信息网络安全 ›› 2026, Vol. 26 ›› Issue (1): 115-124.doi: 10.3969/j.issn.1671-1122.2026.01.010
一种基于P4的多模态网络控制与安全检测方案
李冬1,2, 高源1, 于俊清1,2( ), 曾木虹1, 陈俊鑫1
), 曾木虹1, 陈俊鑫1
- 1.华中科技大学网络空间安全学院,武汉 430074
2.华中科技大学网络与计算中心,武汉 430074
-
收稿日期:2025-06-05出版日期:2026-01-10发布日期:2026-02-13 -
通讯作者:于俊清yjqing@hust.edu.cn -
作者简介:李冬(1979—),男,湖北,高级工程师,博士,主要研究方向为网络安全、软件定义网络及可编程网络|高源(2000—),男,湖北,硕士研究生,主要研究方向为软件定义网络安全|于俊清(1975—),男,内蒙古,教授,博士,CCF会员,主要研究方向为数字媒体处理与检索、网络安全|曾木虹(2001—),男,湖北,硕士研究生,主要研究方向为软件定义网络安全|陈俊鑫(2002—)男,浙江,硕士研究生,主要研究方向为网络安全 -
基金资助:国家重点研发计划(2022YFB2901202)
Polymorphic Network Control and Security Monitor Based on P4
LI Dong1,2, GAO Yuan1, YU Junqing1,2( ), ZENG Muhong1, CHEN Junxin1
), ZENG Muhong1, CHEN Junxin1
- 1. School of Cyber Science and Engineering, Huazhong University of Science and Technology, Wuhan 430074, China
2. Network and Computation Center, Huazhong University of Science and Technology, Wuhan 430074, China
-
