信息网络安全 ›› 2025, Vol. 25 ›› Issue (12): 1889-1900.doi: 10.3969/j.issn.1671-1122.2025.12.005
基于双域多项式框架的随机非线性CPS安全增益调度方法
- 1.南京邮电大学物联网学院,南京 210023
2.南京邮电大学自动化学院,南京 210023
-
收稿日期:2025-09-24出版日期:2025-12-10发布日期:2026-01-06 -
通讯作者:邵邢晨 E-mail:1023051306@njupt.edu.cn -
作者简介:解相朋(1982—),男,山东,教授,博士,主要研究方向为工业控制模糊系统|邵邢晨(2001—),男,江苏,硕士研究生,主要研究方向为工业控制模糊系统 -
基金资助:国家自然科学基金(U25B2056);国家自然科学基金(62373196)
Secure Gain-Scheduling Method for Stochastic Nonlinear CPS Based on Dual-Domain Polynomial Framework
XIE Xiangpeng1, SHAO Xingchen2( )
)
- 1. School of Internet of Things, Nanjing University of Posts and Telecommunications, Nanjing 210023, China
2. College of Automation, Nanjing University of Posts and Telecommunications, Nanjing 210023, China
-
Received:2025-09-24Online:2025-12-10Published:2026-01-06 -
Contact:SHAO Xingchen E-mail:1023051306@njupt.edu.cn
摘要:
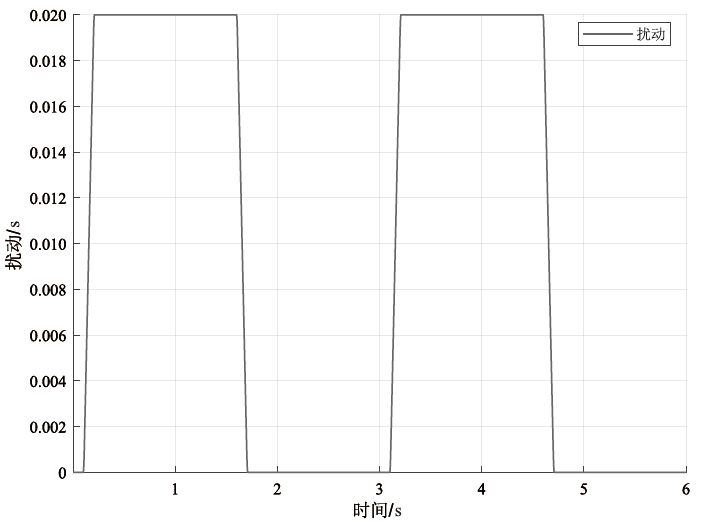
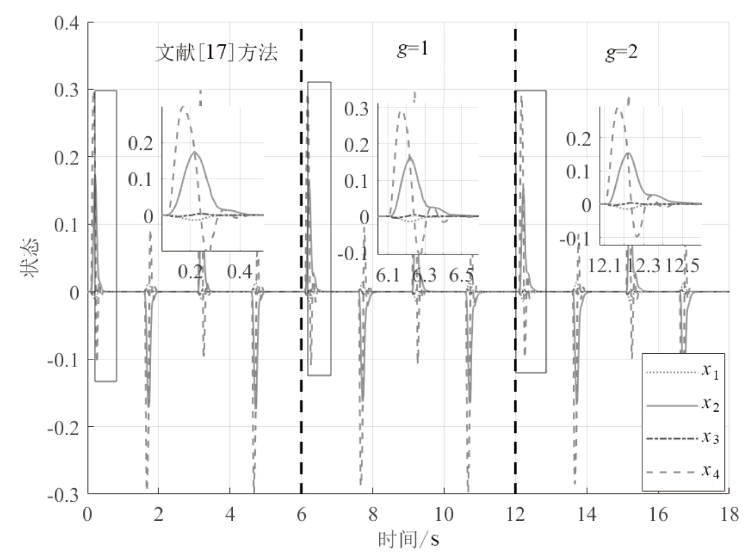
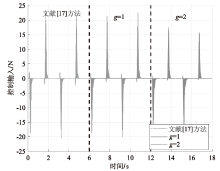
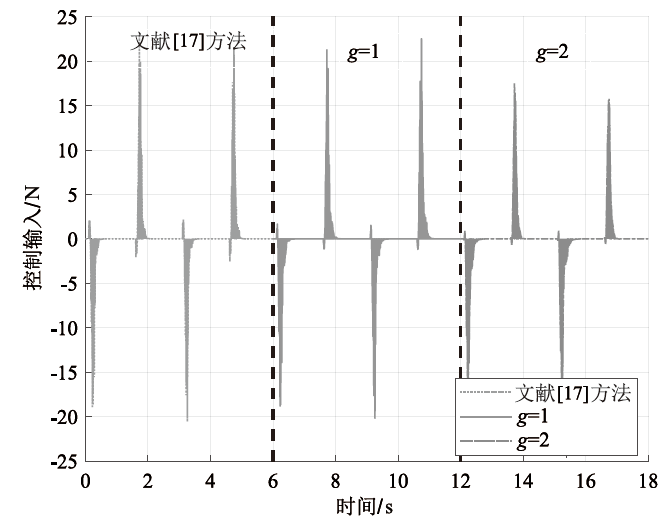
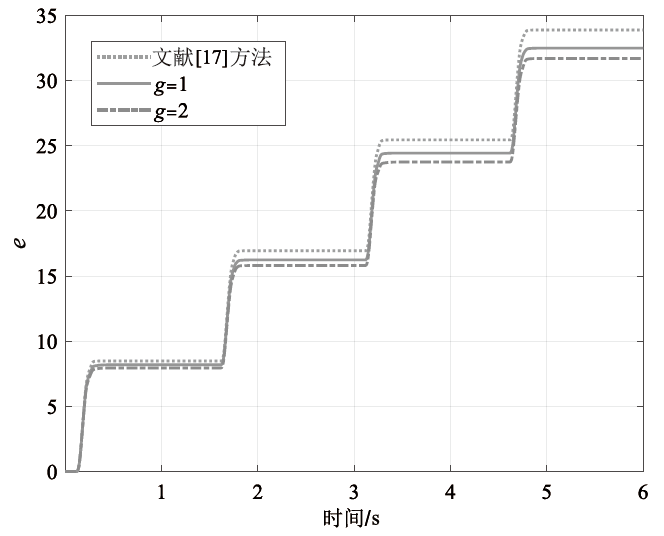
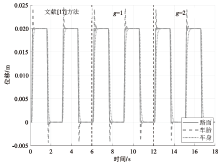
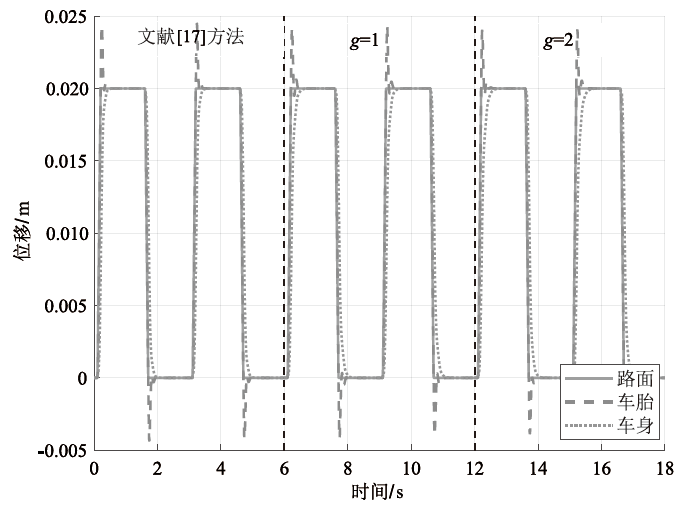
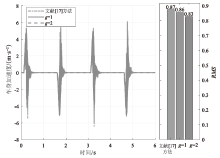
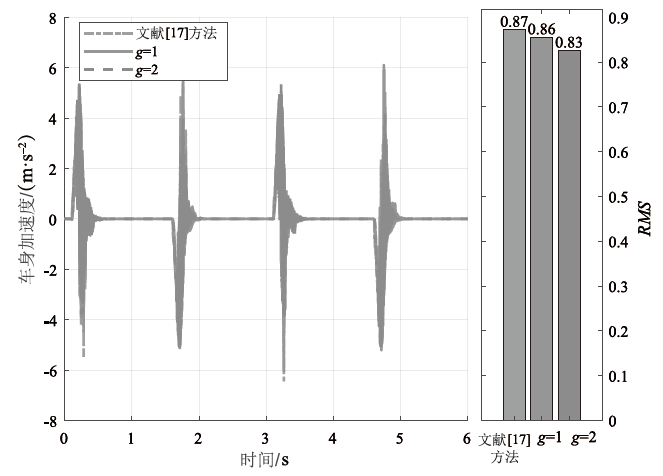
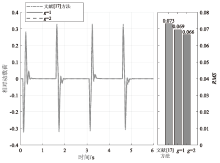
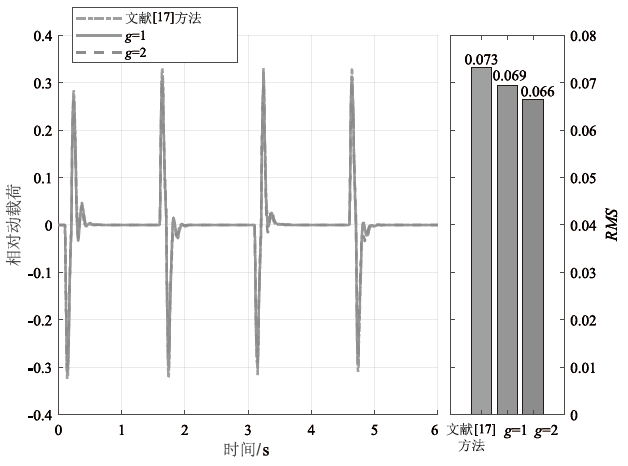
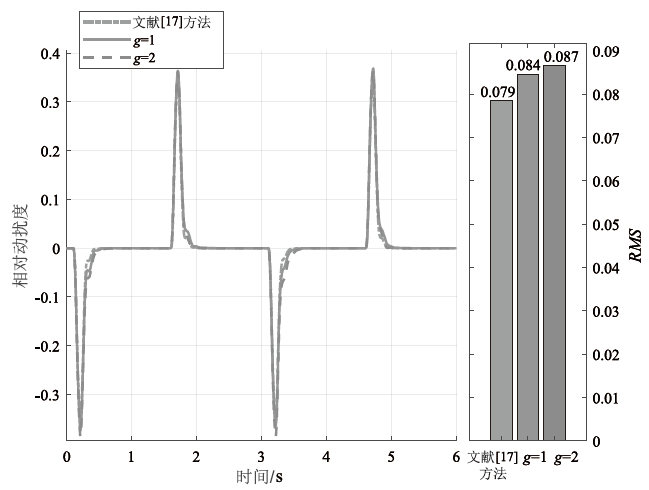
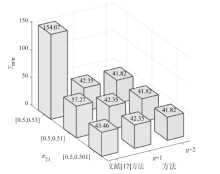
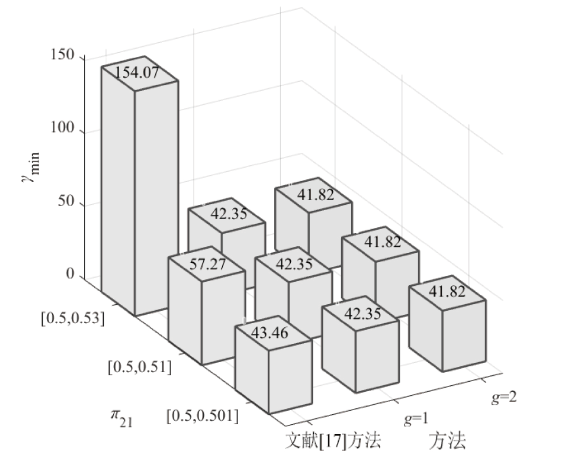
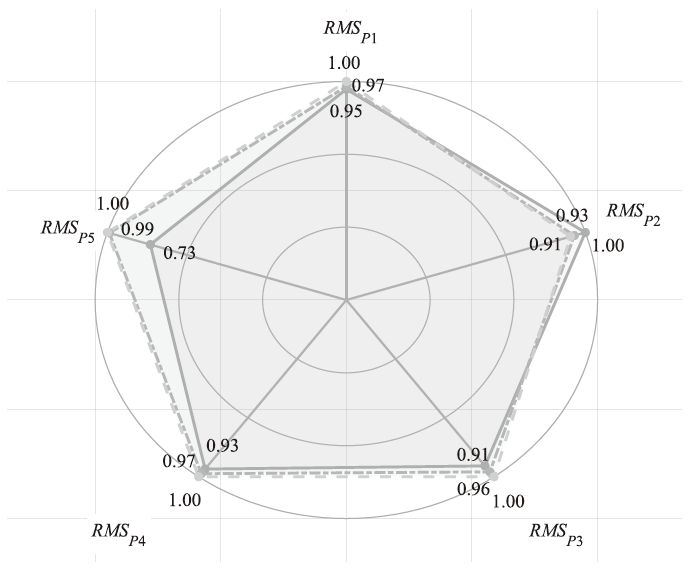
在非线性信息物理系统(CPS)中,随机突变与非线性特性通常同时存在,并受到复杂转移概率与网络攻击的干扰,这为系统的安全与稳定控制带来了严峻挑战。文章提出一种基于双域多项式框架的随机非线性CPS安全增益调度方法,该方法结合模糊建模与马尔可夫跳变系统建立模型,更精确地刻画非线性动态与随机突变行为。在结构域中引入多胞体重构策略,将不精确和部分未知的转移概率转化为多胞体形式,以克服传统方法在复杂概率环境下的局限性。在控制设计域中,利用齐次多项式Lyapunov函数和控制器结构,有效降低设计保守性并提升鲁棒性。理论分析结果表明,该方法在拒绝服务攻击下仍可保证指数均方稳定性与预设性能指标。仿真结果进一步验证了文章所提方法的有效性,显示其在可行解域扩展和性能指标优化方面均优于现有方法,能够为复杂概率与网络威胁环境下的工业CPS安全控制提供一种可行的解决方案。
中图分类号:
引用本文
解相朋, 邵邢晨. 基于双域多项式框架的随机非线性CPS安全增益调度方法[J]. 信息网络安全, 2025, 25(12): 1889-1900.
