信息网络安全 ›› 2024, Vol. 24 ›› Issue (11): 1615-1623.doi: 10.3969/j.issn.1671-1122.2024.11.001
基于人工智能的物联网DDoS攻击检测
- 1.江苏警官学院计算机信息与网络安全系,南京 210031
2.南京市公安局网络安全保卫支队,南京 210005
3.趋势科技(中国)南京分公司,南京 210012
-
收稿日期:2024-08-10出版日期:2024-11-10发布日期:2024-11-21 -
通讯作者:印杰yinjiejspi@163.com -
作者简介:印杰(1977—),男,江苏,高级工程师,硕士,CCF会员,主要研究方向为网络空间安全、人工智能|陈浦(2000—),男,江苏,本科,主要研究方向为网络空间安全、人工智能|杨桂年(1986—),男,江苏,本科,主要研究方向为网络黑灰产犯罪侦查|谢文伟(1978—),男,江苏,工程师,硕士,主要研究方向为网络空间安全、人工智能、计算机视觉|梁广俊(1982—),男,安徽,副教授,博士,CCF会员,主要研究方向为网络空间安全、数据建模 -
基金资助:国家自然科学基金(62272203)
Detection of DDoS Attacks in the Internet of Things Based on Artificial Intelligence
YIN Jie1( ), CHEN Pu1, YANG Guinian2, XIE Wenwei3, LIANG Guangjun1
), CHEN Pu1, YANG Guinian2, XIE Wenwei3, LIANG Guangjun1
