信息网络安全 ›› 2026, Vol. 26 ›› Issue (1): 150-167.doi: 10.3969/j.issn.1671-1122.2026.01.013
融合GAT与可解释DQN的SQL注入攻击检测模型
邓钰洋1, 芦天亮1( ), 李知皓1, 孟昊阳1, 马远声2
), 李知皓1, 孟昊阳1, 马远声2
- 1.中国人民公安大学信息网络安全学院,北京 100038
2.北京市公安局网络安全保卫总队,北京 102611
-
收稿日期:2025-08-25出版日期:2026-01-10发布日期:2026-02-13 -
通讯作者:芦天亮lutianliang@ppsuc.edu.cn -
作者简介:邓钰洋(2003—),男,北京,硕士研究生,CCF会员,主要研究方向为网络安全|芦天亮(1985—),男,北京,教授,博士,主要研究方向为网络安全|李知皓(2003—),男,浙江,硕士研究生,主要研究方向为数据警务|孟昊阳(2003—),男,河北,硕士研究生,主要研究方向为网络安全|马远声(1988—),男,北京,本科,主要研究方向为电子数据取证
A SQL Injection Attack Detection Model Integrating GAT and Interpretable DQN
DENG Yuyang1, LU Tianliang1( ), LI Zhihao1, MENG Haoyang1, MA Yuansheng2
), LI Zhihao1, MENG Haoyang1, MA Yuansheng2
- 1. School of Information Network Security, People’s Public Security University of China, Beijing 100038, China
2. Cyber Security Corps of the Beijing Municipal Public Security Bureau, Beijing 102611, China
-
Received:2025-08-25Online:2026-01-10Published:2026-02-13
摘要:
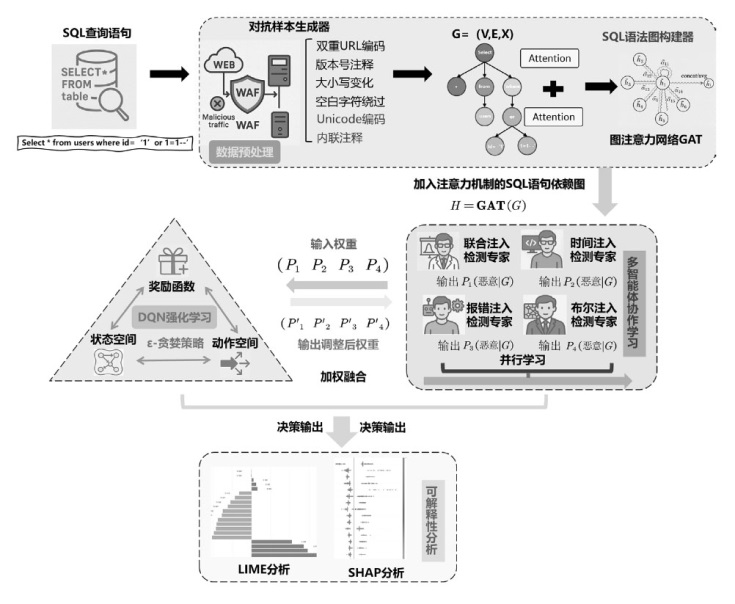
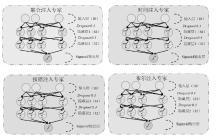
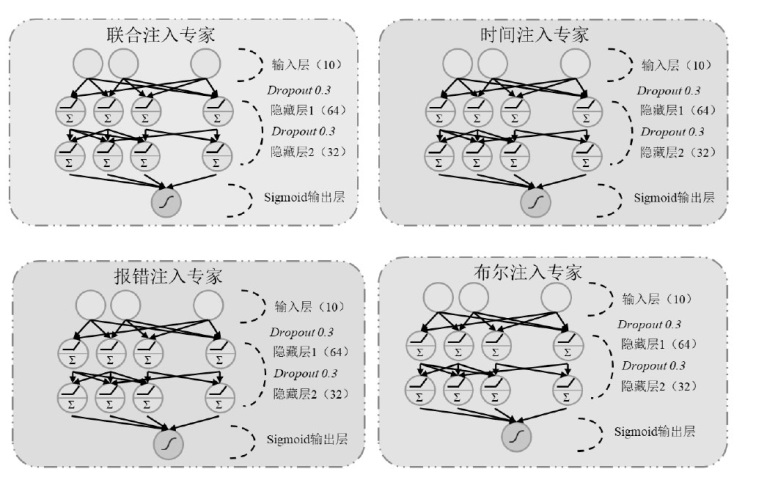
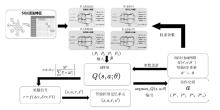
