信息网络安全 ›› 2024, Vol. 24 ›› Issue (2): 167-178.doi: 10.3969/j.issn.1671-1122.2024.02.001
面向物联网的入侵检测技术研究新进展
- 哈尔滨工程大学计算机科学与技术学院,哈尔滨 150000
-
收稿日期:2023-12-12出版日期:2024-02-10发布日期:2024-03-06 -
通讯作者:蒋舜鹏 E-mail:2545451677@qq.com -
作者简介:冯光升(1980—),男,山东,教授,博士,CCF高级会员,主要研究方向为网络技术与信息安全|蒋舜鹏(2001—),男,江西,博士研究生,CCF会员,主要研究方向为信息传播网络、网络安全|胡先浪(1982—),男,江苏,高级工程师,硕士,主要研究方向为入侵检测、物联网|马明宇(2000—),男,辽宁,硕士研究生,CCF会员,主要研究方向为网络技术与信息安全 -
基金资助:国家自然科学基金(62272126)
New Research Progress on Intrusion Detection Techniques for the Internet of Things
FENG Guangsheng, JIANG Shunpeng( ), HU Xianlang, MA Mingyu
), HU Xianlang, MA Mingyu
- College of Computer Science and Technology, Harbin Engineering University, Harbin 150000, China
-
Received:2023-12-12Online:2024-02-10Published:2024-03-06 -
Contact:JIANG Shunpeng E-mail:2545451677@qq.com
摘要:
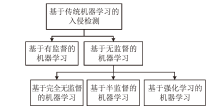
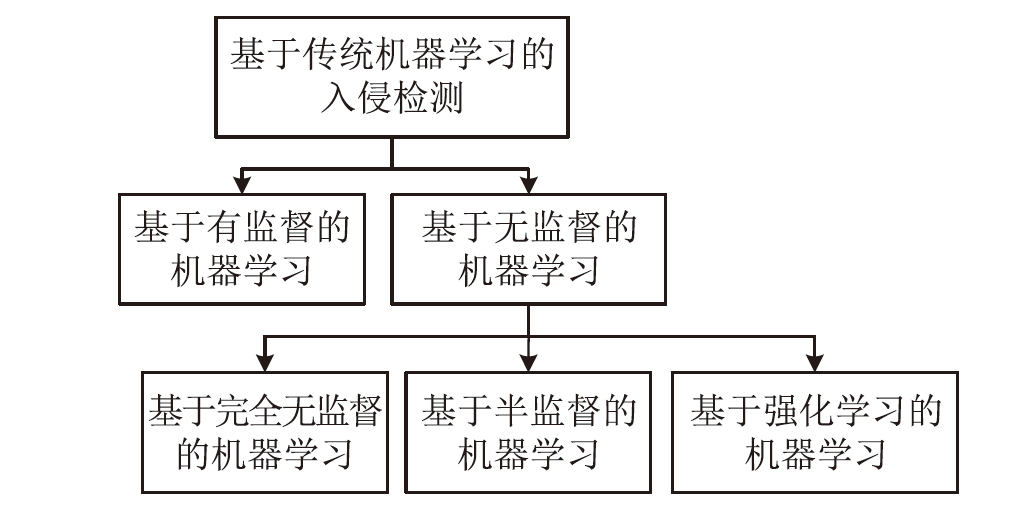
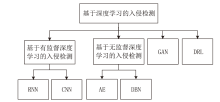
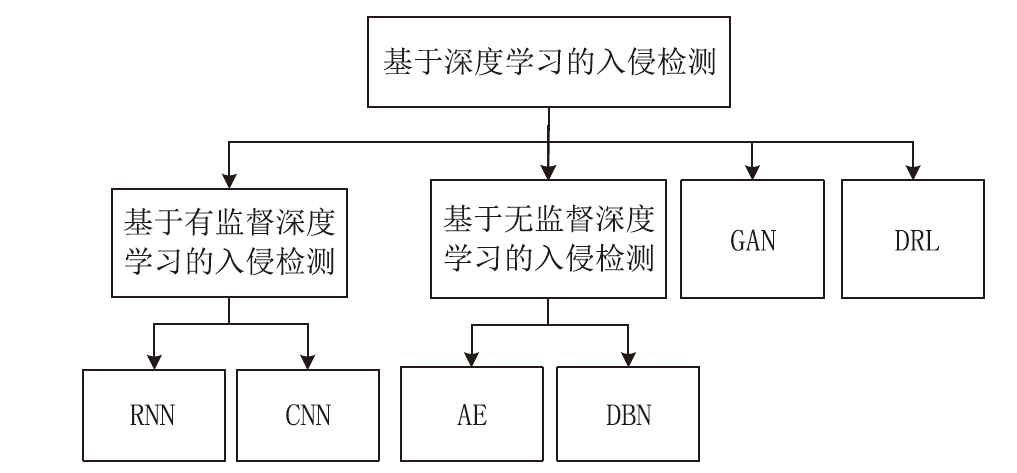
相较于传统入侵检测机制,智能化的入侵检测技术能够充分提取数据特征,具有更高的检测效率,但对数据样本标签的要求也更高。文章按数据样本标签从有监督和无监督角度对物联网入侵检测技术的最新进展进行综述。首先概述了基于签名的入侵检测方法,并基于有监督和无监督的分类分析了近期基于传统机器学习的入侵检测方法;然后分析了近期基于深度学习的入侵检测方法,分别对基于有监督、无监督、生成对抗网络和深度强化学习的入侵检测方法进行分析;最后分析总结了物联网入侵检测技术的研究挑战和未来的研究趋势。
中图分类号:
引用本文
冯光升, 蒋舜鹏, 胡先浪, 马明宇. 面向物联网的入侵检测技术研究新进展[J]. 信息网络安全, 2024, 24(2): 167-178.