Received:2025-06-05Online:2026-01-10Published:2026-02-13
摘要:
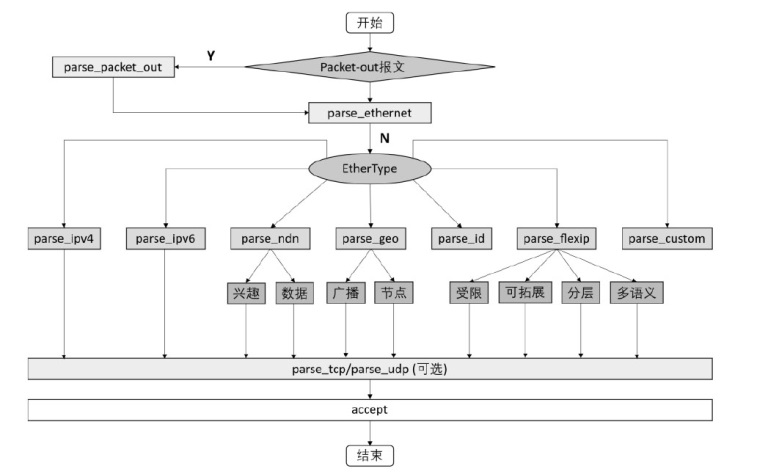
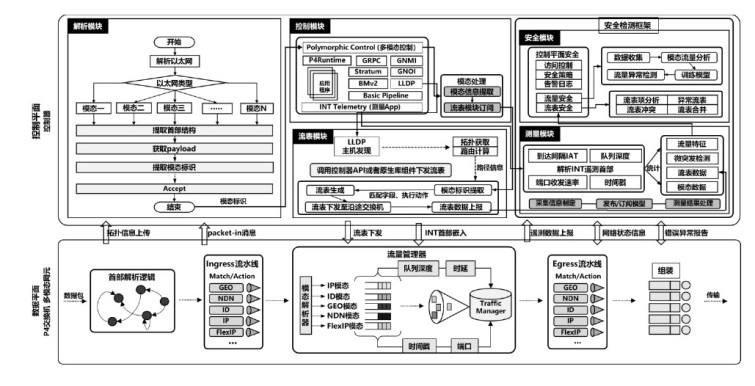
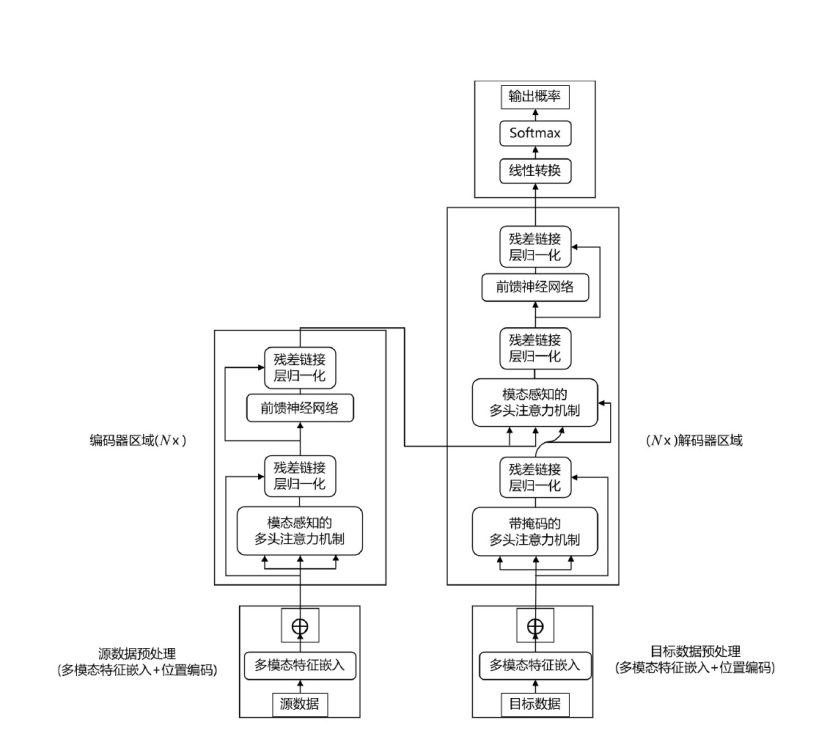
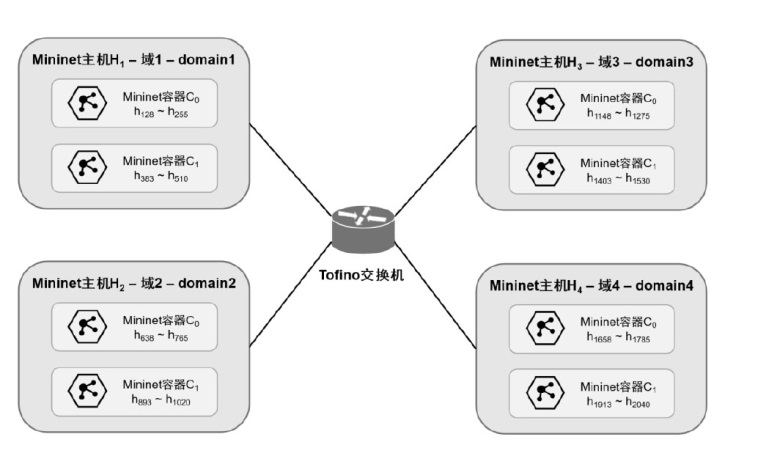
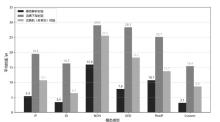
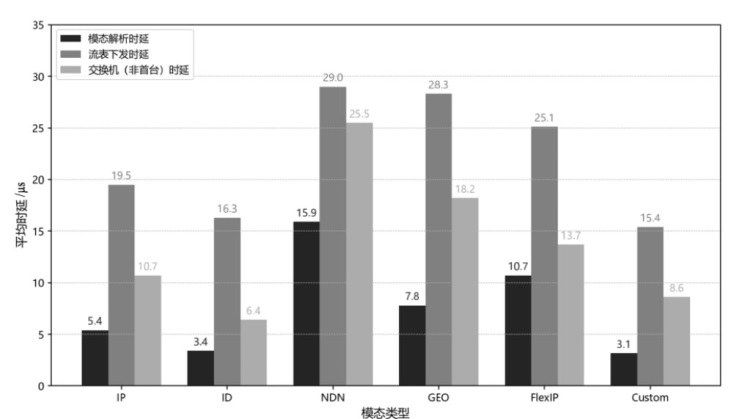
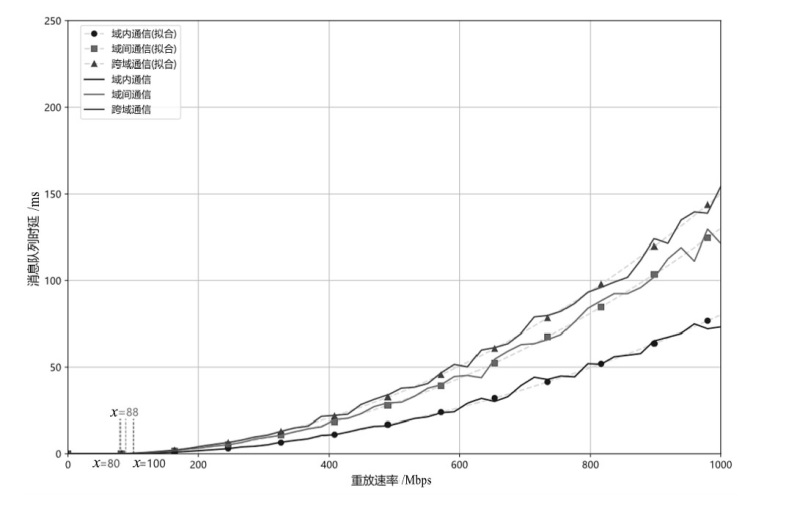
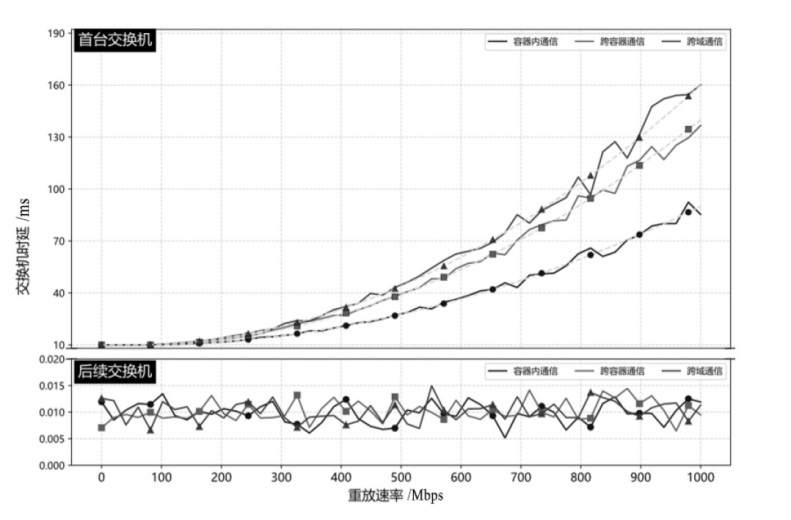
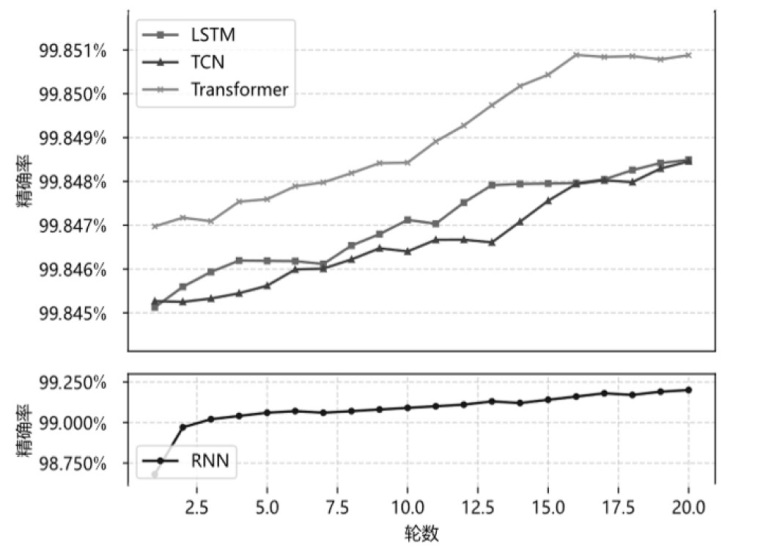
可编程网络技术通过软件定义和编程技术控制网络设备与数据报文,提升网络灵活性、可扩展性和自动化能力,为多模态网络发展奠定基础。文章基于可编程架构设计了身份、内容、地理位置、弹性地址空间、IPv4、IPv6等6种模态的数据报文路由转发机制,并在数据平面实现报文解析、路由寻址与转发。同时,构建多模态网络控制系统,支持报文解析、拓扑管理、流表生成与下发、网络测量等功能,并集成资源协调与调度算法,可实时分析网络状态、计算路由规则并下发流表。文章通过流量特征提取实现安全检测,并基于深度学习构建多模态流量时序模型,实现异常检测与识别,引入内生安全特性,保障系统可用性和可靠性。实验结果表明,文章方案可实现多模态网络统一通信与控制,支持多种模态;控制系统功能完善且性能稳定,拓扑规模超过2000节点,平均端到端时延小于100 ms;安全检测功能可实时识别异常流量与网络模态,其中,异常流量检测准确率达到96.49%,模态识别准确率达到99.72%。
中图分类号:
引用本文
李冬, 高源, 于俊清, 曾木虹, 陈俊鑫. 一种基于P4的多模态网络控制与安全检测方案[J]. 信息网络安全, 2026, 26(1): 115-124.
