信息网络安全 ›› 2026, Vol. 26 ›› Issue (1): 38-48.doi: 10.3969/j.issn.1671-1122.2026.01.003
面向胶囊网络的成员推理风险评估
- 1.北京理工大学网络空间安全学院,北京 100081
2.北京理工大学计算机学院,北京 100081
3.华北电力大学控制与计算机工程学院,北京 102206
-
收稿日期:2025-07-07出版日期:2026-01-10发布日期:2026-02-13 -
通讯作者:范青qingfan@ncepu.edu.cn -
作者简介:王亚杰(1993—),男,河北,研究员,博士,CCF会员,主要研究方向为人工智能安全、数据安全、隐私保护|陆锦标(2002—),男,广东,硕士研究生,主要研究方向为联邦学习|谭冬黎(2002—),女,重庆,博士研究生,主要研究方向为人工智能安全、隐私保护|范青(1996—),女,山东,副教授,博士,CCF会员,主要研究方向为应用密码学、信息安全、安全协议设计|祝烈煌(1978—),男,浙江,教授,博士,CCF会员,主要研究方向为密码算法及安全协议、区块链、云计算安全、大数据 -
基金资助:国家自然科学基金(62402040);国家自然科学基金(62302037);国家重点研发计划(2023YFF0905300);云南省重大科技专项(202502AD080008);云南省新型研发机构培育对象项目(202404BQ040148)
Member Inference Risk Assessment for Capsule Network
