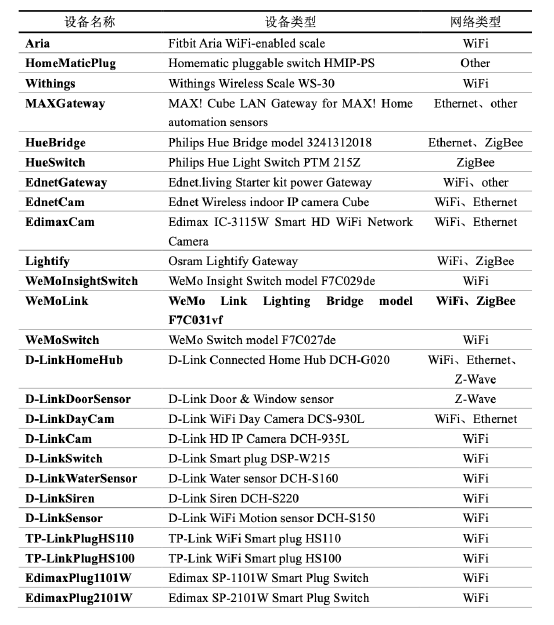
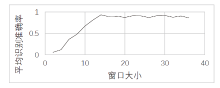
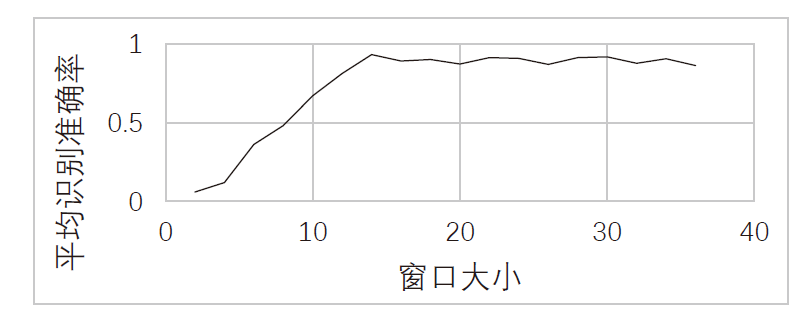
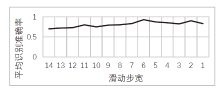
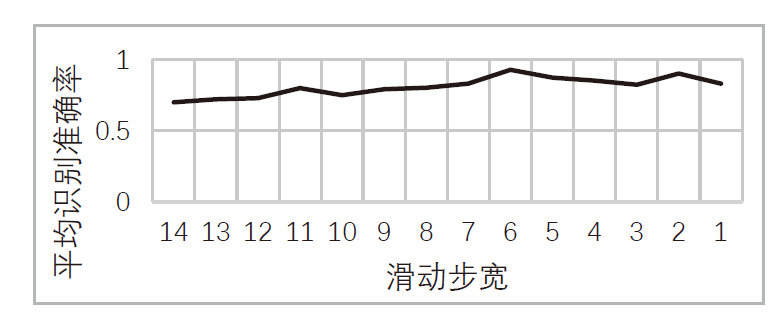
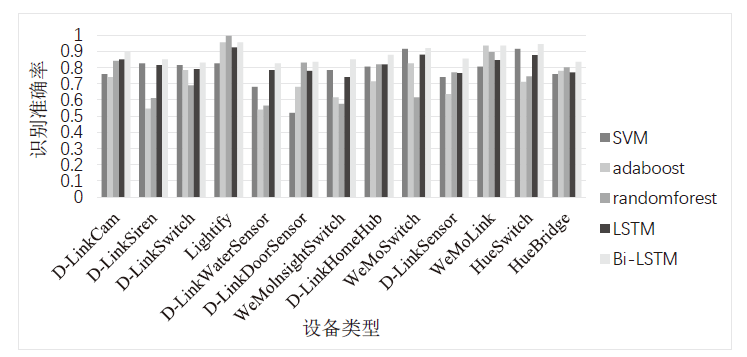
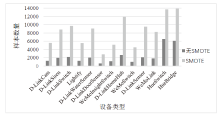
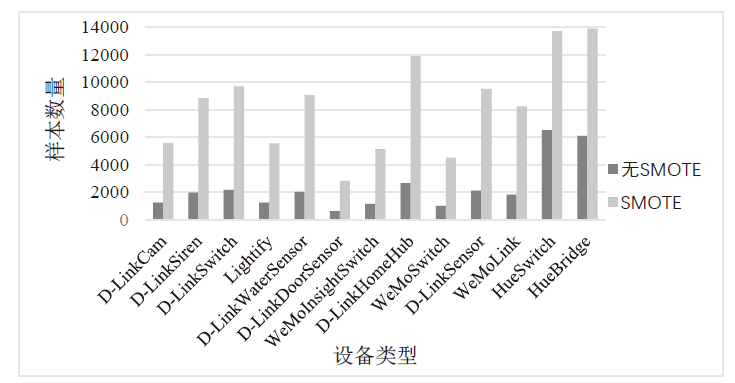
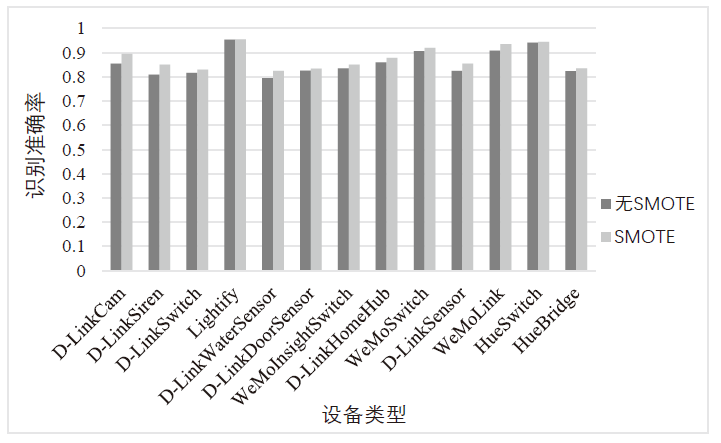
| [1] |
FIFIELD D, EGELMAN S. Fingerprinting Web Users Through Font Metrics[C]// Springer. International Conference Financial Cryptography and Data Security, Springer. January 26-30, 2015, San Juan, Puerto Rico. Berlin: Springer, 2015: 107-134.