LI Dong, GAO Yuan, YU Junqing, ZENG Muhong, CHEN Junxin. Polymorphic Network Control and Security Monitor Based on P4[J]. Netinfo Security, 2026, 26(1): 115-124.
表1
控制调度算法相关名称及符号定义
| 符号及名称 | 说明 |
|---|---|
| 流量集合P | 多模态网络中所有模态数据包的集合 |
| 拓扑视图g | 控制平面获取的拓扑整体视图 |
| 路由策略 | 流表模块根据模态标识计算的最佳路径 |
| 消息队列Q | 生产者C ,消费者F |
| 网络状态S | 进行多模态安全测量的网络状态 |
| 测量指标V | 经过网络测量得到的网络指标 |
| 解析模块I | 输入数据包 |
| 控制模块C | |
| 流表模块F | 输入模态标识 流表项 |
| 测量模块T | 输入网络状态 |
| 安全模块S | 输入 |
| [1] | BOSSHART P, DALY D, GIBB G, et al. P4: Programming Protocol-Independent Packet Processors[J]. ACM SIGCOMM Computer Communication Review, 2014, 44(3): 87-95. |
| [2] |
HU Yuxiang, YI Peng, SUN Penghao, et al. Research on a Fully-Definable Multimodal Intelligent Network Architecture[J]. Journal on Communications, 2019, 40(8): 1-12.
doi: 10.11959/j.issn.1000-436x.2019192 |
|
胡宇翔, 伊鹏, 孙鹏浩, 等. 全维可定义的多模态智慧网络体系研究[J]. 通信学报, 2019, 40(8): 1-12.
doi: 10.11959/j.issn.1000-436x.2019192 |
|