XIE Xiangpeng, SHAO Xingchen. Secure Gain-Scheduling Method for Stochastic Nonlinear CPS Based on Dual-Domain Polynomial Framework[J]. Netinfo Security, 2025, 25(12): 1889-1900.
| [1] | JIN Zengwang, JIANG Lingyang, DING Junyi, et al. A Review of Research on Industrial Control System Security[J]. Netinfo Security, 2025, 25(3): 341-363. |
| 金增旺, 江令洋, 丁俊怡, 等. 工业控制系统安全研究综述[J]. 信息网络安全, 2025, 25(3):341-363. | |
| [2] |
HUANG Penghao, KIM J, KUMAR P R, et al. Enhancing Cybersecurity for Industrial Control Systems: Innovations in Protecting PLC-Dependent Industrial Infrastructures[J]. IEEE Internet of Things Journal, 2024, 11(22): 36486-36493.
doi: 10.1109/JIOT.2024.3408098 URL |
| [3] |
AHMED I, JEON G, PICCIALLI F. From Artificial Intelligence to Explainable Artificial Intelligence in Industry 4.0: A Survey on What, How, and Where[J]. IEEE Transactions on Industrial Informatics, 2022, 18(8): 5031-5042.
doi: 10.1109/TII.2022.3146552 URL |
| [4] |