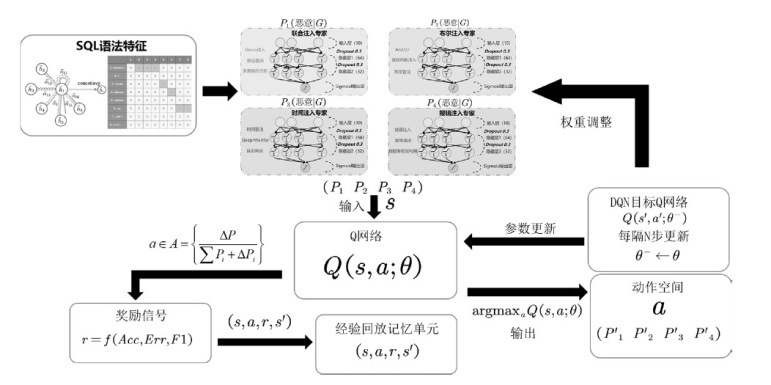
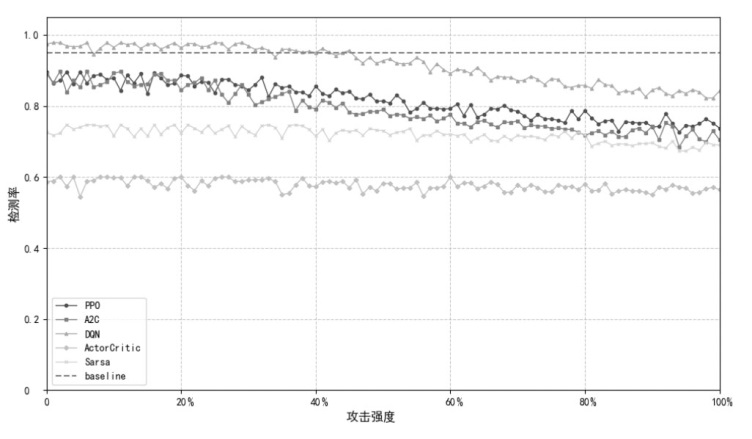
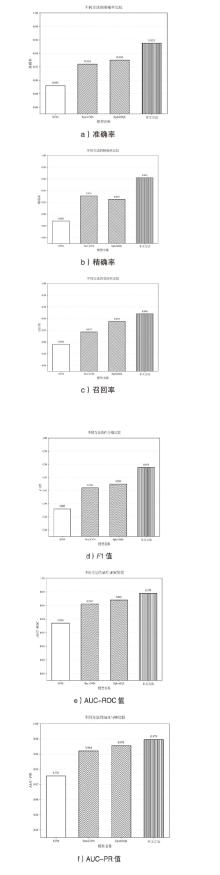
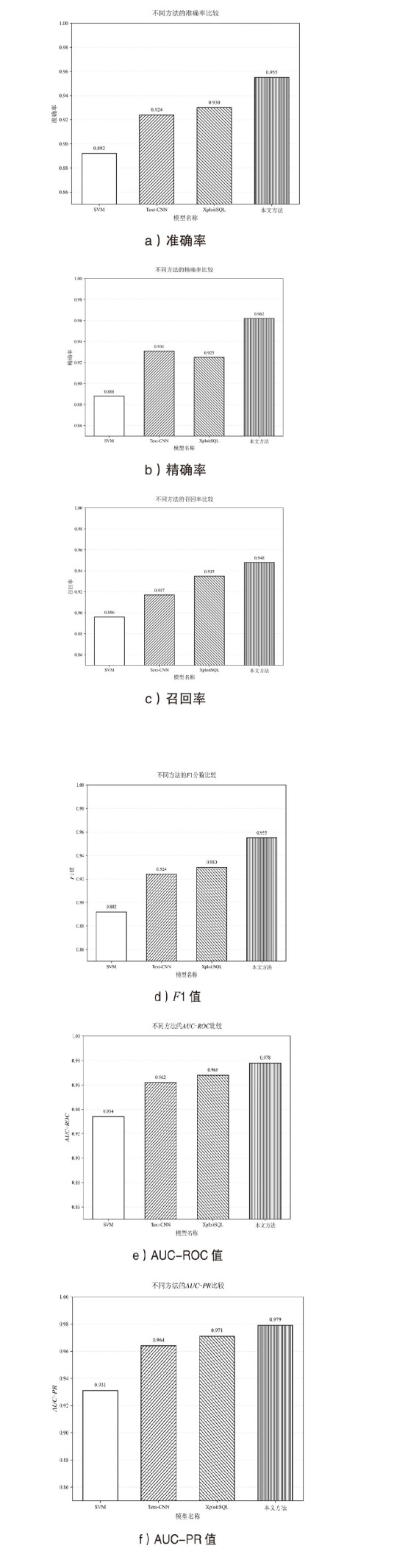
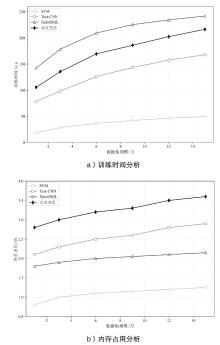
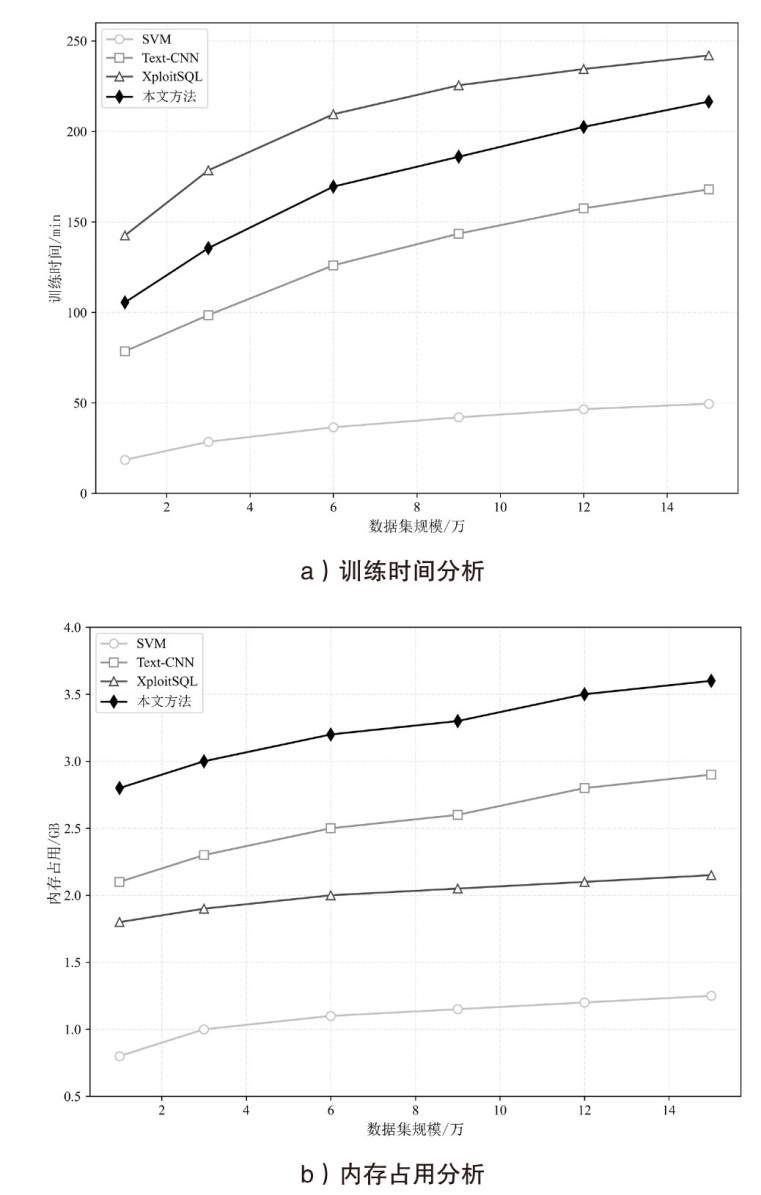
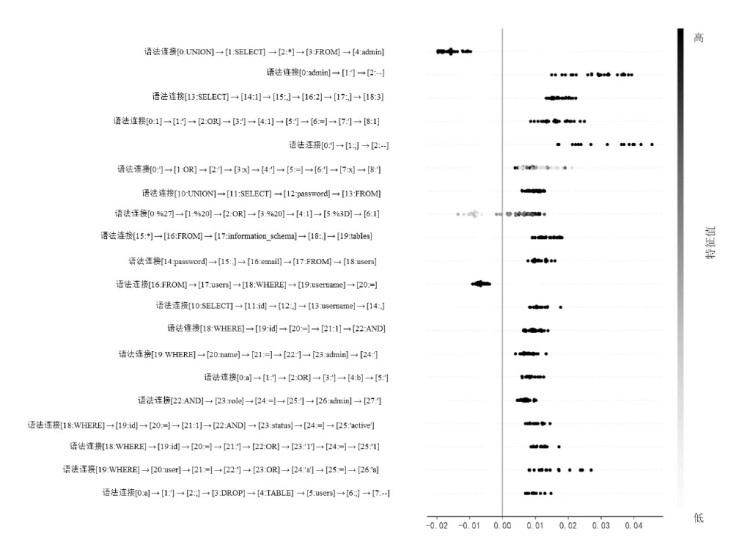
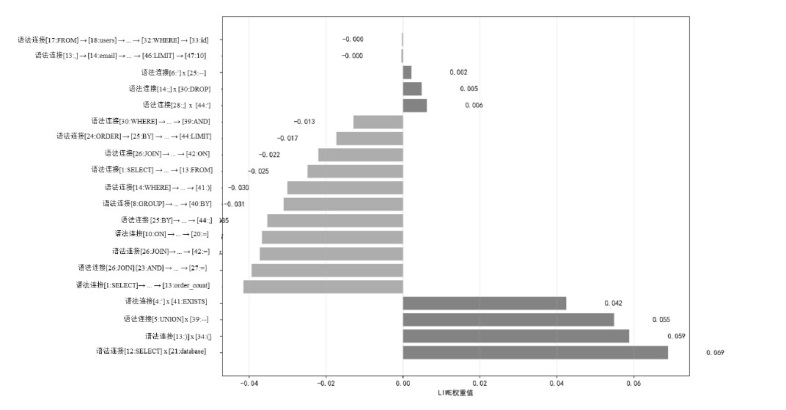
随着Web应用的持续演进及数据库驱动系统的广泛部署,SQL注入攻击作为一种高度隐蔽且破坏力强的网络攻击方式,依然是当前Web安全防护的重要研究对象。针对SQL注入语句结构复杂、语义多样以及攻击样本稀缺等问题,文章提出一种融合图结构建模与强化学习机制的SQL注入攻击检测方法。该方法将SQL语句建模为图结构,通过改进的图注意力网络GAT融合节点与边的语法特征,并构建了包含4个专门化检测专家的多智能体强化学习框架,实现动态集成决策。同时,该检测方法设计了针对SQL注入攻击混淆特点的对抗样本生成模块,增强了模型对复杂变形攻击的识别能力。此外,结合LIME与SHAP方法对检测结果进行可解释性分析,增强系统的透明度与实用性。实验结果表明,该方法在保持较低计算资源消耗的前提下,有效缓解了样本不均衡与攻击模式多样化引起的检测偏差问题。该方法在综合性SQL注入数据集上的检测准确率达0.955,AUC值为0.978,显著优于现有基线方法,为SQL注入攻击的智能化检测提供了有效解决方案。
中图分类号:
引用本文
邓钰洋, 芦天亮, 李知皓, 孟昊阳, 马远声. 融合GAT与可解释DQN的SQL注入攻击检测模型[J]. 信息网络安全, 2026, 26(1): 150-167.
DENG Yuyang, LU Tianliang, LI Zhihao, MENG Haoyang, MA Yuansheng. A SQL Injection Attack Detection Model Integrating GAT and Interpretable DQN[J]. Netinfo Security, 2026, 26(1): 150-167.
表1
SQL注入基本类型表
| 注入类型 | 描述说明 | 攻击载荷示例 |
|---|---|---|