FENG Guangsheng, JIANG Shunpeng, HU Xianlang, MA Mingyu. New Research Progress on Intrusion Detection Techniques for the Internet of Things[J]. Netinfo Security, 2024, 24(2): 167-178.
表2
常见的有监督机器学习技术对比
| 方案 | 数据集 | 机器学习方法 | 评价指标 |
|---|---|---|---|
| MANHAS[ | KDD99 | KNN、SVM、DT、朴素贝叶斯 | 准确率、灵敏度、精确度、F1分数 |
| VERMA[ | CIDDS-001、UNSWNB15、NSL-KDD | 随机森林、AdaBoost | 准确率、灵敏度、AUC、 检测率 |
| ABBAS[ | CICIDS2017 | 集成学习 | 准确率 |
| ABDALJABAR[ | DoH20 | KNN | 准确率、 检测率 |
| GUEZZAZ[ | NSL-KDD、CICIDS2017 | DT | 准确率、检测率、误报率 |
| KASONGO[ | UNSWNB15 | GA-RF | 准确率、AUC |
| KESERWANI[ | KDDCup99、NSL-KDD、CICIDS-2017 | GWO-PSO-RF | 准确率 |
| GU[ | UNSWNB15、CICIDS2017、NSL-KDD、Kyoto 2006+ | NB-SVM | 准确率、检测率、虚警率 |
| HAZMAN[ | BoT-IoT、IoT-23 | 集成学习 | 准确率、精确度、F1分数、误报率 |
| AHMAD[ | UNSWNB15 | RF、SVM、ANN | 准确率 |
| OKEY[ | CICIDS2017、CSE-CIC-IDS2018 | BoostedEnML | 准确率、精确度、AUC、F1分数 |
| 周杰英[ | UNSW-NB15 | RF-GBDT | 检测率、虚警率、F1分数、AUC |
表4
基于无监督机器学习的物联网IDS研究成果
| 方案 | 特点 | 评价指标 |
|---|---|---|
| MOHY-EDDINE[ | 采用PCA、单变量统计检验和遗传算法进行特征选择,以提高数据质量并选出k个表现最好的特征 | 准确率、检测率、虚警率、预测时间和误报率 |
| NASIR[ | 采用SpiderMonkey(SM)、PCA、信息增益和相关属性评价进行特征选择 | 准确率、F1分数、AUC-ROC值 |
| WAHAB[ | 利用PCA法分析数据流中特征方差的变化 | 准确率 |
| VADIGI[ | 所有智能体可通过注意力加权模型聚合过程从其他智能体可用数据的分布和模式中获益 | 准确率、精确度、假阳性率和AUC |
| RAMANA[ | 基于深度Q网络的深度神经网络集成强化学习,用于边缘云基础架构的入侵检测 | 准确率、精确度和 召回率 |
表5
有监督深度学习方案对比
| 方案 | 特点 | 数据集 | 评价指标 |
|---|---|---|---|
| CHEN[ | 多目标进化CNN,运行在物联网雾计算的雾节点上 | AWID、CIC-IDS2107 | 精确度、准确率、召回率、F1分数 |
| ALJUMAH[ | 时间CNN,整合了CNN和通用卷积的物联网入侵检测智能模型,解决了数据集不平衡问题 | Bot-IoT | 精确度、准确率、召回率、F1分数、 日志损失 |
| KAN[ | 自适应粒子群优化CNN,用于物联网入侵检测 | 开源数据集[ | 精确度、准确率、召回率、F1分数 |
| ROOPAK[ | 融合跳跃基因适应NSGA-II多目标优化方法和集成LSTM的CNN,用于数据降维和深度学习 | CICIDS2017 | 精确度、准确率、召回率、F1分数 |
| ALMIANI[ | 基于深度RNN的物联网IDS | NSL-KDD | 准确率、精确度、Mathew相关性、Cohen的Kappa系数 |
| SARAVANAN[ | 结合区块链的BbAB方案和优化的RNN | MED | 准确率、精确度、召回率、F1分数、检测率 |
| SAHEED[ | 基于DRNN和监督机器学习模型的IDS | CICIDS | 精确度、召回率、F1分数 |
| ALIMI[ | RLSTM模型 | CICIDS-2017、NSL-KDS | 精确度、召回率、F1分数 |
| IMRANA[ | BiDLSTM模型 | NSL-KDD | 精确度、准确率、召回率、F1分数 |
| HANAFI[ | 基于改进的二进制Golden Jackal优化算法和LSTM网络的IDS | NSL-KDD、CICIDS2017 | 精确度、准确率、召回率、F1分数 |
| DEORE[ | 基于黑猩猩鸡群优化的深度LSTM,强调CNN的特征提取和LSTM的检测性能 | NSL-KDD、BoT-IoT | 准确率、敏感度 |
表6
无监督深度学习方案对比
