信息网络安全 ›› 2024, Vol. 24 ›› Issue (7): 1015-1026.doi: 10.3969/j.issn.1671-1122.2024.07.004
工业物联网系统基于混沌映射三因素认证与密钥协商协议
张晓均1,2( ), 张楠1,2, 郝云溥1,2, 王周阳1,2, 薛婧婷1,2
), 张楠1,2, 郝云溥1,2, 王周阳1,2, 薛婧婷1,2
- 1.西南石油大学计算机与软件学院,成都 610500
2.西南石油大学四川省油气勘探开发智能化工程研究中心,成都 610500
-
收稿日期:2024-04-17出版日期:2024-07-10发布日期:2024-08-02 -
通讯作者:张晓均zhangxjdzkd2012@163.com -
作者简介:张晓均(1985—),男,四川,副教授,博士,CCF会员,主要研究方向为密码学与信息安全|张楠(1999—),男,河北,硕士研究生,主要研究方向为密码学与工业信息安全|郝云溥(2000—),男,河北,硕士研究生,主要研究方向为密码学与数据安全|王周阳(2001—),男,四川,硕士研究生,主要研究方向为密码学与车联网安全|薛婧婷(1990—),女,四川,讲师,博士,主要研究方向为密码学与区块链。 -
基金资助:国家自然科学基金(61902327);四川省自然科学基金(2023NSFSC1398);中国博士后科学基金(2020M681316);油气勘探开发软件国家工程研究中心开放课题(DFWT-ZYRJ-2024-JS-81)
Three-Factor Authentication and Key Agreement Protocol Based on Chaotic Map for Industrial Internet of Things Systems
ZHANG Xiaojun1,2( ), ZHANG Nan1,2, HAO Yunpu1,2, WANG Zhouyang1,2, XUE Jingting1,2
), ZHANG Nan1,2, HAO Yunpu1,2, WANG Zhouyang1,2, XUE Jingting1,2
- 1. School of Computer Science and Software Engineering, Southwest Petroleum University, Chengdu 610500, China
2. Engineering Research Center for Intelligent Oil & Gas Exploration and Development of Sichuan Province, Southwest Petroleum University, Chengdu 610500, China
-
Received:2024-04-17Online:2024-07-10Published:2024-08-02
摘要:
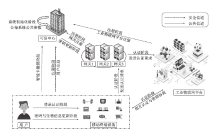
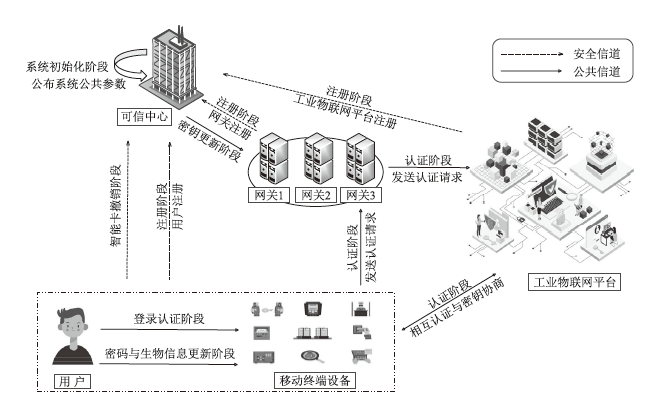
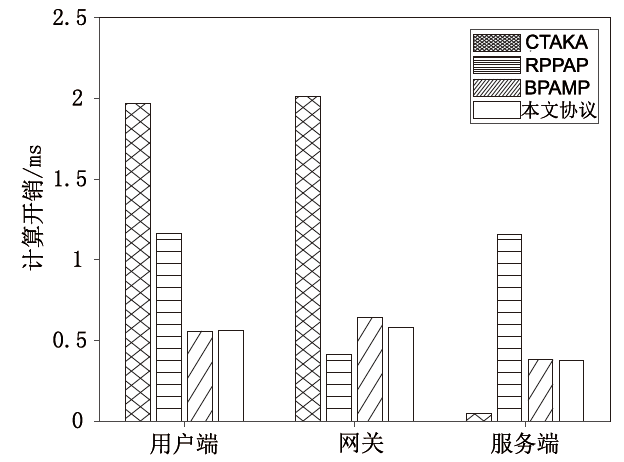
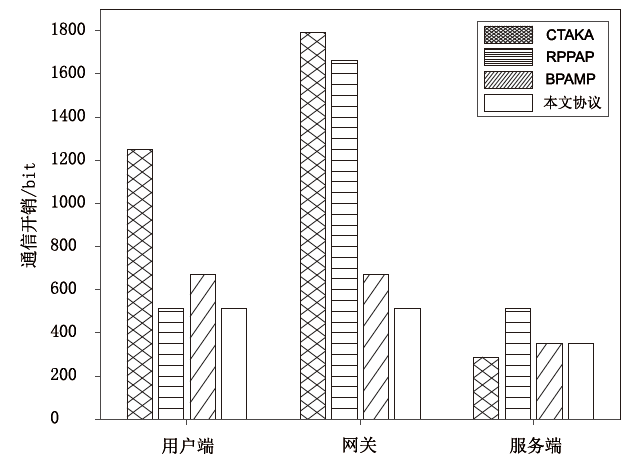
工业物联网系统通过各类终端传感器设备,将采集的关键工业数据实时传输到工业物联网平台,提供数据智能分析与决策。然而,对工业数据的非法访问将导致数据或敏感身份标识泄露、数据篡改等信息安全问题,影响工业物联网系统的正常运行。基于此,文章面向工业物联网系统,搭建多用户、多网关、多工业物联网平台下的分布式数据匿名传输架构,提出基于混沌映射的三因素认证与密钥协商协议。协议实现了用户到移动终端设备的智能卡、口令、生物特征信息的三因素登录认证。在网关协助下,用户利用移动终端设备,基于混沌映射技术与关键凭证,实现了用户到工业物联网平台的双向匿名认证,并协商了用于后续保密通信的会话密钥。文章对协议进行了应用拓展,包括用户口令与生物特征信息的更新、智能卡撤销的功能,基于中国剩余定理实现了对多网关的密钥同步更新。安全性分析与性能评估表明,该设计协议能够安全高效地部署在工业物联网系统。
中图分类号:
引用本文
张晓均, 张楠, 郝云溥, 王周阳, 薛婧婷. 工业物联网系统基于混沌映射三因素认证与密钥协商协议[J]. 信息网络安全, 2024, 24(7): 1015-1026.
ZHANG Xiaojun, ZHANG Nan, HAO Yunpu, WANG Zhouyang, XUE Jingting. Three-Factor Authentication and Key Agreement Protocol Based on Chaotic Map for Industrial Internet of Things Systems[J]. Netinfo Security, 2024, 24(7): 1015-1026.
使用本文
表1
符号描述
| 符号 | 描述 | 符号 | 描述 |
|---|---|---|---|
| 系统私钥和公钥 | 单向哈希 函数 | ||
| 网关身份 标识 | 网关的 共同密钥 | ||
| 平台身份 标识 | 用户身份标识 | ||
| 用户登录 口令 | 生物特征 信息 | ||
| 生成函数和再生函数 | 生物密钥和公共信息 | ||
| 随机数 | 凭证 | ||
| 混沌映射 变量 | 哈希值 | ||
| 盲化值 | 协商的密钥 | ||
| 时间戳 | 智能卡 |
| [1] |
LU Yang, XU Lida. Internet of Things (IoT) Cybersecurity Research: A Review of Current Research Topics[J]. IEEE Internet of Things Journal, 2019, 6(2): 2103-2115.