| [3] | LI Hui, WU Jiangxing, XING Kaixuan, et al. An Analytical Prototype System for Multimodal Network Identifier and Domain Name Generation and Management with Multi-Party Co-Governance[J]. Science China (Information Sciences), 2019, 49(9): 1186-1204. |
| 李挥, 邬江兴, 邢凯轩, 等. 多边共管的多模态网络标识域名生成管理解析原型系统[J]. 中国科学:信息科学, 2019, 49(9): 1186-1204. | |
| [4] | ZHANG Hongke, QUAN Wei, CHAO H C, et al. Smart Identifier Network: A Collaborative Architecture for the Future Internet[J]. IEEE Network, 2016, 30(3): 46-51. |
| [5] | WU Jiangxing. Reflections on the Development of New-Type Network Technologies[J]. Science China (Information Sciences), 2018, 48(8): 1102-1111. |
| 邬江兴. 新型网络技术发展思考[J]. 中国科学:信息科学, 2018, 48(8): 1102-1111. | |
| [6] | LI Dan, HU Yuxiang, WU Jiangxing. Research on the Innovation and Development Strategy of New-Type Network Technologies[J]. Engineering Sciences, 2021, 23(2): 15-21. |
|
李丹, 胡宇翔, 邬江兴. 新型网络技术创新发展战略研究[J]. 中国工程科学, 2021, 23(2): 15-21.
