信息网络安全 ›› 2024, Vol. 24 ›› Issue (11): 1624-1631.doi: 10.3969/j.issn.1671-1122.2024.11.002
基于双注意力机制图神经网络的智能合约漏洞检测方法
- 1.重庆警察学院信息安全系,重庆 401331
2.西南大学计算机信息科学学院,重庆 400715
3.重庆市公安局合川分局,重庆 400153
-
收稿日期:2024-08-10出版日期:2024-11-10发布日期:2024-11-21 -
通讯作者:李鹏超lipengchao61@qq.com -
作者简介:李鹏超(1983—),男,重庆,副教授,博士研究生,主要研究方向为电子数据取证、区块链犯罪侦查|张全涛(1984—),男,重庆,教授,博士,主要研究方向为大数据犯罪侦查、区块链犯罪侦查、人工智能法学|胡源(2001—),男,重庆,本科,主要研究方向为网络犯罪侦查与取证 -
基金资助:重庆市教育委员会科学技术研究项目(KJQN202301701);重庆市教育委员会科学技术研究项目(KJZD-K202201701)
Smart Contract Vulnerability Detection Method Based on Graph Convolutional Network with Dual Attention Mechanism
LI Pengchao1,2( ), ZHANG Quantao1, HU Yuan3
), ZHANG Quantao1, HU Yuan3
- 1. Department of Information Security, Chongqing Police College, Chongqing 401331, China
2. School of Computer and Information Science, Southwest University, Chongqing 400715, China
3. Hechuan Branch of Chongqing Public Security Bureau, Chongqing 400153, China