- 1. Department of Computer Information and Cybersecurity, Jiangsu Police Institute, Nanjing 210031, China
2. Network Security Support Team of Nanjing Public Security Bureau, Nanjing 210005, China
3. Trend Micro(China) Nanjing Branch, Nanjing 210012, China
-
Received:2024-08-10Online:2024-11-10Published:2024-11-21
摘要:
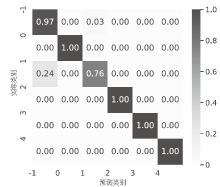
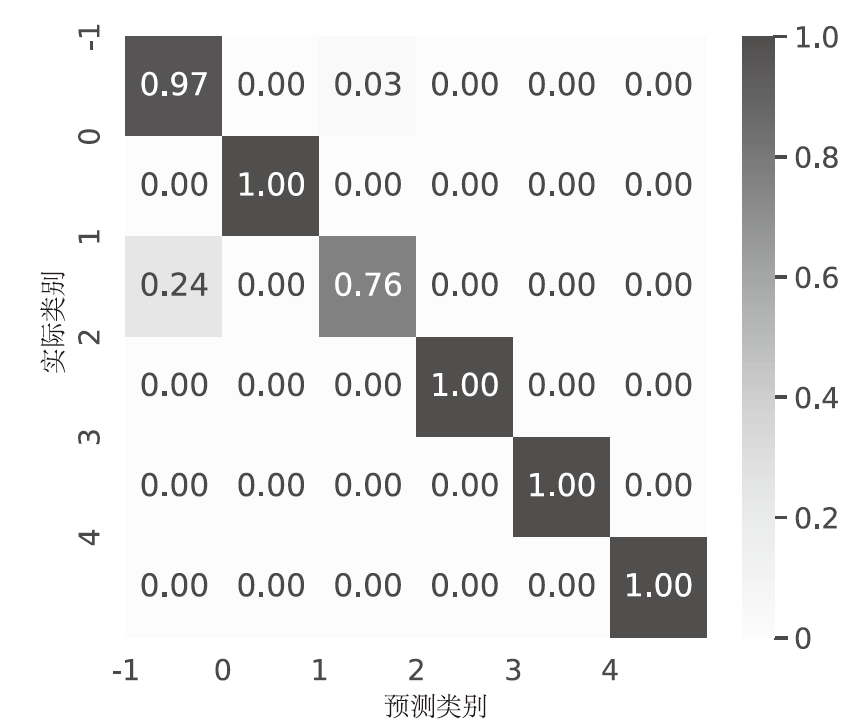
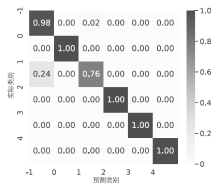
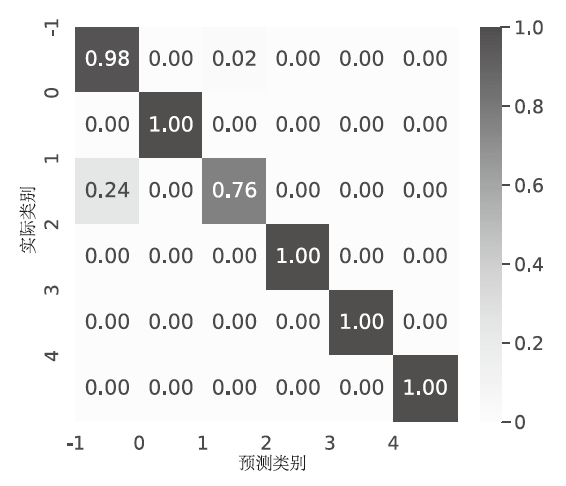
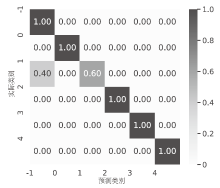
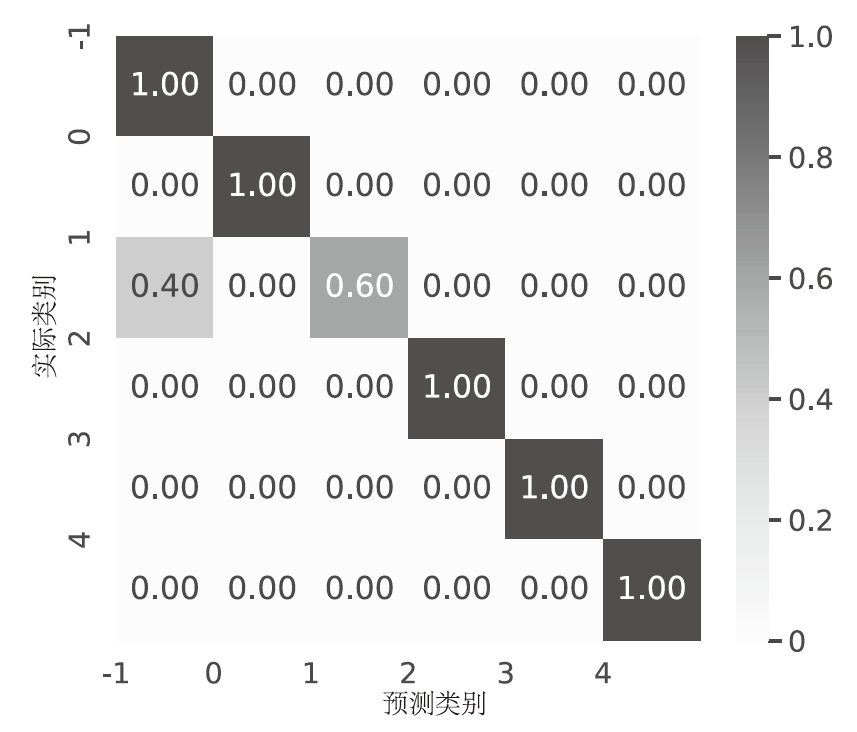
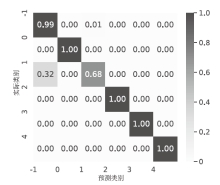
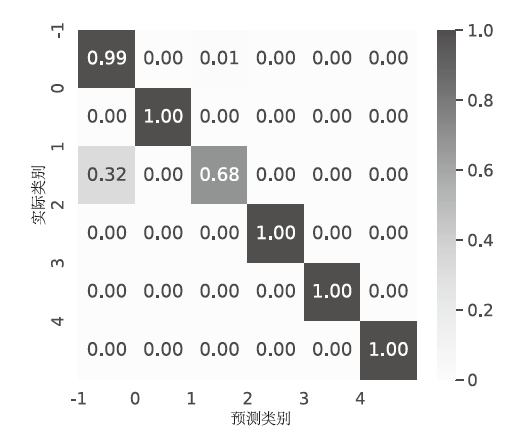
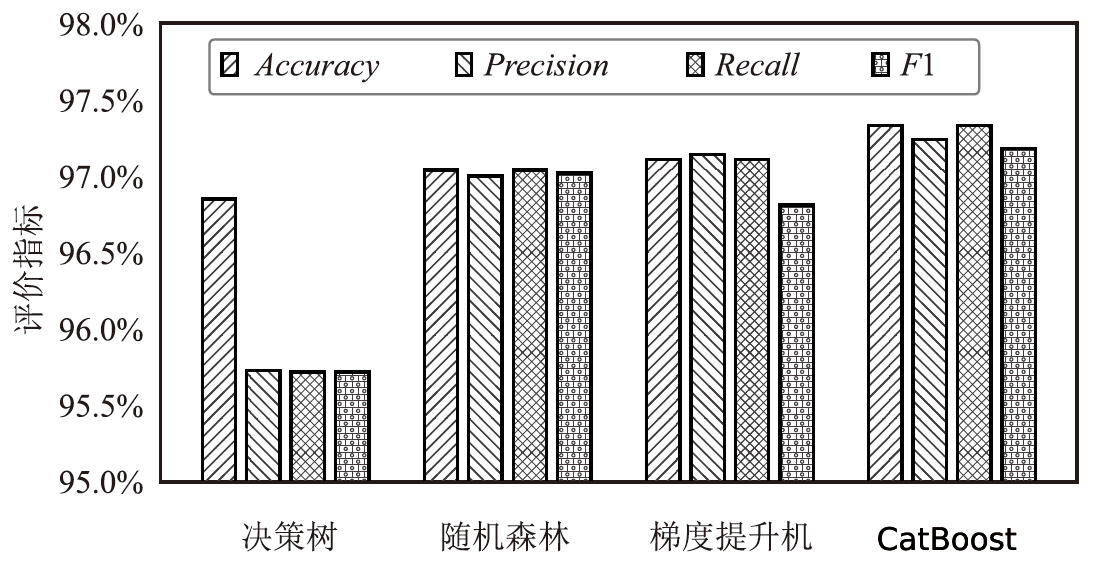
