信息网络安全 ›› 2023, Vol. 23 ›› Issue (4): 51-60.doi: 10.3969/j.issn.1671-1122.2023.04.006
基于密文转换的高效通用同态加密框架
- 1.火箭军工程大学作战保障学院,西安 710025
2.武警工程大学密码工程学院,西安 710086
-
收稿日期:2022-12-16出版日期:2023-04-10发布日期:2023-04-18 -
通讯作者:李敏 E-mail:proflimin@163.com -
作者简介:杜卫东(1988—),男,河北,博士研究生,主要研究方向为深度学习隐私保护|李敏(1971—),女,陕西,教授,博士,主要研究方向为深度学习隐私保护、深度学习目标检测和对抗生成网络|韩益亮(1977—),男,甘肃,教授,博士,主要研究方向为公钥密码学、网络安全和深度学习隐私保护|王绪安(1981—),男,湖北,教授,博士,主要研究方向为可验证公钥加密、安全多方计算协议和网络安全。 -
基金资助:国防科技创新计划自主科研项目(ZZKY20222201)
An Efficient Versatile Homomorphic Encryption Framework Based on Ciphertext Conversion Technique
DU Weidong1,2, LI Min1( ), HAN Yiliang2, WANG Xu’an2
), HAN Yiliang2, WANG Xu’an2
- 1. College of War Support, Rocket Force University of Engineering, Xi’an 710025, China