| 恒真式注入 | 构造永远为真的逻辑条件,绕过WHERE子句的限制 | ?username=admin’ or ‘1’=’1 |
| 联合查询注入 | 通过UNION连接额外查询,窃取其他表的数据 | ?id=999 union select null,database(),version() |
| 报错注入 | 故意触发数据库报错,从错误信息中提取数据 | ?name=1’ and extractvalue(1,concat(0x7e,@@version))—+ |
| 布尔盲注 | 根据页面返回的不同状态判断条件真假,逐字符猜解数据 | ?id=1 and substring(database(),1,1)=’t’ |
| 堆叠查询注入 | 一次执行多条SQL语句,可执行删除、修改等危险操作 | ?id=1; drop table users;— |
| 时间盲注 | 通过延时函数控制响应时间,判断条件是否成立 | ?id=1’ and if(length(database())>5, sleep(3),0)—+ |
| 包含函数 | 使用数据库函数获取系统信息或执行计算 | ?id=1 and concat(user(),0x7e,database()) like ‘%root%’ |
| 包含关键词 | 注入SQL保留字来改变查询逻辑 | ?search=phone’ order by price desc— |
| 包含子查询 | 嵌套SELECT语句获取其他表数据或进行复杂判断 | ?id=1 and exists(select * from admin where password like ‘a%’) |
表3
不同模型超参数组合
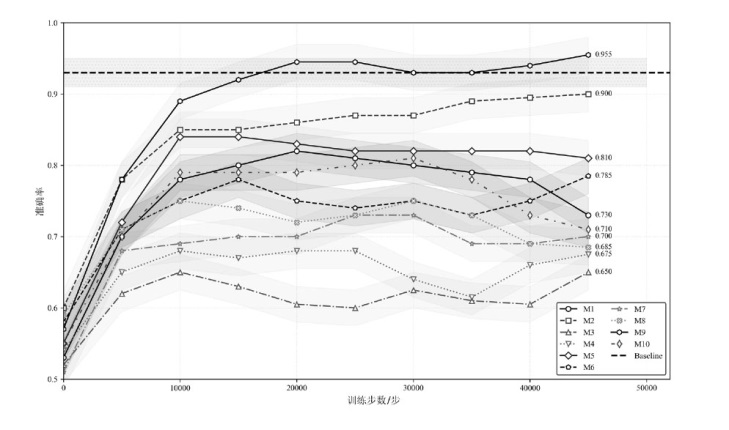
| 模型编号 | 学习率 | 批量大小 | 隐藏层维度 | 折扣 因子γ | ε贪心策略衰减率 | 目标网络更新频率 | 最终 准确率 |
|---|---|---|---|---|---|---|---|
| M1 | 1?10-4 | 64 | 128 | 0.99 | 0.997 | 1000 | 0.730 |
| M2 | 3?10-4 | 128 | 256 | 0.99 | 0.999 | 1000 | 0.900 |
| M3 | 1?10-3 | 32 | 64 | 0.95 | 0.995 | 500 | 0.650 |
| M4 | 3?10-4 | 64 | 256 | 0.99 | 0.997 | 2000 | 0.900 |
