信息网络安全 ›› 2025, Vol. 25 ›› Issue (12): 1914-1926.doi: 10.3969/j.issn.1671-1122.2025.12.007
基于图变分自编码器的多模态特征融合加密流量分类模型
- 中国人民武装警察部队工程大学密码工程学院,西安 710086
-
收稿日期:2025-05-12出版日期:2025-12-10发布日期:2026-01-06 -
通讯作者:韩益亮 E-mail:hanyil@163.com -
作者简介:韩益亮(1977—),男,甘肃,教授,博士,主要研究方向为公钥密码学、深度学习和隐私保护|彭一轩(2001—),男,山西,硕士研究生,主要研究方向为加密流量分析|吴旭光(1986—),男,河南,副教授,博士,主要研究方向为密码学和信息安全|李鱼(1995—),男,重庆,讲师,博士,主要研究方向为密码学 -
基金资助:陕西省自然科学基金(2025JC-YBMS-664)
Multimodal Feature Fusion Encrypted Traffic Classification Model Based on Graph Variational Auto-Encoder
HAN Yiliang( ), PENG Yixuan, WU Xuguang, LI Yu
), PENG Yixuan, WU Xuguang, LI Yu
- College of Cryptographic Engineering, Engineering University of PAP, Xi’an 710086, China
-
Received:2025-05-12Online:2025-12-10Published:2026-01-06 -
Contact:HAN Yiliang E-mail:hanyil@163.com
摘要:
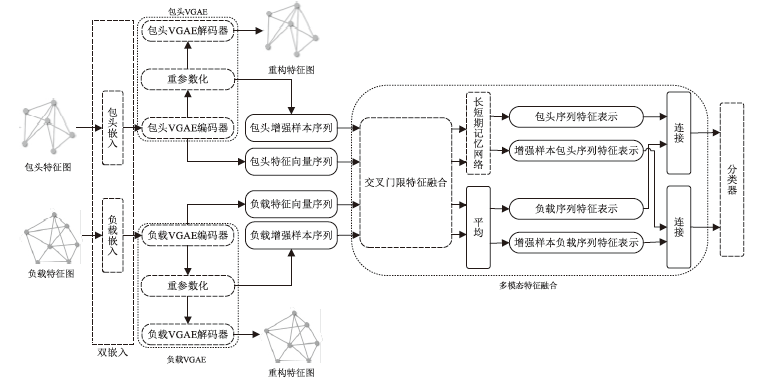
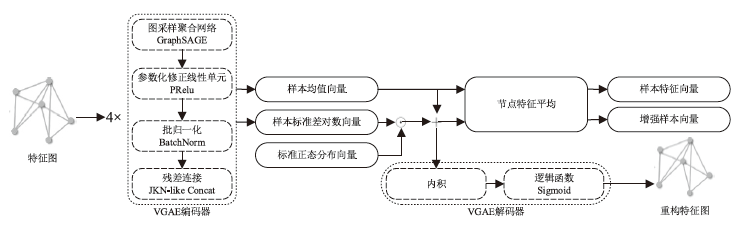
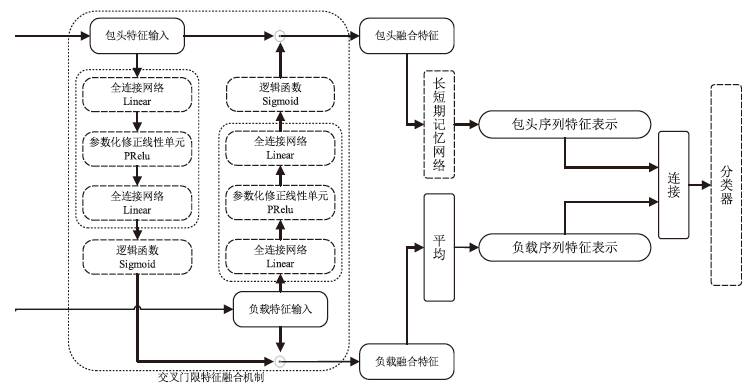
随着流量加密技术的广泛应用与不断演进,如何提升加密流量分类的精度,成为保障网络安全与高效管理的关键技术挑战。现有的加密流量分类方法采用相同的机制提取包头和负载特征,无法充分利用包头和负载中具有不同特性的有效信息,且忽视了密文的随机特征,导致分类精度遇到性能瓶颈。文章提出一种基于图变分自编码器的多模态特征融合加密流量分类模型(MFF-VGAE),该模型运用多模态特征融合技术分别提取并融合包头和负载中的有效信息。此外,该模型使用图变分自编码器,将样本特征映射到服从正态分布的随机空间,在学习密文数据概率分布的同时生成增强样本。通过训练,该模型在提升分类精度与鲁棒性的同时,降低了计算量。实验结果表明,文章所提出的模型在ISCX VPN-nonVPN和ISCX Tor-nonTor数据集上,相较于当前主流基线模型表现更优,且模型计算量相较于使用类似结构的TFE-GNN下降了9.1%。
中图分类号:
引用本文
韩益亮, 彭一轩, 吴旭光, 李鱼. 基于图变分自编码器的多模态特征融合加密流量分类模型[J]. 信息网络安全, 2025, 25(12): 1914-1926.
