信息网络安全 ›› 2020, Vol. 20 ›› Issue (12): 83-90.doi: 10.3969/j.issn.1671-1122.2020.12.011
一种针对恶意软件家族的威胁情报生成方法
- 江南大学人工智能与计算机学院,无锡 214122
-
收稿日期:2020-10-14出版日期:2020-12-10发布日期:2021-01-12 -
通讯作者:李志华 E-mail:jswxzhli@aliyun.com -
作者简介:王长杰(1996—),男,江苏,硕士研究生,主要研究方向为物联网安全、信息安全|李志华(1969—),男,湖南,副教授,博士,主要研究方向为云计算、信息安全|张叶(1996—),男,湖南,硕士研究生,主要研究方向为物联网安全、信息安全 -
基金资助:国家自然科学基金(60704047);工业和信息化部智能制造项目(ZH-XZ-180004);中央高校基本科研业务费专项资金(JUSRP211A41);中央高校基本科研业务费专项资金(JUSRP42003);111基地建设项目(B2018)
A Threat Intelligence Generation Method for Malware Family
WANG Changjie, LI Zhihua( ), ZHANG Ye
), ZHANG Ye
- School of Artificial Intelligence and Computer, Jiangnan University, Wuxi 214122, China
-
Received:2020-10-14Online:2020-12-10Published:2021-01-12 -
Contact:LI Zhihua E-mail:jswxzhli@aliyun.com
摘要:
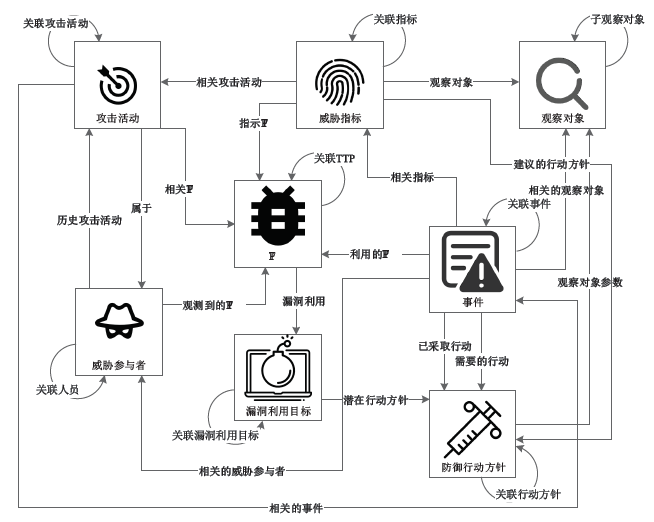
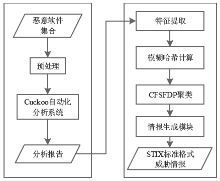
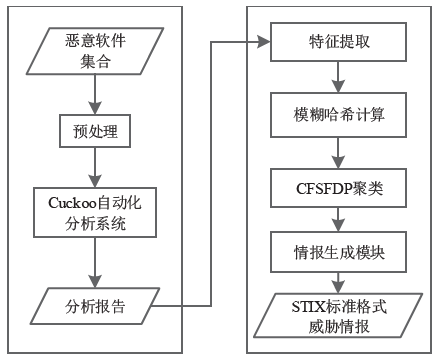
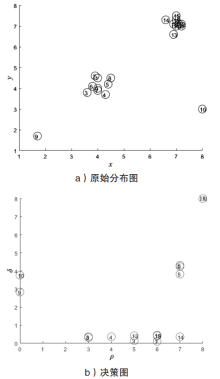
针对目前威胁情报冗余度较高,无法快速生成和共享情报的不足,文章提出一种针对恶意软件家族的威胁情报快速生成方法。该方法通过开源自动化恶意软件分析平台运行恶意软件并提取恶意特征,计算特征模糊哈希值,根据恶意代码的模糊哈希值使用改进的CFSFDP算法对恶意软件进行聚类,最后依据每类恶意软件家族的特征生成符合STIX1.2标准的威胁情报。实验表明,该方法可有效生成可机读、可共享的威胁情报,显著缩短了威胁情报的生成时间。
中图分类号:
引用本文
王长杰, 李志华, 张叶. 一种针对恶意软件家族的威胁情报生成方法[J]. 信息网络安全, 2020, 20(12): 83-90.
WANG Changjie, LI Zhihua, ZHANG Ye. A Threat Intelligence Generation Method for Malware Family[J]. Netinfo Security, 2020, 20(12): 83-90.
