信息网络安全 ›› 2023, Vol. 23 ›› Issue (4): 61-71.doi: 10.3969/j.issn.1671-1122.2023.04.007
云环境下基于秘密共享的安全外包主成分分析方案
- 1.海军工程大学信息安全系,武汉 430033
2.湖北开放大学软件工程学院,武汉 430074
3.国防大学联合作战学院,石家庄 050084
-
收稿日期:2022-12-27出版日期:2023-04-10发布日期:2023-04-18 -
通讯作者:付钰 E-mail:fuyu0219@163.com -
作者简介:马敏(1979—),女,江苏,副教授,博士研究生,主要研究方向为信息安全|付钰(1982—),女,湖北,教授,博士,主要研究方向为人工智能与网络安全|黄凯(1986—),男,安徽,讲师,博士,主要研究方向为信息安全与人工智能。 -
基金资助:国家自然科学基金(62102422)
A Principal Component Analysis Scheme for Security Outsourcing in Cloud Environment Based on Secret Sharing
MA Min1,2, FU Yu1( ), HUANG Kai3
), HUANG Kai3
- 1. Department of Information Security, Naval University of Engineering, Wuhan 430033, China
2. Department of Software Engineering, The Hubei Open University, Wuhan 430074, China
3. College of Joint Operation, National Defense University, Shijiazhuang 050084, China
