信息网络安全 ›› 2021, Vol. 21 ›› Issue (1): 88-96.doi: 10.3969/j.issn.1671-1122.2021.01.011
• 理论研究 • 上一篇
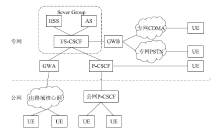
基于IMS的移动通信专网认证和密钥协商方法研究
- 1.中国人民解放军陆军工程大学通信工程学院,南京 210042
2.南京邮电大学,南京 210023
3.天津市大数据管理中心,天津 300221
-
收稿日期:2020-11-20出版日期:2021-01-10发布日期:2021-02-23 -
通讯作者:张永跃 E-mail:zyy_xp@126.com -
作者简介:董锵(1989—),男,湖北,硕士研究生,主要研究方向为移动通信网络|罗国明(1965—),男,重庆,教授,本科,主要研究方向为信息与通信网、通信网规划与设计|史宏逵(1973—),男,浙江,副研究员,博士,主要研究方向为下一代移动通信技术|张永跃(1981—),男,天津,工程师,本科, 主要研究方向为电子政务、数据资源共享开放、电子认证、数据安全。 -
基金资助:国家自然科学基金(61871399)
Research on Authentication and Key Agreement Method of IMS-based Mobile Communication Private Network
DONG Qiang1, LUO Guoming1, SHI Hongkui2, ZHANG Yongyue3( )
)
- 1. Institute of Communication Engineering, Army Engineering University of PLA, Nanjing 210042, China
2. Nanjing University of Posts and Telecommunications, Nanjing 210023, China
3. Tianjin Municipal Big Data Administration Center, Tianjin 300221, China
-
Received:2020-11-20Online:2021-01-10Published:2021-02-23 -
Contact:ZHANG Yongyue E-mail:zyy_xp@126.com
摘要:
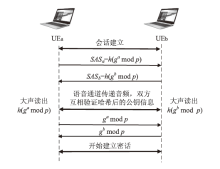
为适应行业移动通信专网发展和保密通话业务需求,文章针对专网独立业务控制特点,在应用IMS技术架构的移动通信专网中,提出一种向前兼容的专网功能结构模型。文章研究分析了多个可应用于IMS专网的认证和密钥协商方案,并根据归属地服务器是否参与认证过程,分端到端、端到服务器两类应用场景,综合比较各类认证和密钥协商方案的安全性能和运算开销,最后给出较优方案,为专网通信安全相关机制建设提供参考。
中图分类号:
引用本文
董锵, 罗国明, 史宏逵, 张永跃. 基于IMS的移动通信专网认证和密钥协商方法研究[J]. 信息网络安全, 2021, 21(1): 88-96.
DONG Qiang, LUO Guoming, SHI Hongkui, ZHANG Yongyue. Research on Authentication and Key Agreement Method of IMS-based Mobile Communication Private Network[J]. Netinfo Security, 2021, 21(1): 88-96.
