信息网络安全 ›› 2024, Vol. 24 ›› Issue (2): 179-187.doi: 10.3969/j.issn.1671-1122.2024.02.002
物联网环境下基于SM9算法和区块链技术的身份认证方法
- 1.北京工业大学信息学部,北京100124
2.济宁学院计算机科学与工程学院,济宁 273100
-
收稿日期:2023-02-27出版日期:2024-02-10发布日期:2024-03-06 -
通讯作者:何泾沙 E-mail:jhe@bjut.edu.cn -
作者简介:翟鹏(1978—),男,山东,副教授,博士,主要研究方向为网络安全、物联网及区块链技术|何泾沙(1961—),男,陕西,教授,博士,主要研究方向为计算机和网络安全、测试与分析和云计算|张昱(1978—),男,山东,讲师,博士,主要研究方向为网络安全、隐私保护 -
基金资助:北京市自然科学基金(IS23054)
An Identity Authentication Method Based on SM9 and Blockchain in the IoT Environment
ZHAI Peng1,2, HE Jingsha1,2( ), ZHANG Yu2
), ZHANG Yu2
- 1. Faculty of Information Technology, Beijing University of Technology, Beijing 100124, China
2. School of Computer Science and Engineering, Jining University, Jining 273100, China
-
Received:2023-02-27Online:2024-02-10Published:2024-03-06 -
Contact:HE Jingsha E-mail:jhe@bjut.edu.cn
摘要:
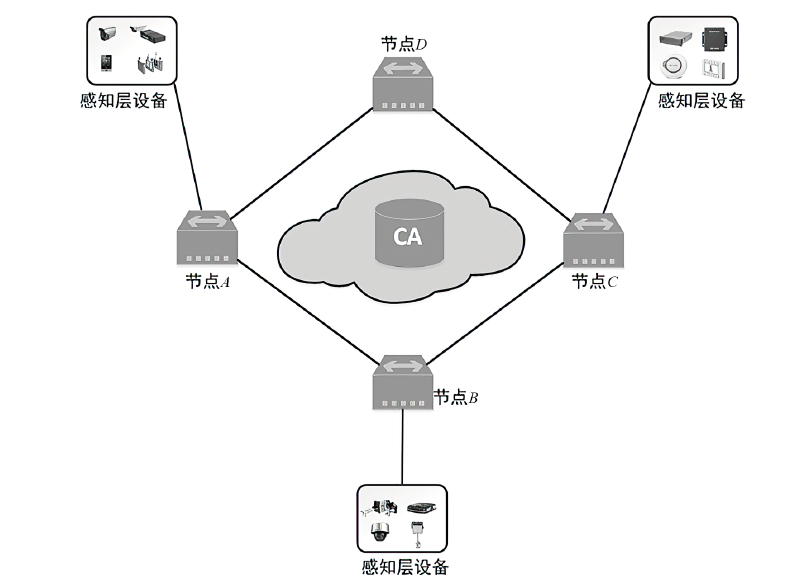
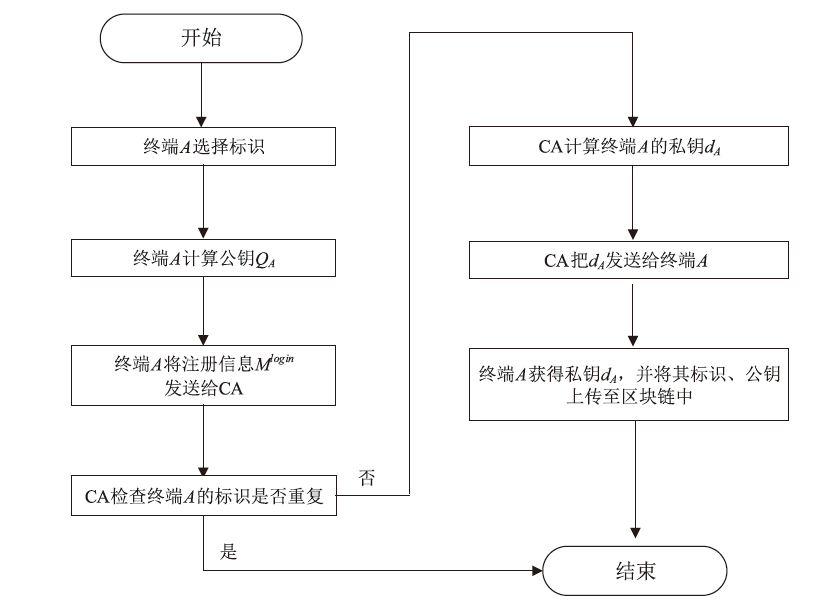
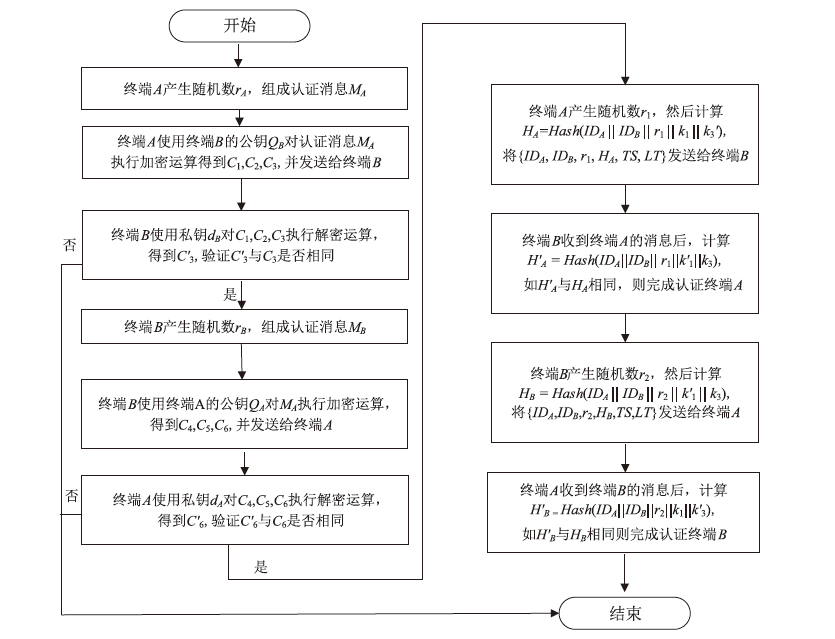
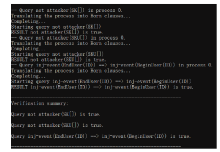
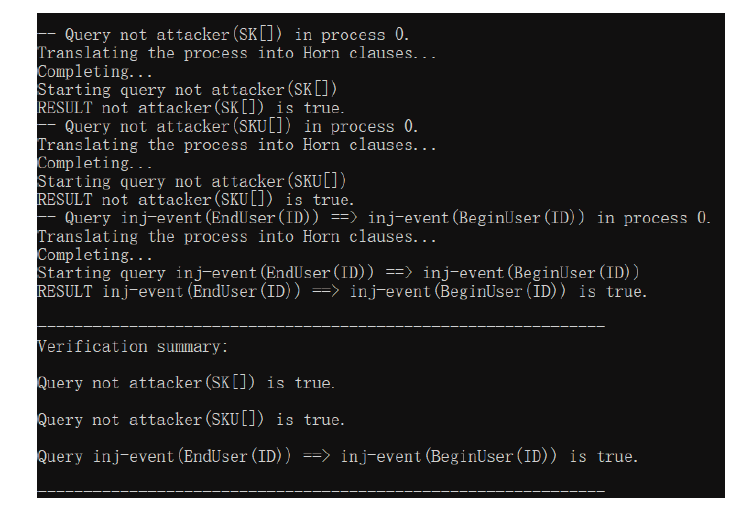
物联网环境下的终端设备需要进行相互识别和身份认证来保障网络安全和数据安全,身份认证是物联网安全保障的第一道防线,现有的传统公钥密码体制(PKI)过程繁琐、计算量大,不能很好地满足资源受限、开放、分布式物联网环境。文章基于SM9标识密码算法设计了一种基于区块链的物联网终端身份认证方案,基于计算性 Diffie-Hellman困难问题、q-Diffie-Hellman逆问题和双线性DH困难问题的假设下,可以极大满足机密性和不可伪造性,更加符合物联网实际应用环境。该方案采用设备身份标识作为公钥,简化了密钥分发管理流程,另外区块链作为一种去中心化的底层存储数据库,用来记录密钥、证书、签名等信息,可以为认证流程进行可信背书。通过性能和Proverif形式化安全性分析,并与目前主流的几种认证方式进行比较,证明该方案可以满足物联网环境下时间、性能及安全性的需求。
中图分类号:
引用本文
翟鹏, 何泾沙, 张昱. 物联网环境下基于SM9算法和区块链技术的身份认证方法[J]. 信息网络安全, 2024, 24(2): 179-187.