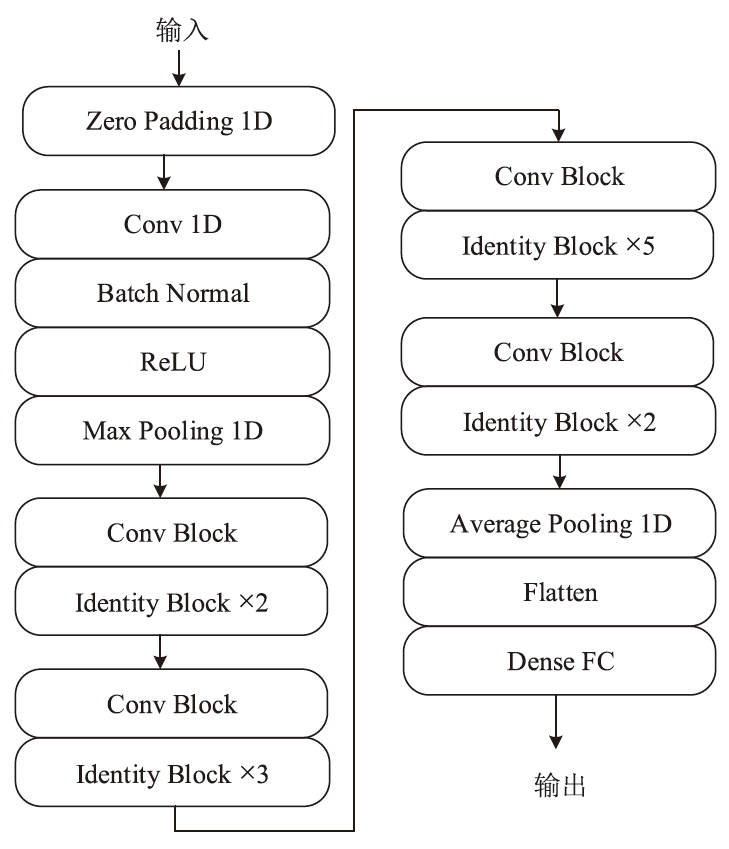
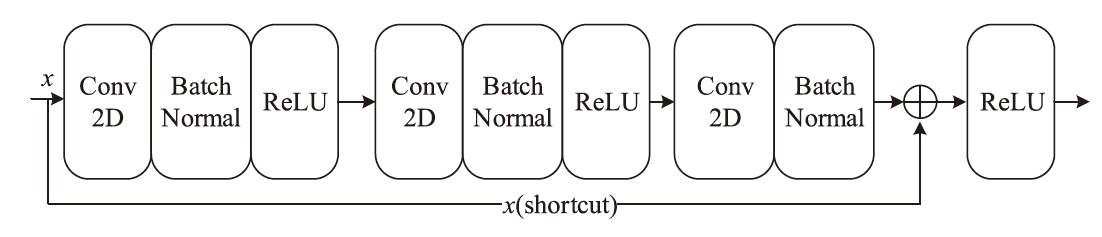
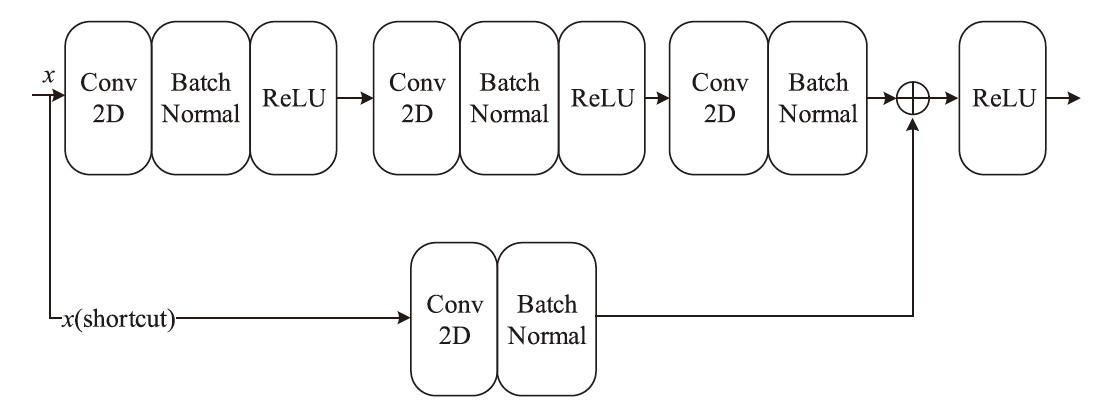
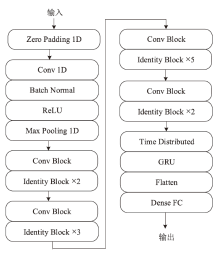
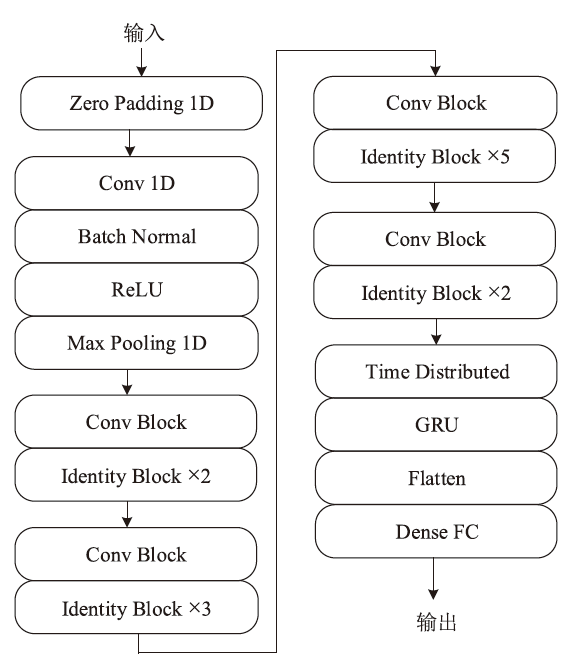
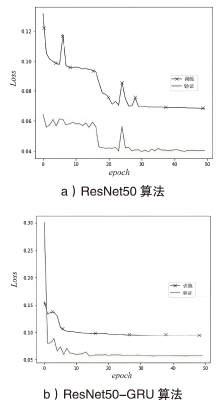
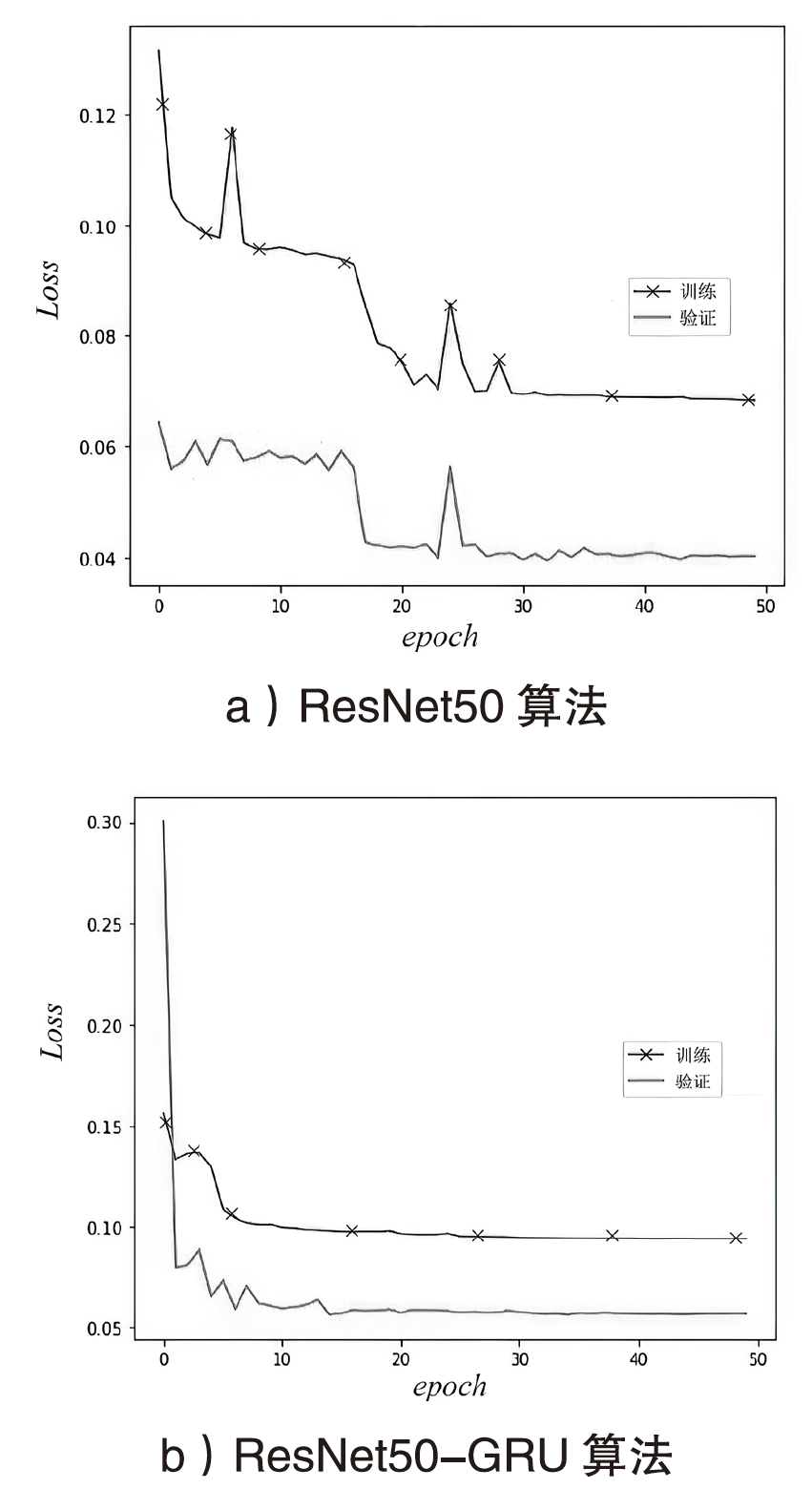
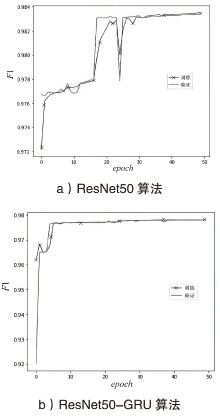
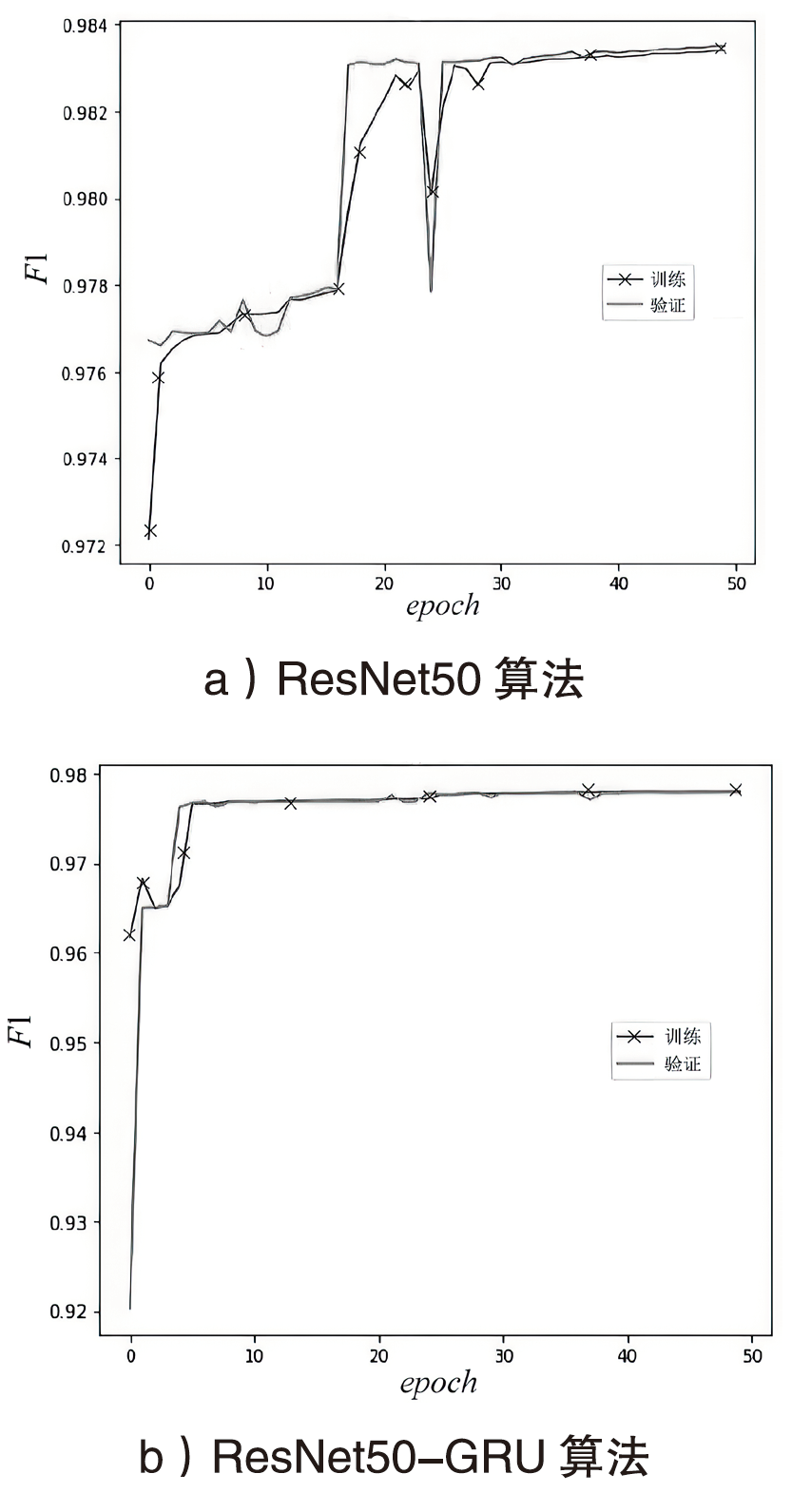