2. College of Cryptography, Engineering University of PAP, Xi’an 710086, China
-
Received:2022-12-16Online:2023-04-10Published:2023-04-18 -
Contact:LI Min E-mail:proflimin@163.com
摘要:
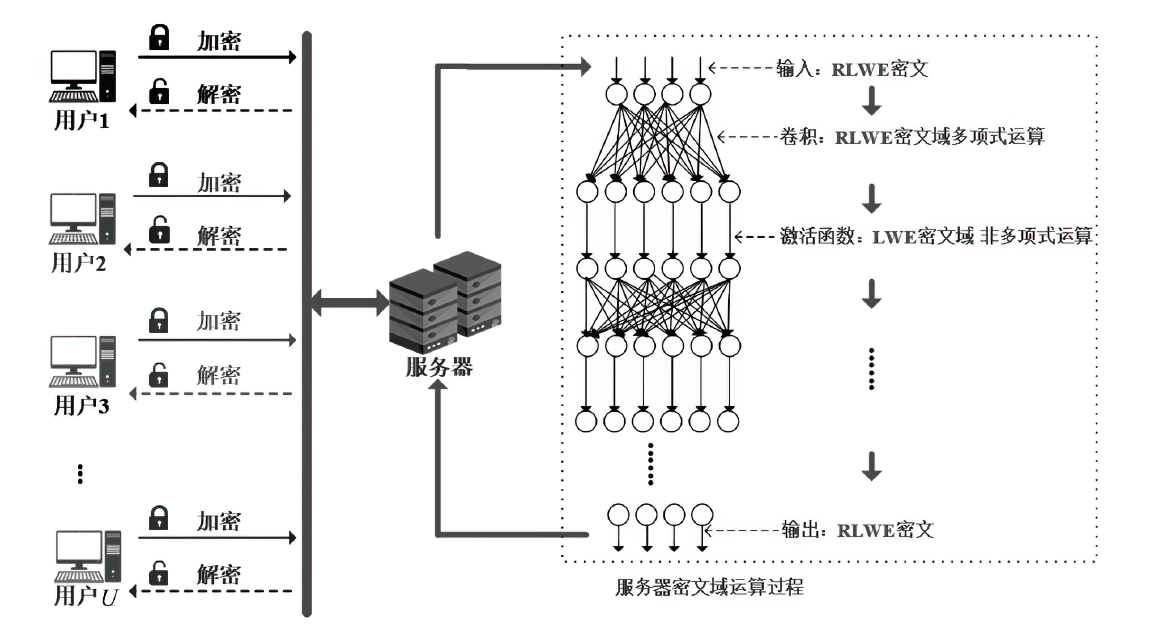
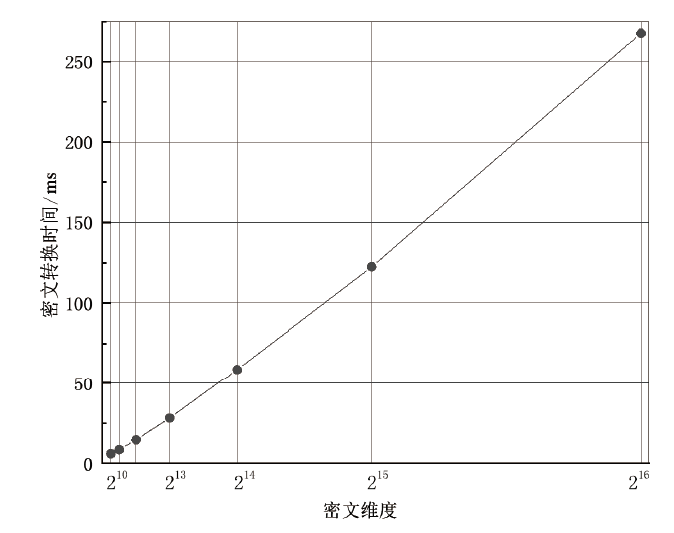
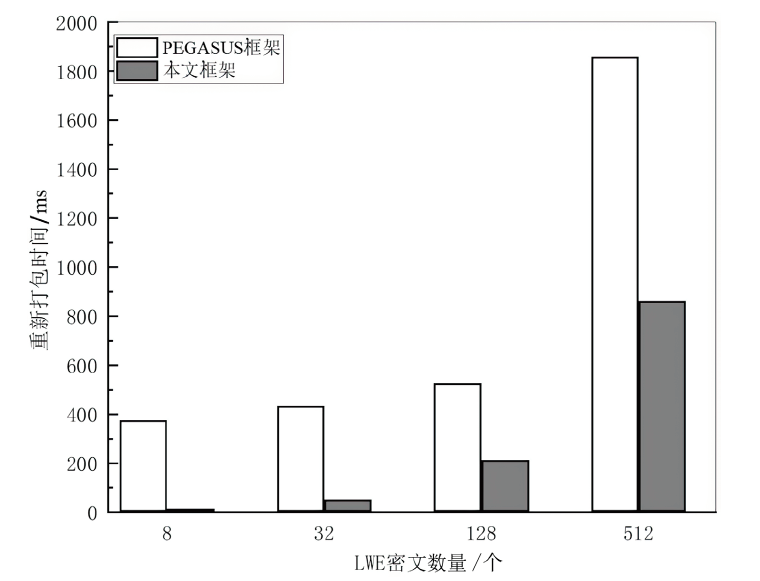
针对不同应用算法的具体特点设计与之匹配的同态加密方案是设计高效的具有隐私保护功能算法的关键途径。文章首先针对深度学习预测中多项式运算只需要密文-密文加法和常数-密文乘法的特点,以多项式向量空间为明文空间,设计了一个基于系数编码的RLWE同态加密方案;然后基于该方案构造了一个同时支持多项式运算和非多项式运算的通用同态加密框架,该框架可以在RLWE密文上进行多项式运算,从RLWE密文中提取出LWE密文,通过查表方法进行非多项式运算;最后利用密文转换方法将LWE密文重新打包成RLWE密文,方便后续进行多项式运算。实验结果表明,相比于通用同态加密框架PEGASUS,文章所提框架的RLWE密文消息容量提高了1倍,并且多项式运算效率也提高了1倍。而在非多项式运算中,文章所提框架不需要转换密文中消息的编码方式,重新打包过程只需要自同构运算,因此,该框架具有更高的通信效率和运算效率。
中图分类号:
引用本文
杜卫东, 李敏, 韩益亮, 王绪安. 基于密文转换的高效通用同态加密框架[J]. 信息网络安全, 2023, 23(4): 51-60.
