信息网络安全 ›› 2020, Vol. 20 ›› Issue (7): 85-95.doi: 10.3969/j.issn.1671-1122.2020.07.010
云环境下Docker容器隔离脆弱性分析与研究
- 1. 中国科学院信息工程研究所,北京 100093
2. 中国科学院大学,北京 100039
-
收稿日期:2020-01-15出版日期:2020-07-10发布日期:2020-08-13 -
通讯作者:王利明 E-mail:wangliming@iie.ac.cn -
作者简介:边曼琳(1994—),女,吉林,硕士研究生,主要研究方向为云计算安全|王利明(1978—),男,北京,研究员,博士,主要研究方向为云计算安全、网络安全、大数据安全、5G安全、区块链安全 -
基金资助:国家重点研发计划(2017YFB0801900)
Analysis and Research on Vulnerability of Docker Container Isolation in Cloud Environment
BIAN Manlin1,2, WANG Liming1( )
)
- 1. Institute of Information Engineering, Chinese Academy of Sciences, Beijing 100093, China
2. University of Chinese Academy of Sciences, Beijing 100039, China
-
Received:2020-01-15Online:2020-07-10Published:2020-08-13 -
Contact:Liming WANG E-mail:wangliming@iie.ac.cn
摘要:
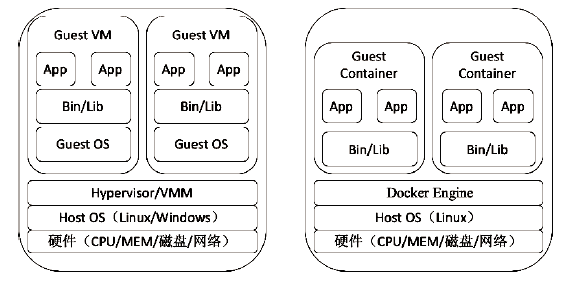