表5
恶意软件家族统计
| 家族名 | 样本数量 |
|---|---|
| Win32:Agent-BARL | 78 |
| Win64:Vitro | 46 |
| Win32:Malware-gen | 49 |
| Win64:Trojan-gen | 30 |
| Patched-HO | 50 |
| Win32:Agent-KKQ | 39 |
| AutoRun-BPN | 34 |
| Win64:Evo-gen | 26 |
| Evo-gen | 16 |
| Kryptik-AZZ | 18 |
| Bluehero | 12 |
| Win64:Winnti | 9 |
| Win32:Patched-XF | 6 |
| Win32:Runouce-E | 3 |
| Win32:Patched-AKC | 3 |
| Win32:Flooder-GR | 2 |
| Win64:Adware-gen | 4 |
| Inject-AII | 3 |
表5
| [1] | SYMANTEC. 2019 Symantec Symantec 2019 Internet Security Threat Report[EB/OL]. https://docs.broadcom.com/doc/istr-24-2019-en, 2020-09-28. |
| [2] | YANG Peian, WU Yang, SU Liya, et al. Overview of Threat Intelligence Sharing Technologies in Cyberspace[J]. Computer Science, 2018,45(6):9-18. |
| 杨沛安, 武杨, 苏莉娅, 等. 网络空间威胁情报共享技术综述[J]. 计算机科学, 2018,45(6):9-18. | |
| [3] | HAN Xiaoguang, QU Wu, YAO Xuanxia, et al. Research on Malicious Code Variants Detection Based on Texture Fingerprint[J]. Journal on Communications, 2014,35(8):125-136. |
| 韩晓光, 曲武, 姚宣霞, 等. 基于纹理指纹的恶意代码变种检测方法研究[J]. 通信学报, 2014,35(8):125-136. | |
| [4] | LIAO Xiaojing, YUAN Kan, WANG Xiaofeng, et al. Acing the IOC Game: Toward Automatic Discovery and Analysis of Open-source Cyber Threat Intelligence[C]// ACM. ACM SIGSAC Conference on Computer & Communications Security, October 24-28, 2016, Vienna, Austria. New York: ACM, 2016: 755-766. |
| [5] | SUN Bo, FUJINO A, MORI T, et al. Automatically Generating Malware Analysis Reports Using Sandbox Logs[J]. IEICE Transactions on Information and Systems, 2018,101(11):2622-2632. |
| [6] | ZHANG Yongsheng, WANG Zhi, WU Yijie, et al. Cyber Threat Intelligence Propagation Based on Conformal Prediction[J]. Netinfo Security, 2020,20(6):90-95. |
| [7] | WANG Qinxin, YANG Wang. Extraction of Threat Intelligence Entities Based on STIX[J]. Cyberspace Security, 2020,11(8):86-91. |
| 王沁心, 杨望. 基于STIX标准的威胁情报实体抽取研究[J]. 网络空间安全, 2020,11(8):86-91. | |
| [8] | GBADEBO A, SWARUP C, LATIFUR K, et al. Automated Threat Report Classification over Multi-source Data[C]// IEEE. 4th International Conference on Collaboration and Internet Computing, October 18-20, 2018, Philadelphia, PA, USA. New Jersey: IEEE, 2018: 236-245. |
| [9] | LYU Zongping, ZHONG Youbing, GU Zhaojun. Threat Intelligence Analysis Research Based on Kill Chain and Network Traffic Detection[J]. Application Research of Computers, 2017,34(6):1794-1797. |
| 吕宗平, 钟友兵, 顾兆军. 基于攻击链和网络流量检测的威胁情报分析研究[J]. 计算机应用研究, 2017,34(6):1794-1797. | |
| [10] | KIM E, KIM K, SHIN D, et al. CyTIME: Cyber Threat Intelligence ManagEment Framework for Automatically Generating Security Rules[C]// ACM. 13th International Conference on Future Internet Technologies, June 20-22, 2018, Seoul, Republic of Korea. New York: ACM, 2018: 1-5. |
| [11] | GASCON H, GROBAUER B, SCHRECK T, et al. Mining Attributed Graphs for Threat Intelligence[C]// ACM. The 7th ACM on Conference on Data and Application Security and Privacy, March 22-24, 2017, Scottsdale, Arizona, USA. New York: ACM, 2017: 15-22. |