-
Received:2024-08-10Online:2024-11-10Published:2024-11-21
摘要:
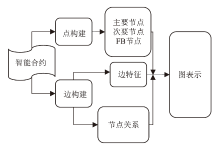
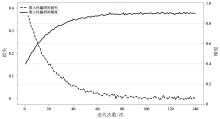
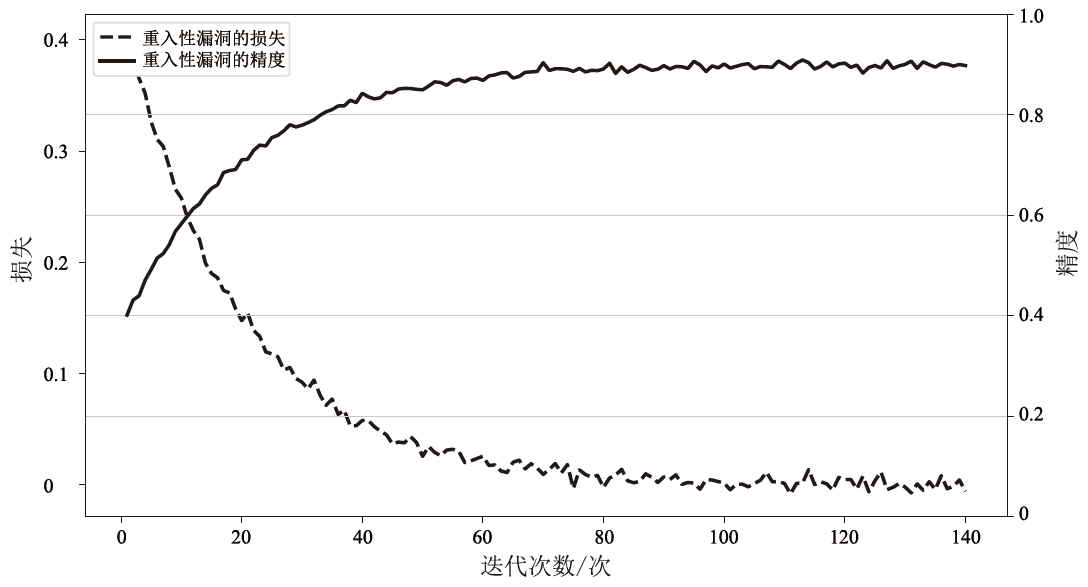
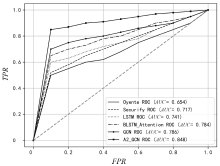
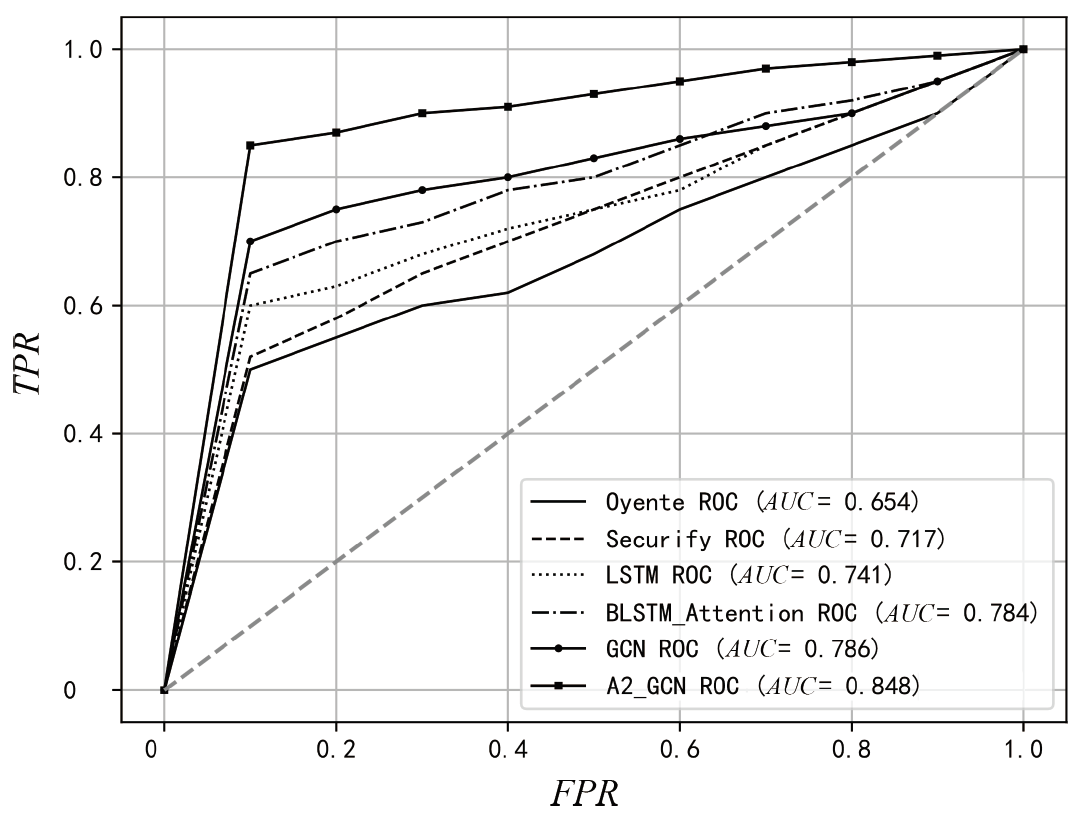
随着区块链技术的广泛应用,智能合约的内部逻辑越来越复杂。然而,目前大多数智能合约漏洞检测方法存在假阳性率高、检测准确率低等问题。为此,文章提出一种基于双注意力机制图神经网络的智能合约漏洞检测方法,用于智能合约漏洞检测,旨在提升检测的准确性和效率。文章在图卷积网络的卷积层中引入了多头注意力机制,并在特征传播阶段动态计算邻接节点信息对应的注意力权重。该机制使模型在特征聚合时更加关注与当前节点最相关的邻居节点,从而提升对重要特征的辨识能力。在图池化阶段,采用注意力池化机制选择和聚合节点特征,进一步提升对关键节点的关注度,提高了对漏洞检测影响较大特征的识别能力。文章采用以太坊智能合约漏洞样本数据集(ESC)进行实验,实验结果表明,与其他检测技术相比,文章所提方法在识别复杂智能合约漏洞方面具有更快的检测速度和更高的准确性。
中图分类号:
引用本文
李鹏超, 张全涛, 胡源. 基于双注意力机制图神经网络的智能合约漏洞检测方法[J]. 信息网络安全, 2024, 24(11): 1624-1631.
LI Pengchao, ZHANG Quantao, HU Yuan. Smart Contract Vulnerability Detection Method Based on Graph Convolutional Network with Dual Attention Mechanism[J]. Netinfo Security, 2024, 24(11): 1624-1631.
