信息网络安全 ›› 2024, Vol. 24 ›› Issue (1): 24-35.doi: 10.3969/j.issn.1671-1122.2024.01.003
一种基于AdaBoost模型的区块链异常交易检测方案
- 中国人民解放军信息工程大学网络空间安全学院,郑州 450001
-
收稿日期:2023-08-02出版日期:2024-01-10发布日期:2024-01-24 -
通讯作者:宋玉涵 E-mail:lynn.redhead@hotmail.com -
作者简介:宋玉涵(1989—),女,安徽,博士研究生,主要研究方向为隐私计算和区块链|祝跃飞(1962—),男,浙江,教授,博士,主要研究方向为网络空间安全|魏福山(1983—),男,甘肃,副教授,博士,主要研究方向为密码学 -
基金资助:国家自然科学基金(61772548);国家重点研发计划(2019QY1300);河南省优秀青年基金(222300420099);河南省重大公益项目(201300210200)
An Anomaly Detection Scheme for Blockchain Transactions Based on AdaBoost Model
SONG Yuhan( ), ZHU Yuefei, WEI Fushan
), ZHU Yuefei, WEI Fushan
- Institute of Cyberspace Security, Information Engineering University of PLA, Zhengzhou 450001, China
-
Received:2023-08-02Online:2024-01-10Published:2024-01-24 -
Contact:SONG Yuhan E-mail:lynn.redhead@hotmail.com
摘要:
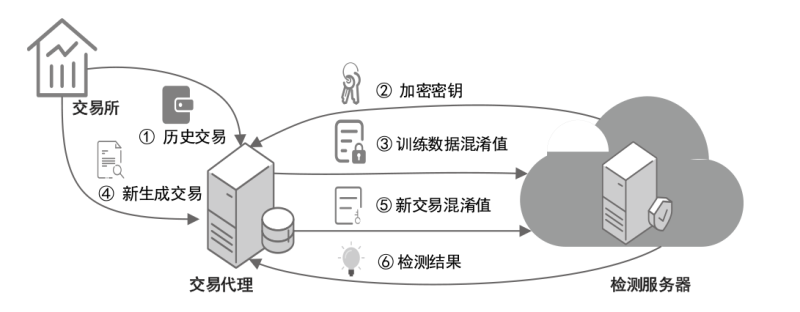
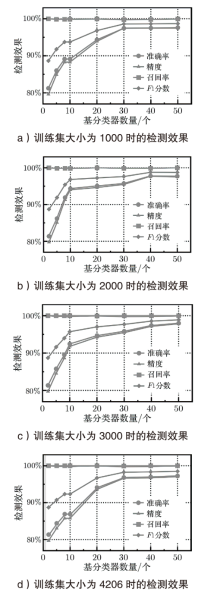
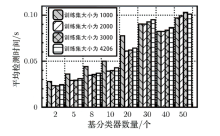
针对区块链系统加密货币交易记录中存在的盗币异常行为,文章基于AdaBoost模型提出一种具有隐私保护功能的异常交易检测方案。该方案采用加法同态加密和矩阵混淆技术,在有效识别并预测异常交易的同时,保证交易数据的隐私性。此外,在云外包环境中设计实现方案的底层协议,并证明了方案的正确性和隐私保护性质。与同类协议相比,该方案在保证隐私性的同时,具有较高的检测准确率和召回率,平均每条记录的检测时间为毫秒级,适用于真实加密货币交易的检测场景。
中图分类号:
引用本文
宋玉涵, 祝跃飞, 魏福山. 一种基于AdaBoost模型的区块链异常交易检测方案[J]. 信息网络安全, 2024, 24(1): 24-35.
SONG Yuhan, ZHU Yuefei, WEI Fushan. An Anomaly Detection Scheme for Blockchain Transactions Based on AdaBoost Model[J]. Netinfo Security, 2024, 24(1): 24-35.