| 方案 | 针对问题 | 评价指标 | 数据集 |
|---|---|---|---|
| MUHAMMAD[ 等人 | 入侵者冒充有效服务提供商的网络 攻击问题 | 准确率 | KDDCUP99、NSL-KDD、aegean WiFi入侵数据集 |
| ABOELWAFA[ 等人 | 物联网中的虚假数据注入(FDI) 攻击 | 准确率 | — |
| SINGH[ | 增加IDS的可靠性,减少IDS的 负担 | 分类准确率、云服务器的延迟、工作负载 | — |
| ELMASRY[ | 因IDS训练数据冗余和不相关特征导致检测率低的问题 | 检测率、 误报率 | — |
| LUNARDI[ | 异构IP连接设备数量和流量增加导致信息漏洞的问题 | 准确率 | — |
| CHEN[ | 基于机器学习的NBAD方法对网络行为分类不灵活、准确率低的问题 | 准确率 | — |
| WANG[ | 云计算环境下网络流量大规模、高维度、高冗余的问题 | 检测性能 | KDDCUP99、 NSL-KDD |
| LU[ | 入侵检测方法误报率高、检测准确率低的问题 | 准确率 | — |
表7
基于GAN的入侵检测方案对比
| 方案 | 面向问题 | 特点 | 数据集 |
|---|---|---|---|
| EGBAD | 证明在非图像层面GAN表现良好 | — | KDDCUP99 |
| GIDS | — | 实现实际部署 | 车载网 |
| 具有精细损失函数的半监督IDS | GAN-IDS不适合处理离散特征 | — | KDDCUP99 |
| MAD-GAN | 现实情况中攻击具有高动态复杂性 | 对多元时间序列进行攻击检测 | SWaT、WADI |
| MAGNETO | 恶意流量与正常流量相比存在不平衡问题 | 具有较高鲁棒性 | 基准数据集 |
| 过采样IDS | 数据不平衡 | 利用WGAN-GP进行建模,通过方差分析进行降维 | NSL-KDD、UNSW-NB15、CICIDS-2017 |
| BiCirGAN | 在离散高维特征的不平衡数据集上检测精确度低和泛化能力差 | — | KDD99、UNSW-NB15、WSN_DS |
| MemFGAN | 在异常样本有限时存在精确度低和容易产生过拟合问题 | 为生成器和判别器设计新的训练目标 | MAWILab、ISCX2012、IDS2017、IDS2018 |
| 安全联邦蒸馏GAN-IDS | 敏感信息保密必要性导致的数据孤岛问题 | 基于Wasserstein距离、EC-GAN | WSTS、AWID |
| TMG-GAN | — | 多生成器结构 | CICIDS2017、UNSW-NB15 |
| 改进CGAN-IDS | CGAN中两类样本重叠导致生成器梯度消失的不稳定问题 | 构建WCGAN-SVM工控系统入侵检测模型 | UCI、SWaT |
表8
基于DRL的入侵检测方案对比
| 方案 | 面向问题 | 使用的方法 | 评价指标 |
|---|---|---|---|
| HSU[ | 具有自我更新的能力,检测异常网络流量 | 基于DRL的异常网络IDS | 准确率、召回率和精确度 |
| PRIYA[ | 自动化和智能的网络ID策略,应对高级攻击者 | 基于二进制蝙蝠算法的特征选择和DRL(BBAFS-DRL)系统 | ROC、呈现率 |
| ALAVIZADEH[ | 持续自动学习,检测不同类型 网络入侵 | 结合基于Q学习的强化学习与深度前馈神经网络方法的网络入侵检测 | 准确率 |
| 李贝贝[ | 有效检测工业物联网多种类型 网络攻击 | 基于DRL算法的工业物联网IDS | 准确率、精确度、召回率、F1分数 |
| 李自若[ | 针对IEC 61850和物联网协议的异常检测 | 构建智能变电站自动化网络架构,明确制造报文规范、GOOSE协议、SV报文、MQTT协议和CoAP协议的使用范围 | 误报率 |
| WANG[ | 高连接性和海量设备导致的广泛安全威胁、漏洞和隐私问题 | 基于DRL的入侵检测策略 | 准确率、精确度、召回率、F1分数 |
| [1] | HASAN K F, KAUR T, HASAN M M, et al. Cognitive Internet of Vehicles: Motivation, Layered Architecture and Security Issues[C]//IEEE. 2019 International Conference on Sustainable Technologies for Industry 4.0(STI). New York: IEEE, 2019: 1-6. |
| [2] |
SISINNI E, SAIFULLAH A, HAN S, et al. Industrial Internet of Things: Challenges, Opportunities, and Directions[J]. IEEE Transactions on Industrial Informatics, 2018, 14(11): 4724-4734.
doi: 10.1109/TII.2018.2852491 URL |
| [3] | ABDALJABAR Z H, UCAN O N, ALHEETI K M A. An Intrusion Detection System for IoT Using KNN and Decision-Tree Based Classification[C]// IEEE. 2021 International Conference of Modern Trends in Information and Communication Technology Industry(MTICTI). New York:IEEE, 2021: 1-5. |
| [4] | GUEZZAZ A, BENKIRANE S, AZROUR M, et al. A Reliable Network Intrusion Detection Approach Using Decision Tree with Enhanced Data Quality[EB/OL]. (2021-01-01)[2023-10-12]. https://doi.org/10.1155/2021/1230593. |
| [5] |
KASONGO S M. An Advanced Intrusion Detection System for IIoT Based on GA and Tree Based Algorithms[J]. IEEE Access, 2021, 9: 113199-113212.
doi: 10.1109/ACCESS.2021.3104113 URL |
| [6] | SABA T, SADAD T, REHMAN A, et al. Intrusion Detection System through Advance Machine Learning for the Internet of Things Networks[J]. IT Professional, 2021, 23(2): 58-64. |
| [7] |
KESERWANI P K, GOVIL M C, PILLI E S, et al. A Smart Anomaly-Based Intrusion Detection System for the Internet of Things(IoT) Network Using GWO-PSO-RF Model[J]. Journal of Reliable Intelligent Environments, 2021, 7: 3-21.
doi: 10.1007/s40860-020-00126-x |
| [8] | ZHOU Jieying, HE Pengfei, QIU Rongfa, et al. Research on Intrusion Detection Based on Random Forest and Gradient Boosting Tree[J]. Journal of Software, 2021, 32(10): 3254-3265. |
| 周杰英, 贺鹏飞, 邱荣发, 等. 融合随机森林和梯度提升树的入侵检测研究[J]. 软件学报, 2021, 32(10):3254-3265. | |
| [9] | GU Jie, LU Shan. An Effective Intrusion Detection Approach Using SVM with Naïve Bayes Feature Embedding[EB/OL]. (2021-04-01)[2023-10-12]. https://doi.org/10.1016/j.cose.2020.102158. |
| [10] | AHMAD M, RIAZ Q, ZEESHAN M, et al. Intrusion Detection in Internet of Things Using Supervised Machine Learning Based on Application and Transport Layer Features Using UNSW-NB15 Data-Set[J]. EURASIP Journal on Wireless Communications and Networking, 2021(1): 1-23. |
| [11] | SARHAN M, LAYEGHY S, MOUSTAFA N, et al. Feature Extraction for Machine Learning-Based Intrusion Detection in IoT networks[EB/OL]. (2022-09-07)[2023-10-12]. https://www.sciencedirect.com/science/article/pii/S2352864822001754. |
| [12] | MANHAS J, KOTWAL S. Implementation of Intrusion Detection System for Internet of Things Using Machine Learning Techniques[EB/OL]. (2021-01-12)[2023-10-12]. https://doi.org/10.1007/978-981-15-8711-5_11. |
| [13] |
VERMA A, RANGA V. Machine Learning Based Intrusion Detection Systems for IoT Applications[J]. Wireless Personal Communications, 2020, 111: 2287-2310.
doi: 10.1007/s11277-019-06986-8 |
| [14] |
HAZMAN C, GUEZZAZ A, BENKIRANE S, et al. lIDS-SIoEL: Intrusion Detection Framework for IoT-Based Smart Environments Security Using Ensemble Learning[J]. Cluster Computing, 2023, 26(6): 4069-4083.