使用本文
| [1] |
CHEN Jinfu, WANG Zhenxin, CAI Saihua, et al. Vulnerability Detection Method for Blockchain Smart Contracts Based on Metamorphic Testing[J]. Journal on Communications, 2023, 44(10): 164-176.
doi: 10.11959/j.issn.1000-436x.2023190 |
|
陈锦富, 王震鑫, 蔡赛华, 等. 基于蜕变测试的区块链智能合约漏洞检测方法[J]. 通信学报, 2023, 44(10): 164-176.
doi: 10.11959/j.issn.1000-436x.2023190 |
|
| [2] | QIAN Peng, LIU Zhenguang, HE Qinming, et al. Smart Contract Vulnerability Detection Technique: A Survey[J]. Journal of Software, 2022, 33(8): 3059-3085. |
| 钱鹏, 刘振广, 何钦铭, 等. 智能合约安全漏洞检测技术研究综述[J]. 软件学报, 2022, 33(8): 3059-3085. | |
| [3] |
HE Daojing, DENG Zhi, ZHANG Yuxing, et al. Smart Contract Vulnerability Analysis and Security Audit[J]. IEEE Network, 2020, 34(5): 276-282.
doi: 10.1109/MNET.001.1900656 |
| [4] | WANG Xinming, HE Jiahao, XIE Zhijian, et al. ContractGuard: Defend Ethereum Smart Contracts with Embedded Intrusion Detection[J]. IEEE Transactions on Services Computing, 2020, 13(2): 314-328. |
| [5] | WANG Zexu, WEN Bin. Smart Contract Vulnerability Detection of Symbol Execution with Critical Path Pre-Searching[J]. Journal of Applied Sciences, 2024, 42(2): 364-374. |
| 王泽旭, 文斌. 关键路径预搜索的符号执行智能合约漏洞检测[J]. 应用科学学报, 2024, 42(2): 364-374. | |
| [6] | PENG Kai, LI Meijun, HUANG Haojun, et al. Security Challenges and Opportunities for Smart Contracts in Internet of Things: A Survey[J]. IEEE Internet of Things Journal, 2021, 8(15): 12004-12020. |
| [7] | NGUYEN T D, PHAM L H, SUN Jun, et al. sFuzz: An Efficient Adaptive Fuzzer for Solidity Smart Contracts[C]//ACM. Proceedings of the ACM/IEEE 42nd International Conference on Software Engineering. New York: ACM, 2020: 778-788. |
| [8] | HU Teng, LIU Xiaolei, CHEN Ting, et al. Transaction-Based Classification and Detection Approach for Ethereum Smart Contract[EB/OL]. (2021-03-01)[2024-08-09]. https://doi.org/10.1016/j.ipm.2020.102462. |
| [9] | ZHANG Xiaosong, NIU Weina, HUANG Shiping, et al. A Survey of Smart Contract Vulnerability Detection Methods Based on Deep Learning[J]. Journal of Sichuan University (Natural Science Edition), 2023, 60(2): 7-18. |
| 张小松, 牛伟纳, 黄世平, 等. 基于深度学习的智能合约漏洞检测方法综述[J]. 四川大学学报(自然科学版), 2023, 60(2): 7-18. | |
| [10] | SONG Zitao, HU Yong. Research on Source Code Vulnerability Detection Method Based on Graph Neural Network[J]. Communication Technology, 2022, 55(5): 640-645. |
| 宋子韬, 胡勇. 基于图神经网络的源码漏洞检测方法研究[J]. 通信技术, 2022, 55(5): 640-645. | |
| [11] | HUANG Jianjun, HAN Songming, YOU Wei, et al. Hunting Vulnerable Smart Contracts via Graph Embedding Based Bytecode Matching[J]. IEEE Transactions on Information Forensics and Security, 2021, 16: 2144-2156. |
| [12] | ZHUANG Yuan, LIU Zhenguang, QIAN Peng, et al. Smart Contract Vulnerability Detection Using Graph Neural Network[C]//ACM. Proceedings of the Twenty-Ninth International Conference on International Joint Conferences on Artificial Intelligence. New York: ACM, 2021: 3283-3290. |
| [13] | ZHOU Yaqin, LIU Shangqing, SIOW J, et al. Devign: Effective Vulnerability Identifcation by Learning Comprehensive Program Semantics via Graph Neural Networks[EB/OL]. (2019-09-18)[2024-08-09]. https://doi.org/10.48550/arXiv.1909.03496. |
| [14] | LIU Zhenguang, QIAN Peng, WANG Xiaoyang, et al. Combining Graph Neural Networks with Expert Knowledge for Smart Contract Vulnerability Detection[J]. IEEE Transactions on Knowledge and Data Engineering, 2023, 35(2): 1296-1310. |
| [15] | CHEN Qiaosong, HE Xiaoyang, XU Wenjie, et al. Reentry Vulnerability Detection Based on Pre-Training Technology and Expert Knowledge[J]. Computer Science, 2022, 49(S2): 713-720. |
| 陈乔松, 何小阳, 许文杰, 等. 基于预训练技术和专家知识的重入漏洞检测[J]. 计算机科学, 2022, 49(S2): 713-720. | |
| [16] |
WEN Min, WANG Rongcun, JIANG Shujuan. Source Code Vulnerability Detection Based on Relational Graph Convolution Network[J]. Journal of Computer Applications, 2022, 42(6): 1814-1821.