HAN Yiliang, PENG Yixuan, WU Xuguang, LI Yu. Multimodal Feature Fusion Encrypted Traffic Classification Model Based on Graph Variational Auto-Encoder[J]. Netinfo Security, 2025, 25(12): 1914-1926.
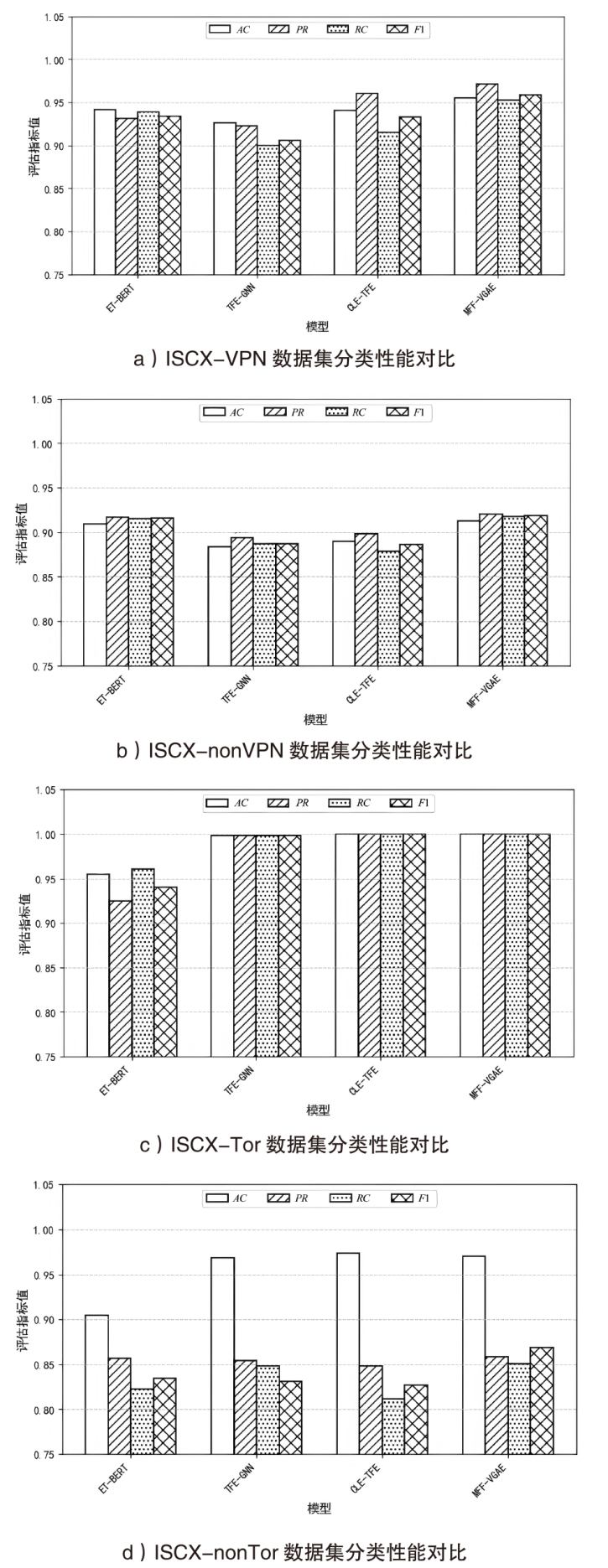
表1
在ISCX VPN-nonVPN和ISCX Tor-nonTor数据集上的性能对比
| 数据集 | vpn | nonvpn | tor | nontor | ||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 模型 | ACC | PR | RC | F1 | ACC | PR | RC | F1 | ACC | PR | RC | F1 | ACC | PR | RC | F1 |
| AppScanner[ | 0.8971 | 0.8761 | 0.8897 | 0.8804 | 0.7291 | 0.7309 | 0.718 | 0.7201 | 0.7403 | 0.6489 | 0.5902 | 0.6023 | 0.9333 | 0.8515 | 0.832 | 0.8453 |
| K-FP | 0.8848 | 0.8885 | 0.8883 | 0.8882 | 0.7530 | 0.7457 | 0.7333 | 0.7366 | 0.7874 | 0.7520 | 0.6312 | 0.6416 | 0.8722 | 0.8434 | 0.7773 | 0.8148 |
| FlowPrint | 0.8570 | 0.7483 | 0.7949 | 0.7598 | 0.6964 | 0.7093 | 0.7330 | 0.7151 | 0.2465 | 0.0365 | 0.1315 | 0.0549 | 0.5203 | 0.7550 | 0.6034 | 0.6113 |
| CUMUL | 0.7586 | 0.7456 | 0.7777 | 0.7569 | 0.6144 | 0.5898 | 0.5928 | 0.5854 | 0.6678 | 0.5341 | 0.4891 | 0.4989 | 0.8497 | 0.8035 | 0.7285 | 0.7519 |
| GRAIN[ | 0.7945 | 0.7893 | 0.7925 | 0.7843 | 0.6917 | 0.6782 | 0.6914 | 0.6817 | 0.6786 | 0.5125 | 0.5218 | 0.5106 | 0.7932 | 0.6751 | 0.6652 | 0.6650 |
| FAAR[ | 0.8286 | 0.8147 | 0.8327 | 0.8214 | 0.7384 | 0.7519 | 0.7131 | 0.7262 | 0.6950 | 0.5894 | 0.4855 | 0.4793 | 0.9034 | 0.8184 | 0.7686 | 0.7890 |
| ETC-PS[ | 0.8995 | 0.8909 | 0.9043 | 0.8957 | 0.7274 | 0.7415 | 0.7134 | 0.7209 | 0.7430 | 0.6755 | 0.5873 | 0.5977 | 0.9350 | 0.8580 | 0.8296 | 0.8471 |
| FS-Net[ | 0.9331 | 0.9296 | 0.9244 | 0.9267 | 0.7681 | 0.7740 | 0.7589 | 0.761 | 0.8337 | 0.7538 | 0.7248 | 0.7293 | 0.9426 | 0.8516 | 0.8402 | 0.8433 |
