信息网络安全 ›› 2021, Vol. 21 ›› Issue (3): 26-36.doi: 10.3969/j.issn.1671-1122.2021.03.004
支持区间查询的基于位置服务外包数据隐私保护方案
- 1.重庆邮电大学计算机科学与技术学院,重庆 400065
2.重庆邮电大学网络空间安全与信息法学院,重庆 400065
-
收稿日期:2020-11-15出版日期:2021-03-10发布日期:2021-03-16 -
通讯作者:周由胜 E-mail:zhouys@cqupt.edu.cn -
作者简介:周由胜(1979—),男,湖北,副教授,博士,主要研究方向为数据安全、认证与密钥协商|王明(1995—),男,安徽,硕士研究生,主要研究方向为位置隐私保护|刘媛妮(1982—),女,河南,副教授,博士,主要研究方向为网络安全、网络智能、未来网络、IP路由技术 -
基金资助:国家自然科学基金(61702067);重庆市自然科学基金(cstc2020joymsxmX0343);重庆市留学人员回国创业创新支持计划(CX2018122)
Privacy Protection Scheme Supporting Interval Query for LBS Outsourced Data
ZHOU Yousheng1,2( ), WANG Ming1, LIU Yuanni2
), WANG Ming1, LIU Yuanni2
- 1. College of Computer Science and Technology, Chongqing University of Posts and Telecommunications, Chongqing 400065, China
2. College of Cyber Security and Information Law, Chongqing University of Posts and Telecommunications, Chongqing 400065, China
-
Received:2020-11-15Online:2021-03-10Published:2021-03-16 -
Contact:ZHOU Yousheng E-mail:zhouys@cqupt.edu.cn
摘要:
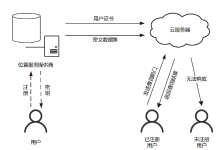
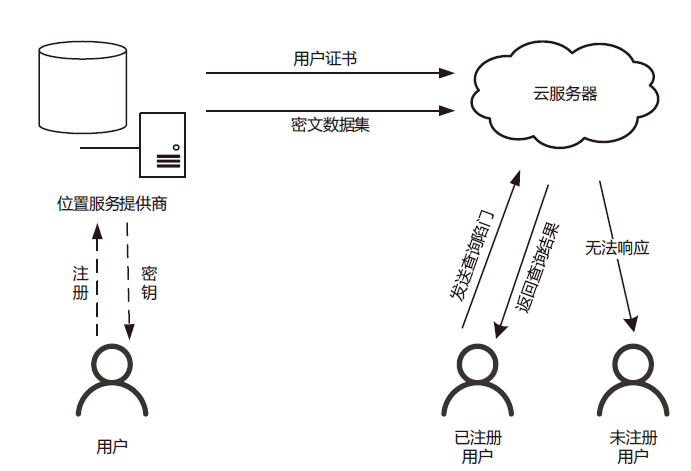
随着云计算技术的迅猛发展,越来越多的LBS服务被外包到云上运行以减少本地的计算和存储成本。然而,外包环境下的云服务器通常被认为是一个半可信的实体,LBS提供商的数据安全和用户的个人隐私将会面临新的安全挑战。针对现有基于位置服务数据外包方案中不支持区间查询和隐私保护不足等问题,文章提出一种支持区间查询的LBS外包数据隐私保护方案,利用非对称向量积保值加密和公钥可搜索加密对LBS坐标和关键词进行加密,实现LBS数据的机密性和用户查询模式的隐私性;利用轻量级的矩阵运算使用户在不泄露查询区间的前提下准确获得所需LBS数据。在新用户注册方面,采用基于双线性配对运算实现用户身份认证。安全性和性能分析表明,文章方案较同类方案具有一定优势。
中图分类号:
引用本文
周由胜, 王明, 刘媛妮. 支持区间查询的基于位置服务外包数据隐私保护方案[J]. 信息网络安全, 2021, 21(3): 26-36.
ZHOU Yousheng, WANG Ming, LIU Yuanni. Privacy Protection Scheme Supporting Interval Query for LBS Outsourced Data[J]. Netinfo Security, 2021, 21(3): 26-36.
