信息网络安全 ›› 2020, Vol. 20 ›› Issue (9): 6-11.doi: 10.3969/j.issn.1671-1122.2020.09.002
基于Char-RNN改进模型的恶意域名训练数据生成技术
- 中国人民公安大学信息网络安全学院,北京 100038
-
收稿日期:2020-07-16出版日期:2020-09-10发布日期:2020-10-15 -
通讯作者:芦天亮 E-mail:lutianliang@ppsuc.edu.cn -
作者简介:吴警(1996—),男,江苏,硕士研究生,主要研究方向为网络信息安全、网络攻防|芦天亮(1985—),男,河北,副教授,博士,主要研究方向为网络信息安全、恶意代码分析与检测|杜彦辉(1969—),男,山西,教授,博士,主要研究方向为网络信息安全、人工智能 -
基金资助:国家自然科学基金(61602489);“十三五”国家密码发展基金密码理论研究重点课题(MMJJ20180108)
Generation of Malicious Domain Training Data Based on Improved Char-RNN Model
WU Jing, LU Tianliang( ), DU Yanhui
), DU Yanhui
- College of Information and Cyber Security, People’s Public Security University of China, Beijing 100038, China
-
Received:2020-07-16Online:2020-09-10Published:2020-10-15 -
Contact:Tianliang LU E-mail:lutianliang@ppsuc.edu.cn
摘要:
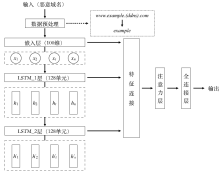
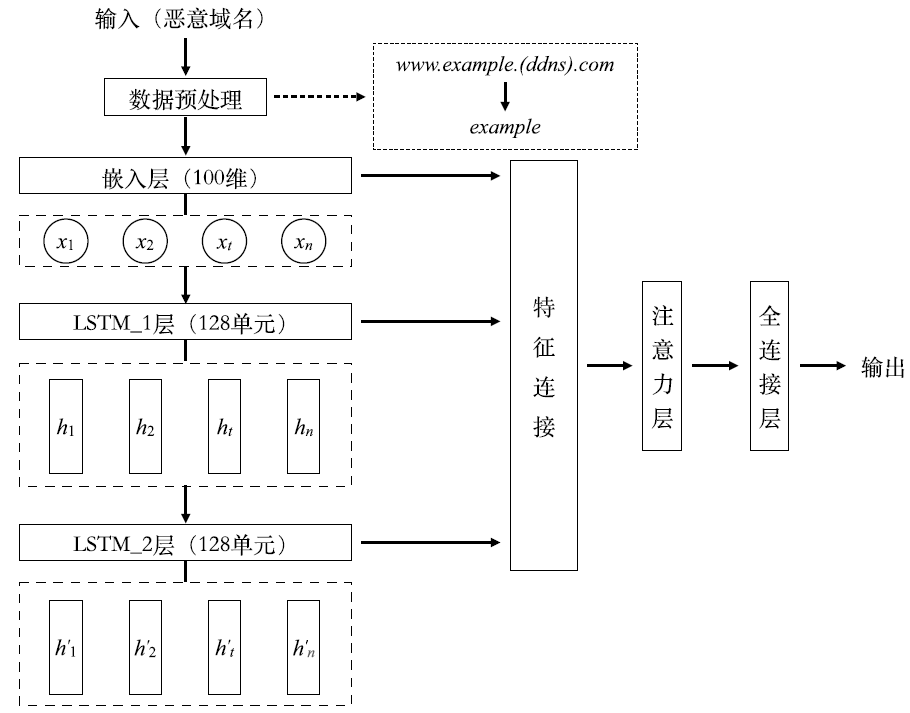
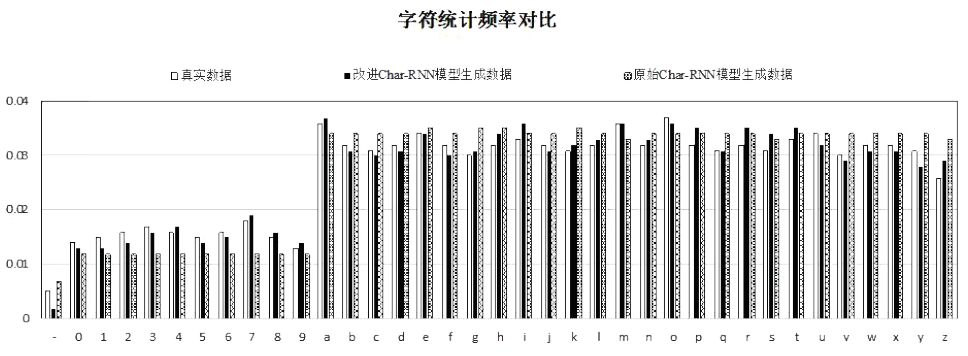
近年来,新型僵尸网络开始使用域名生成算法(DGA)和命令与控制(C&C)服务器通信。针对基于深度学习的检测模型缺少对新出现的DGA变体域名的识别能力等问题,结合文本生成的思想,文章对原始Char-RNN模型进行改进,使用长短期记忆网络(LSTM)构建模型并引入注意力机制,从而生成用于模拟未知变体算法的恶意域名。实验证明,基于该方法生成的域名数据与真实数据在字符组成结构和频率方面具有高度相似性,且以生成数据作为训练集的检测模型保持了较好的性能,验证了基于文本生成模型的数据有效性以及将其作为训练数据集来预测未知DGA变体的可行性。
中图分类号:
引用本文
吴警, 芦天亮, 杜彦辉. 基于Char-RNN改进模型的恶意域名训练数据生成技术[J]. 信息网络安全, 2020, 20(9): 6-11.
WU Jing, LU Tianliang, DU Yanhui. Generation of Malicious Domain Training Data Based on Improved Char-RNN Model[J]. Netinfo Security, 2020, 20(9): 6-11.
表2
真实与生成恶意域名对比
| 真实的恶意域名 | 生成的恶意域名 |
|---|---|
| myjqestnessbiophysicalohax lidouxehktimfpw idofgtxawvoetbb okll04furr sharmainewestbrook elfiumawmoehepu e8d1e174d60449c80a849936eff4fe9e zbynarjrejq | ephetlojlccgmpr avpuonboopcuods5 wqgzmfbh-nz cmwlqwficlloeq c1a22oee5b ejwmitqbpslotdeti qexhfshwopfyjyujkzfr zplxtyfzsupjlyfxcggt |
| [1] | GOEBEL J, HOLZ T. Rishi: Identify Bot Contaminated Hosts by IRC Nickname Evaluation[J]. HotBots, 2007,7(8):192. |
| [2] | JIANG Jian, ZHUGE Jianwei, DUAN Haixin, et al. Research on Botnet Mechanisms and Defenses[J]. Jonrnal of Software, 2012,23(1):82-96. |
| 江健, 诸葛建伟, 段海新, 等. 僵尸网络机理与防御技术[J]. 软件学报, 2012,23(1):82-96. | |
| [3] | MOHAISEN A, ALRAWI O, MOHAISEN M. Amal: High-fidelity, Behavior-based Automated Malware Analysis and Classification[J]. Computers &Security, 2015,15(52):251-266. |
| [4] | WANG Yuanyuan, WU Chunjiang, LIU Qihe, et al. Overview of Malicious Domainname Detection and Application[J]. Computer Applications and Software, 2019,36(9):310-316. |
| 王媛媛, 吴春江, 刘启和, 等. 恶意域名检测研究与应用综述[J]. 计算机应用与软件, 2019,36(9):310-316. | |
| [5] | YU Bin, PAN Jie, HU Jiaming. Character Level based Detection of DGA Domain Names[C]// IEEE. 2018 International Joint Conference on Neural Networks (IJCNN), July 8-13, 2018, Rio de Janeiro, Brazil. New York: IEEE, 2018: 1-8. |
| [6] | YADAV S, REDDY A K, REDDY, et al. Detecting Algorithmically Generated Malicious Domain Names[C]// ACM. Proceedings of the 10th ACM SIGCOMM Conference on Internet Measurement, November 27-30, 2010, Melbourne, Australia. New York: ACM, 2010: 48-61. |
| [7] | BILGE L, KIRDA E, KRUEGEL C, et al. EXPOSURE: Finding Malicious Domains Using Passive DNS Analysis[C]// NDSS. Proceedings of the Network and Distributed System Security Symposium, February 6-9, 2011, San Diego, California, USA. New York: NDSS, 2011: 1-17. |
| [8] | ZANG Xiaodong, GONG Jian, HU Xiaoyan. Detecting Malicious Domain Names Based on AGD[J]. Journal on Communications, 2018,39(7):15-25. |
| 臧小东, 龚俭, 胡晓艳. 基于AGD的恶意域名检测[J]. 通信学报, 2018,39(7):15-25. | |
| [9] | ZHAO Kejun, GE Liansheng, QIN Fenglin, et al. Deep Model for DGA Botnet Detection Based on Word-hashing[J]. Journal of Southeast University(Natural Science Edition), 2017,47(S1):30-33. |
| 赵科军, 葛连升, 秦丰林, 等. 基于word-hashing的DGA僵尸网络深度检测模型[J]. 东南大学学报(自然科学版), 2017,47(S1):30-33. | |