| DF[ | 0.7909 | 0.7696 | 0.8049 | 0.7818 | 0.6812 | 0.6927 | 0.6787 | 0.6771 | 0.6548 | 0.4837 | 0.4801 | 0.4753 | 0.8555 | 0.7990 | 0.7402 | 0.7577 |
| EDC[ | 0.7846 | 0.7757 | 0.8118 | 0.7898 | 0.6885 | 0.7068 | 0.6915 | 0.6893 | 0.6311 | 0.4891 | 0.4439 | 0.4415 | 0.8799 | 0.8101 | 0.7518 | 0.7558 |
| FFB[ | 0.8278 | 0.8688 | 0.8123 | 0.8309 | 0.7097 | 0.7351 | 0.7022 | 0.7127 | 0.6315 | 0.4842 | 0.5175 | 0.4924 | 0.8859 | 0.7450 | 0.7335 | 0.7335 |
| MVML[ | 0.6463 | 0.7203 | 0.6170 | 0.6123 | 0.5089 | 0.5714 | 0.4670 | 0.4769 | 0.6310 | 0.3881 | 0.4071 | 0.3719 | 0.7284 | 0.5537 | 0.5561 | 0.5506 |
| ET-BERT[ | 0.9411 | 0.9315 | 0.9386 | 0.9342 | 0.9091 | 0.9169 | 0.9153 | 0.9159 | 0.9547 | 0.9246 | 0.9610 | 0.9401 | 0.9040 | 0.8571 | 0.8228 | 0.8343 |
| GraphDApp[ | 0.6535 | 0.5712 | 0.6147 | 0.5784 | 0.4386 | 0.4121 | 0.3538 | 0.3505 | 0.4212 | 0.2483 | 0.2435 | 0.2207 | 0.699 | 0.5501 | 0.5452 | 0.5406 |
| ECD-GNN | 0.1178 | 0.0252 | 0.1734 | 0.040 | 0.0599 | 0.0094 | 0.1660 | 0.0183 | 0.062 | 0.012 | 0.1299 | 0.0184 | 0.9093 | 0.8030 | 0.8183 | 0.7992 |
| TFE-GNN[ | 0.9261 | 0.9229 | 0.8995 | 0.9059 | 0.8836 | 0.8939 | 0.8871 | 0.8869 | 0.9979 | 0.9980 | 0.9980 | 0.9980 | 0.9682 | 0.8544 | 0.8482 | 0.8307 |
| CLE-TFE | 0.9405 | 0.9604 | 0.9147 | 0.9326 | 0.8895 | 0.8978 | 0.8786 | 0.8862 | 0.9998 | 0.9998 | 0.9998 | 0.9998 | 0.9737 | 0.8483 | 0.8116 | 0.8269 |
| MFF-VGAE | 0.9554 | 0.9713 | 0.9525 | 0.9589 | 0.9126 | 0.9205 | 0.9179 | 0.9182 | 0.9996 | 0.9996 | 0.9996 | 0.9996 | 0.9702 | 0.8582 | 0.8504 | 0.8684 |
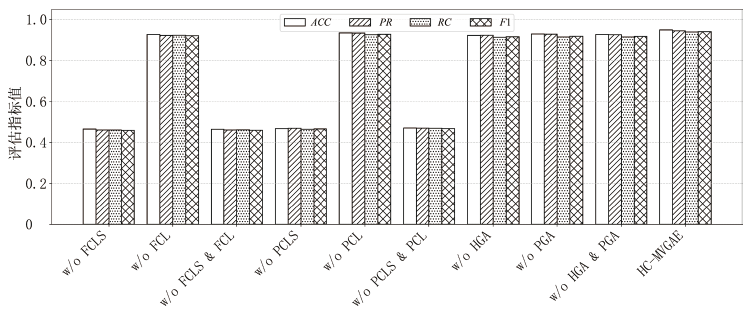
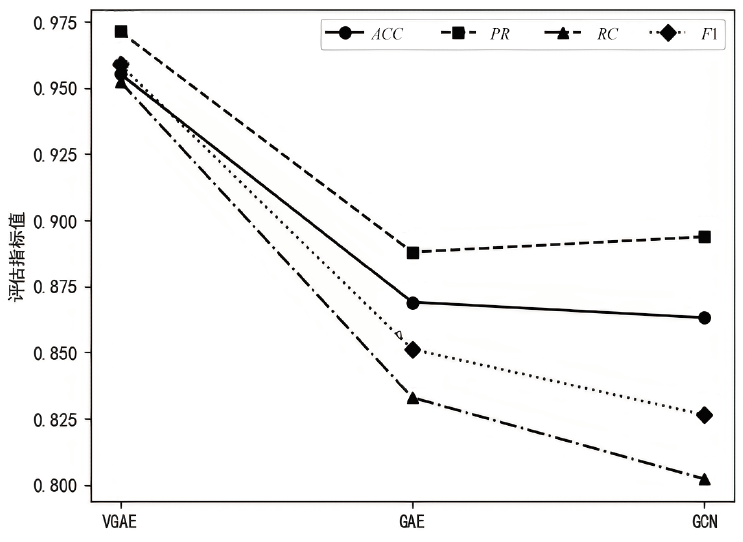
表2
消融实验结果
| Method | H | P | DUAL | JKN | CGFF | A&N | KL | ACC | PR | RC | F1 |