doi: 10.11772/j.issn.1001-9081.2021091691 |
|
文敏, 王荣存, 姜淑娟. 基于关系图卷积网络的源代码漏洞检测[J]. 计算机应用, 2022, 42(6): 1814-1821.
doi: 10.11772/j.issn.1001-9081.2021091691 |
|
| [17] | LIU Zhenguang, QIAN Peng, WANG Xiang, et al. Smart Contract Vulnerability Detection: from Pure Neural Network to Interpretable Graph Feature and Expert Pattern Fusion[EB/OL]. (2021-06-17)[2024-08-09]. https://arxiv.org/abs/2106.09282v1. |
| [18] | PARIZI R M, DEHGHANTANHA A, CHOO K K R, et al. Empirical Vulnerability Analysis of Automated Smart Contracts Security Testing on Blockchains[EB/OL]. (2018-09-07)[2024-08-09]. https://arxiv.org/abs/1809.02702v1. |
| [19] | QIAN Peng, LIU Zhenguang, HE Qinming, et al. Towards Automated Reentrancy Detection for Smart Contracts Based on Sequential Models[J]. IEEE Access, 2020, 8: 19685-19695. |
| [1] | 张立强, 路梦君, 严飞. 一种基于函数依赖的跨合约模糊测试方案[J]. 信息网络安全, 2024, 24(7): 1038-1049. |
| [2] | 董云云, 朱玉玲, 姚绍文. 基于改进U-Net和混合注意力机制的高质量全尺寸图像隐写方法[J]. 信息网络安全, 2024, 24(7): 1050-1061. |
| [3] | 王健, 陈琳, 王凯崙, 刘吉强. 基于时空图神经网络的应用层DDoS攻击检测方法[J]. 信息网络安全, 2024, 24(4): 509-519. |
| [4] | 刘峰, 江佳齐, 黄灏. 面向加密货币交易介质及过程的安全综述[J]. 信息网络安全, 2024, 24(3): 330-351. |
| [5] | 杨志鹏, 刘代东, 袁军翼, 魏松杰. 基于自注意力机制的网络局域安全态势融合方法研究[J]. 信息网络安全, 2024, 24(3): 398-410. |
| [6] | 江魁, 卢橹帆, 苏耀阳, 聂伟. 基于Attention-GRU的SHDoS攻击检测研究[J]. 信息网络安全, 2024, 24(3): 427-437. |
| [7] | 张新有, 孙峰, 冯力, 邢焕来. 基于多视图表征的虚假新闻检测[J]. 信息网络安全, 2024, 24(3): 438-448. |
| [8] | 孙红哲, 王坚, 王鹏, 安雨龙. 基于Attention-BiTCN的网络入侵检测方法[J]. 信息网络安全, 2024, 24(2): 309-318. |
| [9] | 余尚戎, 肖景博, 殷琪林, 卢伟. 关注社交异配性的社交机器人检测框架[J]. 信息网络安全, 2024, 24(2): 319-327. |
| [10] | 芦效峰, 程天泽, 龙承念. 基于随机游走的图神经网络黑盒对抗攻击[J]. 信息网络安全, 2024, 24(10): 1570-1577. |
| [11] | 秦中元, 马楠, 余亚聪, 陈立全. 基于双重图神经网络和自编码器的网络异常检测[J]. 信息网络安全, 2023, 23(9): 1-11. |
| [12] | 覃思航, 代炜琦, 曾海燕, 顾显俊. 基于区块链的电力应用数据安全共享研究[J]. 信息网络安全, 2023, 23(8): 52-65. |
| [13] | 刘刚, 杨雯莉, 王同礼, 李阳. 基于云联邦的差分隐私保护动态推荐模型[J]. 信息网络安全, 2023, 23(7): 31-43. |
| [14] | 蒋英肇, 陈雷, 闫巧. 基于双通道特征融合的分布式拒绝服务攻击检测算法[J]. 信息网络安全, 2023, 23(7): 86-97. |
| [15] | 李春晓, 王耀飞, 徐恩亮, 赵钰. 基于双线性映射的区块链安全范围搜索技术研究[J]. 信息网络安全, 2023, 23(3): 22-34. |
| 阅读次数 | ||||||||||||||||||||||||||||||||||||||||||||||||||
|
全文 222
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||
|
摘要 174
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||