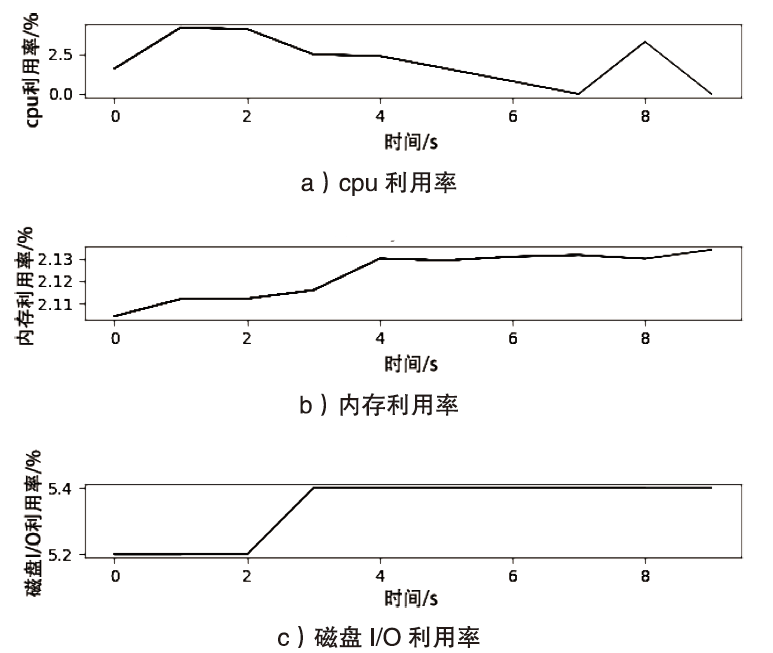
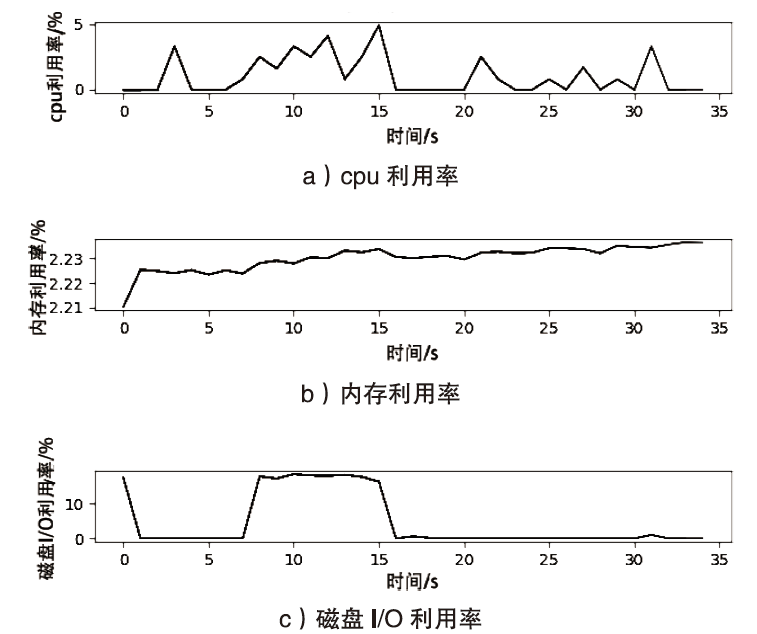
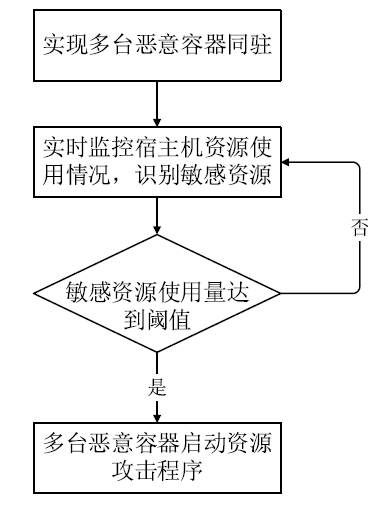
云计算是信息时代下继互联网、计算机后出现的又一革新概念,大数据、物联网、5G通信等新兴技术的发展均离不开云计算的支持。虚拟化技术是支撑云计算的一项关键技术,现有的虚拟化方式主要分为基于虚拟机的虚拟化和基于容器的虚拟化,容器技术随着Docker的出现在云服务领域备受青睐。Docker容器相较于传统虚拟机具有轻量级、高性能等显著优势,但是由于Docker容器采用软件隔离机制,与虚拟机相比隔离性较弱,面临的安全问题更加严重。隔离性差是Docker面临的主要安全挑战之一,严重影响了容器技术的进一步推广与发展,因此容器隔离性的安全研究具有重要意义。文章针对云环境下Docker容器隔离性弱引发的安全问题进行研究,分析Docker容器隔离机制,证明Docker中部分伪文件系统没有实现隔离,利用未隔离的伪文件系统可以获取宿主机相关信息,造成宿主机信息泄露。此外,通过实验证明,若泄露的信息被攻击者恶意利用,将引发恶意容器同驻、同驻容器DoS攻击等安全问题,对同驻合法容器服务构成严重的安全威胁。
中图分类号:
引用本文
边曼琳, 王利明. 云环境下Docker容器隔离脆弱性分析与研究[J]. 信息网络安全, 2020, 20(7): 85-95.
BIAN Manlin, WANG Liming. Analysis and Research on Vulnerability of Docker Container Isolation in Cloud Environment[J]. Netinfo Security, 2020, 20(7): 85-95.