表2
端到端类文献方案开销评估
| 端到端类 文献方案 | 数学 基础 | RTT | 主叫端开销 | 被叫端开销 | 主叫端 估时 | 被叫端 估时 |
|---|---|---|---|---|---|---|
| [7] | DLP | 2.5 | 2RNG+2EXPO+ 2ENCB+3DNCB | 2RNG+2EXPO+ 3ENCB+2DNCB | 8.801 | 8.801 |
| [22] | RSA | 4 | SIGN+SEVR | SIGN+SEVR | 4.0425 | 4.0425 |
| [10] | 双线 性对 | 2 | RNG+2PAIRING+EXPO+ HMAC+H1+2PM | RNG+2PAIRING+ EXPO+HMAC+H1+2PM | 21.4146 | 21.4146 |
| [11](使用SAS) | DLP/ECDLP | 5 | RNG+2EXPO+ 4H+MAAU | RNG+2EXPO+ 4H+MAAU | >104 | >104 |
| [11](使用rs) | HASH | 3 | H+3HMAC | H+3HMAC | 0.0161 | 0.0161 |
| [15] | DLP | 3 | 2RNG+2EXPO+5HMAC+ SIGN+SVER | 2RNG+2EXPO+5HMAC+ SIGN+SVER | 12.8435 | 12.8435 |
表3
端到服务器类文献方案开销评估
| 端到服务器类文献方案 | 数学 基础 | RTT | 用户端开销 | 服务器端开销 | 用户端估时 | 服务器端估时 |
|---|---|---|---|---|---|---|
| [18] | ECDLP | 2 | 2H+2PM+RNG+PA | 2H+2PM+ RNG+PA | 5.0244 | 5.0244 |
| [19] | DLP | 1.5 | RNG+2PM+ENCB+4H | RNG+2PM+ DNCB+5H | 5.0048 | 5.0071 |
| [20] | HASH | 1.5 | RNG+3CHEV+5H | RNG+3CHEV+5H | 2.7765 | 2.7765 |
| [21] | DLP | 2 | 2RNG+EXPO+4H | 2RNG+2EXPO+4H | 16.4872 | 8.7872 |
| [23] | HASH | Y | 6H+RNG | HA开销:10H FA开销:RNG+10H | 0.5528 | 0.585 |
| [1] | LIANG Xuemei, FANG Xiaonong, YANG Shuo, et al. IMS Technology in Industry Private Network[M]. Beijing: Posts & Telecom Press Co.,LTD, 2016. |
| 梁雪梅, 方晓农, 杨硕, 等. IMS技术行业专网应用[M]. 北京: 人民邮电出版社, 2016. | |
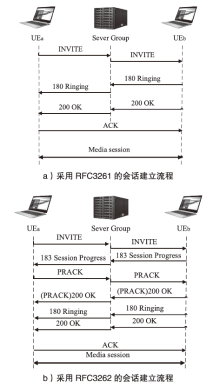
| [2] | ROSENBERG J, SCHULZRINNE H. IETF RFC3261 SIP: Session Initiation Protocol[EB/OL]. https://tools.ietf.org/pdf/rfc3261.pdf, 2020-10-08. |
| [3] | GU Xiaohui, SHI Jiajia, GUO Fang. Security Mechanism of SIP and Improvement of HTTP Digest Authentication[J]. Journal of Donghua University(Natural Science), 2010,36(2):165-169. |
| 顾晓辉, 施佳佳, 郭放. SIP的安全机制及其HTTP摘要认证的改进[J]. 东华大学学报(自然科学版), 2010,36(002):165-169. | |
| [4] | QIANG Lei, RAO Shaoyang, CHEN Hui, et al. IMS Core Principle and Application[M]. Beijing: Posts & Telecom Press Co., LTD, 2008. |
| 强磊, 饶少阳, 陈卉, 等. IMS核心原理与应用[M]. 北京: 人民邮电出版社, 2008. | |
| [5] | ROSENBERG J, SCHULZRINNE H. IETF RFC3262 Reliability of Provisional Responses in the Session Initiation Protocol (SIP)[EB/OL]. https://tools.ietf.org/pdf/rfc3262.pdf, 2020-10-08. |
| [6] | DONG Qiang, LUO Guoming, ZHU Lei, et al. Research on SIP Based Key Distribution Method of Private Mobile Communication System[J]. Command Control & Simulation, 2020,42(4):111-116. |
| 董锵, 罗国明, 朱磊, 等. 基于SIP的专用移动通信系统密钥分发方法[J]. 指挥控制与仿真, 2020,42(4):111-116. | |
| [7] | BELLOVIN S M. Encrypted Key Exchange: Password-based Protocols Secure Against Dictionary Attacks[C] // IEEE. Proc IEEE Symposium on Security & Privacy, May 4-6, 1992, Oakland, CA, USA. USA: IEEE Computer Society, 1992: 72-84. |