DU Weidong, LI Min, HAN Yiliang, WANG Xu’an. An Efficient Versatile Homomorphic Encryption Framework Based on Ciphertext Conversion Technique[J]. Netinfo Security, 2023, 23(4): 51-60.
| [1] | DOWLIN N, GILAD-BACHRACH R, LAINE K, et al. CryptoNets: Applying Neural Networks to Encrypted Data with High Throughput and Accuracy[C]// ACM. Proceedings of the 33rd International Conference on Machine Learning. New York: ACM, 2016: 201-210. |
| [2] | BRUTZKUS A, ELISHA O, GILAD-BACHRACH R. Low Latency Privacy Preserving Inference[C]// ACM. Proceedings of the 36th International Conference on Machine Learning. New York: ACM, 2019: 1295-1304. |
| [3] | LOU Qian, JIANG Lei. SHE: A Fast and Accurate Deep Neural Network for Encrypted Data[C]// ACM. Proceedings of the 33rd International Conference on Neural Information Processing Systems. New York: ACM, 2019: 10035-10043. |
| [4] | BOURSE F, MINELLI M, MINIHOLD M, et al. Fast Homomorphic Evaluation of Deep Discretized Neural Networks[C]// Springer. 38th Annual International Cryptology Conference. Berlin:Springer, 2018: 483-512. |
| [5] | BRAKERSKI Z, GENTRY C, VAIKUNTANATHAN V. (Leveled) Fully Homomorphic Encryption Without Bootstrapping[C]// ACM. Proceedings of the 3rd Innovations in Theoretical Computer Science Conference. New York: ACM, 2014: 309-325. |
| [6] | FAN Junfeng, VERCAUTEREN F. Somewhat Practical Fully Homomorphic Encryption[EB/OL]. (2012-01-16)[2022-12-01]. http://eprint.iacr.org/2012/144. |
| [7] | CHEON J H, KIM A, KIM M, et al. Homomorphic Encryption for Arithmetic of Approximate Numbers[C]// Springer. International Conference on the Theory and Applications of Cryptology and Information Security. Berlin:Springer, 2017: 409-437. |
| [8] | DUCAS L, MICCIANCIO D. FHEW: Bootstrapping Homomorphic Encryption in Less than a Second[C]// Springer. Annual International Conference on the Theory and Applications of Cryptographic Techniques. Berlin:Springer, 2015: 617-640. |
| [9] |
CHILLOTTI I, NICOLAS G, MARIYA G, et al. TFHE Fast Fully Homomorphic Encryption over the Torus[J]. Journal of Cryptology, 2020, 33(1): 34-91.
doi: 10.1007/s00145-019-09319-x |
| [10] | CHEON J H, KIM D, KIM D. Efficient Homomorphic Comparison Methods with Optimal Complexity[C]// Springer. International Conference on the Theory and Application of Cryptology and Information Security. Berlin:Springer, 2020: 221-256. |
| [11] | CHEON J, KIM D, KIM D, et al. Numerical Method for Comparison on Homomorphically Encrypted Numbers[C]// Springer. International Conference on the Theory and Application of Cryptology and Information Security. Berlin:Springer, 2019: 415-445. |
| [12] | MICCIANCIO D, POLYAKOV Y S. Bootstrapping in FHEW-Like Cryptosystems[EB/OL]. (2021-09-19)[2022-12-01]. https://eprint.iacr.org/2020/086. |
| [13] |
BOURA C, GAMA N, GEORGIEVA M, et al. CHIMERA: Combining Ring-LWE-Based Fully Homomorphic Encryption Schemes[J]. Journal of mathematical cryptology, 2020, 14(1): 316-338.
doi: 10.1515/jmc-2019-0026 URL |
| [14] | LU Wenjie, HUANG Zhicong, HONG Cheng, et al. PEGASUS: Bridging Polynomial and Non-Polynomial Evaluations in Homomorphic Encryption[C]// IEEE. 2021 IEEE Symposium on Security and Privacy. New York: IEEE, 2021: 1057-1073. |
| [15] | REGEV O. On Lattices, Learning with Errors, Random Linear Codes, and Cryptography[C]// ACM. Proceedings of the 37th Annual ACM Symposium on Theory of Computing. New York: ACM, 2005: 84-93. |
| [16] | LYUBASHEVSKY V, PEIKERT C, REGEV O. On Ideal Lattices and Learning with Errors over Rings[C]// Springer. Annual International Conference on the Theory and Applications of Cryptographic Techniques. Berlin:Springer, 2010: 1-23. |
| [17] | GENTRY C, SAHAI A, WATERS B. Homomorphic Encryption from Learning with Errors: Conceptually-Simpler, Asymptotically-Faster, Attribute-Based[C]// Springer. Annual Cryptology Conference. Berlin:Springer, 2013: 75-92. |
| [18] |
HAN K, HHAN M, CHEON J H. Improved Homomorphic Discrete Fourier Transforms and FHE Bootstrapping[J]. IEEE Access, 2019, 7: 57361-57370.