JI Zhiduo, CHEN Cailian, HE Jianping, et al. Edge Sensing and Control Co-Design for Industrial Cyber-Physical Systems: Observability Guaranteed Method[J]. IEEE Transactions on Cybernetics, 2022, 52(12): 13350-13362.
doi: 10.1109/TCYB.2021.3079149 URL |
| [5] |
FARIVAR F, HAGHIGHI M S, JOLFAEI A, et al. Artificial Intelligence for Detection, Estimation, and Compensation of Malicious Attacks in Nonlinear Cyber-Physical Systems and Industrial IoT[J]. IEEE Transactions on Industrial Informatics, 2020, 16(4): 2716-2725.
doi: 10.1109/TII.9424 URL |
| [6] | YAN Shen, GU Zhou, PARK J H. Lyapunov-Function-Based Event-Triggered Control of Nonlinear Discrete-Time Cyber-Physical Systems[J]. IEEE Transactions on Circuits and Systems II: Express Briefs, 2022, 69(6): 2817-2821. |
| [7] |
YUAN Xu, YANG Bin, ZHAO Xudong. Adaptive Neural Event-Triggered Fault-Tolerant Control for Uncertain Nonlinear Cyber-Physical Systems with Sensor and Actuator Faults via Triggered Output Feedback[J]. IEEE Transactions on Cybernetics, 2025, 55(8): 3891-3901.