doi: 10.15302/J-SSCAE-2021.02.003 |
|
| [7] |
YU K, EUM S, KURITA T, et al. Information-Centric Networking: Research and Standardization Status[J]. IEEE Access, 2019, 7: 126164-126176.
doi: 10.1109/ACCESS.2019.2938586 |
| [8] | JACOBSON V, SMETTERS D K, THORNTON J D, et al. Networking Named Content[C]// ACM.The 5th International Conference on Emerging Networking Experiments and Technologies (CoNEXT 2009). New York: ACM, 2009: 1-12. |
| [9] |
ZHANG Lixia, AFANASYEV A, BURKE J, et al. Named Data Networking[J]. ACM SIGCOMM Computer Communication Review, 2014, 44(3): 66-73.
doi: 10.1145/2656877.2656887 URL |
| [10] | YUAN Haowei, SONG Tian, CROWLEY P. Scalable NDN Forwarding:Concepts, Issues and Principles[C]// IEEE. The 21st International Conference on Computer Communications and Networks (ICCCN 2012). New York: IEEE, 2012: 1-9. |
| [11] | REFAEI T, MA J, HA S, et al. Integrating IP and NDN through an Extensible IP-NDN Gateway[C]// ACM.The 4th International Conference on Information-Centric Networking (ICN 2017). New York: ACM, 2017: 224-225. |
| [12] | GUO Xingchang. Research and Implementation of IP and NDN Coexistence and Interworking Mechanisms in Multimodal Networks[D]. Beijing: Beijing Jiaotong University, 2021. |
| 国兴昌. 多模态网络中NDN与IP共存互通机制研究与实现[D]. 北京: 北京交通大学, 2021. | |
| [13] | LIU Ying, REN Gang, WU Jianping, et al. Building an IPv6 Address Generation and Traceback System with NIDTGA in Address Driven Network[J]. Science China Information Sciences, 2015, 45: 1-14. |
| [14] | DONG Fang, CHENG Chengqi, GUO Shide. Design and Research on GeoIP[C]// IEEE. The 14th International Conference on Computer Supported Cooperative Work in Design (CSCWD 2010). New York: IEEE, 2010: 13-17. |
| [15] |
HOU Saifeng, TIAN Le, HU Yuxiang, et al. Geographic Routing and Addressing Scheme for Multi-Source Data Retrieval[J]. Journal of Beijing University of Posts and Telecommunications, 2021, 44(2): 1-7.
doi: 10.13190/j.jbupt.2020-227 |
|
侯赛凤, 田乐, 胡宇翔, 等. 面向多源信息采集的地理位置路由寻址机制[J]. 北京邮电大学学报, 2021, 44(2): 1-7.
doi: 10.13190/j.jbupt.2020-227 |
|
| [16] | LUO Wanming, LIU Shihao, JIA Yihao, et al. Flexible IP: An Adaptable IP Address Structure and Its Efficient Addressing Scheme[J]. Computer Networks, 2022, 203: 87-96. |
| [17] | WU Yunbing, ZENG Weisen, GAO Hang, et al. Multimodal Sarcasm Explanation Survey Based on Dual-Stream Residual Fusion[J]. Journal of Chinese Computer Systems. 2024, 45(11): 2628-2635. |
| 吴运兵, 曾炜森, 高航, 等. 基于双流残差融合的多模态讽刺解释研究[J]. 小型微型计算机系统, 2024, 45 (11): 2628-2635. | |
| [18] |
CAO Xiaoli, LI Yitao, XIONG Xingzhong, et al. Dynamic Routings in Satellite Networks: An Overview[J]. Sensors, 2022, 22(12): 4552-4566.