-
Received:2022-12-27Online:2023-04-10Published:2023-04-18 -
Contact:FU Yu E-mail:fuyu0219@163.com
摘要:
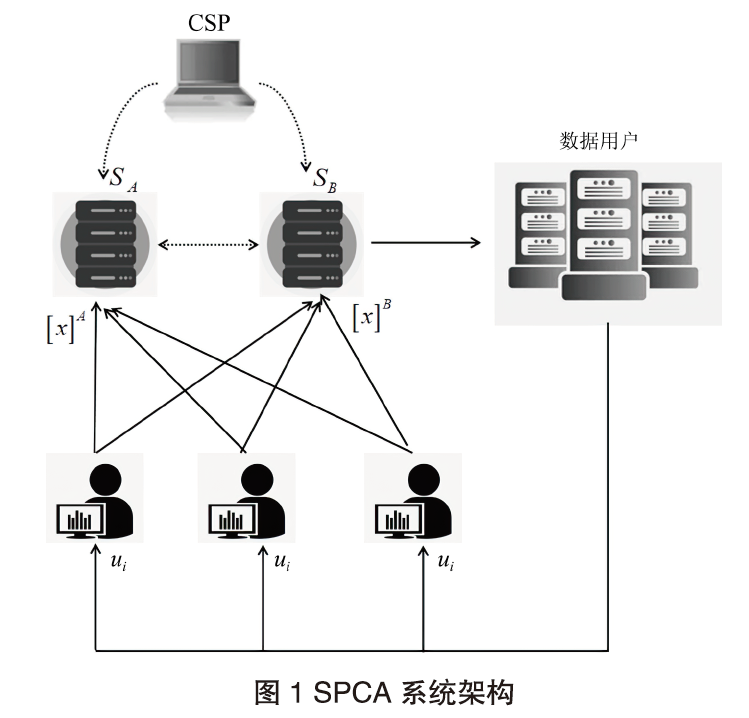
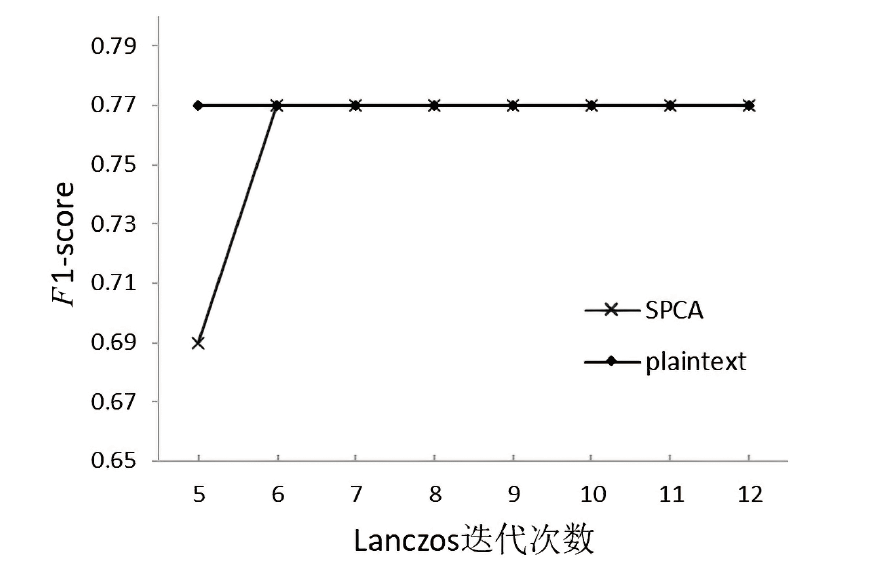
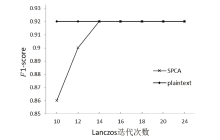
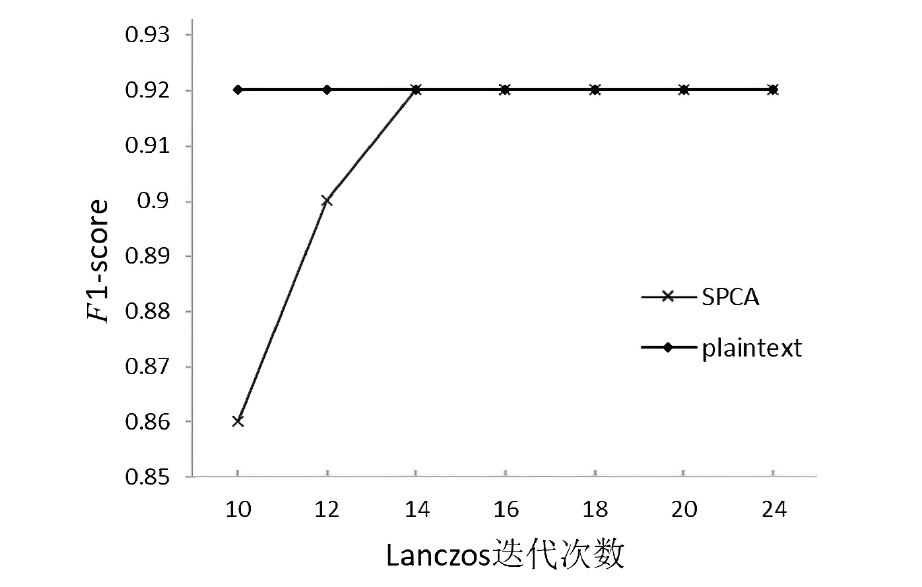
主成分分析技术的计算开销较大,本地设备一般无法负担,常需要将计算任务进行外包,而外包计算的数据安全问题已成为云计算安全领域的一个研究热点。文章提出一种云环境下基于秘密共享的安全外包主成分分析方案,该方案基于加法秘密共享技术,设计了安全除法和安全平方根计算协议。通过两台云服务器协同执行协方差矩阵、Lanczos、Householder等安全协议计算,实现了主成分分析安全外包计算。与其他安全外包计算方案相比,文章所提方案可以更好地支持客户端离线和多方数据聚合,其计算开销更小,并通过实验验证了方案的有效性。
中图分类号:
引用本文
马敏, 付钰, 黄凯. 云环境下基于秘密共享的安全外包主成分分析方案[J]. 信息网络安全, 2023, 23(4): 61-71.
MA Min, FU Yu, HUANG Kai. A Principal Component Analysis Scheme for Security Outsourcing in Cloud Environment Based on Secret Sharing[J]. Netinfo Security, 2023, 23(4): 61-71.
