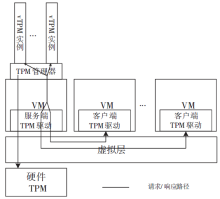
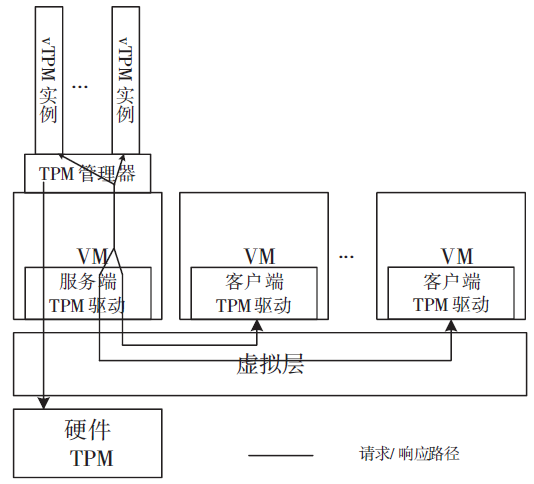
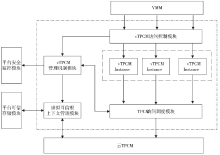
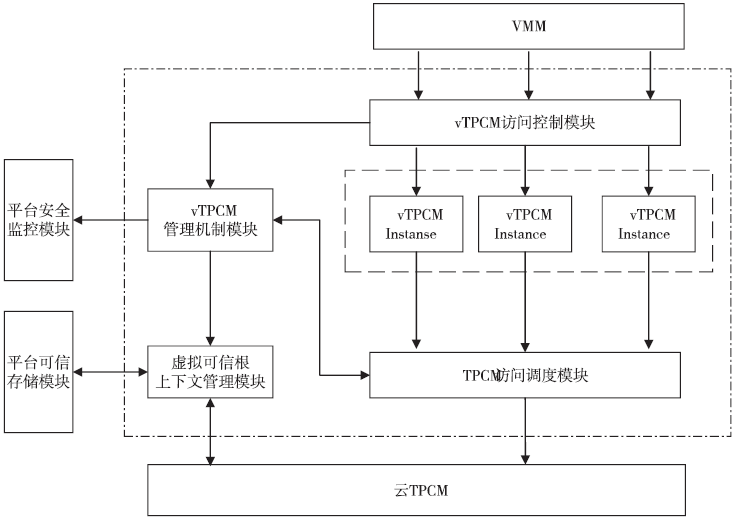
| [1] |
CHAWLA V, SOGANI P.Cloud Computing-The Future[J]. 2011(169):113-118.
|
| [2] |
QING Sihan.Security Protection of Critical Infrastructure[J]. Netinfo Security,2015(2):1-6.
|
|
卿斯汉. 关键基础设施安全防护[J]. 信息网络安全,2015(2):1-6.
|
| [3] |
CHEN Danwei, SHAO Ju, FAN Xiaowei, et al.MAH-ABE Based Privacy Access Control in Cloud Computing[J]. Acta Electronia Sinica, 2014,42(4):821-827.
|
|
陈丹伟, 邵菊, 樊晓唯,等. 基于MAH-ABE的云计算隐私保护访问控制[J]. 电子学报, 2014,42(4):821-827.
|
| [4] |
Trusted Computing Group. TCG Specification Architecture Overview Specification, Revision1.4[EB/OL]., 2017-11-1.
|
| [5] |
ZHANG Jianbiao, ZHAO Zixiao, HU Jun, et al.The Design Framework of Reconfigurable Virtual Root of Trust in Cloud Environment[J]. Netinfo Security, 2018(1): 1-8.
|
|
张建标, 赵子枭, 胡俊, 等. 云环境下可重构虚拟可信根的设计框架[J]. 信息网络安全, 2018(1): 1-8.
|
| [6] |
DING Yan, WANG Huaimin SHI Peichang, et al. Trusted Cloud Service[J]. Chinese Journal of Computers, 2015, 38(1):133-149.
|
|
丁滟, 王怀民, 史佩昌, 等. 可信云服务[J]. 计算机学报, 2015, 38(1):133-149.
|
| [7] |
WEN Weiping, GUO Ronghua, MENG Zheng, et al.Research and Implementation on Information Security Risk Assessment Key Technology[J]. Netinfo Security, 2015 (2): 7-14.
|
|
文伟平,郭荣华,孟正,等. 信息安全风险评估关键技术研究与实现[J]. 信息网络安全,2015(2):7-14.
|
| [8] |
HOSSEINZADEH S, LAURÉN S, LEPPÄNEN V. Security in Container-based Virtualization through vTPM[C] // IEEE. International Conference on Utility and Cloud Computing, November 16-18, Zhangjiajie, China. New York: IEEE, 2017:214-219.
|
| [9] |
WAN X, XIAO Z, REN Y.Building Trust into Cloud Computing Using Virtualization of TPCM[C] //IEEE. 2012 Fourth International Conference on Multimedia Information Networking and Security (MINES), November 2, Nanjing, China. New York: IEEE, 2012:59-63.
|
| [10] |
HU Jun, SHEN Changxiang, GONG Bei, et al.Trusted Computing 3.0 Engineering Fundamentals[M]. Beijing: The People's Posts and Telecommunications Press, 2017.
|
|
胡俊,沈昌祥,公备,等. 可信计算3.0工程初步[M]. 北京:人民邮电出版社,2017.
|
| [11] |
IBM. IBM's Software Trusted Platform Module(TPM)[EB/OL]. .
|
| [12] |
STUMPF F, ECKERT C.Enhancing Trusted Platform Modules with Hardware-based Virtualization Techniques[C] // IEEE. SECURWARE'08 Second International Conference on Emerging Security Information, Systems and Technologies, August 25, 2008, New York, USA. New York: IEEE, 2008:1-9.
|
| [13] |
ENGLAND P, LOESER J.Para-virtualized TPM Sharing[C] // IEEE. 11th Information Security Conference, March 11-12, 2008, Villach, Austria. Berlin Heidelberg: Springer, 2008: 119-132.
|
| [14] |
SADEGHI A R, STÜBLE C, WINANDY M. Property-based TPM Virtualization[J]. Information Security, 2008(1):1-16.
|
 ), 涂山山1,2, 王晓1,2
), 涂山山1,2, 王晓1,2
 ), Shanshan TU1,2, Xiao WANG1,2
), Shanshan TU1,2, Xiao WANG1,2