使用本文
| [1] | WANG Xiong. The History and Advantages of Cloud Computing[J]. Computer & Network, 2019,45(2):44. |
| 王雄. 云计算的历史和优势[J]. 计算机与网络, 2019,45(2):44. | |
| [2] | LI Wenjun. Analysis of Computer Cloud Computing Andits Implementation Technology[J]. Dual Use Technologies & Products, 2018,18(22):57-58. |
| 李文军. 计算机云计算及其实现技术分析[J]. 军民两用技术与产品, 2018,18(22):57-58. | |
| [3] | NSFOCUS Xingyunlab. ContainerSecurity Technical Report of NSFOCUS in 2018[EB/OL]. https://www.nsfocus.com.cn/upload/contents/2018/11/20181109100414_79051.pdf, 2018-11-9. |
| [4] | FORNI A A, MEULEN R. Gartner Identifies the Top Technologies for Security in 2017[EB/OL]. https://www.gartner.com/en/newsroom/press-releases/2017-06-14-gartner-identifies-the-top-technologies-for-security-in-2017, 2017-6-14. |
| [5] | YUNDING Lab, GEEK P. Report of Cloud Security in 2019[[EB/OL]. http://www.cbdio.com/image/site2/20191231/f42853157e261f75544321.pdf, 2019-12-31. |
| [6] | JUNAID K. Iron: Isolating Network-based CPU in Container Environments[C]// USENIX. 15th USENIX Symposium on Networked Systems Design and Implementation(NSDI 18), April 9-11, 2018, Renton, WA, USA. Berkeley: USENIX, 2018:312-328. |
| [7] | GAO Xing, GUZhongshu , KAYAALP M, et al. Container Leaks: Emerging Security Threats of Information Leakages in Container Clouds[C]// IEEE. 2017 47th Annual IEEE/IFIP International Conference on Dependable Systems and Networks(DSN), June 26-29, 2017, Denver, CO, USA. New York: IEEE, 2017: 237-248. |
| [8] | MA Shiyao, JIANG Jingjie, LI Bo, et al. Maximizing Container-based Network Isolation in Parallel Computing Clusters[C]// IEEE. 2016 IEEE 24th International Conference onNetwork Protocols(ICNP), November 8-11, 2016, Singapore. New York: IEEE, 2016: 1-10. |
| [9] | XAVIERMG, NEVES M V, ROSSIF D, et al. Performance Evaluation of Container-based Virtualization for High Performance Computing Environments[C]// IEEE. 2013 21st Euromicro International Conference on Parallel, Distributed and Network-Based Processing(PDP), February 27-March 1, 2013, Belfast, UK. New York: IEEE, 2013: 233-240. |
| [10] | ARNAUTOV S, TRACH B, GREGOR F, et al. SCONE: Secure Linux Containers with Intel SGX[C]// USENIX. 12th USENIXSymposium on Operating Systems Design and Implementation(OSDI 16), November 2-4, 2016, Savannah, GA, USA. Berkeley: USENIX, 2016: 689-703. |
| [11] | MIRKOVIC J, REIHER P. A Taxonomy of DDoS Attack and DDoS Defense Mechanisms[J]. ACM SIGCOMM Computer Communication Review, 2004,34(2):39-53. |
| [12] | HUANG Jingwei, NICOL D M, CAMPELL R H. Denial-of-service Threat to Hadoop/YARN Clusters with Multi-tenancy[C]// IEEE. 2014 IEEE International Congress on Big Data, June 27-July 2, 2014, Anchorage, AK, USA. New York: IEEE, 2014: 48-55. |
| [13] | CHEN Fei, BI Xiaohong, WANG Jingjing, et al. Survey of DDoS Defense: Challenges and Directions[J]. Network and Information Security, 2017,3(10):16-24. |