| [8] | ZUO Liming, CHEN Lanlan. Special Digital Signature Scheme Based on Identity Identification and It’s Application[J]. Computer Science, 2020,47(1):309-314. |
| 左黎明, 陈兰兰. 基于身份标识的特殊数字签名方案及其应用[J]. 计算机科学, 2020,47(1):309-314. | |
| [9] | Al-Riyami S S, PATERSON K G. Certificateless Public Key Cryptography[C] // Springer. Proceedings of International Conference on the Theory and Application of Cryptology and Information Security, January 1-4, 2003,Berlin, Germany: Springer, 2003: 452-473. |
| [10] | XU Ping, ZHANG Fangzhou, ZHANG Xiaoyu, et al. End to End Key Agreement Protocol Based on Mobile Network[J]. Journal of Northeast Petroleum University, 2012,36(4):74-78. |
| 徐平, 张方舟, 张晓宇, 等. 基于移动网络的端到端密钥协商协议[J]. 东北石油大学学报, 2012,36(4):74-78. | |
| [11] | ZIMMERMANN P, JOHNSTON A, CALLAS J. IETF RFC 6189 ZRTP: Media Path Key Agreement for Unicast Secure RTP[EB/OL]. https://tools.ietf.org/pdf/rfc6189.pdf, 2020-10-08. |
| [12] | BAUGHER M, MCGREW D, NASLUND M. IETF RFC 3711 The Secure Real-time Transport Protocol (SRTP)[EB/OL]. https://tools.ietf.org/pdf/rfc3711.pdf, 2020-10-08. |
| [13] | KRAWCZYK H. SIGMA: The 'SIGn-and-MAc' Approach to Authenticated Diffie-Hellman and Its Use in the IKE Protocols[J]. Proc of Crypto, 2003,2729(2):400-425. |
| [14] |
NIKANDER P, GURTOV A, HENDERSON T R. Host Identity Protocol (HIP): Connectivity, Mobility, Multi-Homing, Security, and Privacy over IPv4 and IPv6 Networks[J]. IEEE Communications Surveys & Tutorials, 2010,12(2):186-204.
doi: 10.1109/SURV.2010.021110.00070 URL |
| [15] |
PECORI R, VELTRI L. 3AKEP: Triple-authenticated Key Exchange Protocol for Peer-to-peer VoIP Applications[J]. Computer Communications, 2016,85(1):28-40.
doi: 10.1016/j.comcom.2016.04.005 URL |
| [16] | ARKKO J, CARRARA E, LINDHOLM F. IETF RFC 3830 MIKEY: Multimedia Internet KEYing [EB/OL]. https://tools.ietf.org/pdf/rfc3830.pdf, 2020-10-08. |
| [17] |
KILINC H H, YANIK T. A Survey of SIP Authentication and Key Agreement Schemes[J]. IEEE Communications Surveys & Tutorials, 2014,16(2):1005-1023.
doi: 10.1109/SURV.2013.091513.00050 URL |
| [18] | YOON E J, YOO KY. A New Authentication Scheme for Session Initiation Protocol[C] //IEEE. 2009 International Conference on Complex, Intelligent and Software Intensive Systems, March 16-19, 2009, Fukuoka, Japan. Japan: IEEE, 2009: 549-554. |
| [19] |
ISLAM S H, VIJAYAKUMAR P, BHUIYAN M Z A, et al. A Provably Secure Three-factor Session Initiation Protocol for Multimedia Big Data Communications[J]. IEEE Internet of Things Journal, 2018,5(5):3408-3418.
