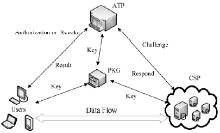
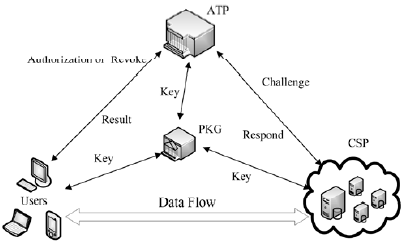
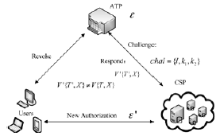
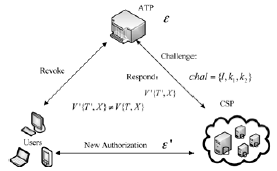
信息网络安全 ›› 2015, Vol. 15 ›› Issue (8): 1-7.doi: 10.3969/j.issn.1671-1122.2015.08.001
• 等级保护 • 下一篇
云环境下一种可撤销授权的数据拥有性证明方案
- 电子科技大学信息与软件工程学院,四川成都 610054
-
收稿日期:2015-05-18出版日期:2015-08-01发布日期:2015-08-21 -
作者简介:赵洋(1973-),男,四川,副教授,博士,主要研究方向:网络安全;陈阳(1985-),男,湖北,硕士研究生,主要研究方向:网络安全;熊虎(1982-),男,四川,副教授,博士,主要研究方向:网络安全;任化强(1990-),男,安徽,硕士研究生,主要研究方向:网络安全。
-
基金资助:国家自然科学基金[61472064,61370026];国家高技术研究发展计划[2015AA016007];四川省科技支撑计划[2014GZ0109]
A Revocable Authorization Provable Data Possession Scheme in Clouds
ZHAO Yang, CHEN Yang( ), XIONG Hu, REN Hua-qiang
), XIONG Hu, REN Hua-qiang
- School of Information and Software Engineering, University of Electronic Science and Technology of China, Chengdu Sichuan 610054, China
-
Received:2015-05-18Online:2015-08-01Published:2015-08-21
摘要:
现有的数据完整性验证主要有公共验证与私有验证两种,但当用户需要指定一个合作第三方来进行验证时就变得十分困难。对此,文章提出了一种可撤销授权的数据拥有性证明方案。方案允许用户对合作第三方审计进行授权,使其可协助用户完成远程数据的完整性验证,同时在一定程度上保护用户隐私,并且方案允许用户在需要时撤销对原第三方的授权并更换新的授权审计。在文中所设计的方案中,只有拥有授权证据的第三方才能完成整个验证过程并将验证结果返回给委托用户。另外,方案中的用户可选择保密授权证据、将授权证据发送给第三方或公开授权证据的方式实现私有验证、授权验证与公有验证的切换。方案的设计基于身份加密技术与双线性对,并通过将授权证据嵌入到完整性证明的实现授权验证与撤销。文章最后进行了安全与性能分析,证明了方案的安全性与高效性。
中图分类号:
引用本文
赵洋, 陈阳, 熊虎, 任化强. 云环境下一种可撤销授权的数据拥有性证明方案[J]. 信息网络安全, 2015, 15(8): 1-7.
ZHAO Yang, CHEN Yang, XIONG Hu, REN Hua-qiang. A Revocable Authorization Provable Data Possession Scheme in Clouds[J]. Netinfo Security, 2015, 15(8): 1-7.
使用本文
| [1] | ATENIESE G, BURNS R, CURTMOLA R, et al.Provable data possession at untrusted stores [C]//Proceedings of the 14th ACM conference on Computer and communications security.Acm, 2007: 598-609. |
| [2] | ATENIESE G, DI PIETRO R, MANCINI L V, et al.Scalable and efficient provable data possession[C]//Proceedings of the 4th international conference on Security and privacy in communication netowrks. ACM, 2008: 9. |
| [3] | SEBÉ F, DOMINGO-FERRER J, MARTINEZ-BALLESTE A, et al.Efficient remote data possession checking in critical information infrastructures[J]. Knowledge and Data Engineering, IEEE Transactions on, 2008, 20(8): 1034-1038. |
| [4] | ERWAY C, KÜPÇÜ A, PAPAMANTHOU C, et al. Dynamic provable data possession[C]//Proceedings of the 16th ACM conference on Computer and communications security. Acm, 2009: 213-222. |
| [5] | WANG C, WANG Q, REN K, et al.Privacy-preserving public auditing for data storage security in cloud computing[C]//INFOCOM, 2010 Proceedings IEEE. Ieee, 2010: 1-9. |
| [6] | ZHU Y, HU H, AHN G J, et al.Cooperative provable data possession for integrity verification in multicloud storage[J]. Parallel and Distributed Systems, IEEE Transactions on, 2012, 23(12): 2231-2244. |
| [7] | WANG H.Proxy provable data possession in public clouds[J]. Services Computing, IEEE Transactions on, 2013, 6(4): 551-559. |
| [8] | WANG H.Identity-based distributed provable data possession in multi-cloud storage[J]. Services Computing IEEE Transactions on, 2015, 8(2):328-340. |
| [9] | ZHU Y, WANG H, HU Z, et al.Dynamic audit services for integrity verification of outsourced storages in clouds[C]//Proceedings of the 2011 ACM Symposium on Applied Computing. ACM, 2011: 1550-1557. |
| [10] | REN Y, CHEN Y, WANG J, et al.Leakage Resilient Provable Data Possession in Public Cloud Storage[C]//Intelligent Information Hiding and Multimedia Signal Processing (IIH-MSP), 2014 Tenth International Conference on. IEEE, 2014: 706-709. |
| [11] | REN Y, SHEN J, WANG J, et al.Security Analysis of Delegable and Proxy Provable Data Possession in Public Cloud Storage[C]//Intelligent Information Hiding and Multimedia Signal Processing (IIH-MSP), 2014 Tenth International Conference on. IEEE, 2014: 795-798. |
| [12] | ESINER E, KÜPÇÜ A, ÖZKASAP Ö. Analysis and Optimizations on FlexDPDP: A Practical Solution for Dynamic Provable Data Possession[C]//ICC: International Conference on Intelligent Cloud Computing, Muscat. 2014. |
| [13] | JUELS A, KALISKI JR B S. PORs: Proofs of retrievability for large files[C]//Proceedings of the 14th ACM conference on Computer and communications security. Acm, 2007: 584-597. |
| [14] | SHACHAM H, WATERS B.Compact proofs of retrievability[C]//14th International Conference on the Theory and Application of Cryptology and Information Security, Melbourne, Australia, 2008: 90-107. |
| [15] | WANG Q, WANG C, LI J, et al.Enabling public verifiability and data dynamics for storage security in cloud computing[C]//14th European Symposium on Research in Computer Security, Saint-Malo, France, 2009: 355-370. |
| [16] | ZHENG Q, XU S.Fair and dynamic proofs of retrievability[C]//Proceedings of the first ACM conference on Data and application security and privacy. ACM, 2011: 237-248. |
| [17] | MO Z, ZHOU Y, CHEN S.A dynamic Proof of Retrievability (PoR) scheme with O (logn) complexity[C]//Communications (ICC), 2012 IEEE International Conference on. IEEE, 2012: 912-916. |
| [18] | YUAN J, YU S.Proofs of retrievability with public verifiability and constant communication cost in cloud[C]//Proceedings of the 2013 international workshop on Security in cloud computing. ACM, 2013: 19-26. |
| [19] | BOWERS K D, JUELS A, OPREA A.Proofs of retrievability: Theory and implementation[C]//Proceedings of the 2009 ACM workshop on Cloud computing security. ACM, 2009: 43-54. |
| [20] | DODIS Y, VADHAN S, WICHS D.Proofs of retrievability via hardness amplification[C]//6th Theory of Cryptography Conference, TCC 2009, San Francisco, CA, USA, 2009, 2009: 109-127. |
| [21] | ZHU Y, WANG H, HU Z X, et al.Zero-knowledge proofs of retrievability[J]. Science China Information Sciences, 2011, 54(8): 1608-1617. |
| [22] | SHI E, STEFANOV E, PAPAMANTHOU C.Practical dynamic proofs of retrievability[C]//Proceedings of the 2013 ACM SIGSAC conference on Computer & communications security. ACM, 2013: 325-336. |
| [23] | LI J, TAN X, CHEN X, et al.OPoR: Enabling Proof of Retrievability in Cloud Computing with Resource-Constrained Devices[J]. Cloud Computing IEEE Transactions on, 2015, 3:1-1. |
| [24] | HUI C, YI M, MAN H A.Proof of retrievability with public verifiability resilient against related-key attacks[J]. Iet Information Security, 2015, 9(1):43-49. |
| [25] | BONEH D, LYNN B, SHACHAM H. Short signatures from the Weil pairing[J]. Journal of Cryptology, 2004, 17, (4): 297-319. |
| [26] | CERTICOM S E C.. SEC 2: Recommended Elliptic Curve Domain Parameters[EB/OL]. , 2015-3-25. |
| [27] | MILLER V.Use of elliptic curves in cryptography[C]//Advances in Cryptology—CRYPTO'85 Proceedings. Springer Berlin/Heidelberg, 1986: 417-426. |
| [28] | RIVEST R L, HELLMAN M E, ANDERSON J C, et al.Responses to NIST's Proposal[J]. Communications of the ACM, 1992, 35(7): 41-54. |
| [1] | 安浩杨, 何德彪, 包子健, 彭聪. 一种基于证书的数字签名方案[J]. 信息网络安全, 2023, 23(3): 13-21. |
| [2] | 郭瑞, 陈宇霜, 郑东. 无线医疗传感网络中基于区块链的高效无证书聚合签名方案[J]. 信息网络安全, 2020, 20(10): 6-18. |
| [3] | 刘全明, 冯杰, 李尹楠, 苏莎莎. 区分身份所在层数的HIBE方案[J]. 信息网络安全, 2019, 19(11): 14-23. |
| [4] | 黎琳, 张旭霞. zk-snark的双线性对的国密化方案[J]. 信息网络安全, 2019, 19(10): 10-15. |
| [5] | 程庆丰, 阮展靖, 张瑞杰. 对三个无双线性对的密钥协商协议分析[J]. 信息网络安全, 2019, 19(1): 16-26. |
| [6] | 张琦, 林喜军, 曲海鹏. 云计算中支持授权相等测试的基于身份加密方案[J]. 信息网络安全, 2018, 18(6): 52-60. |
| [7] | 王越, 程相国, 王戌琦. 基于双线性对的密钥隔离群签名方案研究[J]. 信息网络安全, 2018, 18(6): 61-66. |
| [8] | 陈亚萌, 程相国, 王硕, 高明. 基于双线性对的无证书群签名方案研究[J]. 信息网络安全, 2017, 17(3): 53-58. |
| [9] | 唐春明, 高隆. 区块链系统下的多方密钥协商协议[J]. 信息网络安全, 2017, 17(12): 17-21. |
| [10] | 矢敏, 叶伟伟, 欧庆于. 不需双线性对的基于身份的认证密钥协商协议[J]. 信息网络安全, 2016, 16(10): 21-27. |
| [11] | 秦志光, 包文意, 赵洋, 熊虎. 云计算里的一种无双线性对的模糊关键字加密方式[J]. 信息网络安全, 2015, 15(11): 1-6. |
| [12] | 袁艳祥;游林. 基于身份加密的可认证密钥协商协议[J]. , 2014, 14(3): 0-0. |
| [13] | . 基于身份加密的可认证密钥协商协议[J]. , 2014, 14(3): 1-. |
| [14] | 李舜鹏;张明武. 基于双线性对签名的安全移动客户端[J]. , 2013, 13(5): 0-0. |
| [15] | 李伟;吕克伟. 类背包DH问题的比特安全性研究[J]. , 2013, 13(10): 0-0. |
| 阅读次数 | ||||||||||||||||||||||||||||||||||||||||||||||||||
|
全文 423
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||
|
摘要 436
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||