doi: 10.1109/JIOT.2018.2869847 |
| [2] | ZUO Yanjun, QI Zhenyu. A Blockchain-Based IoT Framework for Oil Field Remote Monitoring and Control[J]. IEEE Access, 2022, 10: 2497-2514. |
| [3] | LI Na, MA Maode, WANG Hui. ASAP-IIoT: An Anonymous Secure Authentication Protocol for Industrial Internet of Things[J]. Sensors, 2024, 24(4): 1243-1265. |
| [4] | CHAUDHRY S A, YAHYA K, GARG S, et al. LAS-SG: An Elliptic Curve-Based Lightweight Authentication Scheme for Smart Grid Environments[J]. IEEE Transactions on Industrial Informatics, 2023, 19(2): 1504-1511. |
| [5] | CHENG Leixiao, MENG Fei. Certificateless Public Key Authenticated Searchable Encryption with Enhanced Security Model in IIoT Applications[J]. IEEE Internet of Things Journal, 2023, 10(2): 1391-1400. |
| [6] | LIU Suhui, CHEN Liquan, YU Hongtao, et al. BP-AKAA: Blockchain-Enforced Privacy-Preserving Authentication and Key Agreement and Access Control for IIoT[J]. Journal of Information Security and Applications, 2023, 73: 103443-103454. |
| [7] | ZHOU Xiaotong, HE Debiao, NING Jianting, et al. Single-Server Public-Key Authenticated Encryption with Keyword Search and Its Application in IIoT[J]. IEEE Transactions on Network Science and Engineering, 2024, 11(1): 404-415. |
| [8] | KARATI A, ISLAM S H, KARUPPIAH M. Provably Secure and Lightweight Certificateless Signature Scheme for IIoT Environments[J]. IEEE Transactions on Industrial Informatics, 2018, 14(8): 3701-3711. |
| [9] | ZHANG Yinghui, DENG R H, ZHENG Dong, et al. Efficient and Robust Certificateless Signature for Data Crowdsensing in Cloud-Assisted Industrial IoT[J]. IEEE Transactions on Industrial Informatics, 2019, 15(9): 5099-5108. |
| [10] | XIONG Hu, WU Yan, JIN Chuanjie, et al. Efficient and Privacy-Preserving Authentication Protocol for Heterogeneous Systems in IIoT[J]. IEEE Internet of Things Journal, 2020, 7(12): 11713-11724. |
| [11] | CUI Jie, WANG Fengqun, ZHANG Qingyang, et al. Efficient Batch Authentication Scheme Based on Edge Computing in IIoT[J]. IEEE Transactions on Network and Service Management, 2023, 20(1): 357-368. |
| [12] | DONG Jingnan, XU Guangxia, MA Chuang, et al. Blockchain-Based Certificate-Free Cross-Domain Authentication Mechanism for Industrial Internet[J]. IEEE Internet of Things Journal, 2024, 11(2): 3316-3330. |
| [13] | CUI Jie, CHENG Fangzheng, ZHONG Hong, et al. Multi-Factor Based Session Secret Key Agreement for the Industrial Internet of Things[J]. Ad Hoc Networks, 2023, 138: 102997-103009. |
| [14] | YANG Jenho. A Multi-Gateway Authentication and Key-Agreement Scheme on Wireless Sensor Networks for IoT[J]. EURASIP Journal on Information Security, 2023, 2023(1): 2-15. |