ZHAI Peng, HE Jingsha, ZHANG Yu. An Identity Authentication Method Based on SM9 and Blockchain in the IoT Environment[J]. Netinfo Security, 2024, 24(2): 179-187.
表1
本文方案所用符号含义
| 符号 | 符号含义 | 符号 | 符号含义 |
|---|---|---|---|
素数 | 终端A的标识 | ||
| 终端B的标识 | |||
| 终端A的公钥 | |||
| KGC | 标识密码认证机构的密钥 生成中心 | 终端A的私钥 | |
| 密钥派生函数 | 终端B的公钥 | ||
| 密钥派生函数生成的字符串 | 终端B的私钥 | ||
| CA | 标识密码认证机构 | 随机数 | |
| 私钥生成函数识别符 | 时间戳 | ||
| 标识密码认证机构服务器的标识 | 生存时间 | ||
| 标识密码认证机构服务器的主公钥 | 用密钥 | ||
| 标识密码认证机构服务器的主私钥 | 用密钥 |
表2
模型安全性对比
| 模型 | 抵御 重放攻击 | 抵御 篡改攻击 | 抵御 串谋攻击 | 抵御 仿冒攻击 | 抵御 中间人 攻击 | 抵御拒 绝服务 攻击 | 前向 安全 |
|---|---|---|---|---|---|---|---|
| 文献[ | No | No | Yes | Yes | No | Yes | Yes |
| 文献[ | Yes | Yes | Yes | No | Yes | Yes | No |
| 文献[ | Yes | No | No | Yes | Yes | No | Yes |
| 文献[ | Yes | No | No | Yes | No | No | Yes |
| 文献[ | No | No | No | Yes | No | No | Yes |
| 文献[ | Yes | Yes | Yes | No | Yes | Yes | No |
| 文献[ | Yes | No | No | No | No | No | Yes |
| 文献[ | No | No | Yes | No | Yes | Yes | Yes |
| 本文 | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| [1] | PORAMBAGE P, KUMAR P, SCHMITT C, et al. Certificate-Based Pairwise Key Establishment Protocol for Wireless Sensor Networks[C]// IEEE. 2013 IEEE 16th International Conference on Computational Science and Engineering. New York: IEEE, 2013: 667-674. |
| [2] | DIAZ-SANCHEZ D, MARIN-LOPEZ A, ALMENAREZ F. TLS/PKI Challenges and Certificate Pinning Techniques for IoT and M2M Secure Communications[C]// IEEE. IEEE Communications Surveys & Tutorials. New York: IEEE, 2019: 3502-3531. |
| [3] |
KUMAR P, GURTOV A, IINATTI J, et al. Lightweight and Secure Session-Key Establishment Scheme in Smart Home Environments[J]. IEEE Sensors Journal, 2016, 16(1): 254-264.
doi: 10.1109/JSEN.2015.2475298 URL |
| [4] | GE Chunpeng, XIA Jinyue, FANG Liming. Key-Private Identity-Based Proxy Re-Encryption[J]. Cmc-Computers Materials & Continua, 2020, 63(2): 633-647. |
| [5] |
RIVEST R L, SHAMIR A, ADLEMAN L. A Method for Obtaining Digital Signatures and Public-Key Cryptosystems[J]. Communications of the ACM, 1978, 21(2): 120-126.
doi: 10.1145/359340.359342 URL |
| [6] |
CHENG Xu, ZHANG Ziyang, CHEN Fulong, et al. Secure Identity Authentication of Community Medical Internet of Things[J]. IEEE Access, 2019, 7: 115966-115977.
doi: 10.1109/ACCESS.2019.2935782 |
| [7] | SHAMIR A. Identity-Based Cryptosystems and Signature Schemes[C]// Springer. Workshop on the Theory and Application of Cryptographic Techniques. Heidelberg: Springer, 1984: 47-53. |
| [8] |
XIAO Hao, WEI Ren, FEI Yangyang, et al. A Blockchain-Based Cross-Domain and Autonomous Access Control Scheme for Internet of Things[J]. IEEE Transactions on Services Computing, 2023, 16(2): 773-786.