|---|---|---|---|---|---|---|---|---|---|---|---|
| w/o P | √ | × | × | √ | × | √ | √ | 0.8095 | 0.7794 | 0.7758 | 0.7723 |
| w/o H | × | √ | × | √ | × | √ | √ | 0.6190 | 0.5983 | 0.5805 | 0.5625 |
| w/o DUAL | √ | √ | × | √ | √ | √ | √ | 0.9286 | 0.9468 | 0.9208 | 0.9318 |
| w/o JKN | √ | √ | √ | × | √ | √ | √ | 0.8750 | 0.8748 | 0.8908 | 0.8744 |
| w/o CGFF | √ | √ | √ | √ | × | √ | √ | 0.8274 | 0.8421 | 0.8079 | 0.8091 |
| w/o A&N | √ | √ | √ | √ | √ | × | √ | 0.4643 | 0.3129 | 0.3234 | 0.2868 |
| w/ SUM | √ | √ | √ | √ | √ | √ | √ | 0.9048 | 0.9048 | 0.8941 | 0.8980 |
| w/ MAX | √ | √ | √ | √ | √ | √ | √ | 0.8452 | 0.8455 | 0.8197 | 0.8208 |
| MFF-VGAE (default) | √ | √ | √ | √ | √ | √ | √ | 0.9554 | 0.9713 | 0.9525 | 0.9589 |
表3
模型复杂度
| 模型 | FLOPs/M | 模型参数量/M |
|---|---|---|
| FS-Net[ | 1.0E+02 | 3.2E+00 |
| DF[ | 2.8E+00 | 9.3E-01 |
| EDC[ | 2.2E+01 | 2.2E+01 |
| FFB[ | 2.6E+02 | 1.7E+00 |
| MVML[ | 7.2E-04 | 3.7E-04 |
| ET-BERT[ | 1.1E+04 | 8.6E+01 |
| GraphDApp[ | 3.8E-02 | 1.1E-02 |
| ECD-GNN | 2.9E+01 | 1.4E+00 |
| TFE-GNN[ | 2.2E+03 | 4.4E+01 |
| CLE-TFE | 1.5E+03 | 4.5E+01 |
| MFF-VGAE | 2.0E+03 | 1.8E+00 |
| [1] | SHARMA R, DANGI S, MISHRA P. A Comprehensive Review on Encryption Based Open Source Cyber Security Tools[C]// IEEE. The 6th International Conference on Signal Processing, Computing and Control (ISPCC). New York: IEEE, 2021: 614-619. |
| [2] | RAMADHANI E. Anonymity Communication VPN and Tor: A Comparative Study[J]. Journal of Physics: Conference Series, 2018, 983(1): 60-69. |
| [3] |
ZHANG Yifan, KANG Bingyi, HOOI B, et al. Deep Long-Tailed Learning: A Survey[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2023, 45(9): 10795-10816.