表1
符号定义表
| 符号 | 符号说明 |
|---|---|
| $<>$ | 内积运算符 |
| ${{M}_{1}},{{M}_{2}}$ | 可逆矩阵 |
| ${{O}_{o}}$ | $l-2$维向量 |
| $b$ | 长度为$l$的比特串 |
| $\{({{x}_{i}},{{y}_{i}}),{{W}_{i}},{{\alpha }_{i}}\}$ | 第$i$条POI数据 |
| $\{({{x}_{u}},{{y}_{u}}),R\}$ | 用户坐标为$({{x}_{u}},{{y}_{u}})$且查询半径为R的圆形区域 |
| $[{{\partial }_{1}},{{\partial }_{2}}]$ | 用户所查询的POI区间属性范围 |
| $lo{{c}_{\partial }},lo{{c}_{-1}}$ | POI中区间属性值I和数字-1在l维向量中的位置 |
| $r,{{r}_{u}},\text{ }r\prime ,\alpha $ | 随机数 |
| $\left\{ S{{K}_{L}},P{{K}_{L}} \right\}$ | LSP公私钥对 |
| $\left\{ S{{K}_{\text{S}}},P{{K}_{S}} \right\}$ | 云服务器公私钥对 |
| $\left\{ S{{K}_{u}},P{{K}_{u}} \right\}$ | 用户公私钥对 |
表3
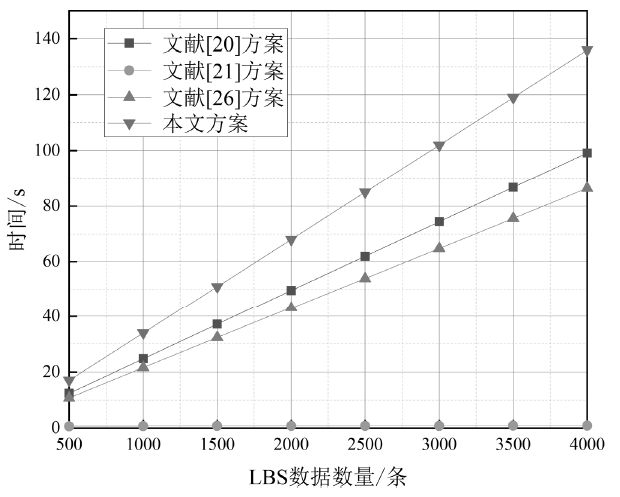
各阶段计算开销比较
| 阶段 | LBS加密数据 | 陷门生成 | 数据检索 |
|---|---|---|---|
| 文献[ | $2N{{T}_{e}}$ | $2{{T}_{e}}$ | $2N{{T}_{p}}$ |
| 文献[ | $N\left( 6{{T}_{e}}+2{{T}_{m}} \right)$ | $4{{T}_{e}}$ | $lo{{g}_{N}}\left( 5{{T}_{m}}+2{{T}_{p}} \right)$ |
| 文献[ | $N\left( {{T}_{p}}+{{T}_{e}} \right)$ | $2{{T}_{e}}$ | $2N({{T}_{p}}+{{T}_{m}})$ |
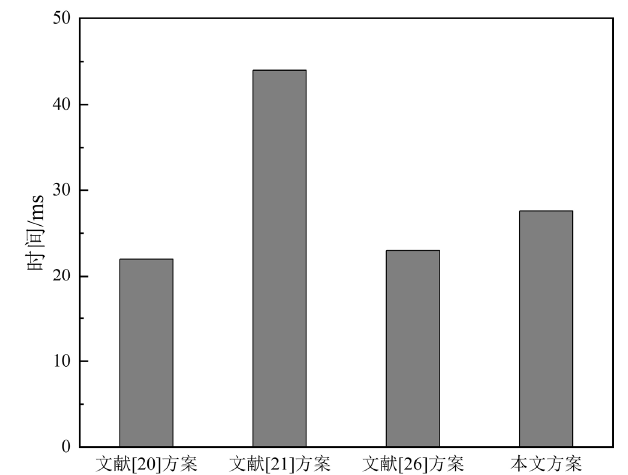
| 本文方案 | $N\left( 2{{T}_{m}}+{{T}_{p}} \right)$ | $3{{T}_{m}}$ | $N\left( {{T}_{m}}+2{{T}_{p}} \right)$ |
| [1] | PAULET R, KAOSAR M G, YI X, et al. Privacy-preserving and Content-protecting Location Based Queries[J]. IEEE Transactions on Knowledge and Data Engineering, 2013,26(5):1200-1210. |
| [2] | PENG Tao, LIU Qin, MENG Dacheng, et al. Collaborative Trajectory Privacy Preserving Scheme in Location-based Services[J]. Information Sciences, 2017,387(5):165-179. |
| [3] | SHAO Jun, LU Rongxing, LIN Xiaodong. FINE: A Fine-grained Privacy-preserving Location-based Service Framework for Mobile Devices [C]//IEEE. IEEE INFOCOM 2014-IEEE Conference on Computer Communications. April 27-May 2, 2014, Toronto, Canada. New York: IEEE, 2014: 244-252. |
| [4] | JIANG Hongbo, ZHAO Ping, WANG Chen. RobLoP: Towards Robust Privacy Preserving Against Location Dependent Attacks in Continuous LBS Queries[J]. IEEE/ACM Transactions on Networking, 2018,26(2):1018-1032. |
| [5] | BERESFORD A R, STAJANO F. Location Privacy in Pervasive Computing[J]. IEEE Pervasive Computing, 2003,2(1):46-55. |
| [6] | HWANG R H, HSUEH Y L, CHUNG H W. A Novel Time-obfuscated Algorithm for Trajectory Privacy Protection[J]. IEEE Transactions on Services Computing, 2013,7(2):126-139. |
| [7] | LI Lichun, LU Rongxing, HUANG Cheng. EPLQ: Efficient Privacy-preserving Location-based Query over Outsourced Encrypted Data[J]. IEEE Internet of Things Journal, 2015,3(2):206-218. |