表1
异常交易检测方法性能对比
| 方法 | 特征 维度 | 隐私 保护 | 通信 带宽 | 通信轮数 | 计算 复杂度 | 准确率 | 精度 | 召回率 | F1 分数 |
|---|---|---|---|---|---|---|---|---|---|
| LOF[ | 3 | 否 | 1 | 89.5% | 0 | 0 | — | ||
| MDB[ | 3 | 否 | 1 | 89.6% | 0.5% | 0.6% | 0.006 | ||
| OCSVM[ | 3 | 否 | 1 | 82.8% | 0.5% | 0.2% | 0.003 | ||
| ADaaS[ | 9 | 是 | 2 | 97.8% | 85.8% | 87.5% | 0.867 | ||
| 本文方法 | 9 | 是 | 2 | 97.3% | 97.1% | 100% | 0.985 |
表1
| [1] | KUMAR N, SINGH A, SHUKLA S K. Detecting Malicious Accounts on the Ethereum Blockchain with Supervised Learning[C]// Springer. Cyber Security Cryptography and Machine Learning- Fourth International Symposium. Heidelberg: Springer, 2020: 94-109. |
| [2] | BARTOLETTI M, LANDE S, POMPIANU L, et al. A General Framework for Blockchain Analytics[C]// ACM. The 1st Workshop on Scalable and Resilient Infrastructures for Distributed Ledgers. New York: ACM, 2017: 1-6. |
| [3] | KHALILOV M C K, LEVI A. A Survey on Anonymity and Privacy in Bitcoin-Like Digital Cash Systems[J]. IEEE Communications Surveys & Tutorials, 2018, 20(3): 2543-2585. |
| [4] | JIA Jinyuan, SALEM A, BACKES M, et al. Memguard: Defending Against Black-Box Membership Inference Attacks via Adversarial Examples[C]// ACM.The 26th ACM Conference on Computer and Communications Security (CCS 2019). New York: ACM, 2019: 259-274. |
| [5] | TRAMER F, ZHANG Fan, JUELS A, et al. Stealing Machine Learning Models via Prediction Apis[C]// USENIX. 25th USENIX Security Symposium 2016. Berkeley: USENIX, 2016: 601-618. |
| [6] | HIRSHMAN J, HUANG Yifei, MACKE S. Unsupervised Approaches to Detecting Anomalous Behavior in the Bitcoin Transaction Network[EB/OL]. (2013-09-23) [2023-08-01]. https://cs229.stanford.edu/proj2013/HirshmanHuangMacke-UnsupervisedApproachesToDetectingAnomalousBehaviorInTheBitcoinTransactionNetwork.pdf. |
| [7] | PHAM T, LEE S. Anomaly Detection in Bitcoin Network Using Unsupervised Learning Methods[EB/OL].(2016-11-12) [2023-08-01]. http://arxiv.org/abs/1611.03941. |
| [8] | PHAM T, LEE S. Anomaly Detection in the Bitcoin System-A Network Perspective[EB/OL]. (2016-11-13) [2023-08-01]. http://arxiv.org/abs/1611.03942. |
| [9] | MONAMO P M, MARIVATE V, TWALA B. A Multifaceted Approach to Bitcoin Fraud Detection: Global and Local Outliers[C]// IEEE. The 15th IEEE International Conference on Machine Learning and Applications. New York: IEEE, 2016: 188-194. |
| [10] | AWAN M K, CORTESI A. Blockchain Transaction Analysis Using Dominant Sets[C]// Springer. The 16th IFIP TC8 International Conference. Heidelberg: Springer, 2017: 229-239. |
| [11] | KIM J, NAKASHIMA M, FAN Wenjun, et al. Anomaly Detection Based on Traffic Monitoring for Secure Blockchain Networking[C]// IEEE. IEEE International Conference on Blockchain and Cryptocurrency (ICBC 2021). New York: IEEE, 2021: 1-9. |
| [12] |
SONG Yuhan, WEI Fushan, ZHU Kaijie, et al. Anomaly Detection as a Service: An Outsourced Anomaly Detection Scheme for Blockchain in a Privacy Preserving Manner[J]. IEEE Transactions on Network and Service Management, 2022, 19(4): 3794-3809.
doi: 10.1109/TNSM.2022.3215006 URL |
| [13] | LI Qinbin, WU Zhaomin, WEN Zeyi, et al. Privacy-Preserving Gradient Boosting Decision Trees[EB/OL]. (2020-10-29) [2023-08-01]. https://arxiv.org/abs/1911.04209. |
| [14] | YANG Mengwei, SONG Linqi, XU Jie, et al. The Tradeoff Between Privacy and Accuracy in Anomaly Detection Using Federated XGBoost[EB/OL]. (2019-10-14) [2023-08-01]. https://arxiv.org/abs/1907.07157. |
| [15] | CHENG Kewei, FAN Tao, JIN Yilun, et al. SecureBoost: A Lossless Federated Learning Framework[EB/OL].(2021-04-07) [2023-08-01]. https://arxiv.org/abs/1901.08755. |
| [16] | CHEN Weijing, MA Guoqiang, FAN Tao, et al. SecureBoost+: A High Performance Gradient Boosting Tree Framework for Large Scale Vertical Federated Learning[EB/OL]. (2021-12-23) [2023-08-01]. https://arxiv.org/abs/2110.10927. |
| [17] |
FREUND Y, SCHAPIRE R E. A Decision-Theoretic Generalization of on-Line Learning and an Application to Boosting[J]. Journal of Computer and System Sciences, 1997, 55(1): 119-139.
doi: 10.1006/jcss.1997.1504 URL |
| [18] | MIVULE K, TURNER C, JI S. Towards A Differential Privacy and Utility Preserving Machine Learning Classifier[C]// Elsevier. The Complex Adaptive Systems 2012 Conference. Amsterdam: Elsevier, 2012: 176-181. |
| [19] | SHEN Siqian. Research on Differential Privacy Protection Classification Algorithm[D]. Nanjing: Nanjing University of Aeronautics and Astronautics, 2017. |
| 沈思倩. 关于差分隐私保护分类算法的研究[D]. 南京: 南京航空航天大学, 2017. | |
| [20] |
MA Zhuo, LIU Yang, LIU Ximeng, et al. Lightweight Privacy-Preserving Ensemble Classification for Face Recognition[J]. IEEE Internet of Things Journal, 2019, 6(3): 5778-5790.
doi: 10.1109/JIOT.2019.2905555 |
| [21] | DAVOUDI M. Efficient and Privacy-Preserving Adaboost Classification Framework for Mining Healthcare Data over Outsourced Cloud[D]. New Jersey: University of New Brunswick, 2020. |
| [22] | PAILLIER P. Public-Key Cryptosystems Based on Composite Degree Residuosity Classes[C]// Springer. EUROCRYPT’ 99. Heidelberg:Springer, 1999: 223-238. |
| [23] | CHEN Binjie. Research on Blockchain Abnormal Transaction Detection for Privacy Protection[D]. Zhengzhou: Information Engineering University of PLA, 2022. |
| 陈彬杰. 隐私保护的区块链异常交易检测研究[D]. 郑州: 战略支援部队信息工程大学, 2022. |
| [1] | 许可, 李嘉怡, 蒋兴浩, 孙锬锋. 一种基于轮廓稀疏对抗的视频步态隐私保护算法[J]. 信息网络安全, 2024, 24(1): 48-59. |
| [2] | 赖成喆, 赵益宁, 郑东. 基于同态加密的隐私保护与可验证联邦学习方案[J]. 信息网络安全, 2024, 24(1): 93-105. |
| [3] | 秦中元, 马楠, 余亚聪, 陈立全. 基于双重图神经网络和自编码器的网络异常检测[J]. 信息网络安全, 2023, 23(9): 1-11. |
| [4] | 薛羽, 张逸轩. 深层神经网络架构搜索综述[J]. 信息网络安全, 2023, 23(9): 58-74. |
| [5] | 王鹃, 张冲, 龚家新, 李俊娥. 基于机器学习的模糊测试研究综述[J]. 信息网络安全, 2023, 23(8): 1-16. |
| [6] | 许春根, 薛少康, 徐磊, 张盼. 基于安全两方计算的高效神经网络推理协议[J]. 信息网络安全, 2023, 23(7): 22-30. |
| [7] | 俞惠芳, 乔一凡, 孟茹. 面向区块链金融的抗量子属性基门限环签密方案[J]. 信息网络安全, 2023, 23(7): 44-52. |
| [8] | 蒋英肇, 陈雷, 闫巧. 基于双通道特征融合的分布式拒绝服务攻击检测算法[J]. 信息网络安全, 2023, 23(7): 86-97. |
| [9] | 唐雨, 张驰. 一种基于Intel SGX的信息中心网络隐私保护方案[J]. 信息网络安全, 2023, 23(6): 55-65. |
| [10] | 赵小林, 王琪瑶, 赵斌, 薛静锋. 基于机器学习的匿名流量分类方法研究[J]. 信息网络安全, 2023, 23(5): 1-10. |
| [11] | 李增鹏, 王梅, 陈梦佳. 新形态伪随机函数研究[J]. 信息网络安全, 2023, 23(5): 11-21. |
| [12] | 杜卫东, 李敏, 韩益亮, 王绪安. 基于密文转换的高效通用同态加密框架[J]. 信息网络安全, 2023, 23(4): 51-60. |
| [13] | 尹曙, 陈兴蜀, 朱毅, 曾雪梅. 基于字符空间构造的域名匿名化算法[J]. 信息网络安全, 2023, 23(4): 80-89. |
| [14] | 郭瑞, 魏鑫, 陈丽. 工业物联网环境下可外包的策略隐藏属性基加密方案[J]. 信息网络安全, 2023, 23(3): 1-12. |
| [15] | 李晓华, 王苏杭, 李凯, 徐剑. 一种支持隐私保护的传染病人际传播分析模型[J]. 信息网络安全, 2023, 23(3): 35-44. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||