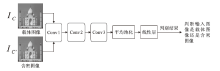
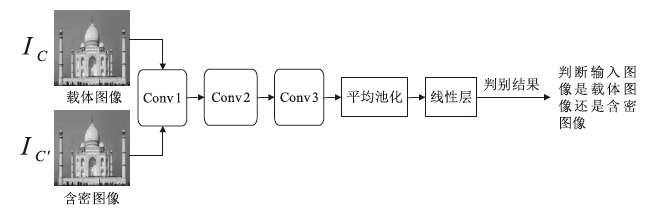
信息网络安全 ›› 2024, Vol. 24 ›› Issue (7): 1050-1061.doi: 10.3969/j.issn.1671-1122.2024.07.007
基于改进U-Net和混合注意力机制的高质量全尺寸图像隐写方法
- 1.云南大学信息学院,昆明 650504
2.云南大学软件学院,昆明 650504
-
收稿日期:2024-03-15出版日期:2024-07-10发布日期:2024-08-02 -
通讯作者:姚绍文yaosw@ynu.edu.cn -
作者简介:董云云(1989—),女,云南,博士研究生,CCF会员,主要研究方向为大数据索引、分布式计算、图像隐写|朱玉玲(1999—),女,云南,硕士研究生,主要研究方向为图像隐写|姚绍文(1966—),男,云南,教授,博士,CCF会员,主要研究方向为网络空间安全、智能信息处理、业务流程建模、信息产业发展与人才培养。 -
基金资助:云南省基础研究计划(202401AT070474)
High-Quality Full-Size Image Steganography Method Based on Improved U-Net and Hybrid Attention Mechanism
DONG Yunyun1, ZHU Yuling2, YAO Shaowen2( )
)
- 1. School of Information Science and Engineering, Yunnan University, Kunming 650504, China
2. School of Software, Yunnan University, Kunming 650504, China
-
Received:2024-03-15Online:2024-07-10Published:2024-08-02
摘要:
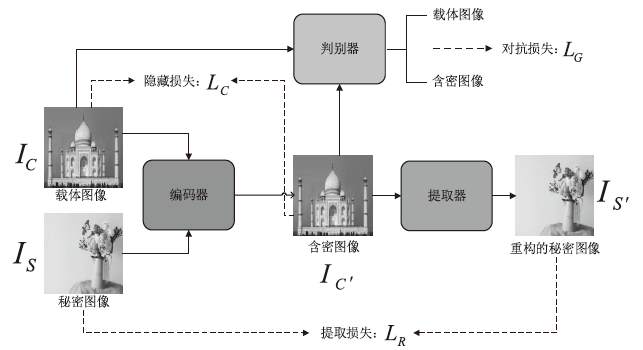