doi: 10.3390/s22124552 URL |
| [19] | MEDVED J, VARGA R, TKACIK A, et al. OpenDaylight: Towards a Model-Driven SDN Controller Architecture[C]// IEEE. IEEE International Symposium on a World of Wireless, Mobile and Multimedia Networks 2014. New York: IEEE, 2014: 1-6. |
| [20] | BERDE P, GEROLA M, HART J, et al. ONOS:Towards an Open, Distributed SDN OS[C]// ACM. HotSDN ’14:The Third Workshop on Hot Topics in Software Defined Networking. New York: ACM, 2014: 1-6. |
| [21] |
BHARDWAJ S, PANDA S N. Performance Evaluation Using RYU SDN Controller in Software-Defined Networking Environment[J]. Wireless Personal Communications, 2022, 122: 701-723.
doi: 10.1007/s11277-021-08920-3 |
| [22] | REN Hui, LI Xiaoming, GENG Junjie, et al. A SDN-Based Dynamic Traffic Scheduling Algorithm[C]// IEEE. 2016 International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery (CyberC). New York: IEEE, 2016: 514-518. |
| [23] |
BEGAM G S, SANGEETHA M, SHANKER N R. Load Balancing in DCN Servers through SDN Machine Learning Algorithm[J]. Arabian Journal for Science and Engineering, 2022, 47: 1423-1434.
doi: 10.1007/s13369-021-05911-1 |
| [24] |
BAGAA M, DUTRA D, TALEB T, et al. On SDN-Driven Network Optimization and QoS Aware Routing Using Multiple Paths[J]. IEEE Transactions on Wireless Communications, 2020, 19(7): 4700-4714.
doi: 10.1109/TWC.7693 URL |
| [25] | FOSIC I, ZAGAR D, GRGIC K, et al. Anomaly Detection in NetFlow Network Traffic Using Supervised Machine Learning Algorithms[J]. Journal of Industrial Information Integration, 2023, 33: 466-482. |
| [26] |
GIOTIS K, ARGYROPOULOS C, ANDROULIDAKIS G, et al. Combining OpenFlow and SFlow for an Effective and Scalable Anomaly Detection and Mitigation Mechanism on SDN Environments[J]. Computer Networks, 2014, 62: 122-136.
doi: 10.1016/j.bjp.2013.10.014 URL |
| [27] | TAN Lizhuang, SU Wei, ZHANG Zhenyi, et al. In-Band Network Telemetry: A Survey[J]. Computer Networks, 2021, 186: 63-77. |
| [28] | JOSHI R, QU Ting, CHAN M C, et al. BurstRadar: Practical Real-Time Microburst Monitoring for Datacenter Networks[C]// ACM. APSys’18: The 9th Asia-Pacific Workshop on Systems. New York: ACM, 2018: 1-8. |
| [29] |
ILHA A S, LAPOLLI A C, MARQUES J A, et al. Euclid: A Fully In-Network, P4-Based Approach for Real-Time DDoS Attack Detection and Mitigation[J]. IEEE Transactions on Network and Service Management, 2020, 18(3): 3121-3139.