doi: 10.1109/ACCESS.2019.2913850 |
| [19] | CHEN Hao, DAI Wei, KIM M, et al. Efficient Homomorphic Conversion Between (Ring) LWE Ciphertexts[C]// Springer. Applied Cryptography and Network Security 19th International Conference. Berlin:Springer, 2021: 460-479. |
| [20] | HAN K, KI D. Better Bootstrapping for Approximate Homomorphic Encryption[C]// Springer. Cryptographers’ Track at the RSA Conference. Berlin:Springer, 2020: 364-390. |
| [21] | Microsoft. Microsoft SEAL[EB/OL]. (2018-12-03)[2022-12-01]. https://github.com/microsoft/SEAL. |
| [1] | 尹曙, 陈兴蜀, 朱毅, 曾雪梅. 基于字符空间构造的域名匿名化算法[J]. 信息网络安全, 2023, 23(4): 80-89. |
| [2] | 郭瑞, 魏鑫, 陈丽. 工业物联网环境下可外包的策略隐藏属性基加密方案[J]. 信息网络安全, 2023, 23(3): 1-12. |
| [3] | 李晓华, 王苏杭, 李凯, 徐剑. 一种支持隐私保护的传染病人际传播分析模型[J]. 信息网络安全, 2023, 23(3): 35-44. |
| [4] | 张学旺, 张豪, 姚亚宁, 付佳丽. 基于群签名和同态加密的联盟链隐私保护方案[J]. 信息网络安全, 2023, 23(3): 56-61. |
| [5] | 王晶宇, 马兆丰, 徐单恒, 段鹏飞. 支持国密算法的区块链交易数据隐私保护方案[J]. 信息网络安全, 2023, 23(3): 84-95. |
| [6] | 于晶, 袁曙光, 袁煜琳, 陈驰. 基于k匿名数据集的鲁棒性水印技术研究[J]. 信息网络安全, 2022, 22(9): 11-20. |
| [7] | 张学旺, 刘宇帆. 可追踪身份的物联网感知层节点匿名认证方案[J]. 信息网络安全, 2022, 22(9): 55-62. |
| [8] | 秦宝东, 余沛航, 郑东. 基于双陷门同态加密的决策树分类模型[J]. 信息网络安全, 2022, 22(7): 9-17. |
| [9] | 陈彬杰, 魏福山, 顾纯祥. 基于KNN的具有隐私保护功能的区块链异常交易检测[J]. 信息网络安全, 2022, 22(3): 78-84. |
| [10] | 王思蝶, 马兆丰, 罗守山, 徐单恒. 面向异构多链的区块链链上数据隐私保护方案[J]. 信息网络安全, 2022, 22(12): 67-75. |
| [11] | 晏燕, 张雄, 冯涛. 大数据统计划分发布的等比差分隐私预算分配方法[J]. 信息网络安全, 2022, 22(11): 24-35. |
| [12] | 梁广俊, 辛建芳, 倪雪莉, 马卓. 智能音箱安全与取证研究[J]. 信息网络安全, 2022, 22(10): 108-113. |
| [13] | 顾海艳, 蒋铜, 马卓, 朱季鹏. k-匿名改进算法及其在隐私保护中的应用研究[J]. 信息网络安全, 2022, 22(10): 52-58. |
| [14] | 徐硕, 张睿, 夏辉. 基于数据属性修改的联邦学习隐私保护策略[J]. 信息网络安全, 2022, 22(1): 55-63. |
| [15] | 路宏琳, 王利明, 杨婧. 一种新的参数掩盖联邦学习隐私保护方案[J]. 信息网络安全, 2021, 21(8): 26-34. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||