| M5 | 1?10-4 | 128 | 128 | 0.95 | 0.999 | 1000 | 0.800 |
| M6 | 3?10-4 | 32 | 256 | 0.99 | 0.999 | 500 | 0.785 |
| M7 | 1?10-4 | 64 | 64 | 0.99 | 0.997 | 2000 | 0.685 |
| M8 | 1?10-3 | 128 | 128 | 0.95 | 0.997 | 1000 | 0.710 |
| M9 | 3?10-4 | 64 | 256 | 0.99 | 0.999 | 1000 | 0.955 |
| M10 | 1?10-4 | 32 | 128 | 0.99 | 0.995 | 2000 | 0.710 |
表4
3个数据集超参数调优最优结果
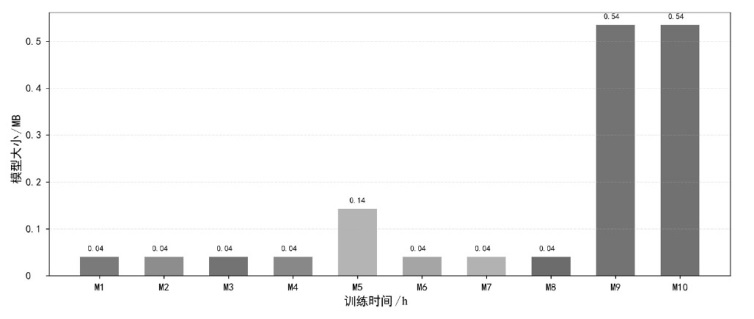
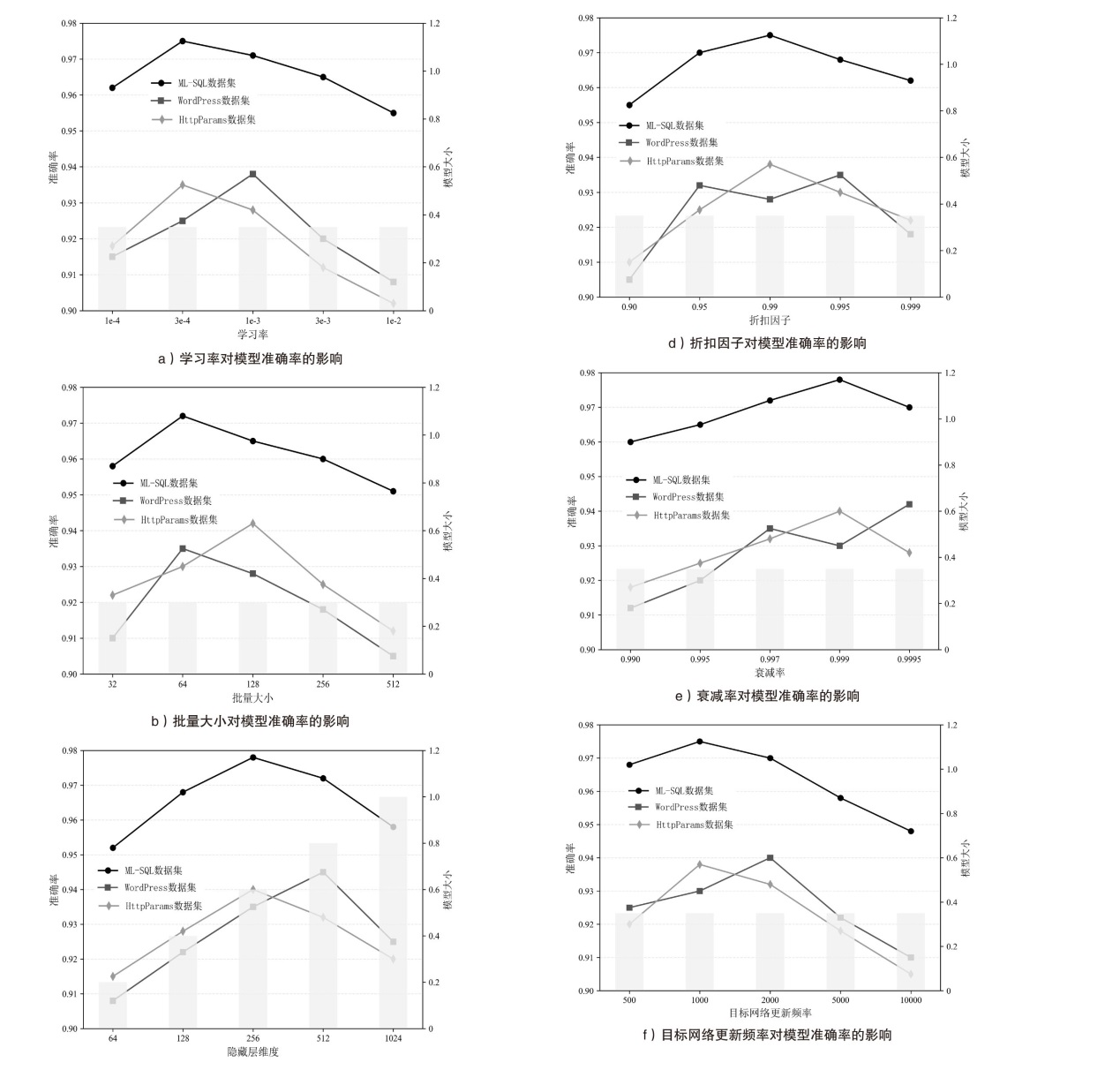
| 超参数 类别 | 参数值范围 | ML-SQL 数据集 | WordPress 数据集 | HttpParams 数据集 | 模型大小 /MB |
|---|---|---|---|---|---|
| 学习率 | 0.0001~0.01 | 0.0003 | 0.001 | 0.004 | 0.42 |
| 批量大小 | 32 ~ 512 | 128 | 64 | 64 | 0.42 |
| 隐藏层 维度 | 64 ~ 1024 | 256 | 512 | 256 | 0.18~1.15 |
| 折扣 因子γ | 0.900 ~ 0.999 | 0.990 | 0.995 | 0.990 | 0.42 |
| ε衰减率 | 0.990 ~ 0.9995 | 0.999 | 0.9995 | 0.999 | 0.42 |
| 目标网络更新频率 | 500 ~ 10000 | 1000 | 2000 | 1000 | 0.42 |
| [1] |
GUI Zhiwen, WANG Enze, DENG Binbin, et al. SqliGPT: Evaluating and Utilizing Large Language Models for Automated SQL Injection Black-Box Detection[J]. Applied Sciences, 2024, 14(16): 1-18.
doi: 10.3390/app14010001 URL |
