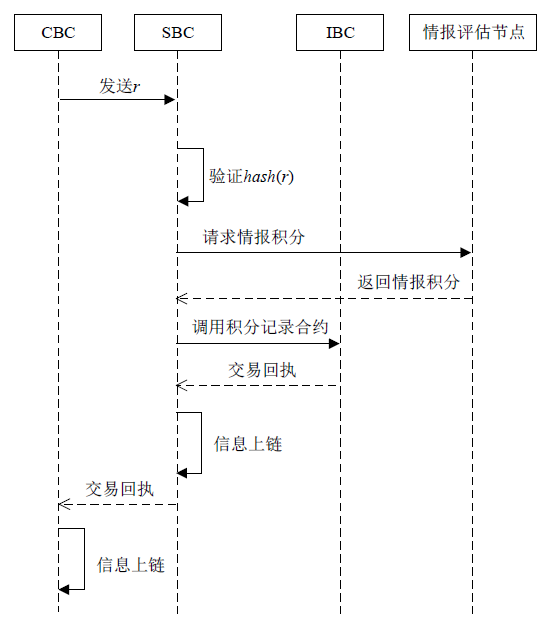
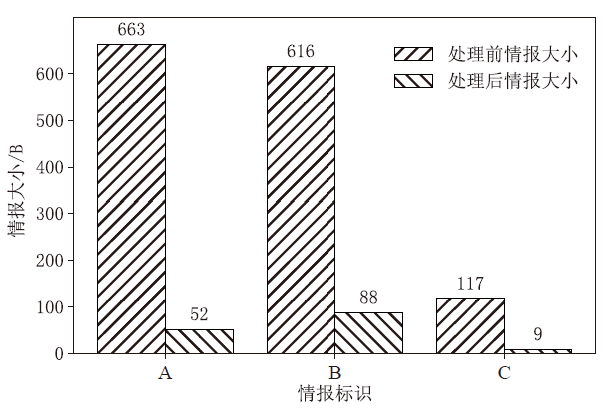
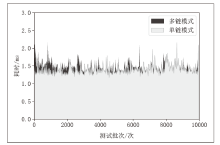
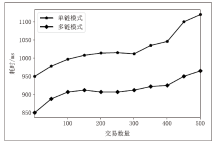
随着数字化转型逐步深入各行业,网络边界正逐渐淡化,网络安全威胁情报共享成为保护信息化基础设施安全的必要手段之一。针对单链威胁情报共享存在的查询和交易性能瓶颈问题,文章在多链模式基础上提出跨区块链交互的威胁情报共享方案。通过设计情报链、监管链和积分链的多链模型,防止内部成员恶意利用情报,有效提升参与方共享意愿及情报共享效率。为保障跨链交互的一致性,采用哈希锁定的跨链机制构建智能合约,确保多链间信息互换安全。考虑到威胁信息具有海量、多元、异构的特性,文章设计了一种情报处理机制,对威胁信息进行统一描述转换。最后在国产开源跨链平台WeCross上进行实验,证明了该方案的有效性。
中图分类号:
引用本文
冯景瑜, 张琪, 黄文华, 韩刚. 基于跨链交互的网络安全威胁情报共享方案[J]. 信息网络安全, 2022, 22(5): 21-29.
FENG Jingyu, ZHANG Qi, HUANG Wenhua, HAN Gang. A Cyber Threat Intelligence Sharing Scheme Based on Cross-Chain Interaction[J]. Netinfo Security, 2022, 22(5): 21-29.
