信息网络安全 ›› 2024, Vol. 24 ›› Issue (1): 14-23.doi: 10.3969/j.issn.1671-1122.2024.01.002
BFT问责机制综述
- 1.北京大学软件与微电子学院,北京 102600
2.北京大学计算机学院,北京 100871
-
收稿日期:2023-12-11出版日期:2024-01-10发布日期:2024-01-24 -
通讯作者:孙惠平 E-mail:sunhp@ss.pku.edu.cn -
作者简介:孙惠平(1975—),男,江苏,讲师,硕士,CCF会员,主要研究方向为身份认证、区块链和智能风控|周进爵(2000—),男,山西,硕士研究生,主要研究方向为区块链技术及应用|刘澍轩(2000—),男,青海,硕士研究生,主要研究方向为区块链技术及应用|陈钟(1964—),男,江苏,教授,博士,CCF会士,主要研究方向为信息安全和区块链 -
基金资助:国家自然科学基金(62172010);南宁市科学研究与技术开发计划(202001073)
Survey on Byzantine Fault Tolerance Accountability Mechanisms
SUN Huiping1( ), ZHOU Jinjue1, LIU Shuxuan1, CHEN Zhong2
), ZHOU Jinjue1, LIU Shuxuan1, CHEN Zhong2
- 1. School of Software & Microelectronics, Peking University, Beijing 102600, China
2. School of Computer Science, Peking University, Beijing 100871, China
-
Received:2023-12-11Online:2024-01-10Published:2024-01-24 -
Contact:SUN Huiping E-mail:sunhp@ss.pku.edu.cn
摘要:
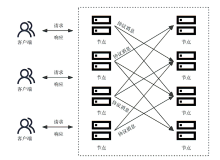
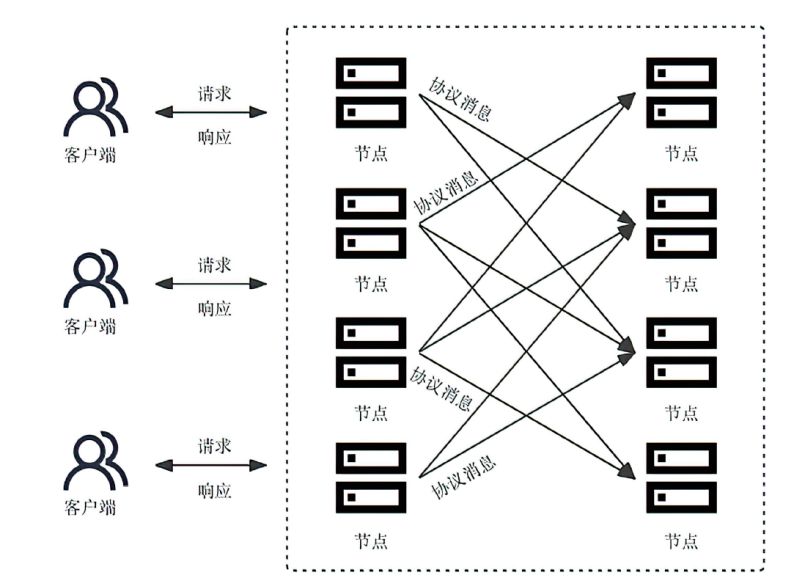
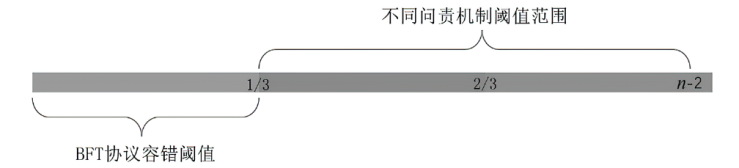
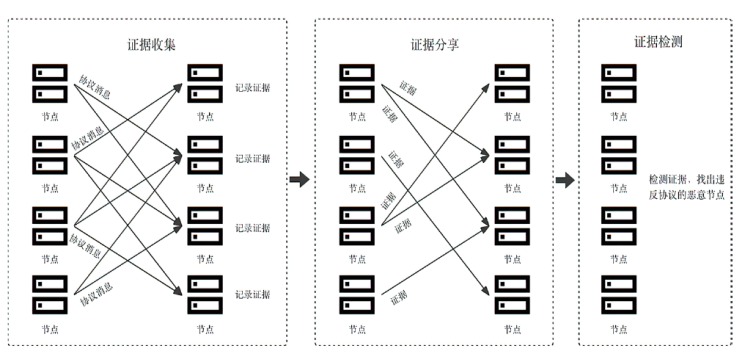
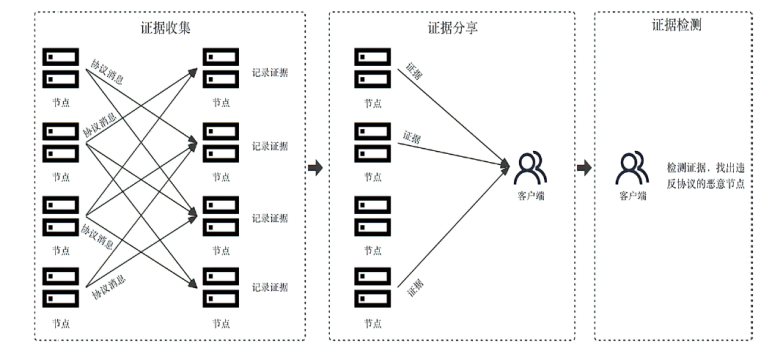
拜占庭容错(Byzantine Fault Tolerance,BFT)协议在保障区块链或分布式系统在面临节点故障和恶意行为时的一致性和可靠性方面发挥着关键作用。BFT问责机制通过记录和共享共识过程中的共识节点行为,旨在识别拜占庭节点,并能够有效解决在拜占庭节点数量超过1/3时,传统的BFT协议无法确保安全性和活性的问题。文章系统地总结了目前已有的BFT问责协议,包括服务端问责机制、客户端问责机制和BFT内嵌问责机制。文章还对这些机制进行比较和分析,探讨了存在的挑战,并展望了未来可能的发展方向。
中图分类号:
引用本文
孙惠平, 周进爵, 刘澍轩, 陈钟. BFT问责机制综述[J]. 信息网络安全, 2024, 24(1): 14-23.
SUN Huiping, ZHOU Jinjue, LIU Shuxuan, CHEN Zhong. Survey on Byzantine Fault Tolerance Accountability Mechanisms[J]. Netinfo Security, 2024, 24(1): 14-23.
| [1] | CASTRO M, LISKOV B. Practical Byzantine Fault Tolerance[C]// ACM. Proceedings of the Third Symposium on Operating Systems Design and Implementatio. New York: ACM, 1999: 173-186. |
| [2] | YIN Maofan, MALKHI D, REITER M K, et al. HotStuff: BFT Consensus with Linearity and Responsiveness[C]// ACM. Proceedings of the 2019 ACM Symposium on Principles of Distributed Computing. New York: ACM, 2019: 347-356. |
| [3] | BUCHMAN E. Tendermint: Byzantine Fault Tolerance in the Age of Blockchains[D]. Guelph: University of Guelph, 2016. |