| [2] | ZULU J, HAN Bonian, ALSMADI I, et al. Enhancing Machine Learning Based SQL Injection Detection Using Contextualized Word Embedding[C]// ACM. 2024 ACM Southeast Conference (ACMSE 2024). New York: ACM, 2024: 211-216. |
| [3] | YANG Guanyan, WANG F, GU Youzong, et al. TPSQLi: Test Prioritization for SQL Injection Vulnerability Detection in Web Applications[EB/OL]. (2024-09-17)[2025-06-14]. https://www.mdpi.com/2076-3417/14/18/8365. |
| [4] |
KAKISIM A G. A Deep Learning Approach Based on Multi-View Consensus for SQL Injection Detection[J]. International Journal of Information Security, 2024, 23(2): 1541-1556.
doi: 10.1007/s10207-023-00791-y |
| [5] | LI Yingbo, ZHANG Bin. Filtration Method of SQL Injection Attacks Based on LD Algorithm[J]. Application Research of Computers, 2020, 37(9): 2793-2796. |
| 李应博, 张斌. 基于LD算法的SQL注入攻击过滤方法研究[J]. 计算机应用研究, 2020, 37(9): 2793-2796. | |
| [6] | HUANG Kaijie, WANG Jian, CHEN Jiongyi. A Large Language Model Based SQL Injection Attack Detection Method[J]. Netinfo Security, 2023, 23(11): 84-93. |
| 黄恺杰, 王剑, 陈炯峄. 一种基于大语言模型的SQL注入攻击检测方法[J]. 信息网络安全, 2023, 23(11): 84-93. | |