doi: 10.1109/JIoT.6488907 URL |
| [20] | GUO Xiangyu, SUN Dazhi, YANG Ying. An Improved Three-factor Session Initiation Protocol Using Chebyshev Chaotic Map [EB/OL]. https://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=9117092, 2020-06-26. |
| [21] | CAI Dazhuang. Research and Design of a Security Mechanism for IMS Access Layer[D]. Shenyang: Shenyang Institute of Computing Technology of Chinese Academy of Sciences, 2015. |
| 才大壮. IMS接入侧安全机制的研究与设计[D]. 沈阳:中国科学院研究生院(沈阳计算技术研究所), 2015. | |
| [22] | KONG L, BALASUBRAMANIYAN V B, AHAMAD M. A Lightweight Scheme for Securely and Reliably Locating SIP Users[C] // IEEE. IEEE Workshop on VoIP Management & Security. April 3-7, 2006, Vancouver, BC, Canada. Canada: IEEE, 2006: 8-16. |
| [23] |
GOPE P, HWANG T. Lightweight and Energy-efficient Mutual Authentication and Key Agreement Scheme With User Anonymity for Secure Communication in Global Mobility Networks[J]. IEEE Systems Journal, 2016,10(4):1-10.
doi: 10.1109/JSYST.2016.2528398 URL |
| [1] | 余果, 王冲华, 陈雪鸿, 李俊. 认证视角下的工业互联网标识解析安全[J]. 信息网络安全, 2020, 20(9): 77-81. |
| [2] | 王利, 李二霞, 纪宇晨, 李小勇. 基于PUF的抗物理克隆RFID安全认证协议[J]. 信息网络安全, 2020, 20(8): 89-97. |
| [3] | 张骁, 刘吉强. 基于硬件指纹和生物特征的多因素身份认证协议[J]. 信息网络安全, 2020, 20(8): 9-15. |
| [4] | 孙子文, 张向阳. 大规模移动RFID系统Shamir’s密钥共享PUF安全认证协议[J]. 信息网络安全, 2020, 20(6): 26-35. |
| [5] | 刘晓芬, 陈晓峰, 连桂仁, 林崧. 基于d级单粒子的可认证多方量子秘密共享协议[J]. 信息网络安全, 2020, 20(3): 51-55. |
| [6] | 侯林, 冯达, 玄鹏开, 周福才. 基于认证树的外包数据库连接查询验证方案[J]. 信息网络安全, 2020, 20(2): 91-97. |
| [7] | 赵国锋, 周文涛, 徐川, 徐磊. 一种基于双线性配对的天地一体化网络安全身份认证方案[J]. 信息网络安全, 2020, 20(12): 33-39. |
| [8] | 余北缘, 刘建伟, 周子钰. 自组织网络环境下的节点认证机制研究[J]. 信息网络安全, 2020, 20(12): 9-18. |
| [9] | 张正, 查达仁, 柳亚男, 方旭明. 基于物理不可克隆函数的Kerberos扩展协议及其形式化分析[J]. 信息网络安全, 2020, 20(12): 91-97. |
| [10] | 刘利娟, 李志慧, 支丹利. 可实现身份认证的多方量子密钥分发协议[J]. 信息网络安全, 2020, 20(11): 59-66. |
| [11] | 程洋, 雷敏, 罗群. 基于深度学习的物联网终端设备接入认证方法[J]. 信息网络安全, 2020, 20(11): 67-74. |
| [12] | 李鱼, 韩益亮, 李喆, 朱率率. 基于LWE的抗量子认证密钥交换协议[J]. 信息网络安全, 2020, 20(10): 92-99. |
| [13] | 胡蝶, 马东堂, 龚旻, 马召. 一种基于PUF的物理层安全认证方法[J]. 信息网络安全, 2020, 20(1): 61-66. |
| [14] | 张富友, 王琼霄, 宋利. 基于生物特征识别的统一身份认证系统研究[J]. 信息网络安全, 2019, 19(9): 86-90. |
| [15] | 侯林, 李明洁, 徐剑, 周福才. 基于变长认证跳表的分布式动态数据持有证明模型[J]. 信息网络安全, 2019, 19(7): 67-74. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||