| [1] | CHENG Li, XU Dongfang, ZENG Kai, et al. Design and Application of Power Quality Terminal Information Security[J]. Electric Power Engineering Technology, 2020, 39(6): 26-33. |
| 程立, 许东方, 曾凯, 等. 电能质量终端信息安全设计及应用[J]. 电力工程技术, 2020, 39(6):26-33. | |
| [2] | LIN Yue, LIU Peng, WANG He, et al. Overview of Threat Intelligence Sharing and Exchange in Cybersecurity[J]. Journal of Computer Research and Development, 2020, 57(10): 2052-2065. |
| 林玥, 刘鹏, 王鹤, 等. 网络安全威胁情报共享与交换研究综述[J]. 计算机研究与发展, 2020, 57(10):2052-2065. | |
| [3] | ZIBAK A, SIMPSON A. Cyber Threat Information Sharing: Perceived Benefits and Barriers[C]// ACM. 14th International Conference on Availability, Reliability and Security. New York: ACM, 2019: 1-9. |
| [4] | WANG Hai, ZENG Fei, YANG Xiong. Blockchain-Based Data Security Protection for Distribution Internet of Things[J]. Electric Power Engineering Technology, 2021, 40(5): 47-53. |
| 王海, 曾飞, 杨雄. 基于区块链的配电物联网数据安全防护方法[J]. 电力工程技术, 2021, 40(5):47-53. | |
| [5] | KAMPANAKIS P. Security Automation and Threat Information-Sharing Options[J]. IEEE Security & Privacy, 2014, 12(5): 42-51. |
| [6] |
LESZCZYNA R, WROBEL M R. Threat Intelligence Platform for the Energy Sector[J]. Software: Practice and Experience, 2019, 49(8): 1225-1254.
doi: 10.1002/spe.2705 URL |
| [7] |
ZHENG Zibin, XIE Shaoan, DAI Hongning, et al. Blockchain Challenges and Opportunities: A Survey[J]. International Journal of Web and Grid Services, 2018, 14(4): 352-375.
doi: 10.1504/IJWGS.2018.095647 URL |
| [8] | GAI Keke, GUO Jinnan, ZHU Liehuang, et al. Blockchain Meets Cloud Computing: A Survey[J]. IEEE Communications Surveys & Tutorials, 2020, 22(3): 2009-2030. |
| [9] | ZHENG Peilin, ZHENG Zibin, CHEN Weili, et al. EtherShare: Share Information in Jointcloud Environment Using Blockchain-Based Smart Contracts[C]// IEEE. 2019 IEEE International Conference on Service-Oriented System Engineering(SOSE). New Jersey: IEEE, 2019: 233-238. |
| [10] |
DU Mingxiao, CHEN Qijun, CHEN Jieying, et al. An Optimized Consortium Blockchain for Medical Information Sharing[J]. IEEE Transactions on Engineering Management, 2020, 68(6): 1677-1689.
doi: 10.1109/TEM.2020.2966832 URL |
| [11] | PENG Ruyue, MA Zhaofeng, LUO Shoushan. Research and Implementation of Digital Content Service and Security Supervision Technology Based on Blockchain[J]. Netinfo Security, 2020, 20(10): 49-56. |
| 彭如月, 马兆丰, 罗守山. 基于区块链的数字内容服务与安全监管技术研究与实现[J]. 信息网络安全, 2020, 20(10):49-56. | |
| [12] |
GONG S, LEE C. BLOCIS: Blockchain-Based Cyber Threat Intelligence Sharing Framework for Sybil-Resistance[J]. Electronics, 2020, 9(3): 521-541.
