信息网络安全 ›› 2020, Vol. 20 ›› Issue (2): 7-13.doi: 10.3969/j.issn.1671-1122.2020.02.002
基于可信软件基的虚拟机动态监控机制研究
- 1.北京工业大学信息学部,北京 100124
2.可信计算北京市重点实验室,北京 100124
3.张家口学院,张家口 075000
-
收稿日期:2019-10-22出版日期:2020-02-10发布日期:2020-05-11 -
作者简介:作者简介:王晓(1983—),女,河北,博士研究生,主要研究方向为信息安全、可信计算、云计算等;赵军(1978—),男,河北,副教授,硕士,主要研究方向为网络安全、可信计算等;张建标(1969—),男,江苏,教授,博士,主要研究方向为信息安全、可信计算等。
-
基金资助:国家自然科学基金[61971014];河北省教育厅科技项目[Z2017158];国防科技实验信息安全实验室对外开放项目[2015XXAQ08]
Research on Dynamic Monitoring Mechanism for Virtual Machine Based on Trusted Software Base
WANG Xiao1,2, ZHAO Jun3, ZHANG Jianbiao1,2( )
)
- 1. Faculty of Information Technology, Beijing University of Technology, Beijing 100124, China
2. Beijing Key Laboratory of Trusted Computing, Beijing 100124, China
3. Zhangjiakou University, Zhangjiakou 075000, China
-
Received:2019-10-22Online:2020-02-10Published:2020-05-11
摘要:
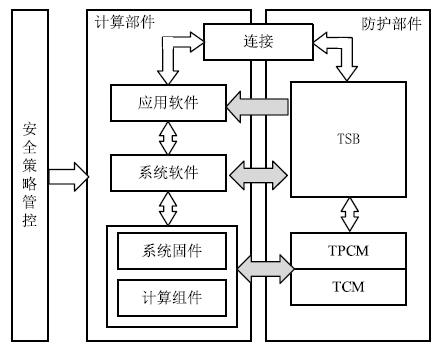
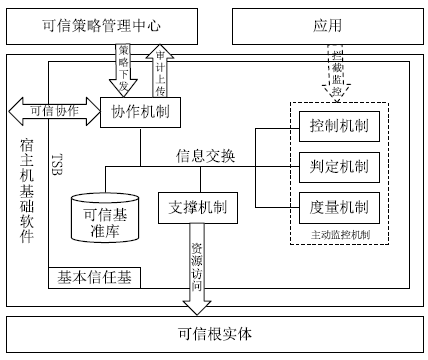
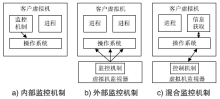
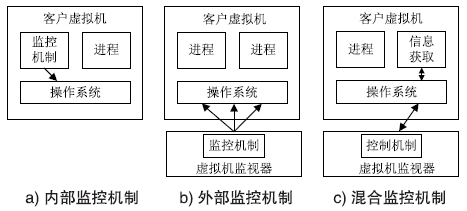
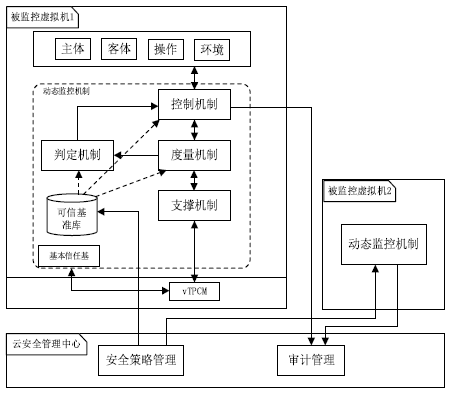
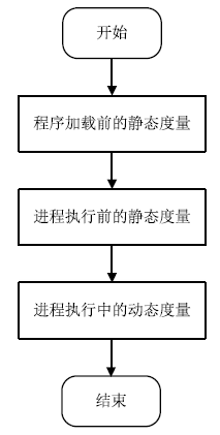
在云计算环境中,虚拟机是云服务提供商为云用户提供服务的主要载体。虚拟机运行过程中的安全可信性至关重要,直接关系到云用户服务的安全可信性。针对虚拟机运行过程中的行为可信性问题,文章提出基于主动免疫可信计算技术的虚拟机动态监控机制。该机制将主动免疫可信计算的双系统体系架构部署在虚拟机系统内部,利用可信软件基实现对虚拟机运行行为的主动可信度量及主动控制,保证了虚拟机运行过程中的安全可信性,解决了云用户服务的安全可信性问题。
中图分类号:
引用本文
王晓, 赵军, 张建标. 基于可信软件基的虚拟机动态监控机制研究[J]. 信息网络安全, 2020, 20(2): 7-13.