使用本文
| [1] |
LI Fenghua, LI Hui, NIU Ben, et al. Privacy Computing: Concept, Computing Framework, and Future Development Trends[J]. Engineering, 2019, 5(6): 1179-1192.
doi: 10.1016/j.eng.2019.09.002 |
| [2] |
ZHOU Xiao, GUO Ying, LI Fangshun, et al. Identifying and Assessing Innovation Pathways for Emerging Technologies: A Hybrid Approach Based on Text Mining and Altmetrics[J]. IEEE Transactions on Engineering Management, 2020, 68(5): 1360-1371.
doi: 10.1109/TEM.2020.2994049 URL |
| [3] |
FENG Chunmei, XU Yong, LIU Jinxing, et al. Supervised Discriminative Sparse PCA for Com-Characteristic Gene Selection and Tumor Classification on Multiview Biological Data[J]. IEEE Transactions on Neural Networks and Learning Systems, 2019, 30(10): 2926-2937.
doi: 10.1109/TNNLS.2019.2893190 pmid: 30802874 |
| [4] | ZHAO Qing, WANG Huiwen, WANG Shanshan. A Principal Component Analysis of Interval Data Based on Center and Log-Radius[J]. Journal of Beijing University of Aeronautics and Astronautics, 2021, 47(7): 1414-1421. |
| 赵青, 王惠文, 王珊珊. 基于中心-对数半长的区间数据主成分分析[J]. 北京航空航天大学学报, 2021, 47(7):1414-1421. | |
| [5] | SONG Yue, SEBE N, WANG Wei. Batch-Efficient Eigen Decom-position for Small and Medium Matrices[EB/OL]. (2022-07-09)[2022-10-23]. https://arxiv.org/abs/2207.04228v1. |
| [6] |
LI Fenghua, LI Hui, JIA Yan, et al. Privacy Computing: Concept, Connotation and Its Research Trend[J]. Journal on Communications, 2016, 37(4): 1-11.
doi: 10.11959/j.issn.1000-436x.2016078 |
|
李凤华, 李晖, 贾焰, 等. 隐私计算研究范畴及发展趋势[J]. 通信学报, 2016, 37(4): 1-11.
doi: 10.11959/j.issn.1000-436x.2016078 |
|
| [7] | ZHANG Yuqing, WANG Xiaofei, LIU Xuefeng, et al. Survey on Cloud Computing Security[J]. Journal of Software, 2016, 27(6): 1328-1348. |
| 张玉清, 王晓菲, 刘雪峰, 等. 云计算环境安全综述[J]. 软件学报, 2016, 27(6): 1328-1348. | |
| [8] | QIAN Wenjun, SHEN Qingni, WU Pengfei, et al. Research Progress on Privacy-Preserving Techniques in Big Data Computing Environment[J]. Chinese Journal of Computers, 2022, 45(4): 669-701. |
| 钱文君, 沈晴霓, 吴鹏飞, 等. 大数据计算环境下的隐私保护技术研究进展[J]. 计算机学报, 2022, 45(4): 669-701. | |
| [9] | FENG Dengguo, YANG Kang. Concretely Efficient Secure Multi-Party Computation Protocols: Survey and More[EB/OL]. (2022-06-14)[2022-10-23]. https://sands.edpsciences.org/articles/sands/full_html/2022/01/sands20210001/sands20210001.html. |
| [10] |
LIU Yang, MA Zhuo, LIU Ximeng, et al. Privacy-Preserving Object Detection for Medical Images with Faster R-CNN[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 69-84.
doi: 10.1109/TIFS.2019.2946476 URL |
| [11] |
YING Zuobin, CAO Shuanglong, LIU Ximeng, et al. Privacy Signal: Privacy-Preserving Traffic Signal Control for Intelligent Transportation System[J]. IEEE Transactions on Intelligent Transportation Systems, 2022, 23(9): 16290-16303.
doi: 10.1109/TITS.2022.3149600 URL |
| [12] |
BI Renwan, XIONG Jinbo, TIAN Youliang, et al. Achieving Lightweight and Privacy-Preserving Object Detection for Connected Autonomous Vehicles[J]. IEEE Internet of Things Journal, 2022, 10(3): 2314-2329.