doi: 10.1109/TCYB.2025.3575516 pmid: 40531635 |
| [8] |
CHEN Zebin, YU Zhaoxu, LI Shugang. Output Feedback Adaptive Fuzzy Inverse Optimal Security Control against Sensor and Actuator Attacks for Nonlinear Cyber-Physical Systems[J]. IEEE Transactions on Fuzzy Systems, 2024, 32(5): 2554-2566.
doi: 10.1109/TFUZZ.2024.3353813 URL |
| [9] |
MA Jiawei, ZHANG Huaguang, ZHANG Juan, et al. Event-Based Adaptive Fault-Tolerant Control for Nonlinear Cyber-Physical Systems via Intermittent Available Signals[J]. IEEE Transactions on Automation Science and Engineering, 2025, 22: 19850-19859.
doi: 10.1109/TASE.2025.3598307 URL |
| [10] | ZHANG Meng, SHEN Chao, WU Zhengguang. Asynchronous Observer-Based Control for Exponential Stabilization of Markov Jump Systems[J]. IEEE Transactions on Circuits and Systems II: Express Briefs, 2020, 67(10): 2039-2043. |
| [11] | ZHANG Yifang, WU Zhengguang. Asynchronous Control of Markov Jump Systems under Aperiodic DoS Attacks[J]. IEEE Transactions on Circuits and Systems II: Express Briefs, 2023, 70(2): 685-689. |
| [12] |
WU Zhengguang, SHEN Ying, SHI Peng, et al. ${{\text{H}}_{\infty }}$ Control for 2-D Markov Jump Systems in Roesser Model[J]. IEEE Transactions on Automatic Control, 2019, 64(1): 427-432.
doi: 10.1109/TAC.2018.2831176 URL |
| [13] | SHEN Hao, WU Jiacheng, WANG Yun, et al. Reinforcement Learning-Based Robust Tracking Control for Unknown Markov Jump Systems and Its Application[J]. IEEE Transactions on Circuits and Systems II: Express Briefs, 2023, 71(3): 1211-1215. |
| [14] | BEYHAN S. Fuzzy Emulated Symbolic Regression for Modelling and Control of Markov Jump Systems with Unknown Transition Rates[J]. IEEE Transactions on Circuits and Systems II: Express Briefs, 2022, 69(3): 1352-1356. |
| [15] |
LIU Xinmiao, WANG Zhuping, ZHANG Hao, et al. Asynchronous Sliding Mode Control for Nonlinear Markov Jumping Systems with PDT-Switched Transition Probabilities[J]. IEEE Transactions on Fuzzy Systems, 2023, 31(10): 3598-3609.
doi: 10.1109/TFUZZ.2023.3262064 URL |
| [16] |
TAO Yueyue, CHE Weiwei, WU Zhengguang, et al. Asynchronous Control of 2-D Markov Jump Roesser Systems with Nonideal Transition Probabilities[J]. IEEE Transactions on Cybernetics, 2024, 54(11): 6643-6652.
doi: 10.1109/TCYB.2024.3433522 pmid: 39093678 |
| [17] | TAO Yueyue, WU Zhengguang. Optimal Asynchronous Control of Discrete-Time Hidden Markov Jump Systems with Complex Transition Probabilities[J]. IEEE Transactions on Systems, Man, and Cybernetics: Systems, 2024, 54(2): 1159-1167. |
| [18] | CHEN Da, CAI Xiao, SUN Yanbin, et al. Optimization of Data Conflict and DDoS Attack Defense Mechanisms in Industrial Control Systems Based on Greedy Algorithm[J]. Netinfo Security, 2025, 25(6): 943-954. |
| 陈大, 蔡肖, 孙彦斌, 等. 基于贪心算法优化工业控制系统数据冲突与DDoS攻击防御机制[J]. 信息网络安全, 2025, 25(6):943-954. | |
| [19] |
BI Yannan, WANG Tong, QIU Jianbin, et al. Adaptive Decentralized Finite-Time Fuzzy Secure Control for Uncertain Nonlinear CPSS under Deception Attacks[J]. IEEE Transactions on Fuzzy Systems, 2023, 31(8): 2568-2580.