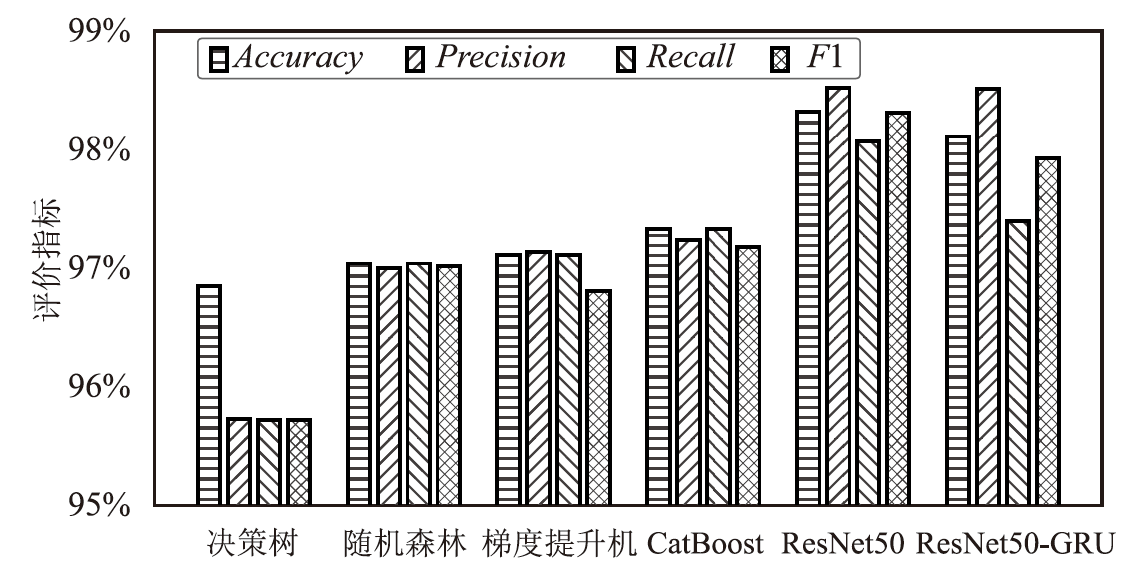
针对物联网DDoS攻击检测最优解问题,文章采用多种算法对物联网DDoS攻击进行检测和建模分类,运用核密度估计筛选出有影响的流量特征字段,建立基于机器学习和深度学习算法的DDoS攻击检测模型,分析了通过可逆残差神经网络和大语言模型处理数据集并进行攻击检测的可行性。实验结果表明,ResNet50算法在综合指标上表现最好;在区分DDoS攻击流量和其他流量问题上,梯度提升类算法表现更优秀;在细分DDoS攻击类型方面,经过优化的ResNet50-GRU算法表现更好。
中图分类号:
引用本文
印杰, 陈浦, 杨桂年, 谢文伟, 梁广俊. 基于人工智能的物联网DDoS攻击检测[J]. 信息网络安全, 2024, 24(11): 1615-1623.