WANG Yajie1, LU Jinbiao1, TAN Dongli2, FAN Qing3( ), ZHU Liehuang1
), ZHU Liehuang1
- 1. School of Cyberspace Science and Technology, Beijing Institute of Technology, Beijing 100081, China
2. School of Computer Science and Technology, Beijing Institute of Technology, Beijing 100081, China
3. School of Control and Computer Engineering, North China Electric Power University, Beijing 102206, China
-
Received:2025-07-07Online:2026-01-10Published:2026-02-13
摘要:
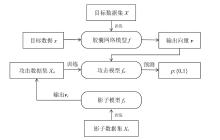
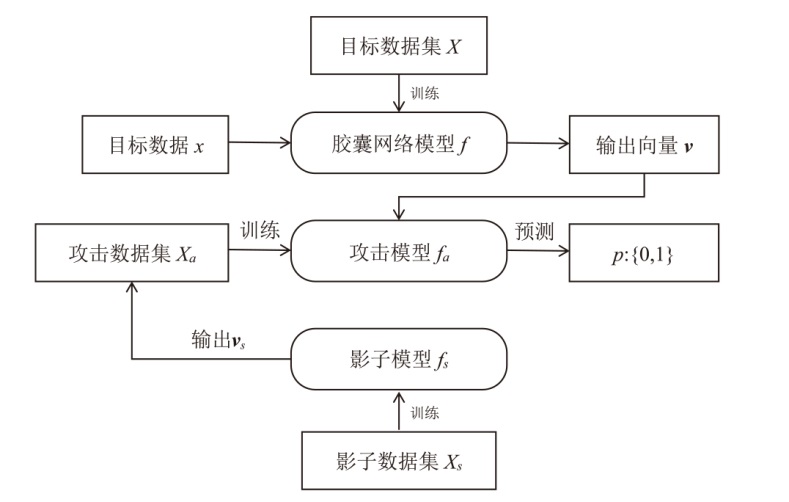
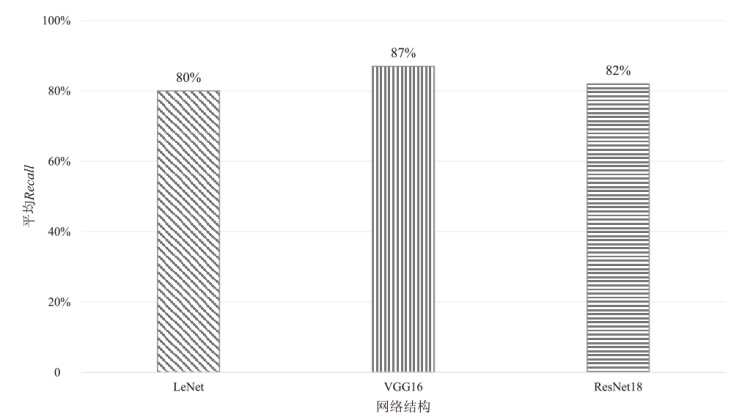
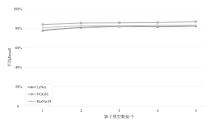
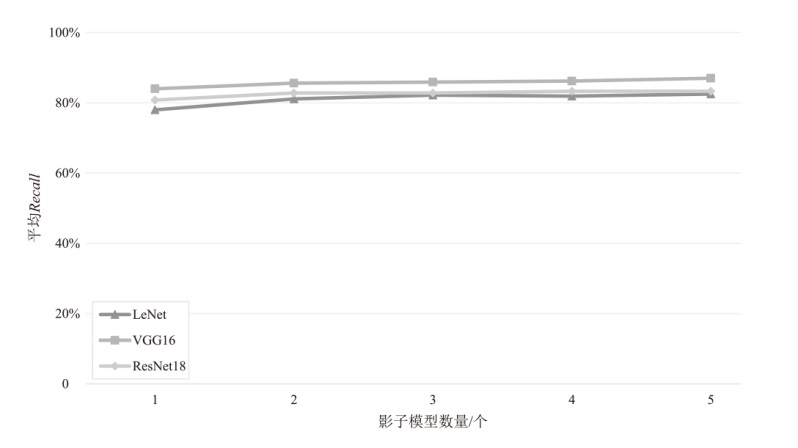