doi: 10.1109/TFUZZ.2022.3229487 URL |
| [20] |
CUAN Zhaoyang, DING Dawei. Fixed-Time Adaptive Fuzzy Tracking Control for Uncertain Nonlinear Cyber-Physical Systems against Malicious Attacks[J]. IEEE Transactions on Network Science and Engineering, 2024, 11(1): 128-139.
doi: 10.1109/TNSE.2023.3292843 URL |
| [21] |
LI Zhiqiang, LI Qing, DING Dawei, et al. Robust Resilient Control for Nonlinear Systems under Denial-of-Service Attacks[J]. IEEE Transactions on Fuzzy Systems, 2020, 29(11): 3415-3427.
doi: 10.1109/TFUZZ.2020.3022566 URL |
| [22] |
YAN Huaicheng, WANG Jiangning, ZHANG Hao, et al. Event-Based Security Control for Stochastic Networked Systems Subject to Attacks[J]. IEEE Transactions on Systems, Man, and Cybernetics: Systems, 2018, 50(11): 4643-4654.
doi: 10.1109/TSMC.6221021 URL |
| [23] |
ZENG Pengyu, DENG Feiqi, ZHANG Hongyang, et al. Event-Based $H_\infty$Control for Discrete-Time Fuzzy Markov Jump Systems Subject to DoS Attacks[J]. IEEE Transactions on Fuzzy Systems, 2022, 30(6): 1853-1863.
doi: 10.1109/TFUZZ.2021.3069345 URL |
| [1] | 陈大, 蔡肖, 孙彦斌, 董崇武. 基于贪心算法优化工业控制系统数据冲突与DDoS攻击防御机制[J]. 信息网络安全, 2025, 25(6): 943-954. |
| [2] | 申秀雨, 姬伟峰. 考虑安全的边—云协同计算卸载成本优化[J]. 信息网络安全, 2024, 24(7): 1110-1121. |
| [3] | 王健, 陈琳, 王凯崙, 刘吉强. 基于时空图神经网络的应用层DDoS攻击检测方法[J]. 信息网络安全, 2024, 24(4): 509-519. |
| [4] | 江魁, 卢橹帆, 苏耀阳, 聂伟. 基于Attention-GRU的SHDoS攻击检测研究[J]. 信息网络安全, 2024, 24(3): 427-437. |
| [5] | 印杰, 陈浦, 杨桂年, 谢文伟, 梁广俊. 基于人工智能的物联网DDoS攻击检测[J]. 信息网络安全, 2024, 24(11): 1615-1623. |
| [6] | 蒋英肇, 陈雷, 闫巧. 基于双通道特征融合的分布式拒绝服务攻击检测算法[J]. 信息网络安全, 2023, 23(7): 86-97. |
| [7] | 范明钰, 李珂. 一种基于RNN区分DDoS攻击类型的方法[J]. 信息网络安全, 2022, 22(7): 1-8. |
| [8] | 罗文华, 程家兴. 基于Hadoop架构的混合型DDoS攻击分布式检测系统[J]. 信息网络安全, 2021, 21(2): 61-69. |
| [9] | 王健, 王语杰, 韩磊. 基于突变模型的SDN环境中DDoS攻击检测方法[J]. 信息网络安全, 2020, 20(5): 11-20. |
| [10] | 马泽文, 刘洋, 徐洪平, 易航. 基于集成学习的DoS攻击流量检测技术[J]. 信息网络安全, 2019, 19(9): 115-119. |
| [11] | 张可, 汪有杰, 程绍银, 王理冬. DDoS攻击中的IP源地址伪造协同处置方法[J]. 信息网络安全, 2019, 19(5): 22-29. |
| [12] | 喻志彬, 马程, 李思其, 王淼. 基于Web应用层的DDoS攻击模型研究[J]. 信息网络安全, 2019, 19(5): 84-90. |
| [13] | 张雪博, 刘敬浩, 付晓梅. 基于改进Logistic回归算法的抗Web DDoS攻击模型的设计与实现[J]. 信息网络安全, 2017, 17(6): 62-67. |
| [14] | 李洁, 许鑫, 陈宇, 张丁文. 模拟DDoS攻击场景下的云取证模型的研究[J]. 信息网络安全, 2015, 15(6): 67-72. |
| [15] | 滕希龙, 曲海鹏. 基于区间值直觉模糊集相似性的信息安全风险评估方法研究[J]. 信息网络安全, 2015, 15(5): 62-68. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||