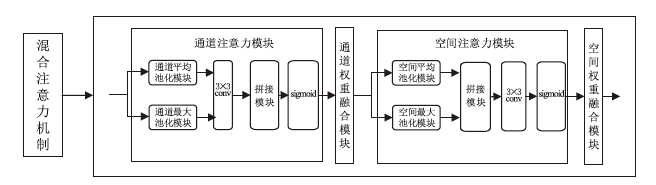
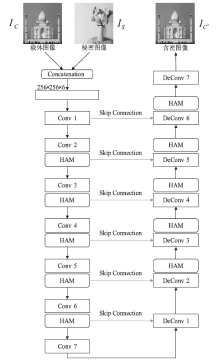
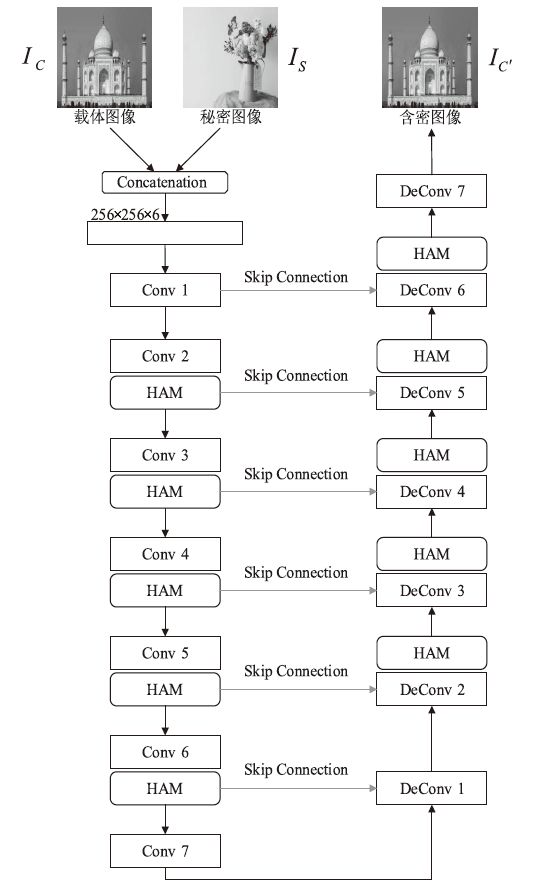
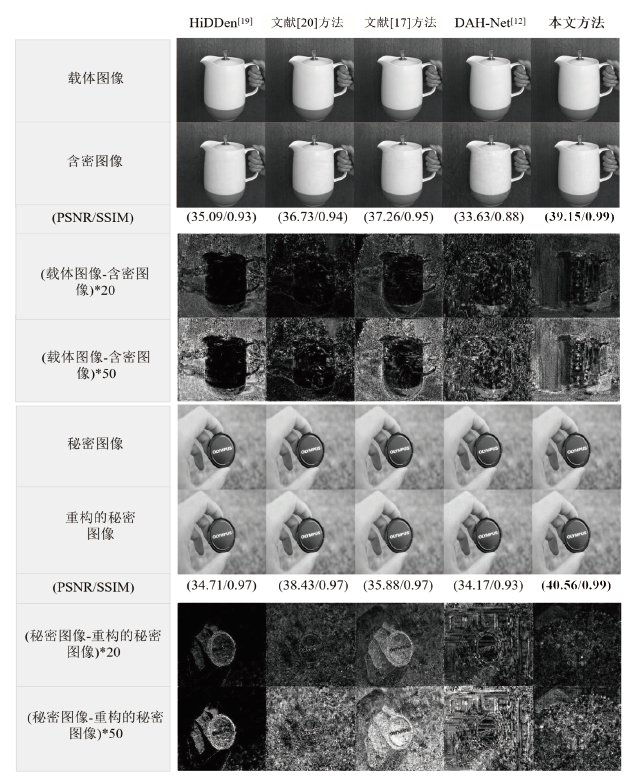
图像隐写术是一种将秘密信息隐藏在图像中以防止被发现的技术。当前的图像隐写模型存在图像生成质量差和抗隐写分析能力弱等问题。混合注意力机制不仅可以抑制无意义的通道信息,避免其在含密图像上产生伪影,而且可以根据载体图像中不同位置的重要程度分配不同的权重,为秘密信息寻找更合适的隐藏区域。基于上述特点,文章提出了基于U-Net和混合注意力机制的高质量全尺寸图像隐写方法。文章所提方法的模型由编码器、提取器和判别器三个子网组成。编码器采用改进的U-Net结构和混合注意力机制模块进行设计;提取器采用卷积神经网络和混合注意力机制模块进行设计;判别器则用于增强模型的安全性。实验结果表明,该方法能够将尺寸为256×256的彩色秘密图像完全隐藏在同尺寸的彩色载体图像中,在不降低隐写容量的情况下实现高质量的图像隐写。该方法在ImageNet、COCO、DIV2K三个数据集上都展现了良好的视觉质量和隐藏容量,在ImageNet数据集上,PSNR值最高可达40.143 dB(载体图像与含密图像)和42.082 dB(秘密图像与重构的秘密图像),同时还能够提高模型的抗隐写分析能力。
中图分类号:
引用本文
董云云, 朱玉玲, 姚绍文. 基于改进U-Net和混合注意力机制的高质量全尺寸图像隐写方法[J]. 信息网络安全, 2024, 24(7): 1050-1061.
DONG Yunyun, ZHU Yuling, YAO Shaowen. High-Quality Full-Size Image Steganography Method Based on Improved U-Net and Hybrid Attention Mechanism[J]. Netinfo Security, 2024, 24(7): 1050-1061.
