信息网络安全 ›› 2020, Vol. 20 ›› Issue (12): 91-97.doi: 10.3969/j.issn.1671-1122.2020.12.012
基于物理不可克隆函数的Kerberos扩展协议及其形式化分析
- 1.中国科学院信息工程研究所,北京 100093
2.金陵科技学院网络安全学院,南京 211169
-
收稿日期:2020-08-02出版日期:2020-12-10发布日期:2021-01-12 -
通讯作者:张正 E-mail:zhangzheng@jit.edu.cn -
作者简介:张正(1973—),男,江苏,研究员,本科,主要研究方向为网络安全、密码协议、无线通信安全|查达仁(1982—),男,河北,高级工程师,博士,主要研究方向为密码工程与应用、可信计算与信息安全|柳亚男(1984—),女,江苏,讲师,博士,主要研究方向为物联网安全、应用密码学|方旭明(1981—),男,江苏,讲师,博士,主要研究方向为无线传感器网络 -
基金资助:国家重点研发计划(2017YFB0802802);国家自然科学基金(61902163)
PUF-based Kerberos Extension Protocol with Formal Analysis
ZHANG Zheng1,2( ), ZHA Daren1, LIU Yanan2, FANG Xuming2
), ZHA Daren1, LIU Yanan2, FANG Xuming2
- 1. Institute of Information Engineering, CAS, Beijing 100093, China
2. School of Network Security, Jinling Institute of Technology, Nanjing 211169, China
-
Received:2020-08-02Online:2020-12-10Published:2021-01-12 -
Contact:ZHANG Zheng E-mail:zhangzheng@jit.edu.cn
摘要:
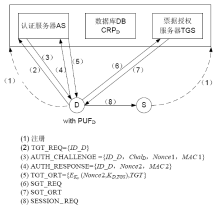
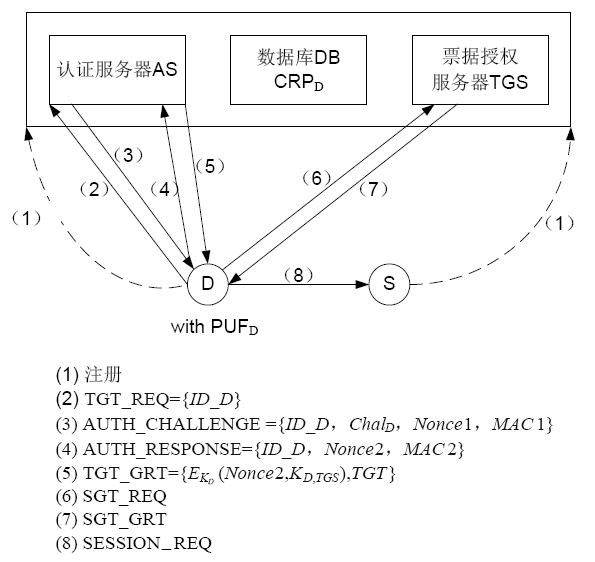
文章提出一种基于物理不可克隆函数(PUF)的Kerberos扩展协议。基于PUF的激励响应认证机制,利用PUF激励响应对代替Kerberos标准协议中的口令或数字证书,可以抵抗口令猜测攻击和假冒攻击。该协议优势在于实现认证服务器与设备的双向认证、设备端无须预存储口令或密钥、降低存储开销和口令或密钥泄露的风险。文章基于BAN逻辑进行形式化分析,证明该协议的安全性;同时与其他协议进行比较,证明该协议能够抵抗物理克隆、建模攻击等威胁。
中图分类号:
引用本文
张正, 查达仁, 柳亚男, 方旭明. 基于物理不可克隆函数的Kerberos扩展协议及其形式化分析[J]. 信息网络安全, 2020, 20(12): 91-97.
ZHANG Zheng, ZHA Daren, LIU Yanan, FANG Xuming. PUF-based Kerberos Extension Protocol with Formal Analysis[J]. Netinfo Security, 2020, 20(12): 91-97.