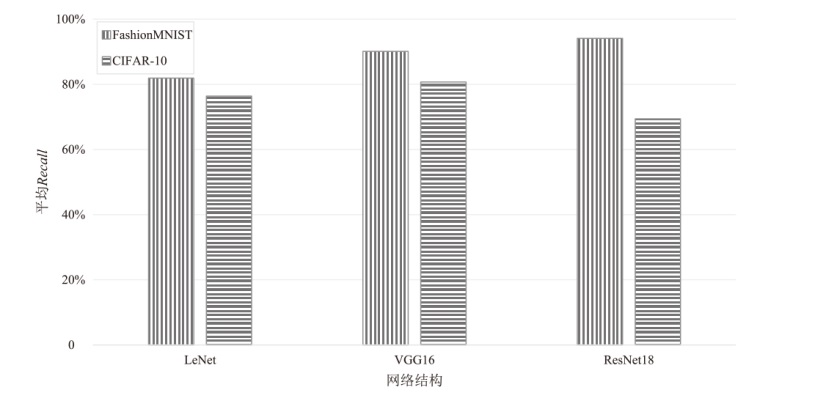
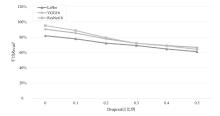
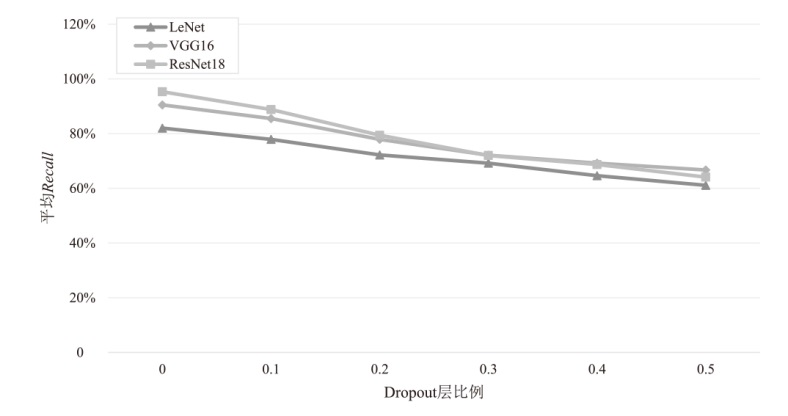
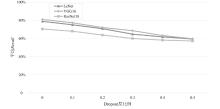
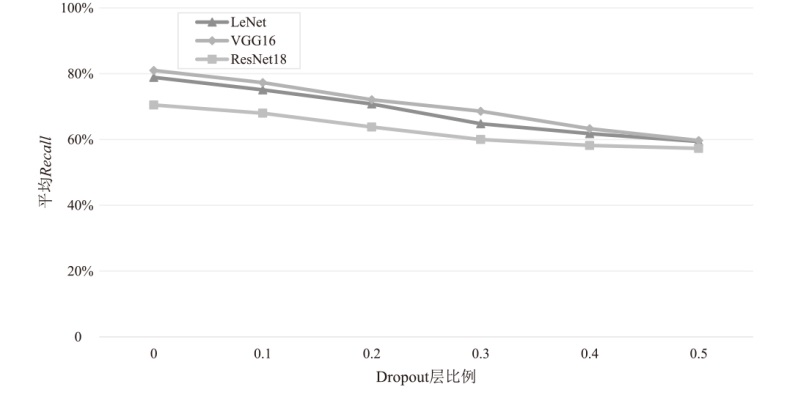
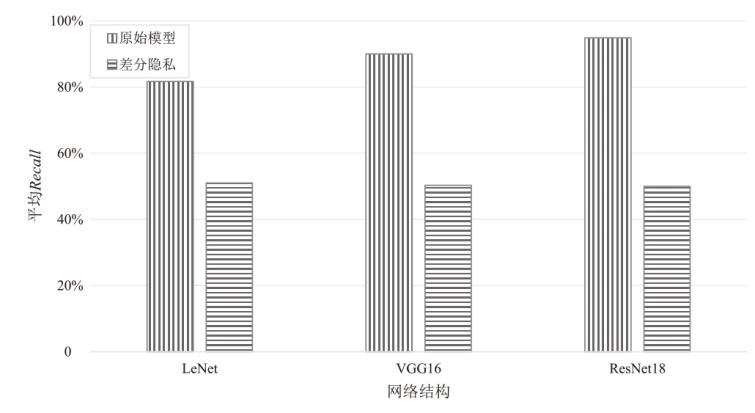
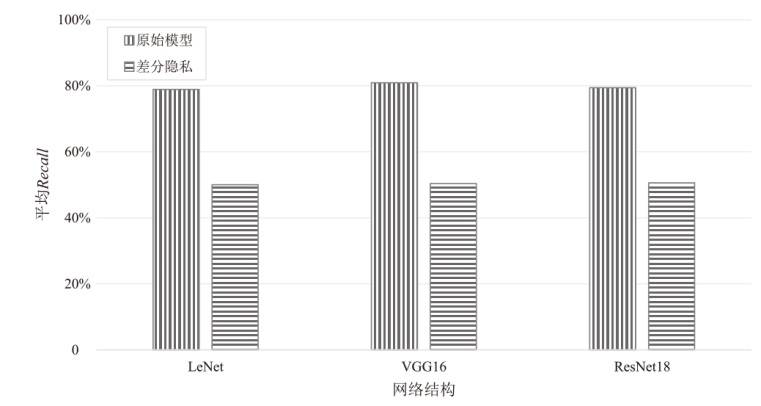
为评估胶囊网络对成员推理攻击的防御能力,文章在FashionMNIST和CIFAR-10数据集上进行成员推理攻击实验,选用LeNet、VGG16和ResNet18作为影子模型。文章测试了影子模型数量对攻击效果的影响,探究了模型过拟合程度与成员推理攻击的关系,并验证了差分隐私对该攻击的防御效果。实验结果表明,成员推理攻击的攻击成功率高达94.8%,但在1~5个影子模型下,影子模型数量对攻击成功率的影响不显著。此外,攻击成功率随模型过拟合程度的增加而上升,虽然差分隐私可有效提升胶囊网络的防御能力,但会导致其训练时间增加133%以上。上述结果显示,针对胶囊网络的成员推理攻击行为及其防御规律与常见模型相似,因此,在胶囊网络的设计与应用中需充分考虑其安全风险。
中图分类号:
引用本文
王亚杰, 陆锦标, 谭冬黎, 范青, 祝烈煌. 面向胶囊网络的成员推理风险评估[J]. 信息网络安全, 2026, 26(1): 38-48.