doi: 10.1109/JIOT.2022.3212464 URL |
| [13] |
LI Minghui, CHOW S S M, HU Shengshan, et al. Optimizing Privacy-Preserving Outsourced Convolutional Neural Network Predictions[J]. IEEE Transactions on Dependable and Secure Computing, 2020, 19(3): 1592-1604.
doi: 10.1109/TDSC.2020.3029899 URL |
| [14] | LIU Xiaoning, ZHENG Yifeng, YUAN Xingliang, et al. Securely Outsourcing Neural Network Inference to the Cloud with Lightweight Techniques[J]. IEEE Transactions on Dependable and Secure Computing, 2022. |
| [15] | FENG Qi, HE Debiao, LIU Zhe, et al. SecureNLP: A System for Multi-Party Privacy-Preserving Natural Language Processing[J]. IEEE Transactions on Information Forensics and Security, 2020(15): 3709-3721. |
| [16] | JOLLIFFE I T, CADIMA J. Principal Component Analysis: A Review and Recent Developments[EB/OL]. (2016-04-13)[2022-10-13]. https://royalsocietypublishing.org/doi/10.1098/rsta.2015.0202. |
| [17] | WANG Xinxin. Improvement and Analysis of Lanczos Algorithm for Solving Eigenvalue Problems of Symmetric Matrices[D]. Harbin:Harbin Institute of Technology, 2008. |
| 王欣欣. 求解对称矩阵特征值问题的 Lanczos 算法的改进及分析[D]. 哈尔滨: 哈尔滨工业大学, 2008. | |
| [18] |
DUBRULLE A A. Householder Transformations Revisited[J]. SIAM Journal on Matrix Analysis and Applications, 2000, 22(1): 33-40.
doi: 10.1137/S0895479898338561 URL |
| [19] | GE J, WANG Zhaoran, WANG Mengdi, et al. Minimax-Optimal Privacy-Preserving Sparse PCA in Distributed Systems[EB/OL]. (2020-02-25)[2022-10-20]. http://proceedings.mlr.press/v84/ge18a.html. |
| [20] |
WANG Di, XU Jinhui. Principal Component Analysis in the Local Differential Privacy Model[J]. Theoretical Computer Science, 2020, 809: 296-312.
doi: 10.1016/j.tcs.2019.12.019 URL |
| [21] | LIU Yingting, CHEN Chaochao, ZHENG Longfei, et al. Privacy Preserving PCA for Multiparty Modeling[EB/OL]. (2020-02-06)[2022-10-23]. https://www2.isye.gatech.edu/-fferdinando3/cfp/PPAI20/papers/paper_16.pdf. |
| [22] |
XIANG Can, TANG Chunming, CAI Yunlu, et al. Privacy-Preserving Face Recognition with Outsourced Computation[J]. Soft Computing, 2016, 20(9): 3735-3744.
doi: 10.1007/s00500-015-1759-5 URL |
| [23] | AL-RUBAIE M, WU Peiyuan, CHANG J M, et al. Privacy-Preserving PCA on Horizontally-Partitioned Data[C]// IEEE. 2017 IEEE Conference on Dependable and Secure Computing. New York: IEEE, 2017: 280-287. |
| [24] |
ZHANG Yushu, XIAO Xiangli, YANG Luxing, et al. Secure and Efficient Outsourcing of PCA-Based Face Recognition[J]. IEEE Transactions on Information Forensics and Security, 2019, 15: 1683-1695.