|
| [2] |
ECKERSLEY P. How Unique Is Your Web Browser?[C]// ACM. Proceedings of the 10th International Conference on Privacy Enhancing Technologies, July 2010, Berlin, Heidelberg. New York: ACM, 2010: 1-18.
|
| [3] |
VASTEL A, LAPERDRIX P, RUDAMETKIN W, et al. FP-STALKER: Tracking Browser Fingerprint Evolutions[C]//IEEE. 2018 IEEE Symposium on Security and Privacy (SP), May 20-24, 2018, San Francisco, USA. Piscataway: IEEE, 2018: 728-741.
|
| [4] |
TAKEI N, SAITO T, TAKASU K, et al. Web Browser Fingerprinting Using Only Cascading Style Sheets[C]//IEEE. IEEE 2015 10th International Conference on Broadband and Wireless Computing, Communication and Applications(BWCCA), November 4-6, 2015, Krakow, Poland. Piscataway: IEEE, 2015: 57-63.
|
| [5] |
MOWERY K, SHACHAM H. Pixel Perfect Fingerprinting Canvas in HTML5[C]//IEEE. Proceedings of Web 2.0 Security & Privacy, May 24, 2012, San Francisco, USA. Piscataway: IEEE, 2012: 1-12.
|
| [6] |
STAROV O, NIKIFORAKIS N. Xhound: Quantifying the Fingerprintability of Browser Extensions[C]//IEEE. 2017 IEEE Symposium on Security and Privacy (SP), May 22-26, 2017, San Jose, USA. Piscataway: IEEE, 2017: 941-956.
|
| [7] |
LUO Yong, HU Han, WEN Yonggang, et al. Transforming Device Fingerprinting for Wireless Security via Online Multitask Metric Learning[J]. IEEE Internet of Things Journal, 2020,7(1):208-219.
|
| [8] |
MIETTINEN M, MARCHAL S, HAFEEZ I, et al. IoT Sentinel Demo: Automated Device-Type Identification for Security Enforcement in IoT[C]//IEEE. 2017 IEEE 37th International Conference on Distributed Computing Systems (ICDCS), June 5-8, 2017, Atlanta, USA. Piscataway: IEEE, 2017: 2511-2514.
|
| [9] |
FRANKLIN J, MCCOY D, TABRIZ P, et al. Passive Data Link Layer 802. 11 Wireless Device Driver Fingerprinting[C]//AMC. Proceedings of the 15th Conference on USENIX Security Symposium, January 17, 2006, Berkeley, USA. New York: ACM, 2006: 167-178.
|
| [10] |
HAMAD S A, ZHANG W E, SHENG Q Z, et al. IoT Device Identification via Network-Flow Based Fingerprinting and Learning[C]//IEEE. 2019 18th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/13th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), August 5-8, 2019, Rotorua, New Zealand. Piscataway: IEEE, 2019: 103-111.
|
| [11] |
RADHAKRISHNAN S V, ULUAGAC A S, BEYAH R. GTID: A Technique for Physical Device and Device Type Fingerprinting[J]. IEEE Transactions on Dependable and Secure Computing, 2015,5(12):519-532.
|
| [12] |
SIBY S, MAITI R R, Tippenhauer N O. IoT Scanner: Detecting Privacy Threats in IoT Neighborhoods[C]//ACM. The 3rd ACM International Workshop. April 2, 2017, Abu Dhabi United Arab Emirates. New York: ACM, 2017: 23-30.
|
| [13] |
ULUAGAC A S, RADHAKRISHNAN S V, CORBETT C, et al. A Passive Technique for Fingerprinting Wireless Devices with Wired-side Observations[C]//IEEE. 2013 IEEE Conference on Communications and Network Security (CNS), Octomber 14-16, 2013, National Harbor, USA. Piscataway: IEEE, 2013: 305-313.
|
| [14] |
KUMAR K, DALAI A K, PANIGRAHY S K, et al. An ANN Based Approach for Wireless Device Fingerprinting[C]//IEEE. 2017 2nd IEEE International Conference on Recent Trends in Electronics, Information & Communication Technology (RTEICT), May 19-20, 2017, Bangalore, India. Piscataway: IEEE, 2017: 1302-1307.
|
| [15] |
DALAI A K, JENA A, SHARMA S, et al. A Fingerprinting Technique for Identification of Wireless Devices[C]//IEEE. 2018 International Conference on Computer, Information and Telecommunication Systems (CITS), July 11-13, 2018, Colmar, France. Piscataway: IEEE, 2018: 1-5.
|
 ), LEI Min, LUO Qun
), LEI Min, LUO Qun