doi: 10.1109/TPAMI.2023.3268118 URL |
| [4] | HAYES J, DANEZIS G. K-Fingerprinting: A Robust Scalable Website Fingerprinting Technique[C]// USENIX. The 25th USENIX Conference on Security Symposium. Berkeley: USENIX, 2016: 1187-1203. |
| [5] | ZAKI F, AFIFI F, ABD R S, et al. GRAIN: Granular Multi-Label Encrypted Traffic Classification Using Classifier Chain[J]. Computer Networks, 2022, 84-93. |
| [6] | LIN Xinjie, XIONG Gang, GOU Gaopeng, et al. ET-BERT: A Contextualized Datagram Representation with Pre-Training Transformers for Encrypted Traffic Classification[C]// ACM. The Web Conference 2022. New York: ACM, 2022: 633-642. |
| [7] | CAI Wei, LI Zhen, FU Peipei, et al. METC-MVAE: Mobile Encrypted Traffic Classification with Masked Variational Autoencoders[C]// IEEE. 2022 IEEE 24th International Conference on High Performance Computing & Communications, New York: IEEE, 2022: 1422-1429. |
| [8] | ZHANG Haozhen, YU Le, XIAO Xi, et al. TFE-GNN: A Temporal Fusion Encoder Using Graph Neural Networks for Fine-Grained Encrypted Traffic Classification[C]// ACM.The ACM Web Conference 2023. New York: ACM, 2023: 2066-2075. |
| [9] | PAPADOGIANNAKI E, IOANNIDIS S. A Survey on Encrypted Network Traffic Analysis Applications, Techniques, and Countermeasures[J]. ACM Computer Survey, 2021, 54(6): 123-135. |
| [10] | XU Shijie, GENG Guanggang, JIN Xiaobo, et al. Seeing Traffic Paths: Encrypted Traffic Classification with Path Signature Features[J]. IEEE Transactions on Information Forensics and Security, 2022, 166-181. |
| [11] |
WU Hua, WU Qiuyan, CHENG Guang, et al. SFIM: Identify User Behavior Based on Stable Features[J]. Peer-to-Peer Networking and Applications, 2021, 14(6): 3674-3687.