WANG Xiao, ZHAO Jun, ZHANG Jianbiao. Research on Dynamic Monitoring Mechanism for Virtual Machine Based on Trusted Software Base[J]. Netinfo Security, 2020, 20(2): 7-13.
| [1] | KADHIM Q K, YUSOF R, MAHDI H S, et al. A Review Study on Cloud Computing Issues[EB/OL]. ,2019-9-20. |
| [2] | ALI M, KHAN S U, VASILAKOS A V.Security in Cloud Computin: Opportunities and Challenges[J]. Information Sciences, 2015, 305(1): 357-383. |
| [3] | ZHANG Yuqing, WANG Xiaofei, LIU Xuefeng, et al.Survey on Cloud Computing Security[J]. Journal of Software, 2016, 27(6): 1328-1348. |
| 张玉清,王晓菲,刘雪峰,等.云计算环境安全综述[J]. 软件学报,2016,27(6):1328-1348. | |
| [4] | FENG Dengguo, ZHANG Min, ZHANG Yan, et al.Study on Cloud Computing Security[J]. Journal of Software, 2011, 22(1): 71-83. |
| 冯登国,张敏,张妍,等.云计算安全研究[J]. 软件学报,2011,22(1):71-83. | |
| [5] | OLIVERO I, HOLTMANNS S, MICHE Y, et al.Experiences in Trusted Cloud Computing[M]//Springer. Network and System Security. Cham: Springer, 2017: 19-30. |
| [6] | DU Ruizhong, PAN Wangyang, TIAN Junfeng.Dynamic Integrity Measurement Model Based on vTPM[J]. China Communications, 2018, 15(2): 88-99. |
| [7] | LIU Chuanyi, LIN Jie, TANG Bo.Dynamic Trustworthiness Verification Mechanism for Trusted Cloud Execution Environment[J]. Journal of Software, 2014, 25(3): 662-674. |
| 刘川意,林杰,唐博.面向云计算模式运行环境可信性动态验证机制[J]. 软件学报,2014,25(3):662-674. | |
| [8] | KUMAR P, SEHGAL V K, CHAUHAN D S, et al.Effective Ways of Secure, Private and Trusted Cloud Computing[J]. International Journal of Computer Science Issues, 2011, 8(3): 412-421. |
| [9] | SANTOS N, GUMMADI K P, RODRIGUES R. Towards Trusted Cloud Computing[EB/OL]. , 2019-9-20. |
| [10] | SHEN Changxiang.Constructing the Security System of Active Defense through Trusted Computing[J]. Information Security and Communications Privacy, 2016(6): 34. |
| 沈昌祥. 可信计算构筑主动防御的安全体系[J]. 信息安全与通信保密, 2016(6):34. | |
| [11] | SHEN Changxiang.Using Active Immune Trusted Computing 3.0 to Build a Strong Network Security Defense and Create a Clear Network Space[J]. Journal of Information Security Research, 2018, 4(4): 282-302. |
| 沈昌祥. 用主动免疫可信计算3.0筑牢网络安全防线营造清朗的网络空间[J]. 信息安全研究,2018,4(4):282-302. | |
| [12] | SHEN Changxiang, CHEN Xingshu.Construction of the Information Security Infrastructure Based on Trusted Computing[J]. Journal of Sichuan University: Engineering Science Edition, 2014, 46(1): 1-7 |
| 沈昌祥,陈兴蜀.基于可信计算构建纵深防御的信息安全保障体系[J]. 四川大学学报:工程科学版,2014,46(1):1-7. | |
| [13] | SHARIF M I, LEE W, CUI Weidong, et al. Secure in-vm Monitoring Using Hardware Virtualization[EB/OL]. , 2019-9-20. |
| [14] | GARFINKEL T, ROSENBLUM M. A Virtual Machine Introspection Based Architecture for Intrusion Detection[EB/OL]. , 2019-9-20 |
| [15] | HEBBAL Y, LANIEPCE S, MENAUD J M.Virtual Machine Introspection: Techniques and Applications[C]//IEEE. 2015 10th International Conference on Availability, Reliability and Security, August 24-27, 2015, Toulouse, France. NJ: IEEE, 2015: 676-685. |
| [16] | BAUMAN E, AYOADE G, LIN Zhiqiang.A Survey on Hypervisor-based Monitoring: Approaches, Applications, and Evolutions[J]. ACM Computing Surveys(CSUR), 2015, 48(1): 1-33. |
| [17] | LI Baohui, XU Kefu, ZHANG Peng, et al.Research and Application Progress of Virtual Machine Introspection Technology[J]. Journal of Software, 2016, 27(6): 1384-1401. |
| 李保珲,徐克付,张鹏,等.虚拟机自省技术研究与应用进展[J]. 软件学报,2016,27(6):1384-1401. | |
| [18] | LIN Jie, LIU Chuanyi, FANG Binxing.IVirt: Integrity Measurement Mechanism for Running Environment Based on Virtual Machine Introspection[J]. Chinese Journal of Computers. 2015, 38(1): 191-203. |
| 林杰,刘川意,方滨兴. IVirt:基于虚拟机自省的运行环境完整性度量机制[J]. 计算机学报,2015,38(1):191-203. | |
| [19] | PAYNE B D, CARBONE M, SHARIF M, et al.Lares: An Architecture for Secure Active Monitoring Using Virtualization[C]//IEEE. 2008 IEEE Symposium on Security and Privacy, May 18-22, 2008, Oakland, CA, USA. NJ: IEEE, 2008: 233-247. |
| [20] | WU Xiaolong, GAO Yunwei, TIAN Xinhui, et al.SecMon: A Secure Introspection Framework for Hardware Virtualization[C]//IEEE. 2013 21st Euromicro International Conference on Parallel, Distributed, and Network-Based Processing, February 27- March 1, Belfast, UK. NJ: IEEE, 2013: 282-286. |
| [21] | WANG Xueyang, KARRI R.Numchecker: Detecting Kernel Control-flow Modifying Rootkits by Using Hardware Performance Counters[C]//IEEE. 2013 50th ACM/EDAC/IEEE Design Automation Conference(DAC), May 29-June 7, 2013, Austin, TX, USA. NJ: IEEE, 2013: 1-7. |
| [1] | 余小军, 吴亚飚, 张玉清. 云安全体系结构设计研究[J]. 信息网络安全, 2020, 20(9): 62-66. |
| [2] | 徐玉伟, 赵宝康, 时向泉, 苏金树. 容器化安全服务功能链低延迟优化编排研究[J]. 信息网络安全, 2020, 20(7): 11-18. |
| [3] | 张健, 高铖, 宫良一, 顾兆军. 虚拟机自省技术研究[J]. 信息网络安全, 2017, 17(9): 63-68. |
| [4] | 张家伟, 张冬梅, 黄偲琪. 一种抗APT攻击的可信软件基设计与实现[J]. 信息网络安全, 2017, 17(6): 49-55. |
| [5] | 王文旭, 张健, 常青, 顾兆军. 云计算虚拟化平台安全问题研究[J]. 信息网络安全, 2016, 16(9): 163-168. |
| [6] | 田健生, 詹静. 基于TPCM的主动动态度量机制的研究与实现[J]. 信息网络安全, 2016, 16(6): 22-27. |
| [7] | 卿斯汉. 关键基础设施安全防护[J]. 信息网络安全, 2015, 15(2): 1-6. |
| [8] | 吴继康, 于徐红, 王虹. 基于第三方可信平台的混合云安全存储系统构建[J]. 信息网络安全, 2015, 26(12): 28-33. |
| [9] | 王李乐, 李明, 汪浩, 毕圣杰. 云WAF技术系统研究[J]. 信息网络安全, 2014, 14(12): 1-6. |
| [10] | 胡杨;胡欣. 基于可信计算的云安全研究与分析[J]. , 2013, 13(Z): 0-0. |
| [11] | 赵继军;陈伟. 一种基于云安全模型的信息系统安全等级保护测评方法[J]. , 2013, 13(Z): 0-0. |
| [12] | 李菊. 基于私有云安全平台的网络安全部署研究与实施[J]. , 2013, 13(8): 0-0. |
| [13] | 张显龙. 云计算安全总体框架与关键技术研究[J]. , 2013, 13(7): 0-0. |
| [14] | 朱圣才. 基于Windows Azure平台的虚拟化技术研究[J]. , 2013, 13(6): 0-0. |
| [15] | 刘川意;方滨兴. T-YUN:云提供商可信性审计与验证[J]. , 2012, 12(8): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||