doi: 10.1109/TSC.2022.3179727 URL |
| [9] | XIE Yong, XU Fang, LI Xiang, et al. EIAS: An Efficient Identity-Based Aggregate Signature Scheme for WSNs against Coalition Attack[J]. Cmc-Computers Materials & Continua, 2019, 59(3): 903-924. |
| [10] | YAN Hongyang, WANG Yu, JIA Chunfu, et al. IoT-FBAC: Function-Based Access Control Scheme Using Identity-Based Encryption in IoT[J]. Future Generation Computer Systems-the International Journal of Escience, 2019, 95: 344-353. |
| [11] | SIDDHARTHA V G, KANSAL L. A Lightweight Authentication Protocol Using Implicit Certificates for Securing IoT Systems[J]. Procedia Computer Science, 2020, 16(7): 9-17. |
| [12] | CUI Zhihua, XUE Fei, ZHANG Shiqiang, et al. A Hybrid BlockChain-Based Identity Authentication Scheme for Multi-WSN[J]. IEEE Transactions on Services Computing, 2020, 13(2): 241-251. |
| [13] |
PUTRA G, DEDEOGLU V, KANHERE S, et al. Trust-Based Blockchain Authorization for IoT[J]. IEEE Transactions on Network and Service Management, 2021, 18(2): 1646-1658.
doi: 10.1109/TNSM.2021.3077276 URL |
| [14] |
CHENG Guanjie, CHEN Yan, DENG Shuiguang, et al. A Blockchain-Based Mutual Authentication Scheme for Collaborative Edge Computing[J]. IEEE Transactions on Computational Social Systems, 2022, 9(1): 146-158.
doi: 10.1109/TCSS.2021.3056540 URL |
| [15] |
XUE Kaiping, LUO Xinyi, MA Yongjin, et al. A Distributed Authentication Scheme Based on Smart Contract for Roaming Service in Mobile Vehicular Networks[J]. IEEE Transactions on Vehicular Technology, 2022, 71(5): 5284-5297.
doi: 10.1109/TVT.2022.3148303 URL |
| [16] | GU Pengpeng, CHEN Liquan. An Efficient Blockchain-Based Cross-Domain Authentication and Secure Certificate Revocation Scheme[C]// IEEE. 2020 IEEE 6th International Conference on Computer and Communications (ICCC). New York:IEEE, 2020: 1776-1782. |
| [17] | LAI Jianchang, HUANG Xinyi, HE Debiao, et al. Security Analysis of SM9 Digital Signature and Key Encapsulation[J]. Science China: Information, 2021, 51(11): 1900-1913. |
| 赖建昌, 黄欣沂, 何德彪, 等. 国密 SM9 数字签名和密钥封装算法的安全性分析[J]. 中国科学:信息科学, 2021, 51(11): 1900-1913. | |
| [18] | YANG Yatao, ZHANG Xiaowei, YUAN Zheng. Privacy Preserving Scheme in Block Chain with Provably Secure Based on SM9 Algorithm[J]. Journal of Software, 2019, 30(6): 1692−1704. |
| 杨亚涛, 张筱薇, 袁征. 基于SM9算法可证明安全的区块链隐私保护方案[J]. 软件学报, 2019, 30(6): 1692-1704. | |
| [19] | YUAN Feng, CHENG Chaohui. Overview on SM9 Identity-Based Cryptographic Algorithm[J]. Journal of Information Security Research. 2016, 2(11): 18-27. |
| 袁峰, 程朝辉. SM9标识密码算法综述[J]. 信息安全研究, 2016, 2(11): 18-27. | |
| [20] | PENG Cong, HE Debiao, LUO Min. An Identity-Based Ring Signature Scheme for SM9 Algorithm[J]. Journal of Cryptologic Research, 2021, 8(4): 724-734. |
| 彭聪, 何德彪, 罗敏. 基于SM9标识密码算法的环签名方案[J]. 密码学报, 2021, 8(4): 724-734. | |
| [21] | ZHANG Xiaoshuai, LIU Chao, CHAI K, et al. A Privacy-Preserving Consensus Mechanism for an Electric Vehicle Charging Scheme[J]. Journal of Network and Computer Applications, 2021, 174: 161-174. |
| [22] | LI Yue. Design of a Key Establishment Protocol for Smart Home Energy Management System[C]// IEEE. 2013 Fifth International Conference on Computational Intelligence, Communication Systems and Networks. New York: IEEE, 2013: 88-93. |
| [23] | BINOD V D M, HUSSEIN T, MOUFTAH. Device Authentication Mechanism for Smart Energy Home Area Networks[C]// IEEE. 2011 IEEE International Conference on Consumer Electronics (ICCE). New York:IEEE, 2011: 787-788. |
| [24] | SCIANCALEPORE S, PIRO G, BOGGIA G, et al. Public Key Authentication and Key Agreement in IoT Devices with Minimal Airtime Consumption[C]// IEEE. IEEE Embedded Systems Letters. New York: IEEE, 2017: 1-4. |
| [25] |
HAN K, KIM J, SHON T, et al. A Novel Secure Key Paring Protocol for RF4CE Ubiquitous Smart Home Systems[J]. Personal and Ubiquitous Computing, 2012, 17(5): 945-965.