| [12] | WAGNER C, DULAUNOY A, LKLODY A, et al. MISP-The Design and Implementation of a Collaborative Threat Intelligence Sharing Platform[C]// ACM. 2016 ACM on Workshop on Information Sharing and Collaborative Security, October 24, 2016, Vienna Austria. New York: ACM, 2016: 49-56. |
| [13] | VERMA M, KUMARGURU P, DEB S B, et al. Analysing Indicator of Compromises for Ransomware: Leveraging IOCs with Machine Learning Techniques[C]// IEEE. 2018 IEEE International Conference on Intelligence and Security Informatics, November 9-11, 2018, Miami, FL, USA. New Jersey: IEEE, 2018: 154-159. |
| [14] | RODRIGUEZ A, LAIO A. Clustering by Fast Search and Find of Density Peaks[EB/OL]. http://sites.psu.edu/mcnl/files/2017/03/9-2dhti48.pdf, 2014-06-14. |
| [15] | MITRE. Structured Threat Information eXpression[EB/OL]. https://stixproject.github.io/about/, 2020-09-28. |
| [16] | HUANG Yajuan. Research on Network Threat Intelligence in the United States[D]. Changsha: National University of Defense Technology, 2018. |
| 黄雅娟. 美国网络威胁情报工作研究[D]. 长沙:国防科技大学, 2018. | |
| [17] | CUCKOO Foundation. Automated Mailware Analysis: Cuckoo Sandbox[EB/OL]. https://cuckoo.sh/docs/, 2020-09-28. |
| [18] | KORNBLUM J. Identifying Almost Identical Files Using Context Triggered Piecewise Hashing[EB/OL]. https://www.sciencedirect.com/science/article/pii/S1742287606000764, 2020-09-28. |
| [19] | MITRE. A Python Library for Parsing, Manipulating, and Generating Structured Threat Information eXpression(STIX™) v1.2.0 Content[EB/OL]. https://github.com/STIXProject/python-stix, 2020-09-28. |
| [20] |
SERKETZIS N, KATOS V, LLIOUDIS C, et al. Actionable Threat Intelligence for Digital Forensics Readiness[J]. Information and Computer Security, 2019,27(2):273-291.
doi: 10.1108/ICS-09-2018-0110 URL |
| [1] | 郑东, 赵月. 基于SM3与多特征值的Android恶意软件检测[J]. 信息网络安全, 2020, 20(6): 17-25. |
| [2] | 张永生, 王志, 武艺杰, 杜振华. 基于Conformal Prediction的威胁情报繁殖方法[J]. 信息网络安全, 2020, 20(6): 90-95. |
| [3] | 徐国天, 沈耀童. 基于XGBoost和LightGBM双层模型的恶意软件检测方法[J]. 信息网络安全, 2020, 20(12): 54-63. |
| [4] | 黄保华, 程琪, 袁鸿, 黄丕荣. 基于距离与误差平方和的差分隐私K-means聚类算法[J]. 信息网络安全, 2020, 20(10): 34-40. |
| [5] | 侯留洋, 罗森林, 潘丽敏, 张笈. 融合多特征的Android恶意软件检测方法[J]. 信息网络安全, 2020, 20(1): 67-74. |
| [6] | 宋鑫, 赵楷, 张琳琳, 方文波. 基于随机森林的Android恶意软件检测方法研究[J]. 信息网络安全, 2019, 19(9): 1-5. |
| [7] | 傅彦铭, 李振铎. 基于拉普拉斯机制的差分隐私保护k-means++聚类算法研究[J]. 信息网络安全, 2019, 19(2): 43-52. |
| [8] | 冯胥睿瑞, 刘嘉勇, 程芃森. 基于特征提取的恶意软件行为及能力分析方法研究[J]. 信息网络安全, 2019, 19(12): 72-78. |
| [9] | 张健, 陈博翰, 宫良一, 顾兆军. 基于图像分析的恶意软件检测技术研究[J]. 信息网络安全, 2019, 19(10): 24-31. |
| [10] | 冯新扬, 沈建京. 一种基于Yarn云计算平台与NMF的大数据聚类算法[J]. 信息网络安全, 2018, 18(8): 43-49. |
| [11] | 陆勰, 罗守山, 张玉梅. 基于Hadoop的海量安全日志聚类算法研究[J]. 信息网络安全, 2018, 18(8): 56-63. |
| [12] | 赵薇, 赵娜, 张怡兴. 基于颜色不变特征的谱聚类双分图分割方法[J]. 信息网络安全, 2018, 18(12): 8-14. |
| [13] | 何利, 姚元辉. 基于上下文聚类的云虚拟机异常检测与识别策略[J]. 信息网络安全, 2018, 18(12): 54-65. |
| [14] | 管磊, 胡光俊, 王专. 基于大数据的网络安全态势感知技术研究[J]. 信息网络安全, 2016, 16(9): 45-50. |
| [15] | 王毅, 唐勇, 卢泽新, 俞昕. 恶意代码聚类中的特征选取研究[J]. 信息网络安全, 2016, 16(9): 64-68. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||