表1
编码器的网络结构参数与输出尺寸
| 输入尺寸 (H∙W∙C) | 网络结构 | 输出尺寸(H∙W∙C) |
|---|---|---|
| 256∙256∙6 | Conv1(4∙4,2,1)+BN+LeakyReLU | 128∙128∙64 |
| Conv2(4∙4,2,1)+BN+HAM+LeakyReLU | 64∙64∙128 | |
| Conv3(4∙4,2,1)+BN+HAM+LeakyReLU | 32∙32∙256 | |
| Conv4(4∙4,2,1)+BN+HAM+LeakyReLU | 16∙16∙512 | |
| Conv5(4∙4,2,1)+BN+HAM+LeakyReLU | 8∙8∙512 | |
| Conv6(4∙4,2,1)+BN+HAM+LeakyReLU | 4∙4∙512 | |
| Conv7(4∙4,2,1)+BN+LeakyReLU | 2∙2∙512 | |
| DeConv1[ConvTranspose2d(4∙4,2,1)+BN+ReLU] | 4∙4∙512 | |
| DeConv2[ConvTranspose2d(4∙4,2,1)+BN+HAM+ReLU] | 8∙8∙512 | |
| DeConv3[ConvTranspose2d(4∙4,2,1)+BN+HAM+ReLU] | 16∙16∙512 | |
| DeConv4[ConvTranspose2d(4∙4,2,1)+BN+HAM+ReLU] | 32∙32∙256 | |
| DeConv5[ConvTranspose2d(4∙4,2,1)+BN+HAM+ReLU] | 64∙64∙128 | |
| DeConv6[ConvTranspose2d(4∙4,2,1)+BN+HAM+ReLU] | 128∙128∙64 | |
| DeConv7[ConvTranspose2d(4∙4,2,1)+Sigmoid] | 256∙256∙3 |
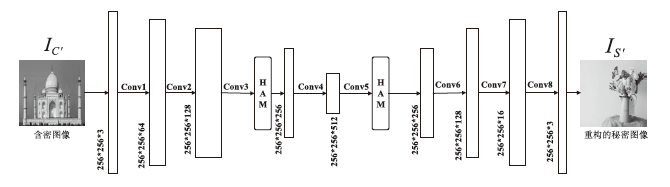
表2
提取器网络结构参数与输出尺寸
| 输入尺寸(H∙W∙C) | 网络结构 | 输出尺寸(H∙W∙C) |
|---|---|---|
| 256∙256∙3 | Conv1(3∙3,1,1)+BN+Relu | 256∙256∙64 |
| Conv2(3∙3,1,1)+BN+Relu+HAM | 256∙256∙128 | |
| Conv3(3∙3,1,1)+BN+Relu | 256∙256∙256 | |
| Conv4(3∙3,1,1)+BN+Relu+HAM | 256∙256∙512 | |
| Conv5(3∙3,1,1)+BN+Relu | 256∙256∙256 | |
| Conv6(3∙3,1,1)+BN+Relu | 256∙256∙128 | |
| Conv7(3∙3,1,1)+BN+Relu | 256∙256∙16 | |
| Conv8(3∙3,1,1)+BN+Tanh | 256∙256∙3 |
表4
本文模型和其他隐写模型在ImageNet数据集上的图像质量对比
| 方法 | 载体图像/含密图像 | 秘密图像/重构的秘密图像 | ||||||
|---|---|---|---|---|---|---|---|---|
| PSNR↑ | SSIM↑ | MAE↓ | RMSE↓ | PSNR↑ | SSIM↑ | MAE↓ | RMSE↓ | |
| HiDDeN[ | 37.351 | 0.948 | 2.655 | 3.490 | 36.317 | 0.954 | 3.061 | 3.921 |
| 文献[ 方法 | 38.431 | 0.947 | 2.375 | 3.079 | 38.511 | 0.973 | 2.279 | 3.048 |
| 文献[ 方法 | 38.978 | 0.975 | 2.288 | 2.952 | 38.001 | 0.970 | 2.427 | 3.232 |
| DAH-Net[ | 38.184 | 0.969 | 2.404 | 3.142 | 38.035 | 0.921 | 1.819 | 3.197 |
| 本文模型 | 40.143 | 0.962 | 1.893 | 2.515 | 42.082 | 0.986 | 1.494 | 2.011 |
表5
本文模型和其他隐写模型在COCO数据集上的图像质量对比
| 方法 | 载体图像/含密图像 | 秘密图像/重构的秘密图像 | ||||||
|---|---|---|---|---|---|---|---|---|
| PSNR↑ | SSIM↑ | MAE↓ | RMSE↓ | PSNR↑ | SSIM↑ | MAE↓ | RMSE↓ | |
| HiDDeN[ | 37.270 | 0.951 | 2.636 | 3.512 | 37.410 | 0.970 | 2.651 | 3.470 |
| 文献[ 方法 | 38.106 | 0.959 | 2.419 | 3.188 | 38.707 | 0.975 | 2.184 | 2.986 |
| 文献[ 方法 | 38.577 | 0.978 | 2.388 | 3.059 | 38.573 | 0.977 | 2.246 | 3.075 |
| DAH-Net[ | 37.323 | 0.963 | 2.684 | 3.470 | 38.203 | 0.975 | 2.295 | 3.315 |
| 本文模型 | 39.368 | 0.965 | 2.019 | 2.743 | 41.679 | 0.986 | 1.558 | 2.121 |
表6
本文模型和其他隐写模型在DIV2K数据集上的图像质量对比
| 方法 | 载体图像/含密图像 | 秘密图像/重构的秘密图像 | ||||||
|---|---|---|---|---|---|---|---|---|
| PSNR↑ | SSIM↑ | MAE↓ | RMSE↓ | PSNR↑ | SSIM↑ | MAE↓ | RMSE↓ | |
| HiDDeN[ | 37.177 | 0.951 | 2.716 | 3.547 | 37.302 | 0.976 | 2.614 | 3.495 |