doi: 10.1007/s10586-022-03810-0 |
| [15] |
ABBAS A, KHAN M A, LATIF S, et al. A New Ensemble-Based Intrusion Detection System for Internet of Things[J]. Arabian Journal for Science and Engineering, 2022, 47: 1805-1819.
doi: 10.1007/s13369-021-06086-5 |
| [16] | OKEY O D, MAIDIN S S, ADASME P, et al. BoostedEnML: Efficient Technique for Detecting Cyberattacks in IoT Systems Using Boosted Ensemble Machine Learning[EB/OL]. (2022-09-19)[2023-10-12]. https://doi.org/10.3390/s22197409. |
| [17] | HAN Weixiang, PENG Jialiang, YU Jiahua, et al. Heterogeneous Data-Aware Federated Learning for Intrusion Detection Systems via Meta-Sampling in Artificial Intelligence of Things[EB/OL]. (2020-11-12)[2023-10-12]. https://doi.org/10.48550/arXiv.2011.06393. |
| [18] | SHAN Yao, YAO Yu, ZHOU Xiaoming, et al. CFL-IDS: An Effective Clustered Federated Learning Framework for Industrial Internet of Things Intrusion Detection[EB/OL]. (2023-10-13)[2023-11-12]. https://ieeexplore.ieee.org/document/10285326. |
| [19] | WEN Weiping, HU Yezhou, ZHAO Guoliang, et al. Design and Implementation of an Abnormal IP Identification System Based on Traffic Feature Classification[J]. Netinfo Security, 2021, 21(8): 1-9. |
| 文伟平, 胡叶舟, 赵国梁, 等. 基于流量特征分类的异常IP识别系统的设计与实现[J]. 信息网络安全, 2021, 21(8):1-9. | |
| [20] |
MOHY-EDDINE M, GUEZZAZ A, BENKIRANE S, et al. An Efficient Network Intrusion Detection Model for IoT Security Using K-NN Classifier and Feature Selection[J]. Multimedia Tools and Applications, 2023, 82: 23615-23633.
doi: 10.1007/s11042-023-14795-2 |
| [21] |
ABDELMOUMIN G, RAWAT D B, RAHMAN A. On the Performance of Machine Learning Models for Anomaly-Based Intelligent Intrusion Detection Systems for the Internet of Things[J]. IEEE Internet of Things Journal, 2021, 9(6): 4280-4290.
doi: 10.1109/JIOT.2021.3103829 URL |
| [22] |
WAHAB O A. Intrusion Detection in the IoT under Data and Concept Drifts: Online Deep Learning Approach[J]. IEEE Internet of Things Journal, 2022, 9(20): 19706-19716.
doi: 10.1109/JIOT.2022.3167005 URL |
| [23] |
NASIR M, JAVED A R, TARIQ M A, et al. Feature Engineering and Deep Learning-Based Intrusion Detection Framework for Securing Edge IoT[J]. The Journal of Supercomputing, 2022, 78: 8852-8866.
doi: 10.1007/s11227-021-04250-0 |
| [24] |
ASHFAQ R A R, WANG Xizhao, HUANG J Z, et al. Fuzziness Based Semi-Supervised Learning Approach for Intrusion Detection System[J]. Information Sciences, 2017, 378: 484-497.
doi: 10.1016/j.ins.2016.04.019 URL |
| [25] | LI Wenjuan, MENG Weizhi, AU M H. Enhancing Collaborative Intrusion Detection via Disagreement-Based Semi-Supervised Learning in IoT Environments[J]. Journal of Network and Computer Applications, 2020, 161: 1-12. |
| [26] |
ZHAO Ruijie, WANG Yijun, XUE Zhi, et al. Semi-Supervised Federated Learning Based Intrusion Detection Method for Internet of Things[J]. IEEE Internet of Things Journal, 2022, 10: 8645-8657.
doi: 10.1109/JIOT.2022.3175918 URL |
| [27] | VADIGI S, SETHI K, MOHANTY D, et al. Federated Reinforcement Learning Based Intrusion Detection System Using Dynamic Attention Mechanism[J]. Journal of Information Security and Applications, 2023, 78: 1-15. |
| [28] |
RAMANA T, THIRUNAVUKKARASAN M, MOHAMMED A S, et al. Ambient Intelligence Approach: Internet of Things Based Decision Performance Analysis for Intrusion Detection[J]. Computer Communications, 2022, 195: 315-322.
doi: 10.1016/j.comcom.2022.09.007 URL |
| [29] | CHEN Yi, LIN Qiuzhen, WEI Wenhong, et al. Intrusion Detection Using Multi-Objective Evolutionary Convolutional Neural Network for Internet of Things in Fog Computing[J]. Knowledge-Based Systems, 2022, 244: 1-14. |
| [30] | ALJUMAH A. IoT-Based Intrusion Detection System Using Convolution Neural Networks[J]. PeerJ Computer Science, 2021, 7: 1-19. |
| [31] |
KAN Xiu, FAN Yixuan, FANG Zhijun, et al. A Novel IoT Network Intrusion Detection Approach Based on Adaptive Particle Swarm Optimization Convolutional Neural Network[J]. Information Sciences, 2021, 568: 147-162.
doi: 10.1016/j.ins.2021.03.060 URL |
| [32] | ROOPAK M, TIAN G Y, CHAMBERS J. An Intrusion Detection System Against DDoS Attacks in IoT Networks[C]// IEEE. 2020 10th Annual Computing and Communication Workshop and Conference(CCWC). New York:IEEE, 2020: 562-567. |
| [33] | ALMIANI M, ABUGHAZLEH A, AL-RAHAYFEH A, et al. Deep Recurrent Neural Network for IoT Intrusion Detection System[J]. Simulation Modelling Practice and Theory, 2020, 101: 1-20. |
| [34] | SARAVANAN V, MADIAJAGAN M, RAFEE S M, et al. IoT-Based Blockchain Intrusion Detection Using Optimized Recurrent Neural Network[EB/OL]. (2023-09-16)[2023-10-12]. https://link.springer.com/article/10.1007/s11042-023-16662-6. |
| [35] |
SAHEED Y K, AROWOLO M O. Efficient Cyber Attack Detection on the Internet of Medical Things-Smart Environment Based on Deep Recurrent Neural Network and Machine Learning Algorithms[J]. IEEE Access, 2021, 9: 161546-161554.
doi: 10.1109/ACCESS.2021.3128837 URL |
| [36] |
ALIMI A, OUAHADA K, ABU-MAHFOUZ A M, et al. Refined LSTM Based Intrusion Detection for Denial-of-Service Attack in Internet of Things[J]. Journal of Sensor and Actuator Networks, 2022, 11(3): 1-14.
doi: 10.3390/jsan11010001 URL |
| [37] | HANAFI A V, GHAFFARI A, REZAEI H, et al. Intrusion Detection in Internet of Things Using Improved Binary Golden Jackal Optimization Algorithm and LSTM[EB/OL]. (2023-08-25)[2023-10-12]. https://link.springer.com/article/10.1007/s10586-023-04102-x. |
| [38] |
DEORE B, BHOSALE S. Hybrid Optimization Enabled Robust CNN-LSTM Technique for Network Intrusion Detection[J]. IEEE Access, 2022, 10: 65611-65622.
doi: 10.1109/ACCESS.2022.3183213 URL |
| [39] | YAIR Meidan. Detection_of_IoT_Botnet_Attacks_N_BaIoT.[EB/OL]. (2018-03-18)[2023-10-12]. http://archive.ics.uci.edu/dataset/442/detection+of+iot+botnet+attacks+n+baiot. |
| [40] | IMRANA Y, XIANG Y, ALI L, et al. A Bidirectional LSTM Deep Learning Approach for Intrusion Detection[EB/OL]. (2021-12-15)[2023-10-12]. https://doi.org/10.1016/j.eswa.2021.115524. |
| [41] |
ABOELWAFA M M, SEDDIK K G, ELDEFRAWY M H, et al. A Machine-Learning-Based Technique for False Data Injection Attacks Detection in Industrial IoT[J]. IEEE Internet of Things Journal, 2020, 7(9): 8462-8471.
doi: 10.1109/JIoT.6488907 URL |
| [42] |
LUNARDI W T, LOPEZ M A, GIACALONE J P. Arcade: Adversarially Regularized Convolutional Autoencoder for Network Anomaly Detection[J]. IEEE Transactions on Network and Service Management, 2022, 20(2): 1305-1318.
doi: 10.1109/TNSM.2022.3229706 URL |
| [43] |
WANG Wenjuan, DU Xuehui, SHAN Dibin, et al. Cloud Intrusion Detection Method Based on Stacked Contractive Auto-Encoder and Support Vector Machine[J]. IEEE Transactions on Cloud Computing, 2020, 10(3): 1634-1646.
doi: 10.1109/TCC.2020.3001017 URL |
| [44] |
LU Huimin, WANG Tian, XU Xing, et al. Cognitive Memory-Guided Autoencoder for Effective Intrusion Detection in Internet of Things[J]. IEEE Transactions on Industrial Informatics, 2021, 18(5): 3358-3366.
doi: 10.1109/TII.2021.3102637 URL |
| [45] |
ALMOGREN A S. Intrusion Detection in Edge-of-Things Computing[J]. Journal of Parallel and Distributed Computing, 2020, 137: 259-265.
doi: 10.1016/j.jpdc.2019.12.008 URL |
| [46] |
LU Kangdi, ZENG Guoqing, LUO Xiaozhao, et al. Evolutionary Deep Belief Network for Cyber-Attack Detection in Industrial Automation and Control System[J]. IEEE Transactions on Industrial Informatics, 2021, 17(11): 7618-7627.
doi: 10.1109/TII.2021.3053304 URL |
| [47] | ELMASRY W, AKBULUT A, ZAIM A H. Evolving Deep Learning Architectures for Network Intrusion Detection Using a Double PSO Metaheuristic[EB/OL]. (2020-02-26)[2023-10-14]. https://doi.org/10.1016/j.comnet.2019.107042. |
| [48] | CHEN Aiguo, FU Yang, ZHENG Xu, et al. An Efficient Network Behavior Anomaly Detection Using a Hybrid DBN-LSTM Network[EB/OL]. (2022-03-15)[2023-10-12]. https://doi.org/10.1016/j.cose.2021.102600. |
| [49] |
MUHAMMAD G, HOSSAIN M S, GARG S. Stacked Autoencoder-Based Intrusion Detection System to Combat Financial Fraudulent[J]. IEEE Internet of Things Journal, 2023, 10(3): 2071-2078.
doi: 10.1109/JIOT.2020.3041184 URL |
| [50] |
SINGH P, KAUR A, AUJLA G S, et al. Daas: Dew Computing as a Service for Intelligent Intrusion Detection in Edge-of-Things Ecosystem[J]. IEEE Internet of Things Journal, 2021, 8(16): 12569-12646.
doi: 10.1109/JIOT.2020.3029248 URL |
| [51] | SCHLEGL T, SEEBÖCK P, WALDSTEIN S M, et al. Unsupervised Anomaly Detection with Generative Adversarial Networks to Guide Marker Discovery[C]// Springer. The 25th International Conference on Information Processing in Medical Imaging. Heidelberg: Springer, 2017: 146-157. |
| [52] | ZENATI H, FOO C S, LECOUAT B, et al. Efficient Gan-Based Anomaly Detection[EB/OL]. (2019-05-01)[2023-10-22]. https://arxiv.org/pdf/1802.06222.pdf. |
| [53] | SEO E, SONG H M, KIM H K. GIDS: GAN Based Intrusion Detection System for In-Vehicle Network[C]// IEEE. 2018 16th Annual Conference on Privacy, Security and Trust(PST). New York:IEEE, 2018: 1-6. |
| [54] | CHEN Hongyu, JIANG Li. Efficient GAN-Based Method for Cyber-Intrusion Detection[EB/OL]. (2019-07-24)[2023-10-22]. https://arxiv.org/abs/1904.02426. |
| [55] |
LIU Yongmin, YANG Yujin, LUO Haoyi, et al. Intrusion Detection Method for Wireless Sensor Network Based on Bidirectional Circulation Generative Adversarial Network[J]. Journal of Computer Applications, 2023, 43(1): 160-168.
doi: 10.11772/j.issn.1001-9081.2021112001 |
|
刘拥民, 杨钰津, 罗皓懿, 等. 基于双向循环生成对抗网络的无线传感网入侵检测方法[J]. 计算机应用, 2023, 43(1):160-168.
doi: 10.11772/j.issn.1001-9081.2021112001 |
|
| [56] | ZHANG Huiyan, LIANG Yong, LAN Jinghong, et al. Intrusion Detection Method Based on a Memory Module and a Filtered Generative Adversarial Network[EB/OL]. (2023-11-15)[2023-11-20]. https://doi.org/10.19678/j.issn.1000-3428.0068157. |
| 张慧妍, 梁勇, 兰景宏, 等. 基于记忆模块和过滤式生成对抗网络的入侵检测方法[EB/OL]. (2023-11-15)[2023-11-20]. https://doi.org/10.19678/j.issn.1000-3428.0068157. | |
| [57] |
DING Hongwei, SUN Yu, HUANG Nana, et al. TMG-GAN: Generative Adversarial Networks-Based Imbalanced Learning for Network Intrusion Detection[J]. IEEE Transactions on Information Forensics and Security, 2023, 19: 1156-1167.
doi: 10.1109/TIFS.2023.3331240 URL |
| [58] | HSU Y F, MATSUOKA M. A Deep Reinforcement Learning Approach for Anomaly Network Intrusion Detection System[C]// IEEE. 2020 IEEE 9th International Conference on Cloud Networking(CloudNet). New York:IEEE, 2020: 1-6. |
| [59] | PRIYA S, KUMAR K. Feature Selection with Deep Reinforcement Learning for Intrusion Detection System[J]. Computer Systems Science & Engineering, 2023, 46(3): 3339-3353. |
| [60] |
ALAVIZADEH H, ALAVIZADEH H, JANG-JACCARD J. Deep Q-Learning Based Reinforcement Learning Approach for Network Intrusion Detection[J]. Computers, 2022, 11(3): 41-59.
doi: 10.3390/computers11030041 URL |
| [61] |
LI Beibei, SONG Jiarui, DU Qingyun, et al. DRL-IDS: Deep Reinforcement Learning-Based Intrusion Detection System for Industrial Internet of Things[J]. Computer Science, 2021, 48(7): 47-54.
doi: 10.11896/jsjkx.210400021 |
|
李贝贝, 宋佳芮, 杜卿芸, 等. DRL-IDS:基于深度强化学习的工业物联网入侵检测系统[J]. 计算机科学, 2021, 48(7):47-54.
doi: 10.11896/jsjkx.210400021 |
|
| [62] | LI Ziruo, SHEN Xi, ZHANG Yibing, et al. Network Anomaly Detection Method for Smart Substation Based on Deep Reinforcement Learning[J]. Southern Power System Technology, 2021, 15(6): 98-105. |
| 李自若, 沈曦, 张亦兵, 等. 基于深度强化学习的智慧变电站网络异常检测方法[J]. 南方电网技术, 2021, 15(6):98-105. | |
| [63] | WANG Zhihao, JIANG Dingde, LV Zhihan, et al. A Deep Reinforcement Learning Based Intrusion Detection Strategy for Smart Vehicular Networks[C]// IEEE. INFOCOM 2022-IEEE Conference on Computer Communications Workshops(INFOCOM WKSHPS). New York:IEEE, 2022: 1-6. |
| [64] | RIZZARDI A, SICARI S, PORISINI A C. Deep Reinforcement Learning for Intrusion Detection in Internet of Things: Best Practices, Lessons Learnt, and Open Challenges[EB/OL]. (2023-10-10)[2023-11-12]. https://doi.org/10.1016/j.comnet.2023.110016. |
| [1] | 翟鹏, 何泾沙, 张昱. 物联网环境下基于SM9算法和区块链技术的身份认证方法[J]. 信息网络安全, 2024, 24(2): 179-187. |
| [2] | 赵鹏程, 于俊清, 李冬. 一种基于深度学习的SRv6网络流量调度优化算法[J]. 信息网络安全, 2024, 24(2): 272-281. |
| [3] | 金志刚, 丁禹, 武晓栋. 融合梯度差分的双边校正联邦入侵检测算法[J]. 信息网络安全, 2024, 24(2): 293-302. |
| [4] | 孙红哲, 王坚, 王鹏, 安雨龙. 基于Attention-BiTCN的网络入侵检测方法[J]. 信息网络安全, 2024, 24(2): 309-318. |
| [5] | 王君艳, 伊鹏, 贾洪勇, 张建辉. 基于改进CAE的物联网终端风险评估模型[J]. 信息网络安全, 2024, 24(1): 150-159. |
| [6] | 宋玉涵, 祝跃飞, 魏福山. 一种基于AdaBoost模型的区块链异常交易检测方案[J]. 信息网络安全, 2024, 24(1): 24-35. |
| [7] | 薛羽, 张逸轩. 深层神经网络架构搜索综述[J]. 信息网络安全, 2023, 23(9): 58-74. |
| [8] | 王鹃, 张冲, 龚家新, 李俊娥. 基于机器学习的模糊测试研究综述[J]. 信息网络安全, 2023, 23(8): 1-16. |
| [9] | 张伟, 李子轩, 徐晓瑀, 黄海平. SDP-CoAP:基于软件定义边界的安全增强CoAP通信框架设计[J]. 信息网络安全, 2023, 23(8): 17-31. |
| [10] | 沈华, 田晨, 郭森森, 慕志颖. 基于对抗性机器学习的网络入侵检测方法研究[J]. 信息网络安全, 2023, 23(8): 66-75. |
| [11] | 彭翰中, 张珠君, 闫理跃, 胡成林. 联盟链下基于联邦学习聚合算法的入侵检测机制优化研究[J]. 信息网络安全, 2023, 23(8): 76-85. |
| [12] | 许春根, 薛少康, 徐磊, 张盼. 基于安全两方计算的高效神经网络推理协议[J]. 信息网络安全, 2023, 23(7): 22-30. |
| [13] | 刘宇啸, 陈伟, 张天月, 吴礼发. 基于稀疏自动编码器的可解释性异常流量检测[J]. 信息网络安全, 2023, 23(7): 74-85. |
| [14] | 蒋英肇, 陈雷, 闫巧. 基于双通道特征融合的分布式拒绝服务攻击检测算法[J]. 信息网络安全, 2023, 23(7): 86-97. |
| [15] | 李志华, 王志豪. 基于LCNN和LSTM混合结构的物联网设备识别方法[J]. 信息网络安全, 2023, 23(6): 43-54. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||