| [7] | FATHI K S, BARAKAT S, REZK A. An Effective SQL Injection Detection Model Using LSTM for Imbalanced Datasets[EB/OL]. (2025-06)[2025-06-14]. https://www.sciencedirect.com/science/article/pii/S016740482500080X. |
| [8] | WANG Qingyu, WANG Hairui, ZHU Guifu, et al. Study on SQL Injection Detection Based on FlexUDA Model[J]. Computer Science, 2023, 50(S1): 797-802. |
| 王清宇, 王海瑞, 朱贵富, 等. 基于FlexUDA模型的SQL注入检测研究[J]. 计算机科学, 2023, 50(S1): 797-802. | |
| [9] | KONG Deguang, JIANG Chaohui, GUO Chun. SQL Injection Attack Detection Method Based on SimHash[J]. Application Research of Computers, 2020, 37(7): 2117-2122. |
| 孔德广, 蒋朝惠, 郭春. 基于SimHash算法的SQL注入攻击检测方法[J]. 计算机应用研究, 2020, 37(7): 2117-2122. | |
| [10] | ZHU Jingwen, XU Jing, CHEN Liang, et al. SQL Injection Attack Detection Based on Hidden Markov Model[J]. Computer Applications and Software, 2023, 40(2): 331-338, 344. |
| 朱静雯, 许静, 陈亮, 等. 基于隐马尔可夫模型的SQL注入攻击行为检测[J]. 计算机应用与软件, 2023, 40(2): 331-338,344. | |
| [11] |
LIU Jihui, HE Chengwan. Online Detection of SQL Injection Attacks Based on ECA Rules and Dynamic Taint Analysis[J]. Journal of Computer Applications, 2023, 43(5): 1534-1542.