| [15] | QIU Shuming, WANG Ding, XU Guoai, et al. Practical and Provably Secure Three-Factor Authentication Protocol Based on Extended Chaotic-Maps for Mobile Lightweight Devices[J]. IEEE Transactions on Dependable and Secure Computing, 2022, 19(2): 1338-1351. |
| [16] | SURESH D, ODELU V, REDDY A G, et al. Provably Secure Pseudo-Identity Three-Factor Authentication Protocol Based on Extended Chaotic-Maps for Lightweight Mobile Devices[J]. IEEE Access, 2022, 10: 109526-109536. |
| [17] | GUO Xianfeng, ZHANG Jiashu. Secure Group Key Agreement Protocol Based on Chaotic Hash[J]. Information Sciences, 2010, 180(20): 4069-4074. |
| [18] | LEE T. Enhancing the Security of Password Authenticated Key Agreement Protocols Based on Chaotic Maps[J]. Information Sciences, 2015, 290: 63-71. |
| [19] | CHATTERJEE S, ROY S, DAS A K, et al. Secure Biometric-Based Authentication Scheme Using Chebyshev Chaotic Map for Multi-Server Environment[J]. IEEE Transactions on Dependable and Secure Computing, 2018, 15(5): 824-839. |
| [20] | RYU J, KANG D, WON D. Improved Secure and Efficient Chebyshev Chaotic Map-Based User Authentication Scheme[J]. IEEE Access, 2022, 10: 15891-15910. |
| [21] | WANG Cong, LI Xiaohang, MA Maode, et al. PSAK: A Provably Secure Authenticated Key Agreement Scheme Based on Extended Chebyshev Chaotic Maps for Smart Grid Environments[J]. Transactions on Emerging Telecommunications Technologies, 2023, 34(5): e4752-e4772. |
| [22] | ZHANG Liping, ZHU Yue, REN Wei, et al. An Energy-Efficient Authentication Scheme Based on Chebyshev Chaotic Map for Smart Grid Environments[J]. IEEE Internet of Things Journal, 2021, 8(23): 17120-17130. |
| [23] | MIAO Junfeng, WANG Zhaoshun, WU Zeqing, et al. A Blockchain-Enabled Privacy-Preserving Authentication Management Protocol for Internet of Medical Things[J]. Expert Systems with Applications, 2024, 237: 121329-121339. |
| [24] | QIAO Hui, DONG Xuewen, JIANG Qi, et al. Anonymous Lightweight Authenticated Key Agreement Protocol for Fog-Assisted Healthcare IoT System[J]. IEEE Internet of Things Journal, 2023, 10(19): 16715-16726. |
| [25] | CUI Jie, YU Jing, ZHONG Hong, et al. Chaotic Map-Based Authentication Scheme Using Physical Unclonable Function for Internet of Autonomous Vehicle[J]. IEEE Transactions on Intelligent Transportation Systems, 2023, 24(3): 3167-3181. |
| [26] | SRINIVAS J, DAS A K, WAZID M, et al. Anonymous Lightweight Chaotic Map-Based Authenticated Key Agreement Protocol for Industrial Internet of Things[J]. IEEE Transactions on Dependable and Secure Computing, 2020, 17(6): 1133-1146. |
| [27] | TANVEER M, BADSHAH A, KHAN A U, et al. CMAF-IIoT: Chaotic Map Based Authentication Framework for Industrial Internet of Things[J]. Internet of Things, 2023, 23: 100902-100919. |
