信息网络安全 ›› 2015, Vol. 15 ›› Issue (6): 67-72.doi: 10.3969/j.issn.1671-1122.2015.06.011
模拟DDoS攻击场景下的云取证模型的研究
- 1.国网吉林省电力有限公司电力科学研究院,吉林长春 130021
2.吉林大学计算机科学与技术学院,吉林长春 130012
Research on Cloud Forensics Model under the Simulation DDoS Attack Scenarios
LI Jie1, XU Xin1, CHEN Yu1, ZHANG Ding-wen2( )
)
- 1.Jilin Grid Electric Power Research Institute of China Grid, Changchun Jilin 130021, China
2. College of Computer Science and Technology, Jilin University, Changchun Jilin 130012, China
摘要:
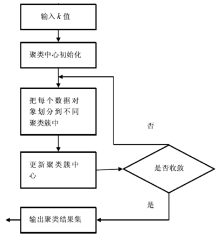
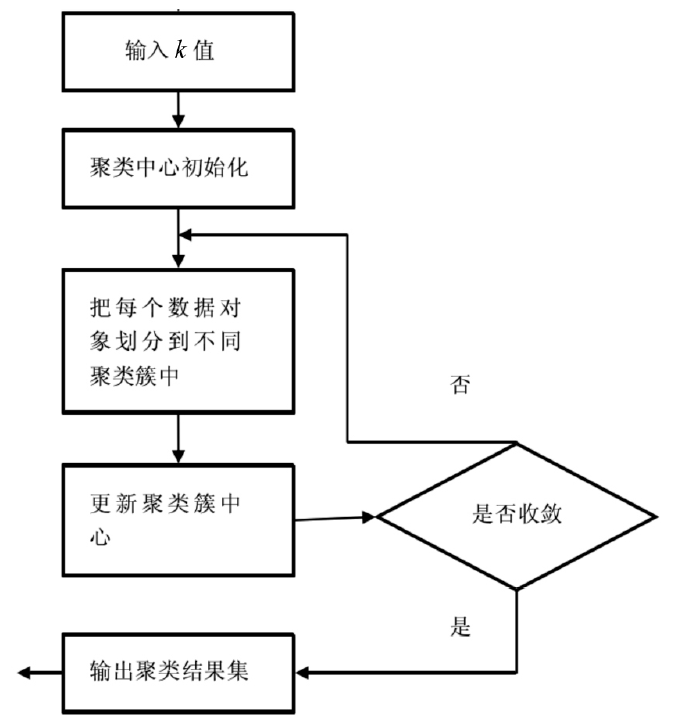
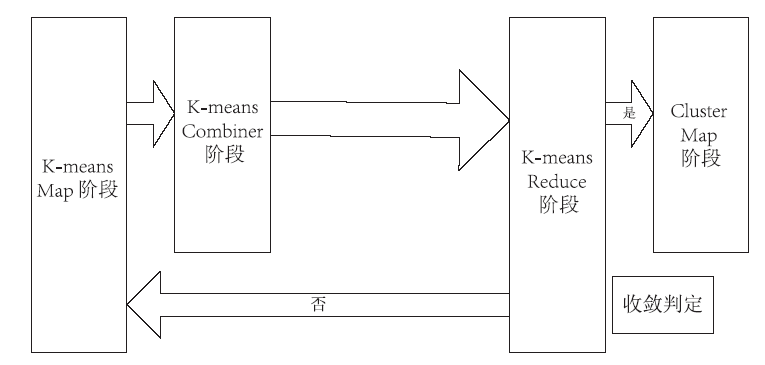
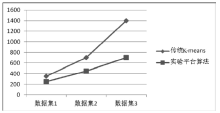
云计算是一种新型的计算概念,它以开放的标准和服务为基础,以互联网为中心,让互联网上的各种计算资源协同工作,共同组成数个庞大的数据中心和计算中心,为各类用户提供安全、快速、便捷的数据存储和网络计算等特定服务。云计算环境下互联网面临着更多的计算机犯罪问题,给取证工作带来了极大的挑战:一方面要对已经发生的攻击进行证据的收集与分析,另一方面也为防范攻击的技术手段收集实验数据。云计算环境是攻击者新的攻击对象,一旦攻击成功,其带来的损失将直接影响最终用户的数据安全性和数据完整性。在众多攻击当中,DDos攻击是云计算平台最容易发生且难以防范的攻击之一。因此,文章针对云环境面临的DDoS攻击问题展开研究,对相关工作进行总结,提出了一种模拟DDoS攻击场景下的云取证框架模型。
中图分类号: