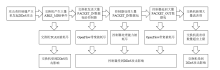
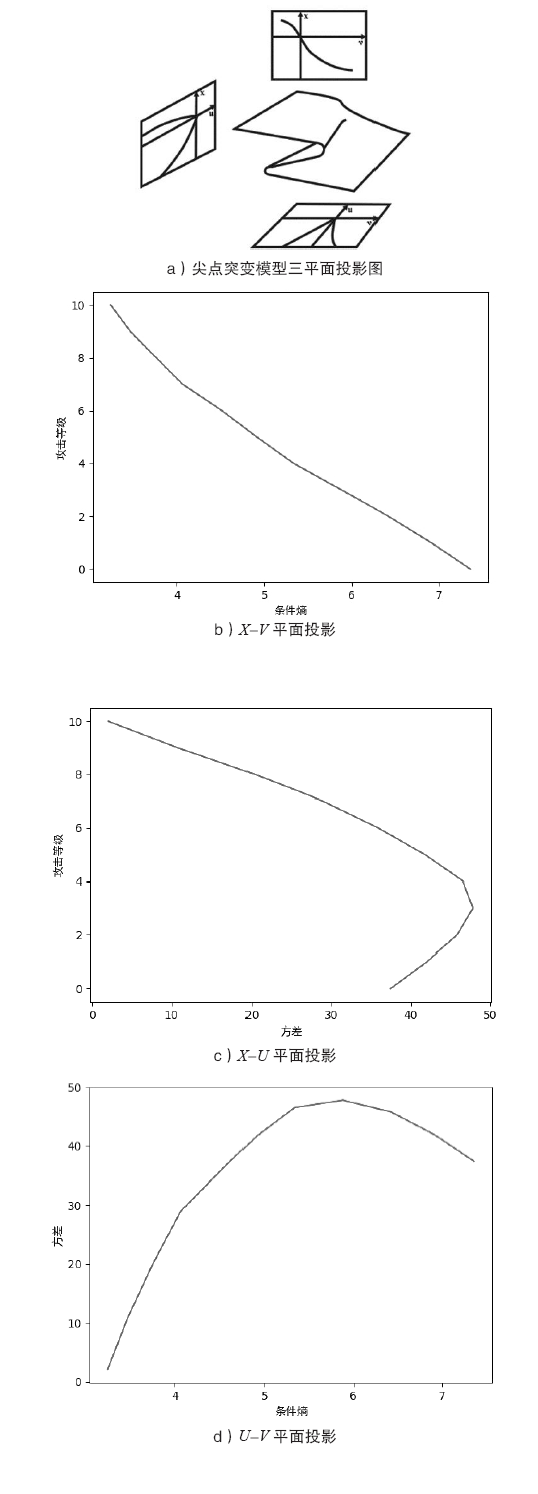
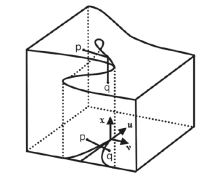
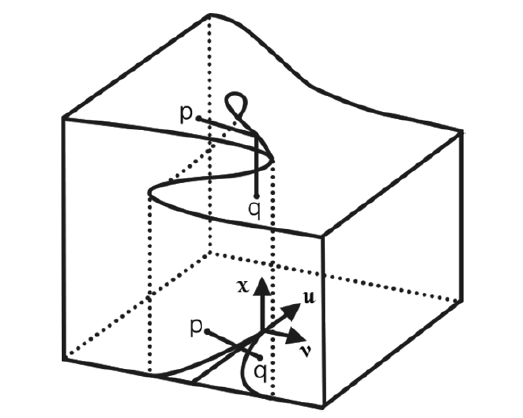
信息网络安全 ›› 2020, Vol. 20 ›› Issue (5): 11-20.doi: 10.3969/j.issn.1671-1122.2020.05.002
基于突变模型的SDN环境中DDoS攻击检测方法
- 1. 北京交通大学智能交通数据安全与隐私保护技术北京市重点实验室,北京 100044
2. 北京交通大学计算机与信息技术学院,北京 100044
3. 北京计算机技术及应用研究所,北京 100854
-
收稿日期:2020-03-18出版日期:2020-05-10发布日期:2020-06-05 -
通讯作者:王健 E-mail:wangjian@bjtu.edu.cn -
作者简介:王健(1975—),男,山东,副教授,博士,主要研究方向为网络安全、密码应用、智能计算;|王语杰(1996—),男,北京,硕士研究生,主要研究方向为大数据与物联网安全|韩磊(1983—),男,河北,高级工程师,博士,主要研究方向为信息安全、密码应用、智能算法安全等 -
基金资助:国家自然科学基金(61672092);中央高校基本科研业务费(2018JBZ103);山东省重大科技创新工程(2019JZZY020128)
DDoS Attack Detection Based on Catastrophe Theory in SDN Environment
WANG Jian1,2,*( ), WANG Yujie1,2, HAN Lei3
), WANG Yujie1,2, HAN Lei3
- 1. Beijing Key Laboratory of Security and Privacy in Intelligent Transportation, Beijing Jiaotong University, Beijing 100044, China
2. School of Computer and Information Technology, Beijing Jiaotong University, Beijing 100044, China
3. Beijing Institute of Computer Technology and Applications, Beijing 100854, China
-
Received:2020-03-18Online:2020-05-10Published:2020-06-05 -
Contact:Jian WANG E-mail:wangjian@bjtu.edu.cn
摘要:
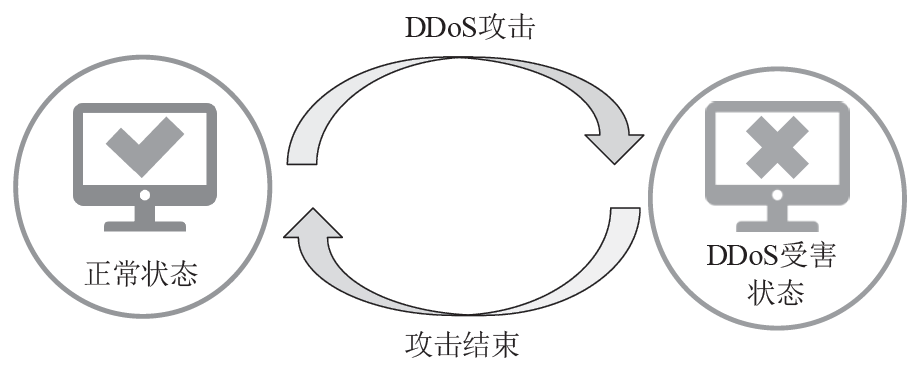
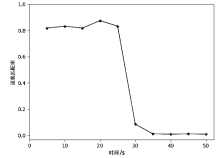
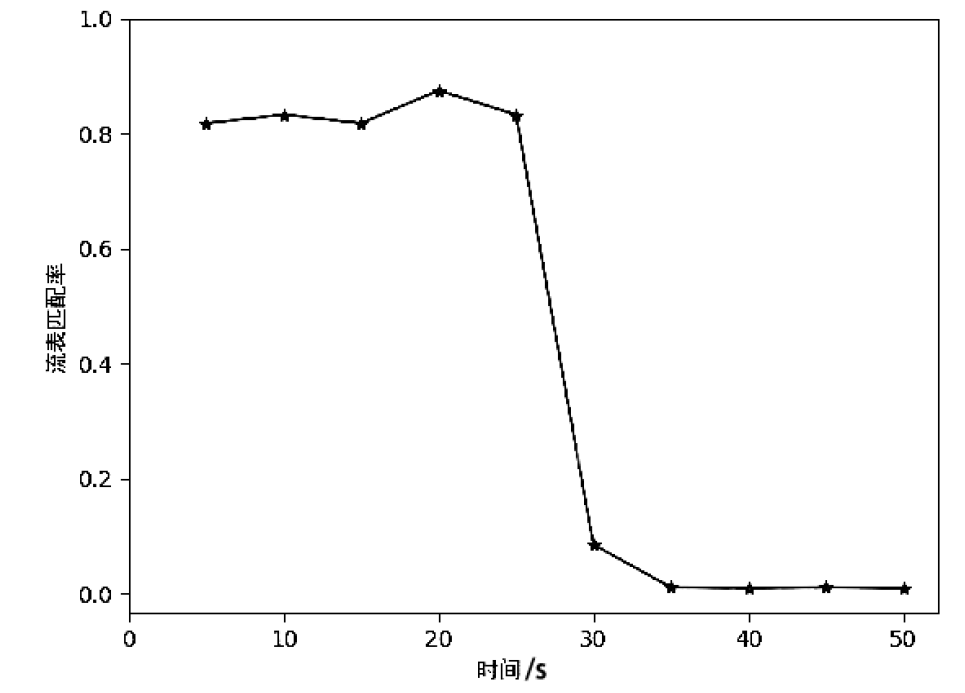
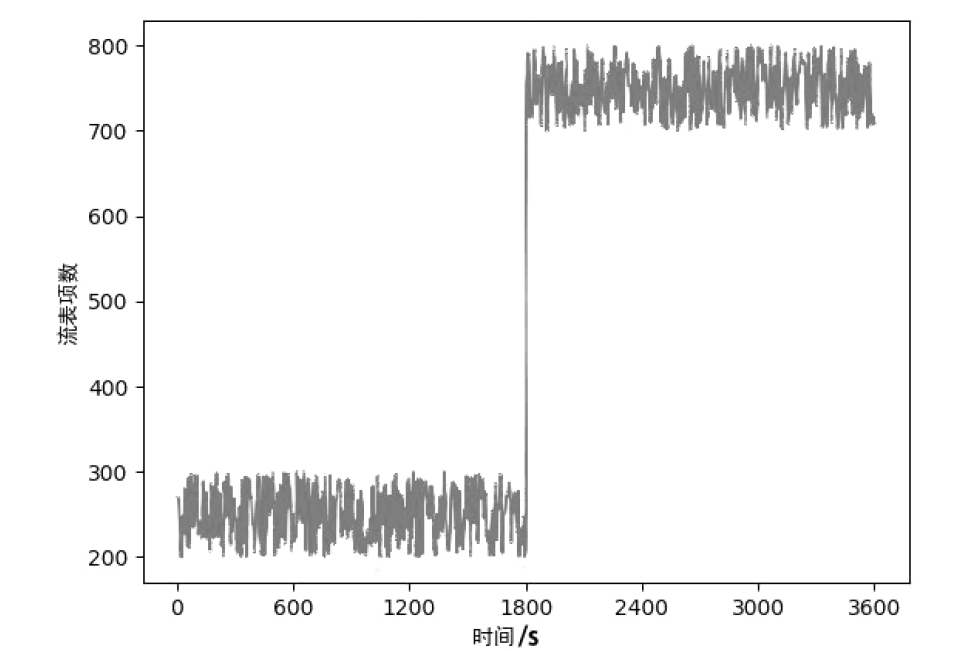
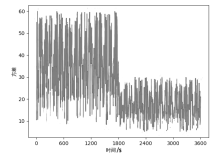
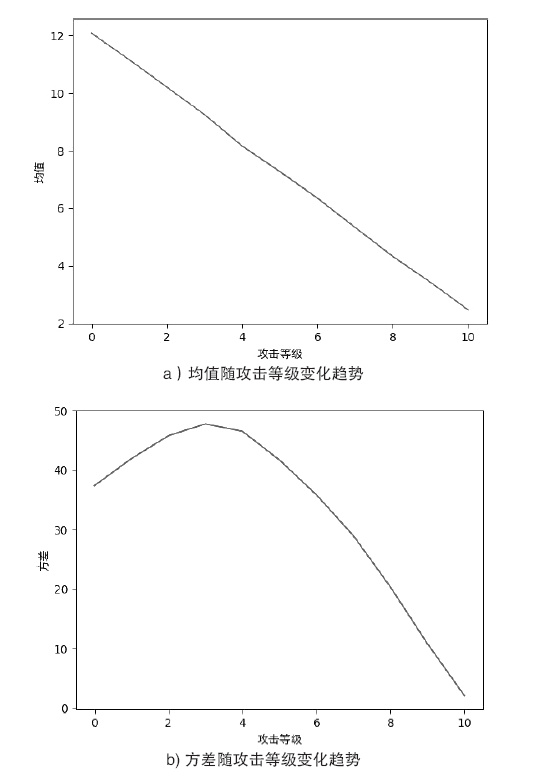
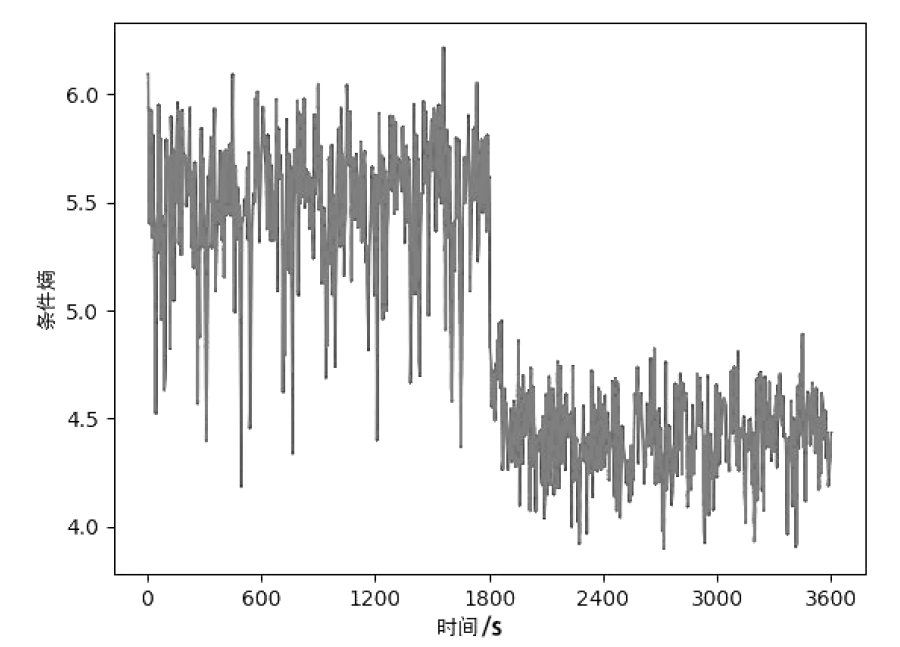
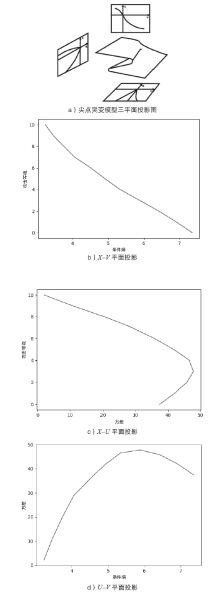
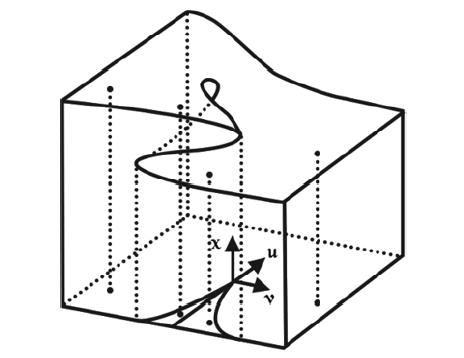
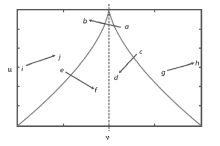
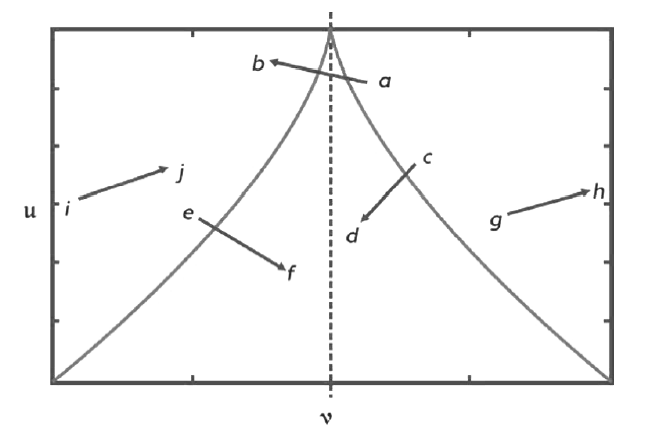
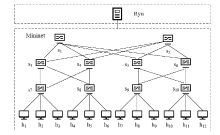
文章提出一种基于尖点突变模型的DDoS攻击检测方法,通过分析DDoS攻击的行为特征和SDN下流表的特点,对该模型提出了基于流表的改良型控制变量和状态变量。最后通过仿真实验采集的数据,与常见方法进行多次对比实验,通过对实验结果进行分析可知,该方法可以有效检测DDoS攻击,并且相较于其他方法在具有较高检测率的同时拥有较低的误报率。
中图分类号:
引用本文
王健, 王语杰, 韩磊. 基于突变模型的SDN环境中DDoS攻击检测方法[J]. 信息网络安全, 2020, 20(5): 11-20.
WANG Jian, WANG Yujie, HAN Lei. DDoS Attack Detection Based on Catastrophe Theory in SDN Environment[J]. Netinfo Security, 2020, 20(5): 11-20.
| [1] | DONG Shi, ABBAS K, JAIN R . A Survey on Distributed Denial of Service(DDoS) Attacks in SDN and Cloud Computing Environments[J]. IEEE Access, 2019(7):80813-80828. |
| [2] | CHEN K Y, JUNUTHULA A R, SIDDHRAU I K , et al. SDNShield: Towards More Comprehensive Defense Against DDoS Attacks on SDN Control Plane [C]//IEEE. IEEE Conference on Communications and Network Security, October 17-19, 2016, Philadelphia, PA, USA. New Jersey: IEEE, 2016: 28-36. |
| [3] | SAKIR S, SANDRA S H, PUSHPINDER K C , et al. Are We Ready for SDN? Implementation Challenges for Software-Defined Networks[J]. IEEE Communications Magazine, 2013,51(7):36-43. |
| [4] | DHARMA N I G, MUTHOHAR M F, PRAYUDA J D A , et al. Time-based DDoS Detection and Mitigation for SDN Controller [C]//IEEE. 17th Asia-Pacific Network Operations and Management Symposium, August 19-21, 2015, Busan, South Korea. New Jersey: IEEE, 2015: 550-553. |
| [5] | BENTON K, CAMP L J, SMALL C . Open Flow Vulnerability Assessment [C]//ACM. ACM SIGCOMM Workshop on Hot Topics in Software Defined Networking, August 16, 2013, Hong Kong, China. New York: ACM, 2013: 151-152. |
| [6] | WANG Haopei, XU Lei, GU Guofei . FloodGuard: A DoS Attack Prevention Extension in Software-defined Networks [C]//IEEE/IFIP. 45th Annual IEEE/IFIP International Conference on Dependable Systems and Networks, June 22-25, 2015, Rio de Janeiro, Brazil. New Jersey: IEEE, 2015: 239-250. |
| [7] | GIOTIS K, ARGYROPOULOS C, ANDROULIDAKIS G , et al. Combining OpenFlow and sFlow for an Effective and Scalable Anomaly Detection and Mitigation Mechanism on SDN Environments[J]. Computer Networks, 2014(62):122-136. |
| [8] | ZHENG Shiji . Research on SDN-based IoT Security Architecture Model [C]//IEEE. IEEE 8th Joint International Information Technology and Artificial Intelligence Conference, May 24-26, 2019, Chongqing, China. New Jersey: IEEE, 2019: 575-579. |
| [9] | BRAGA R, MOTA E, PASSITO A . Lightweight DDoS Flooding Attack Detection Using NOX/OpenFlow [C]//IEEE. The 35th Annual IEEE Conference on Local Computer Networks, October 10-14, 2010, Denver, CO, USA. New Jersey: IEEE, 2010: 408-415. |
| [10] | JIANG Wenti, GU Yu, REN Danni , et al. DDoS Attacks and Flash Crowds Detection Based on Flow Characteristics in SDN[J]. Journal of Chongqing University of Posts and Telecommunications(Natural Science Edition), 2019,31(3):420-426. |
| 姜文醍, 谷宇, 任丹妮 , 等. SDN中基于流特征的DDoS攻击与闪拥事件检测[J]. 重庆邮电大学学报(自然科学版), 2019,31(3):420-426. | |