doi: 10.1109/TIFS.10206 URL |
| [25] | REN Yanli, XU Xiao, FENG Guorui, et al. Non-Interactive and Secure Outsourcing of PCA-Based Face Recognition[EB/OL]. (2021-11-01)[2022-10-23]. https://dl.acm.org/doi/10.1016/j.cose.2021.102416. |
| [26] | WEI Lu, SARWATE A D, CORANDER J, et al. Analysis of a Privacy-Preserving PCA Algorithm Using Random Matrix Theory[C]// IEEE. 2016 IEEE Global Conference on Signal and Information Processing (GlobalSIP). New York: IEEE, 2016: 1335-1339. |
| [27] | ANOWAR F, SADAOUI S, SELIM B. Conceptual and Empirical Comparison of Dimensionality Reduction Algorithms (PCA, KPCA, LDA, MDS, SVD, LLE, ISOMAP, LE, ICA, t-SNE)[EB/OL]. (2021-05-01)[2022-10-23]. https://www.sciencedirect.com/science/article/abs/pii/S1574013721000186. |
| [28] | HUANG Kai, LIU Ximeng, FU Shaojing, et al. A Lightweight Privacy-Preserving CNN Feature Extraction Framework for Mobile Sensing[J]. IEEE Transactions on Dependable and Secure Computing, 2019, 18(3): 1441-1455. |
| [29] |
WANG Qian, DU Minxin, CHEN Xiuying, et al. Privacy-Preserving Collaborative Model Learning: The Case of Word Vector Training[J]. IEEE Transactions on Knowledge and Data Engineering, 2018, 30(12): 2381-2393.
doi: 10.1109/TKDE.69 URL |
| [30] | LINDELL Y. How to Simulate It-A Tutorial on the Simulation Proof Technique[J]. Tutorials on the Foundations of Cryptography, 2017(6): 277-346. |
| [1] | 张学旺, 张豪, 姚亚宁, 付佳丽. 基于群签名和同态加密的联盟链隐私保护方案[J]. 信息网络安全, 2023, 23(3): 56-61. |
| [2] | 刘芹, 郭凯圆, 涂航. 基于SM2和SM4的TEE下任务数据迁移方案[J]. 信息网络安全, 2023, 23(1): 9-17. |
| [3] | 于成丽, 张阳, 贾世杰. 云环境中数据安全威胁与防护关键技术研究[J]. 信息网络安全, 2022, 22(7): 55-63. |
| [4] | 金波, 唐前进, 唐前临. CCF计算机安全专业委员会2022年网络安全十大发展趋势解读[J]. 信息网络安全, 2022, 22(4): 1-6. |
| [5] | 吕凯欣, 李志慧, 黑吉辽, 宋云. 一类图存取结构的最优信息率计算[J]. 信息网络安全, 2022, 22(4): 77-85. |
| [6] | 陈妍, 韦湘, 陆臻. 云计算环境下网络安全产品检测方法研究[J]. 信息网络安全, 2022, 22(12): 1-6. |
| [7] | 林发鑫, 张健. 虚拟化平台异常行为检测系统的设计与实现[J]. 信息网络安全, 2022, 22(11): 62-67. |
| [8] | 肖晓雷, 赵雪莲. 我国跨境数据流动治理的研究综述[J]. 信息网络安全, 2022, 22(10): 45-51. |
| [9] | 杨晓琪, 白利芳, 唐刚. 基于DSMM模型的数据安全评估模型研究与设计[J]. 信息网络安全, 2021, 21(9): 90-95. |
| [10] | 刘璐, 李志慧, 芦殿军, 闫晨红. 基于线性码的量子秘密共享方案[J]. 信息网络安全, 2021, 21(8): 62-69. |
| [11] | 陈柏沩, 夏璇, 钟卫东, 吴立强. 基于秘密共享的LBlock的S盒防御方案[J]. 信息网络安全, 2021, 21(7): 80-86. |
| [12] | 游文婷, 张乐友, 叶亚迪, 李晖. 多用户通信机制中支持隐私保护的属性基动态广播加密[J]. 信息网络安全, 2021, 21(4): 21-30. |
| [13] | 石乐义, 徐兴华, 刘祎豪, 刘佳. 一种改进概率神经网络的工业控制系统安全态势评估方法[J]. 信息网络安全, 2021, 21(3): 15-25. |
| [14] | 周由胜, 王明, 刘媛妮. 支持区间查询的基于位置服务外包数据隐私保护方案[J]. 信息网络安全, 2021, 21(3): 26-36. |
| [15] | 朱艳华, 廖方宇, 胡良霖, 王志强. 科学数据安全标准规范关键问题探索[J]. 信息网络安全, 2021, 21(11): 1-8. |
| 阅读次数 | ||||||||||||||||||||||||||||||||||||||||||||||||||
|
全文 210
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||
|
摘要 315
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||