YIN Jie, CHEN Pu, YANG Guinian, XIE Wenwei, LIANG Guangjun. Detection of DDoS Attacks in the Internet of Things Based on Artificial Intelligence[J]. Netinfo Security, 2024, 24(11): 1615-1623.
| [1] | KONG Dezhang, CHEN Xiang, WU Chunming, et al. RDefender: A Lightweight and Robust Defense against Flow Table Overflow Attacks in SDN[J]. IEEE Transactions on Information Forensics and Security, 2024, 19: 9436-9451. |
| [2] | LI Ziqiang, SUN Hong, XIA Pengfei, et al. A Proxy Attack-Free Strategy for Practically Improving the Poisoning Efficiency in Backdoor Attacks[J]. IEEE Transactions on Information Forensics and Security, 2024, 19: 9730-9743. |
| [3] | ANTONAKAKIS M, APRIL T, BAILEY M, et al. Understanding the Mirai Botnet[C]//ACM. 26th USENIX Conference on Security Symposium. New York: ACM, 2017: 1093-1110. |
| [4] | China Mobile Communications Research Institute. White Paper on Future Application Scenarios and Capabilities of 6G Internet of Things(2023)[EB/OL]. [2024-06-10]. http://cmri.chinamobile.com/wp-content/uploads/2023/08/6G物联网未来应用场景及能力白皮书.pdf. |
| 中国移动通信研究院. 6G物联网未来应用场景及能力白皮书(2023年)[EB/OL]. [2024-06-10]. http://cmri.chinamobile.com/wp-content/uploads/2023/08/6G物联网未来应用场景及能力白皮书.pdf. | |
| [5] | ELIYAN L F, DI PIETRO R. DoS and DDoS Attacks in Software Defined Networks: A Survey of Existing Solutions and Research Challenges[J]. Future Generation Computer Systems, 2021, 122: 149-171. |
| [6] | FANG Xin, WAN Yang, WEN Xia, et al. DDoS Attacks Based on Protocol Analysis of Network Intrusion Detection System Research[J]. Netinfo Security, 2012, 12(4): 36-38. |
| 方欣, 万扬, 文霞, 等. 基于协议分析技术的网络入侵检测系统中DDoS攻击的方法研究[J]. 信息网络安全, 2012, 12(4):36-38. | |
| [7] | MOHAMMAD R M A, ALSMADI M K, ALMARASHDEH I, et al. An Improved Rule Induction Based Denial of Service Attacks Classification Model[EB/OL]. [2024-08-01]. https://www.sciencedirect.com/science/article/abs/pii/S0167404820302819?via%3Dihub. |
| [8] | HAJIMAGHSOODI M, JALILI R. RAD: A Statistical Mechanism Based on Behavioral Analysis for DDoS Attack Countermeasure[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 2732-2745. |
| [9] | LIU Xinqian, REN Jiadong, HE Haitao, et al. Low-Rate DDoS Attacks Detection Method Using Data Compression and Behavior Divergence Measurement[EB/OL]. [2024-07-20]. https://www.sciencedirect.com/science/article/abs/pii/S0167404820303801?via%3Dihub. |
| [10] | SEIFOUSADATI A, GHASEMSHIRAZI S, FATHIAN M. A Machine Learning Approach for DDoS Detection on IoT Devices[EB/OL]. [2024-08-01]. https://arxiv.org/abs/2110.14911v1. |
| [11] | MUGHAID A, ALQAHTANI A, ALZU’BI S, et al. Utilizing Machine Learning Algorithms for Effectively Detection IoT DDoS Attacks[C]// Springer. International Conference on Advances in Computing Research. Heidelberg: Springer, 2023: 617-629. |
| [12] | GAO Neng, FENG Dengguo, XIANG Ji. A Data-Mining Based DoS Detection Technique[J]. Chinese Journal of Computers, 2006, 29(6): 944-951. |
| 高能, 冯登国, 向继. 一种基于数据挖掘的拒绝服务攻击检测技术[J]. 计算机学报, 2006, 29(6):944-951. | |
| [13] | LI Junfeng, TANG Wei. Application of Feedforward Neural Network Algorithm in DDoS Detection[J]. China Science and Technology Information, 2009(17): 115-116. |
| 李俊峰, 汤伟. 前馈神经网络算法在DDoS检测中的应用[J]. 中国科技信息, 2009(17):115-116. | |
| [14] | DUAN Weiheng. Research and Analysis of Anti-DDOS Market Based on Cloud Computing Technology[D]. Beijing: Beijing University of Posts and Telecommunications, 2012. |
| 段伟恒. 基于云计算技术的抗DDOS市场研究分析[D]. 北京: 北京邮电大学, 2012. | |
| [15] | WANG Chunhui. Analysis of Six Legal Systems on Cyber Security Law[J]. Journal of Nanjing University of Posts and Telecommunications(Natural Science Edition), 2017, 37(1): 1-13. |
| 王春晖. 《网络安全法》六大法律制度解析[J]. 南京邮电大学学报(自然科学版), 2017, 37(1):1-13. | |
| [16] | HOSSAIN M S, RAGHUNATHAN V. AEGIS: A Lightweight Firewall for Wireless Sensor Networks[C]//Springer. Distributed Computing in Sensor Systems:6th IEEE International Conference. Heidelberg: Springer, 2010: 258-272. |
| [17] | ZHANG Yu, WEN Jiangtao. An IoT Electric Business Model Based on the Protocol of Bitcoin[C]//IEEE. 2015 18th International Conference on Intelligence in Next Generation Networks. New York: IEEE, 2015: 184-191. |
| [18] | XIE Yunzhou. The Evolution of NB-IoT Standard System and Development of Internet of Things Industry[J]. Chinese Journal on Internet of Things, 2018, 2(1): 76-87. |
|
解运洲. NB-IoT标准体系演进与物联网行业发展[J]. 物联网学报, 2018, 2(1):76-87.