| 陈飞, 毕小红, 王晶晶, 等. DDoS攻击防御技术发展综述[J]. 网络与信息安全学报, 2017,3(10):16-24. | |
| [14] | CROSBY S A, WALLACH D S. Denial of Service via Algorithmic Complexity Attacks[C]// USENIX. 12th Conferenceon USENIX Security Symposium, August 4-8, 2003, Washington, DC, USA. Berkeley: USENIX, 2003: 29-44. |
| [15] | CHELLADHURA J, CHELLIAH P R, KUMAR S A. Securing Docker Containers from Denial of Service(DoS) Attacks[C]// IEEE. 2016 IEEE International Conference on Services Computing(SCC), June 27-July 2, 2016, SanFrancisco, CA, USA. New York: IEEE, 2016: 856-859. |
| [16] | YAROM Y, FALKNER K. Flush Reload: A High Resolution, Low Noise, L3 Cache Side-channel Attack[C]// USENIX. 23rd USENIX Security Symposium(USENIX Security 14), June 20-22, 2014, Diego, CA, USA. Berkeley: USENIX, 2014: 719-732. |
| [17] | WU Zhenyu, XU Zhang, WANG Haining. Whispers in the Hyper-space: High-bandwidth and Reliable Covert Channel Attacks Inside the Cloud[J]. IEEE/ACM Transactions on Networking, 2014,23(2):603-615. |
| [18] | DELIMITROU C, KOZYRAKIS C. Bolt: I Know What You did Last Summer in the Cloud[J]. ACM SIGARCH Computer Architecture News, 2017,45(1):599-613. |
| [19] | DELIMITROU C, KOZYRAKIS C. iBench: Quantifying Interference for Datacenter Applications[C]// IEEE. 2013 IEEE International Symposium on Workload Characterization(IISWC), September 22-24, 2013, Portland, OR, USA. New York: IEEE, 2013: 23-33. |
| [1] | 王湘懿, 张健. 基于图像和机器学习的虚拟化平台异常检测[J]. 信息网络安全, 2020, 20(9): 92-96. |
| [2] | 刘渊, 乔巍. 云环境下基于Kubernetes集群系统的容器网络研究与优化[J]. 信息网络安全, 2020, 20(3): 36-44. |
| [3] | 白嘉萌, 寇英帅, 刘泽艺, 查达仁. 云计算平台基于角色的权限管理系统设计与实现[J]. 信息网络安全, 2020, 20(1): 75-82. |
| [4] | 任良钦, 王伟, 王琼霄, 鲁琳俪. 一种新型云密码计算平台架构及实现[J]. 信息网络安全, 2019, 19(9): 91-95. |
| [5] | 余奕, 吕良双, 李肖坚, 王天博. 面向移动云计算场景的动态网络拓扑描述语言[J]. 信息网络安全, 2019, 19(9): 120-124. |
| [6] | 王紫璇, 吕良双, 李肖坚, 王天博. 基于共享存储的OpenStack虚拟机应用分发策略[J]. 信息网络安全, 2019, 19(9): 125-129. |
| [7] | 崔艳鹏, 冯璐铭, 闫峥, 蔺华庆. 基于程序切片技术的云计算软件安全模型研究[J]. 信息网络安全, 2019, 19(7): 31-41. |
| [8] | 葛新瑞, 崔巍, 郝蓉, 于佳. 加密云数据上支持可验证的关键词排序搜索方案[J]. 信息网络安全, 2019, 19(7): 82-89. |
| [9] | 田春岐, 李静, 王伟, 张礼庆. 一种基于机器学习的Spark容器集群性能提升方法[J]. 信息网络安全, 2019, 19(4): 11-19. |
| [10] | 赵谱, 崔巍, 郝蓉, 于佳. 一种针对El-Gamal数字签名生成的安全外包计算方案[J]. 信息网络安全, 2019, 19(3): 81-86. |
| [11] | 张振峰, 张志文, 王睿超. 网络安全等级保护2.0云计算安全合规能力模型[J]. 信息网络安全, 2019, 19(11): 1-7. |
| [12] | 冯新扬, 沈建京. 一种基于Yarn云计算平台与NMF的大数据聚类算法[J]. 信息网络安全, 2018, 18(8): 43-49. |
| [13] | 陶源, 黄涛, 张墨涵, 黎水林. 网络安全态势感知关键技术研究及发展趋势分析[J]. 信息网络安全, 2018, 18(8): 79-85. |
| [14] | 张琦, 林喜军, 曲海鹏. 云计算中支持授权相等测试的基于身份加密方案[J]. 信息网络安全, 2018, 18(6): 52-60. |
| [15] | 张建标, 杨石松, 涂山山, 王晓. 面向云计算环境的vTPCM可信管理方案[J]. 信息网络安全, 2018, 18(4): 9-14. |
| 阅读次数 | ||||||||||||||||||||||||||||||||||||||||||||||||||
|
全文 435
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||
|
摘要 956
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||