| 文献[20] 方法 | 37.024 | 0.938 | 2.771 | 3.608 | 38.434 | 0.979 | 2.079 | 3.053 |
| 文献[17] 方法 | 37.361 | 0.976 | 2.792 | 3.549 | 37.673 | 0.973 | 2.523 | 3.358 |
| DAH-Net[ | 34.591 | 0.954 | 3.676 | 4.752 | 32.344 | 0.933 | 4.548 | 6.156 |
| 本文模型 | 38.758 | 0.967 | 2.269 | 2.944 | 41.512 | 0.989 | 1.568 | 2.168 |
| [1] | MANDAL P C, MUKHERJEE I, PAUL G, et al. Digital Image Steganography: A Literature Survey[J]. Information Sciences, 2022, 609: 1451-1488. |
| [2] | XIA Qiang, HE Peisong, LUO Jie, et al. An Efficient Enhancement Algorithm of Cover Image Based on Universal Adversarial Noise[J]. Netinfo Security, 2022, 22(2): 64-75. |
| 夏强, 何沛松, 罗杰, 等. 基于普遍对抗噪声的高效载体图像增强算法[J]. 信息网络安全, 2022, 22(2): 64-75. | |
| [3] |
ZHANG Hongjuan, ZHU Chenming. Novel LSB Steganography Algorithm of Against Statistical Analysis[J]. Computer Engineering, 2008, 34(23): 144-146.
doi: 10.3969/j.issn.1000-3428.2008.23.052 |
| [4] | LI Xiaolong, YANG Bin, CHENG Daofang, et al. A Generalization of LSB Matching[J]. IEEE Signal Processing Letters, 2009, 16(2): 69-72. |
| [5] | HOLUB V, FRIDRICH J. Designing Steganographic Distortion Using Directional Filters[C]// IEEE. 2012 IEEE International Workshop on Information Forensics and Security (WIFS). New York: IEEE, 2012: 234-239. |
| [6] | PEVNY T, FILLER T, BAS P. Using High-Dimensional Image Models to Perform Highly Undetectable Steganography[C]// Springer. 12th Information Hiding Conference. Heidelberg: Springer, 2010: 161-177. |
| [7] | LI Bin, WANG Ming, HUANG Jiwu, et al. A New Cost Function for Spatial Image Steganography[C]// IEEE. 2014 IEEE International Conference on Image Processing (ICIP). New York: IEEE, 2014: 4206-4210. |
| [8] | HOLUB V, FRIDRIVH J, DENEMARK T. Universal Distortion Function for Steganography in an Arbitrary Domain[J]. EURASIP Journal on Information Security, 2014, 2014: 1-13. |
| [9] | CHAUMONT M. Deep Learning in Steganography and Steganalysis[M]. New York: Academic Press, 2020. |
| [10] | YU Chong. Attention Based Data Hiding with Generative Adversarial Networks[C]// AAAI. 34th AAAI Conference on Artificial Intelligence. Menlo Park: AAAI, 2020: 1120-1128. |
| [11] | TAN Jingxuan, LIAO Xin, LIU Jiate, et al. Channel Attention Image Steganography with Generative Adversarial Networks[J]. IEEE Transactions on Network Science and Engineering, 2021, 9(2): 888-903. |
| [12] | ZHANG Le, LU Yao, LI Jinxing, et al. Deep Adaptive Hiding Network for Image Hiding Using Attentive Frequency Extraction and Gradual Depth Extraction[J]. Neural Computing and Applications, 2023, 35(15):10909-10927. |
| [13] | GOODFELLOW I, POUGET-ABADIE J, MIRZA M, et al. Generative Adversarial Networks[J]. Communications of the ACM, 2020, 63(11): 139-144. |