表2
标准Kerberos协议与本文扩展协议的认证过程比较
| 标准Kerberos协议 | 本文扩展协议 | ||
|---|---|---|---|
| Message1 | TGT_REQ | {ID_Client, password} | {ID_D} |
| Message2 | AUTH_CHALLENGE | —— | {ID_D,ChalD,Nonce1,MAC1} |
| Message3 | AUTH_RESPONSE | —— | {ID_D,Nonce2,MAC2} |
| Message4 | TGT_GRT | $\left\{ {{E}_{{{K}_{D}}}}\left( {{K}_{D,TGS}} \right)\text{ },TGT\text{ } \right\}$ | ${{E}_{{{K}_{D}}}}\left( Nonce2,{{K}_{D,TGS}} \right)\text{ },TGT\text{ }$ |
| [1] | RFC 4120. The Kerberos Network Authentication Service(V5)FC 4120. The Kerberos Network Authentication Service(V5)[S]. USA: IETF, 2005. |
| [2] |
NEEDHAM R M, SCHROEDER M D. Using Encryption for Authentication in Large Networks of Computers[J]. Communications of the ACM, 1978,21(12):993-999.
doi: 10.1145/359657.359659 URL |
| [3] | STEINER J G, NEUMAN B C, SCHILLER J I. Kerberos: An Authentication Service for Network System[EB/OL]. https://ieeexplore.ieee.org/document/312841/references#references, 2020-05-15. |
| [4] | RFC 6113. A Generalized Framework for Kerberos Pre-AuthenticationFC 6113. A Generalized Framework for Kerberos Pre-Authentication[S]. USA: IETF, 2011. |
| [5] | TUNG B, NEUMAN C, HUR M, Public Key Cryptography for Initial Authentication in Kerberos (PKINIT)[EB/OL]. https://www.researchgate.net/publication/243788044_Public_key_cryptography_for_initial_authentication_in_Kerberos, 2020-05-15. |
| [6] | RFC 4556. Public Key Cryptography for Initial Authentication in Kerberos(PKINIT)[S]. USA: IETF, 2006. |
| [7] | GAIKWAD P P, GABHANE J P, GOLAIT S S. 3-level Secure Kerberos Authentication for Smart Home Systems Using IoT[EB/OL]. https://xueshu.baidu.com/usercenter/paper/show?paperid=df202d88fa2d7afc656e4958b5d8c00b&site=xueshu_se, 2020-05-15. |
| [8] | RAO K, BHARADWAJ, RAM N, et al. Application of Time Synchronization Process to Kerberos[J]. Procedia Computer Science, 2016(85):249-254. |
| [9] | SUTRADHAR M R, SULTANA N, DEY H, et al. A New Version of Kerberos Authentication Protocol Using ECC and Threshold Cryptography for Cloud Security[EB/OL]. https://ieeexplore.ieee.org/document/8641010, 2020-05-15. |
| [10] |
JENA S K, TRIPATHY B K, GUPTA P, et al. A Kerberos Based Secure Communication System in Smart (Internet of Things) Environment[J]. Journal of Computational and Theoretical Nanoscience, 2019,16(5):2381-2388.
doi: 10.1166/jctn.2019.7904 URL |
| [11] | DELVAUX J, PEETERS R, GU D, et al. A Survey on Lightweight Entity Authentication with Strong PUFs[J]. ACM Computing Surveys (CSUR), 2015,48(2):1-26. |
| [12] | ABUTALEB M, ALLAM A. FPGA-based Authenticated Key Exchange Scheme Utilizing PUF and CSI for Wireless Networks[EB/OL]. https://xueshu.baidu.com/usercenter/paper/show?paperid=86c0537a937e7aaf801639fd7786bbb2&site=xueshu_se, 2020-05-15. |
| [13] | LIU Dan, GUO Limin, YU Jun, et al. A Secure Mutual Authentication Protocol Based on SRAM PUF[J]. Journal of Cryptologic Research, 2017,4(4):58-69. |
| 刘丹, 郭丽敏, 俞军, 等. 一种基于SRAM PUF的安全双向认证协议[J]. 密码学报, 2017,4(4):58-69. | |
| [14] | WANG Jun, LIU Shubo, LIANG Cai, et al. Two-factor Wearable Device Authentication Protocol Based on PUF and IPI[J]. Journal on Communications, 2017,38(6):127-135. |
| 王俊, 刘树波, 梁才, 等. 基于PUF和IPI的可穿戴设备双因子认证协议[J]. 通信学报, 2017,38(6):127-135. | |
| [15] | CHATTERJEE U, CHAKRABORTY R S, MUKHOPADHYAY D. A PUF Based Secure Communication Protocol for IoT[J]. ACM Transactions on Embedded Computing Systems, 2017,16(3):1-25. |
| [16] |
BRAEKEN A. PUF Based Authentication Protocol for IoT[J]. Symmetry, 2018,10(8):1-15.
