信息网络安全 ›› 2018, Vol. 18 ›› Issue (4): 1-8.doi: 10.3969/j.issn.1671-1122.2018.04.001
• • 下一篇
基于同态加密与生物特征的安全身份认证研究
- 杭州电子科技大学通信工程学院,浙江杭州 310018
-
收稿日期:2018-02-02出版日期:2018-04-15发布日期:2020-05-11 -
作者简介:作者简介:游林(1966—),男,江西,教授,博士,主要研究方向为计算代数、密码学、生物特征识别及其应用等;梁家豪(1990—),男,河南,硕士研究生,主要研究方向为生物特征密码学。
-
基金资助:国家自然科学基金[61772166,61272045];浙江省自然科学基金重点项目[ LZ17F020002]
Research on Secure Identity Authentication Based on Homomorphic Encryption and Biometric
- College of Communication Engineering, Hangzhou Dianzi University, Hangzhou Zhejiang 310018, China
-
Received:2018-02-02Online:2018-04-15Published:2020-05-11
摘要:
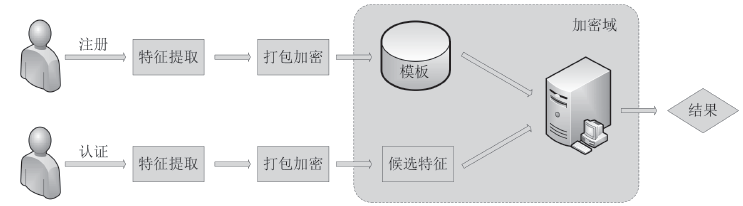
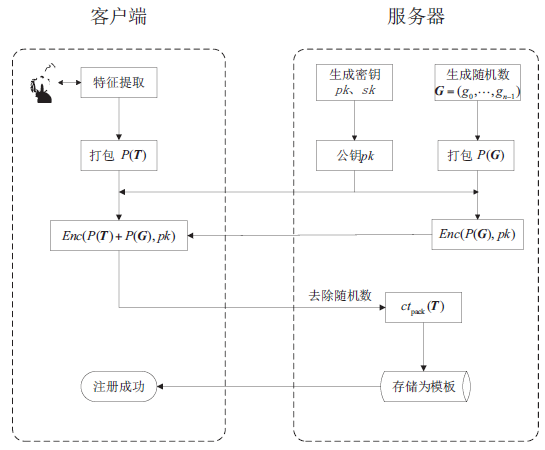
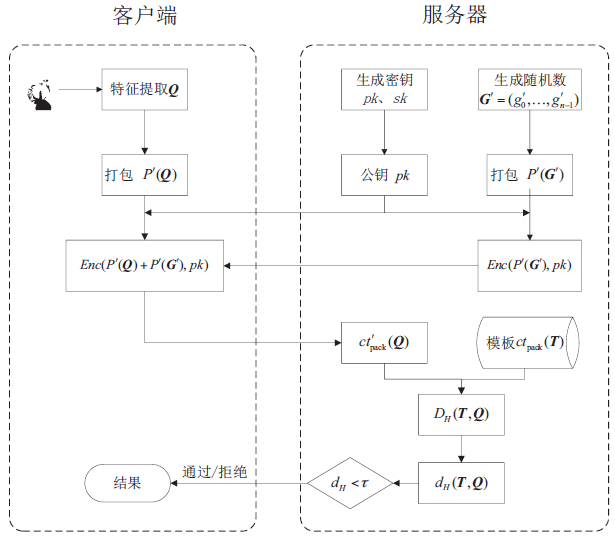
大数据技术的快速发展和广泛应用,给传统的身份认证技术带来了新的安全挑战,因此研究适应于复杂网络环境的安全身份认证技术具有重要的实际意义。在基于传统生物特征的认证技术的基础上,文章提出了一个基于同态加密与生物特征的身份认证方案。该方案借助基于RLWE的同态加密技术和一种消息编码技术,将用户的生物特征信息加密后外包存储,用户的身份信息匹配过程在加密域进行。方案在数据传输过程中引入随机数,用于抵抗重放攻击。文章利用大数据环境下的多种典型的攻击手段对方案进行安全性分析证明,结果表明方案对复杂网络环境具有良好的适用性。
中图分类号:
引用本文
游林, 梁家豪. 基于同态加密与生物特征的安全身份认证研究[J]. 信息网络安全, 2018, 18(4): 1-8.