WANG Yajie, LU Jinbiao, TAN Dongli, FAN Qing, ZHU Liehuang. Member Inference Risk Assessment for Capsule Network[J]. Netinfo Security, 2026, 26(1): 38-48.
| [1] | AL-RUBAIE M, CHANG J M. Privacy-Preserving Machine Learning: Threats and Solutions[J]. IEEE Security & Privacy, 2019, 17(2): 49-58. |
| [2] | SABOUR S, FROSST N, HINTON G E. Dynamic Routing between Capsules[C]// ACM. The 31st International Conference on Neural Information Processing Systems. New York: ACM, 2017: 3856-3866. |
| [3] |
YADAV S, DHAGE S. TE-CapsNet: Time Efficient Capsule Network for Automatic Disease Classification from Medical Images[J]. Multimedia Tools and Applications, 2024, 83(16): 49389-49418.
doi: 10.1007/s11042-023-17458-4 |
| [4] |
DHALLA S, MITTAL A, GUPTA S. LeukoCapsNet: A Resource-Efficient Modified CapsNet Model to Identify Leukemia from Blood Smear Images[J]. Neural Computing and Applications, 2024, 36(5): 2507-2524.
doi: 10.1007/s00521-023-09157-w |
| [5] | LEI Yongjia, WU Zujian, LI Zhiying, et al. BP-CapsNet: An Image-Based Deep Learning Method for Medical Diagnosis[EB/OL]. (2023-10-01)[2025-05-23]. https://doi.org/10.1016/j.asoc.2023.110683. |
| [6] | SHOKRI R, STRONATI M, SONG Congzheng, et al. Membership Inference Attacks Against Machine Learning Models[C]// IEEE. 2017 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2017: 3-18. |
| [7] | BACKES M, BERRANG P, HUMBERT M, et al. Membership Privacy in MicroRNA-Based Studies[C]// ACM. The 2016 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2016: 319-330. |
| [8] | HAGESTEDT I, ZHANG Yang, HUMBERT M, et al. MBeacon: Privacy-Preserving Beacons for DNA Methylation Data[C]// IEEE. 2019 Network and Distributed System Security Symposium. New York: IEEE, 2019: 21-27. |
| [9] | PYRGELIS A, TRONCOSO C, DE C E. Knock Knock, Who’s There? Membership Inference on Aggregate Location Data[C]// IEEE. 2018 Network and Distributed System Security Symposium. New York: IEEE, 2018: 35-42. |
| [10] | HU Hongsheng, SALCIC Z, SUN Lichao, et al. Membership Inference Attacks on Machine Learning: A Survey[J]. ACM Computing Surveys, 2022, 54(11s): 1-37. |
| [11] | LONG Yunhui, BINDSCHAEDLER V, WANG Lei, et al. Understanding Membership Inferences on Well-Generalized Learning Models[EB/OL]. (2018-02-13)[2025-05-23]. https://doi.org/10.48550/arXiv.1802.04889. |
| [12] | IROLLA P, CHATEL G. Demystifying the Membership Inference Attack[C]// IEEE. 2019 12th CMI Conference on Cybersecurity and Privacy (CMI). New York: IEEE, 2019: 1-7. |
| [13] | LEINO K, FREDRIKSON M. Stolen Memories: Leveraging Model Memorization for Calibrated White-Box Membership Inference[C]// USENIX. The 29th USENIX Conference on Security Symposium. Berkeley: USENIX, 2020: 291-313. |