| [10] | WOODBRIDGE J, ANDERSON H S, AHUJA A, et al. Predicting Domain Generation Algorithms with Long Short-term Memory Networks[EB/OL]. https://xueshu.baidu.com/usercenter/paper/show?paperid=d3e2183530fbe98be88b18431f31dc19&site=xueshu_se, 2020-4-25. |
| [11] | YANG Luhui, LIU Guangjie, ZHAI Jiangtao, et al. Improved Algorithm for Detection of the Malicious Domain Name Based on the Convolutional Neural Network[J]. Journal of Xidian University, 2020,47(1):37-43. |
| 杨路辉, 刘光杰, 翟江涛, 等. 一种改进的卷积神经网络恶意域名检测算法[J]. 西安电子科技大学学报, 2020,47(1):37-43. | |
| [12] | ANDERSON H S, WOODBRIDGE J, FILAR B. Deep DGA: Adversarially-tuned Domain Generation and Detection[C]// ACM. Proceedings of the 2016 ACM Workshop on Artificial Intelligence and Security, October 27-30, 2016, Vienna ,Austria. New York: ACM, 2016: 13-21. |
| [13] | YUAN Chen. Research and Implementation of Malicious Domains' Detection Method Based on Adversarial Model[D]. Beijing: Beijing University of Civil Engineering and Architecture, 2018. |
| 袁辰. 基于对抗模型的恶意域名检测方法的研究与实现[D]. 北京:北京建筑大学, 2018. | |
| [14] | CHENG Hua, CAI Jing, FANG Yiquan. RL-Gen: A Character-Level Text Generation Framework with Reinforcement Learning in Domain Generation Algorithm Case[C]// Springer. International Conference on Neural Information Processing, December 12-15, 2019, Sydney, Australia. Berlin: Springer, 2019: 690-697. |
| [15] | WANG Qixin, LUO Tianyi, WANG Dong. Chinese Song Iambics Generation with Neural Attention-based Model[EB/OL]. Eprint arXiv: 1604. 06274, 2016-12-20. |
| [16] | KARPATHY A. The Unreasonable Effectiveness of Recurrent Neural Networks[EB/OL]. http://karpathy.github.io/2015/05/21/rnn-effectiveness, 2020-5-21. |
| [17] | GLUSHKOVA T, ARTEMOVA E. Char-RNN and Active Learning for Hashtag Segmentation[EB/OL]. https://xueshu.baidu.com/usercenter/paper/show?paperid=1x3f0at0h42a0gp09m080pb0bn496380&site=xueshu_se, 2019-12-31. |
| [18] |
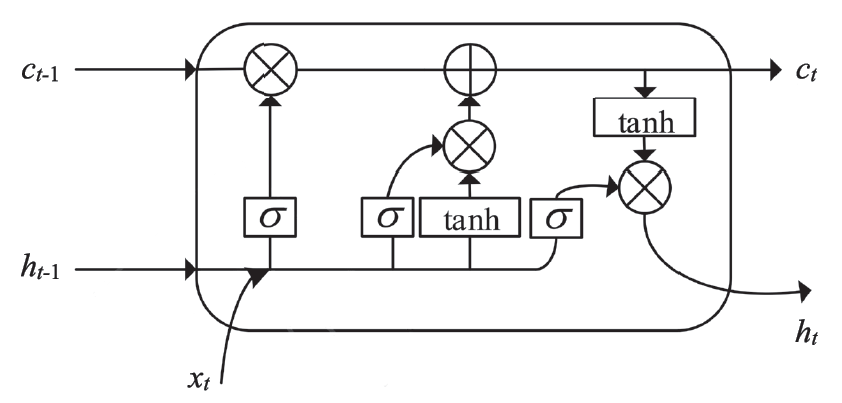
HOCHREITER S, SCHMIDHUBER J. Long Short-term Memory[J]. Neural Computation, 1997,9(8):1735-1780.