| [14] | VOLKHONSKIY D, NAZAROV I, BURNAEV E. Steganographic Generative Adversarial Networks[C]// ICMV. Twelfth International Conference on Machine Vision (ICMV 2019). Bellingham: SPIE, 2020: 991-1005. |
| [15] | WANG Yaojie, NIU Ke, YANG Xiaoyuan. Image Steganography Scheme Based on GANs[J]. Netinfo Security, 2019, 19(5): 54-60. |
| 王耀杰, 钮可, 杨晓元. 基于生成对抗网络的信息隐藏方案[J]. 信息网络安全, 2019, 19(5): 54-60. | |
| [16] | LEI Yu, LIU Jia, LI Jun, et al. Research and Implementation of a Image Steganography Method Based on Conditional Generative Adversarial Networks[J]. Netinfo Security, 2021, 21(11): 48-57. |
| 雷雨, 刘佳, 李军, 等. 一种基于条件生成对抗网络的图像隐写方法研究与实现[J]. 信息网络安全, 2021, 21(11): 48-57. | |
| [17] | BALUJA S. Hiding Images within Images[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2019, 42(7): 1685-1697. |
| [18] | XIONG Jinbo, MA Rong, ZHANG Yuanyuan, et al. Image Information Hiding Method and Implementation for Social Network[J]. Netinfo Security, 2017, 17(3): 6-8. |
| 熊金波, 马蓉, 张媛媛, 等. 面向社交网络的图片信息隐藏方法与实现[J]. 信息网络安全, 2017, 17(3): 6-8. | |
| [19] | ZHU Jiren, KAPLAN R, JOHNSON J, et al. Hidden: Hiding Data with Deep Networks[C]// ECCV. 15th European Conference on Computer Vision. Heidelberg: Springer, 2018: 657-672. |
| [20] | WENG Xinyu, LI Yongzhi, CHI Lu, et al. High-Capacity Convolutional Video Steganography with Temporal Residual Modeling[C]// ACM. Proceedings of the 2019 on International Conference on Multimedia Retrieval. New York: ACM, 2019: 87-95. |
| [21] | RUSSAKOVSKY O, DENG Jia, SU Hao, et al. Imagenet Large Scale Visual Recognition Challenge[J]. International Journal of Computer Vision, 2015, 115: 211-252. |
| [22] | LIN T Y, MAIRE M, BELONGIE S, et al. Microsoft COCO: Common Objects in Context[C]// ECCV. 13th European Conference on Computer Vision. Heidelberg: Springer, 2014: 740-755. |
| [23] | AGUSTSSON E, TIMOFTE R. Ntire 2017 Challenge on Single Image Super-Resolution: Dataset and Study[C]// IEEE. 30th IEEE/CVF Conference on Computer Vision and Pattern Recognition Workshops (CVPRW). New York: IEEE, 2017: 126-135. |
| [24] | RUSTAD S, ANDONO P N, SHIDIK G F. Digital Image Steganography Survey and Investigation (Goal, Assessment, Method, Development, and Dataset)[J]. Signal Processing, 2023, 27(5): 985-1024. |
| [25] | AGRAWAL R, AHUJA K. CSIS: Compressed Sensing-Based Enhanced-Embedding Capacity Image Steganography Scheme[J]. IET Image Processing, 2021, 15(9): 1909-1925. |
| [1] | 夏强, 何沛松, 罗杰, 刘嘉勇. 基于普遍对抗噪声的高效载体图像增强算法[J]. 信息网络安全, 2022, 22(2): 64-75. |
| [2] | 王耀杰, 杨晓元, 刘文超. 基于数字化卡登格的生成图像隐写方案[J]. 信息网络安全, 2021, 21(2): 70-77. |
| [3] | 雷雨, 刘佳, 李军, 柯彦. 一种基于条件生成对抗网络的图像隐写方法研究与实现[J]. 信息网络安全, 2021, 21(11): 48-57. |
| [4] | 毕新亮, 杨海滨, 杨晓元, 黄思远. 基于StarGAN的生成式图像隐写方案[J]. 信息网络安全, 2020, 20(12): 64-71. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||