| [14] | CHOO C A C, TRAMER F, CARLINI N, et al. Label-Only Membership Inference Attacks[C]// ACM. The 38th International Conference on Machine Learning. New York: ACM, 2021: 1964-1974. |
| [15] | LI Zheng, ZHANG Yang. Membership Leakage in Label-Only Exposures[C]// ACM. The 2021 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2021: 880-895. |
| [16] | YEOM S, GIACOMELLI I, FREDRIKSON M, et al. Privacy Risk in Machine Learning: Analyzing the Connection to Overfitting[C]// IEEE. 2018 IEEE 31st Computer Security Foundations Symposium (CSF). New York: IEEE, 2018: 268-282. |
| [17] | REZAEI S, SHAFIQ Z, LIU Xin. Accuracy-Privacy Trade-Off in Deep Ensembles[C]// IEEE. 2023 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2023: 364-381. |
| [18] | SRIVASTAVA N, HINTON G, KRIZHEVSKY A, et al. Dropout: A Simple Way to Prevent Neural Networks from Overfitting[J]. Journal of Machine Learning Research, 2014, 15(1): 1929-1958. |
| [19] | KAYA Y, DUMITRAS T. When Does Data Augmentation Help with Membership Inference Attacks[C]// ACM. The 38th International Conference on Machine Learning. New York: ACM, 2021: 5345-5355. |
| [20] | CARUANA R, LAWRENCE S, GILES C. Overfitting in Neural Nets:Backpropagation, Conjugate Gradient, and Early Stopping[C]// NIPS. The 14th International Conference on Neural Information Processing Systems. Cambridge: MIT Press, 2000: 381-387. |
| [21] | NASR M, SHOKRI R, HOUMANSADR A. Machine Learning with Membership Privacy Using Adversarial Regularization[C]// ACM. The 2018 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2018: 634-646. |
| [22] | SALEM A, ZHANG Yang, HUMBERT M, et al. ML-Leaks: Model and Data Independent Membership Inference Attacks and Defenses on Machine Learning Models[C]// IEEE. 2019 Network and Distributed System Security Symposium. New York: IEEE, 2019: 111-115. |
| [23] |
DWORK C, ROTH A. The Algorithmic Foundations of Differential Privacy[J]. Foundations and Trends in Theoretical Computer Science, 2014, 9(3/4): 211-407.
doi: 10.1561/TCS URL |
| [24] | JIA Jinyuan, SALEM A, BACKES M, et al. MemGuard: Defending against Black-Box Membership Inference Attacks via Adversarial Examples[C]// ACM. The 2019 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2019: 259-274. |
| [25] | ZHANG Liheng, EDRAKI M, QI Guojun. CapProNet: Deep Feature Learning via Orthogonal Projections onto Capsule Subspaces[C]// ACM. The 32nd International Conference on Neural Information Processing Systems. New York: ACM, 2018: 5819-5828. |
| [26] | PHAYE S S R, SIKKA A, DHALL A, et al. Dense and Diverse Capsule Networks: Making the Capsules Learn Better[EB/OL]. (2018-05-10)[2025-05-23]. https://doi.org/10.48550/arXiv.1805.04001. |