doi: 10.1162/neco.1997.9.8.1735 URL pmid: 9377276 |
| [19] | CHO K, VAN Merriënboer B, GULCEHRE C, et al. Learning Phrase Representations Using RNN Encoder-decoder for Statistical Machine Translation[EB/OL]. https://xueshu.baidu.com/usercenter/paper/show?paperid=2ba31a0b87d74d25317da3521cca2915&site=xueshu_se&hitarticle=1, 2014-12-31. |
| [20] | RAFFEL C, ELLIS D P W. Feed-forward Networks with Attention can Solve some Long-term Memory Problems[EB/OL]. https://www.researchgate.net/publication/288890112_Feed-Forward_Networks_with_Attention_Can_Solve_Some_Long-Term_Memory_Problems, 2015-12-20. |
| [1] | 王文华, 郝新, 刘焱, 王洋. AI系统的安全测评和防御加固方案[J]. 信息网络安全, 2020, 20(9): 87-91. |
| [2] | 张蕾华, 黄进, 张涛, 王生玉. 视频侦查中人像智能分析应用及算法优化[J]. 信息网络安全, 2020, 20(5): 88-93. |
| [3] | 王蓉, 马春光, 武朋. 基于联邦学习和卷积神经网络的入侵检测方法[J]. 信息网络安全, 2020, 20(4): 47-54. |
| [4] | 谢永恒, 冯宇波, 董清风, 王梅. 基于深度学习的数据接入方法研究[J]. 信息网络安全, 2019, 19(9): 36-40. |
| [5] | 马春光, 郭瑶瑶, 武朋, 刘海波. 生成式对抗网络图像增强研究综述[J]. 信息网络安全, 2019, 19(5): 10-12. |
| [6] | 方勇, 朱光夏天, 刘露平, 贾鹏. 基于深度学习的浏览器Fuzz样本生成技术研究[J]. 信息网络安全, 2019, 19(3): 26-33. |
| [7] | 朱海麒, 姜峰. 人工智能时代面向运维数据的异常检测技术研究与分析[J]. 信息网络安全, 2019, 19(11): 24-35. |
| [8] | 徐国天. 基于DGA的恶意程序域名生成算法破解[J]. 信息网络安全, 2017, 17(9): 26-29. |
| [9] | 段大高, 谢永恒, 盖新新, 刘占斌. 基于神经网络的微博虚假消息识别模型[J]. 信息网络安全, 2017, 17(9): 134-137. |
| [10] | 任浩, 罗森林, 潘丽敏, 高君丰. 基于图结构的文本表示方法研究[J]. 信息网络安全, 2017, 17(3): 46-52. |
| [11] | 雷青, 荆丽桦, 赵德明, 郑继龙. 基于深度学习的安卓APP视频枪支检测技术研究[J]. 信息网络安全, 2016, 16(9): 149-153. |
| [12] | 崔鹏飞, 裘玥, 孙瑞. 面向网络内容安全的图像识别技术研究[J]. 信息网络安全, 2015, 15(9): 154-157. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||