doi: 10.11772/j.issn.1001-9081.2022040636 |
|
刘吉会, 何成万. 基于ECA规则和动态污点分析的SQL注入攻击在线检测[J]. 计算机应用, 2023, 43(5): 1534-1542.
doi: 10.11772/j.issn.1001-9081.2022040636 |
|
| [12] | HAN Chenwang, LIN Hui, HUANG Chuan. Research on the SQL Injection Filtering Based on SQL Syntax Tree[J]. Chinese Journal of Network and Information Security, 2016, 2(11): 70-77. |
| 韩宸望, 林晖, 黄川. 基于SQL语法树的SQL注入过滤方法研究[J]. 网络与信息安全学报, 2016, 2(11): 70-77. | |
| [13] |
ARASTEH B, AGHAEI B, FARZAD B, et al. Detecting SQL Injection Attacks by Binary Gray Wolf Optimizer and Machine Learning Algorithms[J]. Neural Computing and Applications, 2024, 36(12): 6771-6792.
doi: 10.1007/s00521-024-09429-z |
| [14] | LE T T H, HWANG Y, CHOI C, et al. Enhancing Structured Query Language Injection Detection with Trustworthy Ensemble Learning and Boosting Models Using Local Explanation Techniques[EB/OL]. (2024-11-06)[2025-06-14]. https://www.mdpi.com/2079-9292/13/22/4350. |
| [15] | ARASTEH B, BOUYER A, SEFATI S S, et al. Effective SQL Injection Detection: A Fusion of Binary Olympiad Optimizer and Classification Algorithm[EB/OL]. (2024-09-19)[2025-06-14]. https://www.mdpi.com/2227-7390/12/18/2917. |
| [16] | LIU Yixian, DAI Yupeng. Deep Learning in Cybersecurity: A Hybrid BERT-LSTM Network for SQL Injection Attack Detection[EB/OL]. [2025-06-14]. https://doi.org/10.1049/2024/5565950. |
| [17] | BISHT P, MADHUSUDAN P, VENKATAKRISHNAN V N. CANDID: Dynamic Candidate Evaluations for Automatic Prevention of SQL Injection Attacks[J]. ACM Transactions on Information and System Security (TISSEC), 2010, 13(2): 1-39. |
| [18] | ZHAO Wei, YOU Junling, CHEN Qinghui. SQL Injection Attack Detection Based on Text-CNN[C]// ACM. 2024 International Conference on Generative Artificial Intelligence and Information Security (GAIIS 2024). New York: ACM, 2024: 292-296. |
| [19] | YANG Wanrong, ACUTO A, ZHOU Yihang, et al. A Survey for Deep Reinforcement Learning Based Network Intrusion Detection[EB/OL]. (2024-09-25)[2025-06-14]. https://arxiv.org/abs/2410.07612. |
| [20] | ERDODI L, SOMMERVOLL A A, ZENNARO F M. Simulating SQL Injection Vulnerability Exploitation Using Q-Learning Reinforcement Learning Agents[EB/OL]. [2025-06-14]. https://doi.org/10.1016/j.jisa.2021.102903. |
| [21] | SHETH T, ANAP J, PATEL H, et al. Detection of SQL Injection Attacks by Giving Apriori to Q-Learning Agents[C]// IEEE. 2023 IEEE IAS Global Conference on Emerging Technologies (GlobConET 2023). New York: IEEE, 2023: 1-6. |
| [22] | DEL VERME M, SOMMERVOLL A A, ERDODI L, et al. SQL Injections and Reinforcement Learning: An Empirical Evaluation of the Role of Action Structure[C]// Springer. Secure IT Systems:26th Nordic Conference, NordSec 2021. Heidelberg: Springer, 2021: 95-113. |
| [23] | LEUNG D, TSAI O, HASHEMI K, et al. XploitSQL: Advancing Adversarial SQL Injection Attack Generation with Language Models and Reinforcement Learning[C]// ACM. The 33rd ACM International Conference on Information and Knowledge Management (CIKM ’24). New York: ACM, 2024: 4653-4660. |
| [24] | GUAN Yuting, HE Junjiang, LI Tao, et al. SSQLi: A Black-Box Adversarial Attack Method for SQL Injection Based on Reinforcement Learning[EB/OL]. (2023-03-30)[2025-08-18]. https://doi.org/10.3390/fi15040133. |
| [25] | SETHI K, MADHAV Y V, KUMAR R, et al. Attention Based Multi-Agent Intrusion Detection Systems Using Reinforcement Learning[EB/OL]. [2025-10-18]. https://doi.org/10.1016/j.jisa.2021.102923. |
| [26] |
DONG Shi, XIA Yuanjun, PENG Tao. Network Abnormal Traffic Detection Model Based on Semi-Supervised Deep Reinforcement Learning[J]. IEEE Transactions on Network and Service Management, 2021, 18(4): 4197-4212.