doi: 10.11959/j.issn.2096-3750.2018.00044 |
|
| [19] | CAO Jichang, WANG Jiayi, CHEN Mingqi. Research and Application of Key Technologies of Intelligent Site System Based on BIM+GIS+IoT Technology[J]. Construction Science and Technology, 2020(S1): 74-77. |
| 曹吉昌, 王佳仪, 陈明琪. 基于BIM+GIS+IoT技术的智慧工地系统关键技术研究及应用[J]. 建设科技, 2020(S1):74-77. | |
| [20] | KANG Shilong, DU Zhongyi, LEI Yongmei, et al. Overview of Industrial Internet of Things[J]. Internet of Things Technologies, 2013, 3(6): 80-82. |
| 康世龙, 杜中一, 雷咏梅, 等. 工业物联网研究概述[J]. 物联网技术, 2013, 3(6):80-82. | |
| [21] | YIN Zhouping, TAO Bo. Technologies of the Industrial Internet of Things and Its Applications[M]. Beijing: Tsinghua University Press, 2022. |
| 尹周平, 陶波. 工业物联网技术及应用[M]. 北京: 清华大学出版社, 2022. |
| [1] | 张学旺, 陈思宇, 罗欣悦, 雷志滔, 谢昊飞. 面向云辅助工业物联网的高效可搜索属性基加密方案[J]. 信息网络安全, 2024, 24(9): 1352-1363. |
| [2] | 邢长友, 王梓澎, 张国敏, 丁科. 基于预训练Transformers的物联网设备识别方法[J]. 信息网络安全, 2024, 24(8): 1277-1290. |
| [3] | 张晓均, 张楠, 郝云溥, 王周阳, 薛婧婷. 工业物联网系统基于混沌映射三因素认证与密钥协商协议[J]. 信息网络安全, 2024, 24(7): 1015-1026. |
| [4] | 申秀雨, 姬伟峰. 考虑安全的边—云协同计算卸载成本优化[J]. 信息网络安全, 2024, 24(7): 1110-1121. |
| [5] | 李志华, 陈亮, 卢徐霖, 方朝晖, 钱军浩. 面向物联网Mirai僵尸网络的轻量级检测方法[J]. 信息网络安全, 2024, 24(5): 667-681. |
| [6] | 王健, 陈琳, 王凯崙, 刘吉强. 基于时空图神经网络的应用层DDoS攻击检测方法[J]. 信息网络安全, 2024, 24(4): 509-519. |
| [7] | 戚晗, 王敬童, 拱长青. 基于随机量子层的变分量子卷积神经网络鲁棒性研究[J]. 信息网络安全, 2024, 24(3): 363-373. |
| [8] | 杨杰超, 胡汉平, 帅燕, 邓宇昕. 基于时变互耦合双混沌系统的轻量级序列密码[J]. 信息网络安全, 2024, 24(3): 385-397. |
| [9] | 冯光升, 蒋舜鹏, 胡先浪, 马明宇. 面向物联网的入侵检测技术研究新进展[J]. 信息网络安全, 2024, 24(2): 167-178. |
| [10] | 翟鹏, 何泾沙, 张昱. 物联网环境下基于SM9算法和区块链技术的身份认证方法[J]. 信息网络安全, 2024, 24(2): 179-187. |
| [11] | 陈宝刚, 张毅, 晏松. 民航空管信息系统用户多因子持续身份可信认证方法研究[J]. 信息网络安全, 2024, 24(11): 1632-1642. |
| [12] | 兰浩良, 王群, 徐杰, 薛益时, 张勃. 基于区块链的联邦学习研究综述[J]. 信息网络安全, 2024, 24(11): 1643-1654. |
| [13] | 王南, 袁也, 杨浩然, 文周之, 苏明, 刘晓光. 环保大数据在区块链中的隐私计算[J]. 信息网络安全, 2024, 24(10): 1515-1527. |
| [14] | 张子涵, 赖清楠, 周昌令. 深度学习框架模糊测试研究综述[J]. 信息网络安全, 2024, 24(10): 1528-1536. |
| [15] | 萨其瑞, 尤玮婧, 张逸飞, 邱伟杨, 马存庆. 联邦学习模型所有权保护方案综述[J]. 信息网络安全, 2024, 24(10): 1553-1561. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||