doi: 10.1007/s12083-021-01214-2 |
| [12] | SIRINAM P, IMANI M, JUAREZ M, et al. Deep Fingerprinting: Undermining Website Fingerprinting Defenses with Deep Learning[C]// ACM. The 2018 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2018: 1928-1943. |
| [13] | LIU Chang, HE Longtao, XIONG Gang, et al. FS-Net: A Flow Sequence Network for Encrypted Traffic Classification[C]// IEEE. 2019 IEEE Conference on Computer Communications. New York: IEEE, 2019: 1171-1179. |
| [14] | ZHANG Haozhen, XIAO Xi, YU Le, et al. One Train for Two Tasks: An Encrypted Traffic Classification Framework Using Supervised Contrastive Learning[EB/OL]. (2024-02-12)[2025-01-10]. https://arxiv.org/abs/2402.07501. |
| [15] | CHANG Sa, FENG Yong. Multi-Modal Deep Learning Blockchain Smart Contract Vulnerability Detection Method[J]. Journal of Chinese Computer Systems, 2025, 46(4): 958-965. |
| 常萨, 冯勇. 多模态深度学习的区块链智能合约漏洞检测方法[J]. 小型微型计算机系统, 2025, 46(4): 958-965. | |
| [16] | LASHKARI A H, GIL G D, MAMUN M S I, et al. Characterization of Tor Traffic Using Time Based Features[C]// SciTePress. International Conference on Information Systems Security and Privacy. Lisbon: SciTePress, 2017: 253-262. |
| [17] |
SHAPIRA T, SHAVITT Y. FlowPic: A Generic Representation for Encrypted Traffic Classification and Applications Identification[J]. IEEE Transactions on Network and Service Management, 2021, 18(2): 1218-1232.
doi: 10.1109/TNSM.2021.3071441 URL |
| [18] | TAYLOR V F, SPOLAOR R, CONTI M, et al. AppScanner: Automatic Fingerprinting of Smartphone Apps from Encrypted Network Traffic[C]// IEEE. Conference 2016 IEEE European Symposium on Security and Privacy (EuroS&P). New York: ACM, 2016: 439-454. |
| [19] | PANCHENKO A, LANZE F, PENNEKAMP J, et al. Website Fingerprinting at Internet Scale[C]// IEEE. Conference Network and Distributed System Security Symposium (NDSS). New York: IEEE, 2016: 23-47. |
| [20] | VAN EDE T, BORTOLAMEOTTI R, CONTINELLA A, et al. Flowprint: Semi-Supervised Mobile-App Fingerprinting on Encrypted Network Traffic[C]// IEEE. Conference Network and Distributed System Security Symposium (NDSS). New York: IEEE, 2020: 24-41. |
| [21] | LIU Xue, ZHANG Shigeng, LI Huihui, et al. Fast Application Activity Recognition with Encrypted Traffic[C]// IEEE. Wireless Algorithms, Systems and Applications Conference. New York: IEEE, 2021: 314-325. |