| [4] | GILAD Y, HEMO R, MICALI S, et al. Algorand: Scaling Byzantine Agreements for Cryptocurrencies[C]// ACM. Proceedings of the 26th Symposium on Operating Systems Principles. New York: ACM, 2017: 51-68. |
| [5] | MAO Zhilai, LIU Yanan, SUN Huiping, et al. Research on Blockchain Performance Scalability and SecuritylJ]. Netinfo Security, 2020, 20(3): 56-64. |
| 毛志来, 刘亚楠, 孙惠平, 等. 区块链性能扩展与安全研究. 信息网络安全, 2020, 20(3):56-64. | |
| [6] |
LAMPORT L, SHOSTAK R, PEASE M. The Byzantine Generals Problem[J]. ACM Transactions on Programming Languages and Systems, 1982, 4(3): 382-401.
doi: 10.1145/357172.357176 URL |
| [7] | HAEBERLEN A, KOUZNETSOV P, DRUSCHEL P. PeerReview: Practical Accountability for Distributed Systems[J]. ACM SIGOPS Operating Systems Review, 2007, 41(6): 175-188. |
| [8] | CIVIT P, GILBERT S, GRAMOLI V. Polygraph: Accountable Byzantine Agreement[C]// IEEE. 2021 IEEE 41st International Conference on Distributed Computing Systems (ICDCS). New York: IEEE, 2021: 403-413. |
| [9] | SHENG Peiyao, WANG Gerui, NAYAK K, et al. BFT Protocol Forensics[C]// ACM. Proceedings of the 2021 ACM SIGSAC Conference on Computer and Communications Security. New York: IEEE, 2021: 1722-1743. |
| [10] | SHAMIS A, PIETZUCH P, CANAKCI B, et al. IA-CCF: Individual Accountability for Permissioned Ledgers[C]// USENIX. 19th USENIX Symposium on Networked Systems Design and Implementation (NSDI 22). Renton: USENIX Association, 2022: 467-491. |
| [11] | BUTERIN V, GRIFFITH V. Casper the Friendly Finality Gadget[EB/OL]. (2019-01-22) [2023-12-01]. https://arxiv.org/abs/1710.09437. |
| [12] | ABRAHAM I, MALKHI D. The Blockchain Consensus Layer and BFT[EB/OL]. (2017-10-20) [2023-12-01]. http://eatcs.org/beatcs/index.php/beatcs/article/view/506/495. |
| [13] | ZHENG Min, WANG Hong, LIU Hong, et al. Survey on Consensus Algorithms of Blockchain[J]. Netinfo Security, 2019, 19(7): 8-24. |
| 郑敏, 王虹, 刘洪, 等. 区块链共识算法研究综述[J]. 信息网络安全, 2019, 19(7):8-24. | |
| [14] | WANG Gang. SoK: Understanding BFT Consensus in the Age of Blockchains[EB/OL]. (2021-07-05) [2023-12-01]. https://eprint.iacr.org/2021/911. |
| [15] |
FENG Liaoliao, DING Yan, LIU Kunlin, et al. Research Progress on Blockchain BFT Consensus Algorithm[J]. Computer Science, 2022, 49(4): 329-339.