| [11] | LI Chuanhuang, WU Yan, YUAN Xiaoyong , et al. Detection and Defense of DDoS Attack-based on Deep Learning in OpenFlow-based SDN[EB/OL]. http://smartsearch.nstl.gov.cn/paper_detail.html?id=f9f7fd77d39aaea3e4dcb5c026a490c6, 2019-9-11. |
| [12] | AERTS D, CZACHOR M, GABORA M , et al. Quantum Morphogenesis: A Variation on Thom’s Catastrophe Theory[EB/OL]. https://arxiv.org/pdf/quant-ph/0211105v2.pdf, 2019-9-12 |
| [13] | GUO Yi, MIAO FU, ZHANG Liancheng , et al. CATH: An Effective Method for Detecting Denial-of-Service Attacks in Software Defined Networks[J]. Science China Information Sciences, 2019,62(3):75-89. |
| [14] | QI Liuling . Research of DDoS Attack Detection Method Based on Entropy and Neural Networks in SDN[D]. Baoding: Hebei University, 2018. |
| 齐鎏岭 . SDN中基于熵和神经网络的DDoS攻击检测方法研究[D]. 保定:河北大学, 2018. | |
| [15] | HU Wusheng . IP Network Anomalous Behavior Detection and Mechanism Based on Catastrophe Theory[D]. Chengdu: University of Electronic Science and Technology of China, 2010. |
| 胡武生 . 基于突变理论的IP网络异常行为检测和控制机制[D]. 成都:电子科技大学, 2010. | |
| [16] | IMAN S, ARASH H L, SAQIB H , et al. Developing Realistic Distributed Denial of Service(DDoS) Attack Dataset and Taxonomy [C]//IEEE. IEEE 53rd International Carnahan Conference on Security Technology, October 1-3, 2019, Chennai, India. New Jersey: IEEE, 2019: 1-8. |
| [1] | 周亚球, 任勇毛, 李琢, 周旭. 基于SDN的科学DMZ研究与实现[J]. 信息网络安全, 2019, 19(9): 134-138. |
| [2] | 张可, 汪有杰, 程绍银, 王理冬. DDoS攻击中的IP源地址伪造协同处置方法[J]. 信息网络安全, 2019, 19(5): 22-29. |
| [3] | 喻志彬, 马程, 李思其, 王淼. 基于Web应用层的DDoS攻击模型研究[J]. 信息网络安全, 2019, 19(5): 84-90. |
| [4] | 赖成喆, 王文娟. 面向车队的安全且具备隐私保护的移动性管理框架[J]. 信息网络安全, 2018, 18(7): 36-46. |
| [5] | 石悦, 李相龙, 戴方芳. 一种基于属性基加密的增强型软件定义网络安全框架[J]. 信息网络安全, 2018, 18(1): 15-22. |
| [6] | 李剑锋, 刘渊, 张浩, 王晓锋. 面向IaaS云平台的路由转发优化研究与实现[J]. 信息网络安全, 2017, 17(9): 10-15. |
| [7] | 张雪博, 刘敬浩, 付晓梅. 基于改进Logistic回归算法的抗Web DDoS攻击模型的设计与实现[J]. 信息网络安全, 2017, 17(6): 62-67. |
| [8] | 徐洋, 陈燚, 何锐, 谢晓尧. SDN中DDoS检测及多层防御方法研究[J]. 信息网络安全, 2017, 17(12): 22-28. |
| [9] | 齐宇. SDN安全研究[J]. 信息网络安全, 2016, 16(9): 69-72. |
| [10] | 陈颖聪, 陈广清, 陈智明, 万能. 面向智能电网SDN的二进制代码分析漏洞扫描方法研究[J]. 信息网络安全, 2016, 16(7): 35-39. |
| [11] | 蒋宽, 杨鹏. 基于数据包回溯的软件定义网络中的故障排除[J]. 信息网络安全, 2016, 16(3): 71-76. |
| [12] | 武泽慧, 魏强. 基于OwnShip-Proof模型的软件定义网络控制器集群故障安全恢复方法[J]. 信息网络安全, 2016, 16(12): 13-18. |
| [13] | 王刚. 一种基于SDN技术的多区域安全云计算架构研究[J]. 信息网络安全, 2015, 15(9): 20-24. |
| [14] | 周益周, 王斌, 谢小权. 云环境下软件定义入侵检测系统设计[J]. 信息网络安全, 2015, 15(9): 191-195. |
| [15] | 李洁, 许鑫, 陈宇, 张丁文. 模拟DDoS攻击场景下的云取证模型的研究[J]. 信息网络安全, 2015, 15(6): 67-72. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||