doi: 10.1007/s00779-012-0541-2 URL |
| [26] | HOSSAIN M, NOOR S, HASAN R. HSC-IoT: A Hardware and Software Co-Verification Based Authentication Scheme for Internet of Things[C]// IEEE. 2017 5th IEEE International Conference on Mobile Cloud Computing, Services, and Engineering (MobileCloud). New York:IEEE, 2017: 212-219. |
| [27] |
KUMAR P, BRAEKEN A, GURTOV A, et al. Anonymous Secure Framework in Connected Smart Home Environments[J]. IEEE Transactions on Information Forensics and Security, 2017, 12(4): 968-979.
doi: 10.1109/TIFS.2016.2647225 URL |
| [28] | PATEL S P D R, NAVIK A P. Energy Efficient Integrated Authentication and Access Control Mechanisms for Internet of Things[C]// IEEE. 2016 International Conference on Internet of Things and Applications (IOTA). New York:IEEE, 2016: 304-319. |
| [1] | 冯光升, 蒋舜鹏, 胡先浪, 马明宇. 面向物联网的入侵检测技术研究新进展[J]. 信息网络安全, 2024, 24(2): 167-178. |
| [2] | 何业锋, 权家辉, 刘妍. 基于混合区块链的位置隐私保护方案[J]. 信息网络安全, 2024, 24(2): 229-238. |
| [3] | 吴昊天, 李一凡, 崔鸿雁, 董琳. 基于零知识证明和区块链的联邦学习激励方案[J]. 信息网络安全, 2024, 24(1): 1-13. |
| [4] | 王君艳, 伊鹏, 贾洪勇, 张建辉. 基于改进CAE的物联网终端风险评估模型[J]. 信息网络安全, 2024, 24(1): 150-159. |
| [5] | 朱郭诚, 何德彪, 安浩杨, 彭聪. 基于区块链和SM9数字签名的代理投票方案[J]. 信息网络安全, 2024, 24(1): 36-47. |
| [6] | 公鹏飞, 谢四江, 程安东. 基于HotStuff改进的多主节点共识算法[J]. 信息网络安全, 2023, 23(9): 108-117. |
| [7] | 周权, 陈民辉, 卫凯俊, 郑玉龙. 基于SM9的属性加密的区块链访问控制方案[J]. 信息网络安全, 2023, 23(9): 37-46. |
| [8] | 赵佳豪, 蒋佳佳, 张玉书. 基于动态默克尔哈希树的跨链数据一致性验证模型[J]. 信息网络安全, 2023, 23(9): 95-107. |
| [9] | 邵震哲, 蒋佳佳, 赵佳豪, 张玉书. 面向跨链的改进加权拜占庭容错算法[J]. 信息网络安全, 2023, 23(8): 109-120. |
| [10] | 张伟, 李子轩, 徐晓瑀, 黄海平. SDP-CoAP:基于软件定义边界的安全增强CoAP通信框架设计[J]. 信息网络安全, 2023, 23(8): 17-31. |
| [11] | 覃思航, 代炜琦, 曾海燕, 顾显俊. 基于区块链的电力应用数据安全共享研究[J]. 信息网络安全, 2023, 23(8): 52-65. |
| [12] | 李志华, 王志豪. 基于LCNN和LSTM混合结构的物联网设备识别方法[J]. 信息网络安全, 2023, 23(6): 43-54. |
| [13] | 郭瑞, 魏鑫, 陈丽. 工业物联网环境下可外包的策略隐藏属性基加密方案[J]. 信息网络安全, 2023, 23(3): 1-12. |
| [14] | 李春晓, 王耀飞, 徐恩亮, 赵钰. 基于双线性映射的区块链安全范围搜索技术研究[J]. 信息网络安全, 2023, 23(3): 22-34. |
| [15] | 王晶宇, 马兆丰, 徐单恒, 段鹏飞. 支持国密算法的区块链交易数据隐私保护方案[J]. 信息网络安全, 2023, 23(3): 84-95. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||