doi: 10.1109/TNSM.2020.3048265 URL |
| [30] | NAM S, LIM J, YOO J, et al. Network Anomaly Detection Based on In-band Network Telemetry with RNN[C]// IEEE. 2020 IEEE International Conference on Consumer Electronics-Asia (ICCE-Asia). New York: IEEE, 2020: 1-4. |
| [31] | SCANO D, PAOLUCCI F, KONDEPU K, et al. Extending P4 In-Band Telemetry to User Equipment for Latency- and Localization-Aware Autonomous Networking with AI Forecasting[J]. Journal of Optical Communications and Networking, 2021, 13(9): 103-114. |
| [32] | TULI S, CASALE G, JENNINGS N R. TranAD: Deep Transformer Networks for Anomaly Detection in Multivariate Time Series Data[J]. VLDB Endowment, 2022, 15(6): 1201-1214. |
| [33] | XU Jiehui, WU Haixu, WANG Jianmin, et al. Anomaly Transformer: Time Series Anomaly Detection with Association Discrepancy[EB/OL]. (2022-04-15)[2025-03-21]. https://ise.thss.tsinghua.edu.cn/-mlong/doc/anomaly-transformer-iclr22.pdf. |
| [34] | SHARAFALDIN I, LASHKARI A H, HAKAK S, et al. Developing Realistic Distributed Denial of Service (DDoS) Attack Dataset and Taxonomy[C]// IEEE.The 53rd IEEE International Carnahan Conference on Security Technology (ICCST). New York: IEEE, 2019: 1-8. |
| [35] | SHARAFALDIN I, LASHKARI A H, GHORBANI A A. Toward Generating a New Intrusion Detection Dataset and Intrusion Traffic Characterization[C]// ACM. The 4th International Conference on Information Systems Security and Privacy (ICISSP). New York: ACM, 2023: 108-116. |
| [1] | 陈红松, 刘新蕊, 陶子美, 王志恒. 基于深度学习的时序数据异常检测研究综述[J]. 信息网络安全, 2025, 25(3): 364-391. |
| [2] | 杨致远, 崔允贺, 陈意, 郭春. 基于探测间隔变化的OpenFlow交换机超时嗅探方法[J]. 信息网络安全, 2025, 25(2): 295-305. |
| [3] | 兰佳晨, 陈夏润, 周杨凯, 文伟平. 多模态网络中的路由技术与协议研究综述[J]. 信息网络安全, 2025, 25(10): 1506-1522. |
| [4] | 周书丞, 李杨, 李传荣, 郭璐璐, 贾辛洪, 杨兴华. 基于上下文的异常根因算法[J]. 信息网络安全, 2024, 24(7): 1062-1075. |
| [5] | 张浩, 谢大智, 胡云晟, 叶骏威. 基于半监督学习的网络异常检测研究综述[J]. 信息网络安全, 2024, 24(4): 491-508. |
| [6] | 王健, 陈琳, 王凯崙, 刘吉强. 基于时空图神经网络的应用层DDoS攻击检测方法[J]. 信息网络安全, 2024, 24(4): 509-519. |
| [7] | 江荣, 刘海天, 刘聪. 基于集成学习的无监督网络入侵检测方法[J]. 信息网络安全, 2024, 24(3): 411-426. |
| [8] | 赵鹏程, 于俊清, 李冬. 一种基于深度学习的SRv6网络流量调度优化算法[J]. 信息网络安全, 2024, 24(2): 272-281. |
| [9] | 何泽平, 许建, 戴华, 杨庚. 联邦学习应用技术研究综述[J]. 信息网络安全, 2024, 24(12): 1831-1844. |
| [10] | 陈宝刚, 张毅, 晏松. 民航空管信息系统用户多因子持续身份可信认证方法研究[J]. 信息网络安全, 2024, 24(11): 1632-1642. |
| [11] | 宋玉涵, 祝跃飞, 魏福山. 一种基于AdaBoost模型的区块链异常交易检测方案[J]. 信息网络安全, 2024, 24(1): 24-35. |
| [12] | 秦中元, 马楠, 余亚聪, 陈立全. 基于双重图神经网络和自编码器的网络异常检测[J]. 信息网络安全, 2023, 23(9): 1-11. |
| [13] | 蒋英肇, 陈雷, 闫巧. 基于双通道特征融合的分布式拒绝服务攻击检测算法[J]. 信息网络安全, 2023, 23(7): 86-97. |
| [14] | 施园, 李杨, 詹孟奇. 一种面向微服务的多维度根因定位算法[J]. 信息网络安全, 2023, 23(3): 73-83. |
| [15] | 吴圣麟, 刘汪根, 严明, 吴杰. 基于无监督系统调用规则生成的容器云实时异常检测系统[J]. 信息网络安全, 2023, 23(12): 91-102. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||