| [27] | DELIEGE A, CIOPPA A, VAN D M. HitNet: A Neural Network with Capsules Embedded in a Hit-or-Miss Layer, Extended with Hybrid Data Augmentation and Ghost Capsules[EB/OL]. (2018-06-18)[2025-05-23]. https://doi.org/10.48550/arXiv.1806.06519. |
| [28] | SAHU S K, KUMAR P, SINGH A P. Dynamic Routing Using Inter Capsule Routing Protocol between Capsules[EB/OL]. (2018-05-27)[2025-05-23]. https://ieeexplore.ieee.org/document/8588168. |
| [29] | WANG Dilin, LIU Qiang. An Optimization View on Dynamic Routing between Capsules[C]// ACM. The 6th International Conference on Learning Representations. New York: ACM, 2018: 11-14. |
| [30] | YANG Jucheng, HAN Shujie, MAO Lei, et al. Overview of Capsule Network Model[J]. Journal of Shandong University (Engineering Science), 2019, 49(6): 1-10. |
| 杨巨成, 韩书杰, 毛磊, 等. 胶囊网络模型综述[J]. 山东大学学报(工学版), 2019, 49(6): 1-10. | |
| [31] | HINTON G E, SABOUR S, FROSST N. Matrix Capsules with EM Routing[C]// ACM. The 6th International Conference on Learning Representations. New York: ACM, 2018: 21-29. |
| [32] | KRIZHEVSKY A, HINTON G. Learning Multiple Layers of Features from Tiny Images[C]// IEEE. The Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2009: 2311-2320. |
| [33] | HAN Xiao, KASHIF R, ROLAND V. Fashion-MNIST: A Novel Image Dataset for Benchmarking Machine Learning Algorithms[EB/OL]. (2017-09-15)[2025-05-23]. https://doi.org/10.48550/arXiv.1708.07747. |
| [1] | 赵伟, 任潇宁, 薛吟兴. 基于集成学习的成员推理攻击方法[J]. 信息网络安全, 2024, 24(8): 1252-1264. |
| [2] | 戚晗, 王敬童, ABDULLAH Gani, 拱长青. 基于随机量子层的变分量子卷积神经网络鲁棒性研究[J]. 信息网络安全, 2024, 24(3): 363-373. |
| [3] | 冯光升, 蒋舜鹏, 胡先浪, 马明宇. 面向物联网的入侵检测技术研究新进展[J]. 信息网络安全, 2024, 24(2): 167-178. |
| [4] | 林怡航, 周鹏远, 吴治谦, 廖勇. 基于触发器逆向的联邦学习后门防御方法[J]. 信息网络安全, 2024, 24(2): 262-271. |
| [5] | 印杰, 陈浦, 杨桂年, 谢文伟, 梁广俊. 基于人工智能的物联网DDoS攻击检测[J]. 信息网络安全, 2024, 24(11): 1615-1623. |
| [6] | 陈宝刚, 张毅, 晏松. 民航空管信息系统用户多因子持续身份可信认证方法研究[J]. 信息网络安全, 2024, 24(11): 1632-1642. |
| [7] | 兰浩良, 王群, 徐杰, 薛益时, 张勃. 基于区块链的联邦学习研究综述[J]. 信息网络安全, 2024, 24(11): 1643-1654. |
| [8] | 王南, 袁也, 杨浩然, 文周之, 苏明, 刘晓光. 环保大数据在区块链中的隐私计算[J]. 信息网络安全, 2024, 24(10): 1515-1527. |
| [9] | 张子涵, 赖清楠, 周昌令. 深度学习框架模糊测试研究综述[J]. 信息网络安全, 2024, 24(10): 1528-1536. |
| [10] | 萨其瑞, 尤玮婧, 张逸飞, 邱伟杨, 马存庆. 联邦学习模型所有权保护方案综述[J]. 信息网络安全, 2024, 24(10): 1553-1561. |
| [11] | 宋玉涵, 祝跃飞, 魏福山. 一种基于AdaBoost模型的区块链异常交易检测方案[J]. 信息网络安全, 2024, 24(1): 24-35. |
| [12] | 薛羽, 张逸轩. 深层神经网络架构搜索综述[J]. 信息网络安全, 2023, 23(9): 58-74. |
| [13] | 王鹃, 张冲, 龚家新, 李俊娥. 基于机器学习的模糊测试研究综述[J]. 信息网络安全, 2023, 23(8): 1-16. |
| [14] | 许春根, 薛少康, 徐磊, 张盼. 基于安全两方计算的高效神经网络推理协议[J]. 信息网络安全, 2023, 23(7): 22-30. |
| [15] | 赵小林, 王琪瑶, 赵斌, 薛静锋. 基于机器学习的匿名流量分类方法研究[J]. 信息网络安全, 2023, 23(5): 1-10. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||