doi: 10.3390/electronics9030521 URL |
| [13] | HOMAN D, SHIEL I, THORPE C. A New Network Model for Cyber Threat Intelligence Sharing Using Blockchain Technology[C]// IEEE. 10th IFIP International Conference on New Technologies, Mobility and Security(NTMS). New Jersey: IEEE, 2019: 1-6. |
| [14] | HUANG Kezhen, LIAN Yifeng, FENG Dengguo, et al. Cyber Security Threat Intelligence Sharing Model Based on Blockchain[J]. Journal of Computer Research and Development, 2020, 57(4): 836-846. |
| 黄克振, 连一峰, 冯登国, 等. 基于区块链的网络安全威胁情报共享模型[J]. 计算机研究与发展, 2020, 57(4):836-846. | |
| [15] | GB/T 36643-2018 Information Security Technology-Cyber Security Threat Information Format[S]. Beijing: Standards Press, 2018. |
| GB/T 36643-2018 信息安全技术网络安全威胁信息格式规范[S]. 北京: 标准出版社, 2018. | |
| [16] | Oasis. Introduction to Structured Threat Information Expression (STIX)[EB/OL]. [2021-10-05]. https://oasis-open.github.io/cti-documentation/stix/intro. |
| [17] | LU Aitong, ZHAO Kuo, YANG Jingying, et al. Research on Cross-Chain Technology of Blockchain[J]. Netinfo Security, 2019, 19(8): 83-90. |
| 路爱同, 赵阔, 杨晶莹, 等. 区块链跨链技术研究[J]. 信息网络安全, 2019, 19(8):83-90. | |
| [18] | LI Dawei, HUO Ying. Cross Domain Authentication of Power IoT Based on Side Chain[J]. Electric Power Engineering Technology, 2020, 39(6): 8-12. |
| 李大伟, 霍瑛. 基于侧链技术的电力物联网跨域认证[J]. 电力工程技术, 2020, 39(6):8-12. | |
| [19] | WeBank. WeCross Open Source Blockchain Platform[EB/OL]. [2021-10-11]. https://wecross.readthedocs.io/zh_CN/latest/. |
| WeBank. WeCross开源区块链跨链协作平台[EB/OL]. [2021-10-11]. https://wecross.readthedocs.io/zh_CN/latest/. | |
| [20] | Oasis. Oasis CTI TC Open Source Cyber Threat Reports[EB/OL]. [2021-10-05]. https://oasis-open.github.io/cti-documentation/stix/examples. |
| [1] | 华景煜, 黄达明. 以太坊智能合约定理证明中的形式化规约研究综述[J]. 信息网络安全, 2022, 22(5): 11-20. |
| [2] | 刘嘉微, 马兆丰, 王姝爽, 罗守山. 基于区块链的隐私信用数据受限共享技术研究[J]. 信息网络安全, 2022, 22(5): 54-63. |
| [3] | 崔皓宇, 马利民, 王佳慧, 张伟. 基于区块链的属性加密多授权机构安全模型研究[J]. 信息网络安全, 2022, 22(5): 84-93. |
| [4] | 石润华, 王树豪, 李坤昌. V2G中一种轻量级的跨域双向认证方案[J]. 信息网络安全, 2022, 23(3): 20-28. |
| [5] | 陈彬杰, 魏福山, 顾纯祥. 基于KNN的具有隐私保护功能的区块链异常交易检测[J]. 信息网络安全, 2022, 23(3): 78-84. |
| [6] | 王健, 张蕴嘉, 刘吉强, 陈志浩. 基于区块链的司法数据管理及电子证据存储机制[J]. 信息网络安全, 2022, 22(2): 21-31. |
| [7] | 刘峰, 杨成意, 於欣澄, 齐佳音. 面向去中心化双重差分隐私的谱图卷积神经网络[J]. 信息网络安全, 2022, 22(2): 39-46. |
| [8] | 侯雨桐, 马兆丰, 罗守山. 基于区块链的数据安全共享与受控分发技术研究与实现[J]. 信息网络安全, 2022, 22(2): 55-63. |
| [9] | 刘忻, 王家寅, 杨浩睿, 张瑞生. 一种基于区块链和secGear框架的车联网认证协议[J]. 信息网络安全, 2022, 22(1): 27-36. |
| [10] | 冯景瑜, 汪涛, 于婷婷, 张文波. 基于多云多链协同的医疗数据安全共享机制[J]. 信息网络安全, 2022, 22(1): 9-18. |
| [11] | 孙力. 区块链+在线教育资源联盟信息保护机制研究与应用[J]. 信息网络安全, 2021, 21(9): 32-39. |
| [12] | 陈凯杰, 熊焰, 黄文超, 武建双. 一种基于拜占庭容错的PoS共识协议形式化分析方法[J]. 信息网络安全, 2021, 21(8): 35-42. |
| [13] | 任涛, 金若辰, 罗咏梅. 融合区块链与联邦学习的网络入侵检测算法[J]. 信息网络安全, 2021, 21(7): 27-34. |
| [14] | 吴奕, 仲盛. 区块链共识算法Raft研究[J]. 信息网络安全, 2021, 21(6): 36-44. |
| [15] | 李鹏, 郑田甜, 徐鹤, 朱枫. 基于区块链技术的RFID安全认证协议[J]. 信息网络安全, 2021, 21(5): 1-11. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||