doi: 10.1109/TNSM.2021.3120804 URL |
| [27] | SETHI K, KUMAR R, MOHANTY D, et al. Robust Adaptive Cloud Intrusion Detection System Using Advanced Deep Reinforcement Learning[C]// Springer. Security, Privacy, and Applied Cryptography Engineering:The 10th International Conference, SPACE 2020. Heidelberg: Springer, 2020: 66-85. |
| [28] |
LOPEZ-MARTIN M, SANCHEZ-ESGUEVILLAS A, ARRIBAS J I, et al. Network Intrusion Detection Based on Extended RBF Neural Network with Offline Reinforcement Learning[J]. IEEE Access, 2021, 9: 153153-153170.
doi: 10.1109/ACCESS.2021.3127689 URL |
| [29] |
SETHI K, KUMAR R, PATRA P K. A Context-Aware Robust Intrusion Detection System: A Reinforcement Learning-Based Approach[J]. International Journal of Information Security, 2020, 19: 657-678.
doi: 10.1007/s10207-019-00482-7 |
| [30] | HOLLAND C A. ML-SQL-Injection-Detector: Research for Determining the Best Classifier for Detecting SQL Injections[EB/OL]. (2019-12-04)[2025-06-03]. https://github.com/ChrisAHolland/ML-SQL-Injection-Detector. |
| [31] | LIU Xin, HUANG Yuanyuan, WANG Tianyi, et al. SQLStateGuard: Statement-Level SQL Injection Defense Based on Learning-Driven Middleware[C]// ACM. The 2024 ACM Symposium on Cloud Computing (SoCC 2024). New York: ACM, 2024: 69-82. |
| [32] | Morzeux. HttpParamsDataset: Dataset Contains Several Benign and Attacks Samples which Can be Used as Values in HTTP Protocol[EB/OL]. [2025-06-03]. https://github.com/Morzeux/HttpParamsDataset. |
| [33] | ALGHAWAZI M, ALGHAZZAWI D, ALARIFI S. Deep Learning Architecture for Detecting SQL Injection Attacks Based on RNN Autoencoder Model[EB/OL]. (2023-07-26)[2025-06-14]. https://doi.org/10.3390/math11153286. |
| [34] | SCHULMAN J, WOLSKI F, DHARIWAL P, et al. Proximal Policy Optimization Algorithms[EB/OL]. (2017-07-20)[2025-06-14]. https://arxiv.org/abs/1707.06347. |
| [35] |
DU Xixi, CHENG Hua, FANG Yiquan. Reinforcement Automatic Summarization Model Based on Advantage Actor-Critic Algorithm[J]. Journal of Computer Applications, 2021, 41(3): 699-705
doi: 10.11772/j.issn.1001-9081.2020060837 |
|
杜嘻嘻, 程华, 房一泉. 基于优势演员-评论家算法的强化自动摘要模型[J]. 计算机应用, 2021, 41(3): 699-705.
doi: 10.11772/j.issn.1001-9081.2020060837 |
|
| [36] | RUMMERY G A, NIRANJAN M. On-Line Q-Learning Using Connectionist Systems[R]. Cambridge: Cambridge University Engineering Department, 1994. |
| [37] |
KONDA V R, TSITSIKLIS J N. On Actor-Critic Algorithms[J]. SIAM Journal on Control and Optimization, 2003, 42(4): 1143-1166.
doi: 10.1137/S0363012901385691 URL |
| [38] | CHINTHALAPUDI S S. Detecting and Mitigating SQL Injection in. NET Applications Using AI-Based Anomaly Detection[J]. International Journal of Innovative Science and Research Technology, 2025, 10(3): 2582-2595. |
| [39] | DE-LA-RICA-ESCUDERO A, GARRIDO-MERCHAN E C, CORONADO-VACA M. Explainable Post Hoc Portfolio Management Financial Policy of a Deep Reinforcement Learning Agent[EB/OL]. (2025-01-16)[2025-08-19]. https://doi.org/10.1371/journal.pone.0315528. |
| [1] | 汪正阳, 刘晓露, 沈卓炜, 韦梦立. 多智能体系统安全防护技术研究综述[J]. 信息网络安全, 2025, 25(7): 1138-1152. |
| [2] | 耿致远, 许泽轩, 张恒巍. 基于随机博弈和DQN算法的云原生移动目标防御决策方法[J]. 信息网络安全, 2025, 25(6): 967-976. |
| [3] | 刘晨飞, 万良. 基于时空图神经网络的CAN总线入侵检测方法[J]. 信息网络安全, 2025, 25(3): 478-493. |
| [4] | 姚昌华, 许浩, 付澍, 刘鑫. 基于边界点过滤的多智能体快速协同探索算法[J]. 信息网络安全, 2023, 23(11): 58-68. |
| [5] | 沈传鑫, 王永杰, 熊鑫立. 基于图注意力网络的DNS隐蔽信道检测[J]. 信息网络安全, 2023, 23(1): 73-83. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||