doi: 10.3390/sym10010001 URL |
| [17] |
USMANI M A, KESHAVARZ S, MATTHEWS E, et al. Efficient PUF-based Key Generation in FPGAs Using Per-device Configuration[J]. IEEE Transactions on Very Large Scale Integration (VLSI) Systems, 2019,27(2):364-375.
doi: 10.1109/TVLSI.2018.2877438 URL |
| [1] | 余果, 王冲华, 陈雪鸿, 李俊. 认证视角下的工业互联网标识解析安全[J]. 信息网络安全, 2020, 20(9): 77-81. |
| [2] | 王利, 李二霞, 纪宇晨, 李小勇. 基于PUF的抗物理克隆RFID安全认证协议[J]. 信息网络安全, 2020, 20(8): 89-97. |
| [3] | 张骁, 刘吉强. 基于硬件指纹和生物特征的多因素身份认证协议[J]. 信息网络安全, 2020, 20(8): 9-15. |
| [4] | 孙子文, 张向阳. 大规模移动RFID系统Shamir’s密钥共享PUF安全认证协议[J]. 信息网络安全, 2020, 20(6): 26-35. |
| [5] | 刘晓芬, 陈晓峰, 连桂仁, 林崧. 基于d级单粒子的可认证多方量子秘密共享协议[J]. 信息网络安全, 2020, 20(3): 51-55. |
| [6] | 侯林, 冯达, 玄鹏开, 周福才. 基于认证树的外包数据库连接查询验证方案[J]. 信息网络安全, 2020, 20(2): 91-97. |
| [7] | 赵国锋, 周文涛, 徐川, 徐磊. 一种基于双线性配对的天地一体化网络安全身份认证方案[J]. 信息网络安全, 2020, 20(12): 33-39. |
| [8] | 余北缘, 刘建伟, 周子钰. 自组织网络环境下的节点认证机制研究[J]. 信息网络安全, 2020, 20(12): 9-18. |
| [9] | 刘利娟, 李志慧, 支丹利. 可实现身份认证的多方量子密钥分发协议[J]. 信息网络安全, 2020, 20(11): 59-66. |
| [10] | 程洋, 雷敏, 罗群. 基于深度学习的物联网终端设备接入认证方法[J]. 信息网络安全, 2020, 20(11): 67-74. |
| [11] | 李鱼, 韩益亮, 李喆, 朱率率. 基于LWE的抗量子认证密钥交换协议[J]. 信息网络安全, 2020, 20(10): 92-99. |
| [12] | 胡蝶, 马东堂, 龚旻, 马召. 一种基于PUF的物理层安全认证方法[J]. 信息网络安全, 2020, 20(1): 61-66. |
| [13] | 张富友, 王琼霄, 宋利. 基于生物特征识别的统一身份认证系统研究[J]. 信息网络安全, 2019, 19(9): 86-90. |
| [14] | 侯林, 李明洁, 徐剑, 周福才. 基于变长认证跳表的分布式动态数据持有证明模型[J]. 信息网络安全, 2019, 19(7): 67-74. |
| [15] | 亢保元, 颉明明, 司林. 基于生物识别技术的多云服务器认证方案研究[J]. 信息网络安全, 2019, 19(6): 45-52. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||