| [28] | KRISHNASRIJA R, MANDAL A K, CORTESI A. A Lightweight Mutual and Transitive Authentication Mechanism for IoT Network[J]. Ad Hoc Networks, 2023, 138: 103003-103019. |
| [29] | ZHANG Yu, SUN Guangmin, ZHAI Peng, et al. A Provably Secure Traceability Authentication Protocol Based on Chebyshev Chaotic Map[J]. Netinfo Security, 2022, 22(12): 25-33. |
| 张昱, 孙光民, 翟鹏, 等. 一种基于切比雪夫混沌映射的可证明安全的溯源认证协议[J]. 信息网络安全, 2022, 22(12): 25-33. | |
| [30] | ZHANG Linhua. Cryptanalysis of the Public Key Encryption Based on Multiple Chaotic Systems[J]. Chaos, Solitons & Fractals, 2008, 37(3): 669-674. |
| [31] | KOCAREV L, TASEV Z. Public-Key Encryption Based on Chebyshev Maps[EB/OL]. (2003-06-20)[2024-04-02]. https://ieeexplore.ieee.org/document/1204947. |
| [32] | JIANG Qi, ZHANG Ning, NI Jianbing, et al. Unified Biometric Privacy Preserving Three-Factor Authentication and Key Agreement for Cloud-Assisted Autonomous Vehicles[J]. IEEE Transactions on Vehicular Technology, 2020, 69(9): 9390-9401. |
| [33] | RANGWANI D, SADHUKHAN D, RAY S, et al. A Robust Provable-Secure Privacy-Preserving Authentication Protocol for Industrial Internet of Things[J]. Peer-to-Peer Networking and Applications, 2021, 14(3): 1548-1571. |
| [1] | 刘一丹, 马永柳, 杜宜宾, 程庆丰. 一种车联网中的无证书匿名认证密钥协商协议[J]. 信息网络安全, 2024, 24(7): 983-992. |
| [2] | 孙隽丰, 李成海, 宋亚飞. ACCQPSO:一种改进的量子粒子群优化算法及其应用[J]. 信息网络安全, 2024, 24(4): 574-586. |
| [3] | 张敏, 冯永强, 许春香, 张建华. 智能家居网络下基于多因子的认证密钥协商方案[J]. 信息网络安全, 2024, 24(1): 133-142. |
| [4] | 郭瑞, 魏鑫, 陈丽. 工业物联网环境下可外包的策略隐藏属性基加密方案[J]. 信息网络安全, 2023, 23(3): 1-12. |
| [5] | 张敏, 许春香, 张建华. 无人机网络中基于多因子的认证密钥协商协议研究[J]. 信息网络安全, 2022, 22(9): 21-30. |
| [6] | 佟晓筠, 苏煜粤, 张淼, 王翥. 基于混沌和改进广义Feistel结构的轻量级密码算法[J]. 信息网络安全, 2022, 22(8): 8-18. |
| [7] | 王姝爽, 马兆丰, 刘嘉微, 罗守山. 区块链跨链安全接入与身份认证方案研究与实现[J]. 信息网络安全, 2022, 22(6): 61-72. |
| [8] | 沈延, 姚萌萌. 基于事件的群组密钥协商协议形式化分析研究[J]. 信息网络安全, 2022, 22(5): 30-36. |
| [9] | 张昱, 孙光民, 翟鹏, 李煜. 一种基于切比雪夫混沌映射的可证明安全的溯源认证协议[J]. 信息网络安全, 2022, 22(12): 25-33. |
| [10] | 吴克河, 程瑞, 郑碧煌, 崔文超. 电力物联网安全通信协议研究[J]. 信息网络安全, 2021, 21(9): 8-15. |
| [11] | 刘忻, 杨浩睿, 郭振斌, 王家寅. 一种实现在线注册与权限分离的工业物联网身份认证协议[J]. 信息网络安全, 2021, 21(7): 1-9. |
| [12] | 刘忻, 郭振斌, 宋宇宸. 一种基于SGX的工业物联网身份认证协议[J]. 信息网络安全, 2021, 21(6): 1-10. |
| [13] | 董锵, 罗国明, 史宏逵, 张永跃. 基于IMS的移动通信专网认证和密钥协商方法研究[J]. 信息网络安全, 2021, 21(1): 88-96. |
| [14] | 赵国锋, 周文涛, 徐川, 徐磊. 一种基于双线性配对的天地一体化网络安全身份认证方案[J]. 信息网络安全, 2020, 20(12): 33-39. |
| [15] | 陈瑞滢, 陈泽茂, 王浩. 工业控制系统安全监控协议的设计与优化研究[J]. 信息网络安全, 2019, 19(2): 60-69. |
| 阅读次数 | ||||||||||||||||||||||||||||||||||||||||||||||||||
|
全文 73
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||
|
摘要 169
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||