| [8] | BERESFORD A R, STAJANO F. Location Privacy in Pervasive Computing[J]. IEEE Pervasive Computing, 2003 ( 1):46-55. |
| [9] | PALANISAMY B, LIU Ling. Attack-resilient Mix-zones over Road Networks: Architecture and Algorithms[J]. IEEE Transactions on Mobile Computing, 2014,14(3):495-508. |
| [10] | SUN Yipin, ZHANG Bofeng, ZHAO Baokang, et al. Mix-zones Optimal Deployment for Protecting Location Privacy in VANET[J]. Peer-to-Peer Networking and Applications, 2015,8(6):1108-1121. |
| [11] | KIDO H, YANAGISAWA Y, SATOH T. An Anonymous Communication Technique Using Dummies for Location-based Services [C]//ICPS ‘05. Proceedings. International Conference on Pervasive Services, July 11-14, 2005, Santorini, Greece. Piscataway: IEEE, 2005: 88-97. |
| [12] | YIU M L, JENSEN C S, HUANG Xuegang, et al. SpaceTwist: Managing the Trade-offs among Location Privacy, Query Performance, and Query Accuracy in Mobile Services [C]//IEEE. 2008 IEEE 24th International Conference on Data Engineering. April 7-12, 2008, Cancun, Mexico. Los Alamitos: IEEE, 2008: 366-375. |
| [13] | ZHAO Dapeng, JIN Yuanyuan, ZHANG Kai, et al. EPLA: Efficient Personal Location Anonymity[J]. GeoInformatica, 2018,22(1):29-47. |
| [14] | Vu, Khuong, ZHENG Rong, GAO Jie. Efficient Algorithms for K-anonymous Location Privacy in Participatory Sensing [C]//IEEE. 2012 Proceedings IEEE INFOCOM, March 25-30, 2012, Orlando, FL, USA. New York: IEEE, 2012: 2399-2407. |
| [15] | GEDIK B, LIU Ling. Protecting Location Privacy with Personalized K-anonymity: Architecture and Algorithms[J]. IEEE Transactions on Mobile Computing, 2007,7(1):1-18. |
| [16] | NIU Ben, LI Qinghua, ZHU Xiaoyan, et al. Achieving K-anonymity in Privacy-aware Location-based Services [C]//IEEE INFOCOM 2014-IEEE Conference on Computer Communications. April 27-May 2, 2014, Toronto, Canada. New York: IEEE, 2014: 754-762. |
| [17] | CHEN Jing, HE Kun, YUAN Quan, et al. Blind Filtering at Third Parties: An Efficient Privacy-preserving Framework for Location-based Services[J]. IEEE Transactions on Mobile Computing, 2018,17(11):2524-2535. |
| [18] |
ZHU Hui, LIU Fen, LI Hui. Efficient and Privacy-preserving Polygons Spatial Query Framework for Location-based Services[J]. IEEE Internet of Things Journal, 2016,4(2):536-545.
doi: 10.1109/JIOT.2016.2553083 URL |
| [19] |
ZHANG Shaobo, WANG Guojun, BHUIYAN M Z A, et al. A Dual Privacy Preserving Scheme in Continuous Location-based Services[J]. IEEE Internet of Things Journal, 2018,5(5):4191-4200.
doi: 10.1109/JIoT.6488907 URL |
| [20] | YANG Xue, YIN Fan, TANG Xiaohu. A Fine-grained and Privacy-preserving Query Scheme for Fog Computing-enhanced Location-based Service[EB/OL]. https://www.mdpi.com/1424-8220/17/7/1611, 2017-05-31. |
| [21] |
ZHU Hui, LU Rongxing, HUANG Cheng, et al. An Efficient Privacy-preserving Location-based Services Query Scheme in Outsourced Cloud[J]. IEEE Transactions on Vehicular Technology, 2015,65(9):7729-7739.
doi: 10.1109/TVT.2015.2499791 URL |
| [22] | ZENG Ming, ZHANG Kai, CHEN Jie, et al. P3GQ: A Practical Privacy-preserving Generic Location-based Services Query Scheme[J]. Pervasive and Mobile Computing, 2018,51:56-72. |
| [23] | KARRAS P, NIKITIN A, SAAD M, et al. Adaptive Indexing over Encrypted Numeric Data [C]//ACM. Proceedings of the 2016 International Conference on Management of Data, June 26-July 1, 2016, San Francisco California, USA. New York: ACM, 2016: 171-183. |
| [24] | XU Zhou, LIN Yaping, SANDOR V K A, et al. A Lightweight Privacy and Integrity Preserving Range Query Scheme for Mobile Cloud Computing[J]. Computers & Security, 2019,84(7):318-333. |
| [25] | WONG W K, CHEUNG D W, KAO B, et al. Secure KNN Computation on Encrypted Databases [C]//ACM. Proceedings of the 2009 ACM SIGMOD International Conference on Management of Data. June 29-July 2, 2009, Providence Rhode Island USA. New York: ACM, 2009: 139-152. |
| [26] | OU LU, YIN Hui, QIN Zheng, et al. An Efficient and Privacy-preserving Multiuser Cloud-Based LBS Query Scheme[J]. Security & Communication Networks, 2018,2018(3):1-11. |
| [1] | 路宏琳, 王利明. 面向用户的支持用户掉线的联邦学习数据隐私保护方法[J]. 信息网络安全, 2021, 21(3): 64-71. |
| [2] | 刘峰, 杨杰, 齐佳音. 基于哈希证明系统的区块链两方椭圆曲线数字签名算法研究[J]. 信息网络安全, 2021, 21(1): 19-26. |
| [3] | 汪金苗, 谢永恒, 王国威, 李易庭. 基于属性基加密的区块链隐私保护与访问控制方法[J]. 信息网络安全, 2020, 20(9): 47-51. |
| [4] | 李宁波, 周昊楠, 车小亮, 杨晓元. 云环境下基于多密钥全同态加密的定向解密协议设计[J]. 信息网络安全, 2020, 20(6): 10-16. |
| [5] | 张佳程, 彭佳, 王雷. 大数据环境下的本地差分隐私图信息收集方法[J]. 信息网络安全, 2020, 20(6): 44-56. |
| [6] | 肖彪, 闫宏强, 罗海宁, 李炬成. 基于差分隐私的贝叶斯网络隐私保护算法的改进研究[J]. 信息网络安全, 2020, 20(11): 75-86. |
| [7] | 何泾沙, 杜晋晖, 朱娜斐. 基于k匿名的准标识符属性个性化实现算法研究[J]. 信息网络安全, 2020, 20(10): 19-26. |
| [8] | 黄保华, 程琪, 袁鸿, 黄丕荣. 基于距离与误差平方和的差分隐私K-means聚类算法[J]. 信息网络安全, 2020, 20(10): 34-40. |
| [9] | 唐春明, 林旭慧. 隐私保护集合交集计算协议[J]. 信息网络安全, 2020, 20(1): 9-15. |
| [10] | 汪金苗, 王国威, 王梅, 朱瑞瑾. 面向雾计算的隐私保护与访问控制方法[J]. 信息网络安全, 2019, 19(9): 41-45. |
| [11] | 郝文江, 林云. 互联网企业社会责任现状与启示研究[J]. 信息网络安全, 2019, 19(9): 130-133. |
| [12] | 周权, 许舒美, 杨宁滨. 一种基于ABGS的智能电网隐私保护方案[J]. 信息网络安全, 2019, 19(7): 25-30. |
| [13] | 李怡霖, 闫峥, 谢皓萌. 车载自组织网络的隐私保护综述[J]. 信息网络安全, 2019, 19(4): 63-72. |
| [14] | 赵谱, 崔巍, 郝蓉, 于佳. 一种针对El-Gamal数字签名生成的安全外包计算方案[J]. 信息网络安全, 2019, 19(3): 81-86. |
| [15] | 傅彦铭, 李振铎. 基于拉普拉斯机制的差分隐私保护k-means++聚类算法研究[J]. 信息网络安全, 2019, 19(2): 43-52. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||