doi: 10.11896/jsjkx.210700011 |
|
冯了了, 丁滟, 刘坤林, 等. 区块链BFT共识算法研究进展[J]. 计算机科学, 2022, 49(4):329-339.
doi: 10.11896/jsjkx.210700011 |
|
| [16] |
DWORK C, LYNCH N. Stockmeyer L: Consensus in the Presence of Partial Synchrony[J]. Journal of the ACM, 2002, 35(2): 288-323.
doi: 10.1145/42282.42283 URL |
| [17] | BEN-OR M. Another Advantage of Free Choice (Extended Abstract)Completely Asynchronous Agreement Protocols[C]// ACM. Proceedings of the Second Annual ACM Symposium on Principles of Distributed Computing. New York: ACM, 1983: 27-30. |
| [18] | ZENG Shuai, YUAN Yong, NI Xiaochun, et al. Scaling Blockchain towards Bitcoin: Key Technologies, Constraints and Related Issues[J]. Acta Automatica Sinica, 2019, 45(6): 1015-1030. |
| 曾帅, 袁勇, 倪晓春, 等. 面向比特币的区块链扩容:关键技术,制约因素与衍生问题[J]. 自动化学报, 2019, 45(6):1015-1030. | |
| [19] | RUSSINOVICH M, ASHTON E, AVANESSIANS C, et al. CCF: A Framework for Building Confidential Verifiable Replicated Services[EB/OL]. (2019-06-11) [2023-12-01]. https://www.microsoft.com/en-us/research/publication/ccf-a-framework-for-building-confidential-verifiable-replicated-services/. |
| [20] | NAKAMOTO S. Bitcoin: A Peer to Peer Electronic Cash System[EB/OL]. (2018-04-10) [2023-12-01]. http://bitcoins.info/bitcoin.pdf. |
| [21] | ZAMFIR V, RUSH N, ASGAONKAR A, et al. Introducing the Minimal CBC Casper Family of Consensus Protocols. [EB/OL]. (2018-11-17) [2023-12-01]. https://github.com/cbc-casper/cbc-casper-paper/blob/master/cbc-casper-paper-draft.pdf. |
| [22] | CIVIT P, GILBERT S, GRAMOLI V, et al. As Easy As ABC: Optimal (A) Ccountable (B) Yzantine (C) Onsensus is Easy![J]. Journal of Parallel and Distributed Computing, 2023, 181: 560-570. |
| [23] | TANG Weizhao, SHENG Peiyao, ROY P, et al. Raft-Forensics: High Performance CFT Consensus with Accountability for Byzantine Faults[EB/OL]. (2023-11-02) [2023-12-01]. https://arxiv.org/abs/2305.09123. |
| [24] | ONGARO D, OUSTERHOUT J. In Search of an Understandable Consensus Algorithm[C]// USENIX. 2014 USENIX Annual Technical Conference (USENIX ATC 14). Renton: USENIX Association, 2014: 305-319. |
| [25] | TOBIAS D. Byzantine Fault-Tolerant State-Machine Replication from a Systems Perspective[J]. ACM Computing Surveys, 2021, 54(1): 1-38. |
| [1] | 邵震哲, 蒋佳佳, 赵佳豪, 张玉书. 面向跨链的改进加权拜占庭容错算法[J]. 信息网络安全, 2023, 23(8): 109-120. |
| [2] | 王健, 张蕴嘉, 刘吉强, 陈志浩. 基于区块链的司法数据管理及电子证据存储机制[J]. 信息网络安全, 2022, 22(2): 21-31. |
| [3] | 陈凯杰, 熊焰, 黄文超, 武建双. 一种基于拜占庭容错的PoS共识协议形式化分析方法[J]. 信息网络安全, 2021, 21(8): 35-42. |
| [4] | 张淑清, 蔡志文. 云数据下基于可问责属性即可撤销的加密方案[J]. 信息网络安全, 2021, 21(12): 70-77. |
| [5] | 郑敏, 王虹, 刘洪, 谭冲. 区块链共识算法研究综述[J]. 信息网络安全, 2019, 19(7): 8-24. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||