| [22] | LI Wenbin, QUENARD G. Towards a Multi-Label Dataset of Internet Traffic for Digital Behavior Classification[C]// IEEE. Conference 2021 3rd International Conference on Computer Communication and the Internet (ICCCI). New York: IEEE, 2021: 38-46. |
| [23] | ZHANG Hui, GOU Gaopeng, XIONG Gang, et al. Multi-Granularity Mobile Encrypted Traffic Classification Based on Fusion Features[EB/OL]. (2021-10-10)[2025-01- 10]. https://link.springer.com/chapter/10.1007/978-3-030-89137-4_11. |
| [24] | FU Yanjie, LIU Junming, LI Xiaolin, et al. A Multi-Label Multi-View Learning Framework for In-App Service Usage Analysis[J]. ACM Trans Intell Syst Technol, 2018, 9(4): 40-49. |
| [25] | SHEN Meng, ZHANG Jinpeng, ZHU Liehuang, et al. Accurate Decentralized Application Identification via Encrypted Traffic Analysis Using Graph Neural Networks[EB/OL]. (2021-01-11)[2025-01-10]. https://ieeexplore.ieee.org/document/9319399. |
| [26] | HUOH T L, LUO Yan, ZHANG Tong. Encrypted Network Traffic Classification Using a Geometric Learning Model[C]// IEEE. Conference 2021 IFIP/IEEE International Symposium on Integrated Network Management (IM). New York: IEEE, 2021: 376-383. |
| [1] | 李骁, 宋晓, 李勇. 基于知识蒸馏的医疗诊断差分隐私方法研究[J]. 信息网络安全, 2025, 25(4): 524-535. |
| [2] | 刘晨飞, 万良. 基于时空图神经网络的CAN总线入侵检测方法[J]. 信息网络安全, 2025, 25(3): 478-493. |
| [3] | 张璐, 贾鹏, 刘嘉勇. 基于多元语义图的二进制代码相似性检测方法[J]. 信息网络安全, 2025, 25(10): 1589-1603. |
| [4] | 李涛, 程柏丰. 基于图神经网络的网络资产主动识别技术研究[J]. 信息网络安全, 2025, 25(10): 1615-1626. |
| [5] | 邰滢滢, 魏苑苑, 周翰逊, 王妍. 基于最优传输与改进型极限学习机的加密流量分类方法[J]. 信息网络安全, 2025, 25(1): 148-158. |
| [6] | 刘强, 王坚, 王亚男, 王珊. 基于集成学习的恶意代码动态检测方法[J]. 信息网络安全, 2025, 25(1): 159-172. |
| [7] | 王健, 陈琳, 王凯崙, 刘吉强. 基于时空图神经网络的应用层DDoS攻击检测方法[J]. 信息网络安全, 2024, 24(4): 509-519. |
| [8] | 张新有, 孙峰, 冯力, 邢焕来. 基于多视图表征的虚假新闻检测[J]. 信息网络安全, 2024, 24(3): 438-448. |
| [9] | 余尚戎, 肖景博, 殷琪林, 卢伟. 关注社交异配性的社交机器人检测框架[J]. 信息网络安全, 2024, 24(2): 319-327. |
| [10] | 李奕轩, 贾鹏, 范希明, 陈尘. 基于控制流变换的恶意程序检测GNN模型对抗样本生成方法[J]. 信息网络安全, 2024, 24(12): 1896-1910. |
| [11] | 张选, 万良, 罗恒, 杨阳. 基于两阶段图学习的僵尸网络自动化检测方法[J]. 信息网络安全, 2024, 24(12): 1933-1947. |
| [12] | 李鹏超, 张全涛, 胡源. 基于双注意力机制图神经网络的智能合约漏洞检测方法[J]. 信息网络安全, 2024, 24(11): 1624-1631. |
| [13] | 芦效峰, 程天泽, 龙承念. 基于随机游走的图神经网络黑盒对抗攻击[J]. 信息网络安全, 2024, 24(10): 1570-1577. |
| [14] | 秦中元, 马楠, 余亚聪, 陈立全. 基于双重图神经网络和自编码器的网络异常检测[J]. 信息网络安全, 2023, 23(9): 1-11. |
| [15] | 仝鑫, 金波, 王靖亚, 杨莹. 一种面向Android恶意软件的多视角多任务学习检测方法[J]. 信息网络安全, 2022, 22(10): 1-7. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||