Lin YOU, Jiahao LIANG. Research on Secure Identity Authentication Based on Homomorphic Encryption and Biometric[J]. Netinfo Security, 2018, 18(4): 1-8.
| [1] | ZHOU Liansong, YANG Jie, TAN Pingzhang, et al.Identity Authentication Technology and Its Development Trend[J]. Communications Technology, 2009,42(10):183-185. |
| 周楝淞,杨洁, 谭平嶂, 等. 身份认证技术及其发展趋势[J]. 通信技术, 2009,42(10):183-185. | |
| [2] | FENG Quan.Privacy-protection Authentication Based on Fingerprint [D]. Beijing: Beijing University of Posts and Telecommunications, 2010. |
| 冯全. 基于指纹的隐私保护型身份认证技术 [D]. 北京:北京邮电大学,2010. | |
| [3] | WANG Yuna, LV Qiuyun.A New Network Authentication Scheme Based on Biometric Recognition[J]. Netinfo Security, 2014(8):1-5. |
| 王毓娜, 吕秋云. 基于生物识别的网络身份认证新方案[J]. 信息网络安全, 2014(8):1-5. | |
| [4] | JAIN A K, NANDAKNMAR K, NAGAR A.Biometric Template Security[J]. EURASIP Journal on Advances in Signal Processing, 2008(1): 1-17. |
| [5] | RIVEST R L, ADLEMAN L, DERTOUZOS M L.On Data Banks and Privacy Homomorphisms[J]. Foundations of Secure Computations, 1978,4(11):169-180. |
| [6] | ELGAMAL T.A Public Key Cryptosystem and a Signature Scheme Based on Discrete Logarithms[J]. IEEE Trans.inf.theory, 1985, 31(4):469-472. |
| [7] | PAILLIER P.Public-key Cryptosystems Based on Composite Degree Residuosity Classes[C]// EUROCRYPT. the 17th Internatinal Conference on Theory and Application of Cryptographic Techniques, May 2-6, 1999, Prague, Czech Republic. Heidelberg: Springer Berlin Heidelberg, 1999, 547(1):223-238. |
| [8] | BONEH D, GOH E J, NISSIM K.Evaluating 2-DNF Formulas on Ciphertexts[C]// TCC. the Second International Conference on Theory of Cryptography, February 10 - 12, 2005. Cambridge, MA,USA.Heidelberg: Springer Berlin Heidelberg, 2005:325-341. |
| [9] | GENTRY C.A Fully Homomorphic Encryption Scheme [D]. Palo Alto :Stanford University, 2009. |
| [10] | SMART N P, VERCAUTEREN F.Fully Homomorphic Encryption with Relatively Small Key and Ciphertext Sizes[C]// PKC. the 13th International Conference on Practice and Theory in Public Key Cryptography, May 26 - 28, 2010, Paris, France. Heidelberg: Springer Berlin Heidelberg, 2010:420-443. |
| [11] | EL-YAHYAOUI A.A Verifiable Fully Homomorphic Encryption Scheme to Secure Big Data in Cloud Computing[C]// IEEE. the International Conference on Wireless Networks and Mobile Communications, November 1-4, 2017,Rabat, Morocco.NJ: IEEE,2017:1-5. |
| [12] | ZHU Zhengyang, LIU Qiang, TANG Chunming, et al.Electronic Voting Scheme based on LWE Homomorphic Encryption[J]. Netinfo Security, 2013(5):8-11. |
| 朱正阳, 刘镪, 唐春明,等. 基于LWE同态加密的电子投票方案[J]. 信息网络安全, 2013(5):8-11. | |
| [13] | UPMANYU M, NAMBOODIRI A M, SRINATHAN K, et al.Blind Authentication: a Secure Crypto-biometric Verification Protocol[J]. IEEE Transactions on Information Forensics and Security, 2010, 5(2): 255-268. |
| [14] | BARNI M, BIANCHI T, CATALANO D.et al.A Privacy-compliant Fingerprint Recognition System Based on Homomorphic Encryption and Fingercode Template[C]// IEEE. Fourth IEEE International Conference on Biometrics: Theory Applications and Systems, September 27-29, 2010, Washington, DC, USA.NJ: IEEE, 2010:1-7. |
| [15] | SARIER N D.Practical Multi-factor Biometric Remote Authentication[C]// IEEE. Fourth IEEE International Conference on Biometric: Theory Application & Systems, September 27-29, 2010, Washington, DC, USA.NJ: IEEE,2010:1-6. |
| [16] | HIRANO T, HATTORI M, ITO T, et al.Homomorphic Encryption-based Cancelable Biometrics Secure against Replay and Its Related Attack[C]//IEEE. International Symposium on Information Theory and Its Application(ISITA), October 28-31, 2012, Honolulu, HI, USA. NJ: IEEE, 2012:421-425. |
| [17] | BRINGER J, CHABANNE H, PATEY A.Privacy-preserving Biometric Identification Using Secure Multiparty Computation: An Overview and Recent Trends[J]. IEEE Signal Processing Magazine, 2013, 30(2):42-52. |
| [18] | ABDULJABBAR Z A, JIN Hai, IBRAHIM A, et al.Secure Biometric Image Retrieval in IoT-cloud[C]//IEEE. IEEE International Conference on Signal Processing, Communications and Computing, August 5-8, 2016, Hong Kong, China.NJ: IEEE, 2016:1-6. |
| [19] | HAHN C, HUR J.Efficient and Privacy-preserving Biometric Identification in Cloud[J]. ICT Express, 2016, 2(3):135-139. |
| [20] | YASUDA M.Secure Hamming Distance Computation for Biometrics Using Ideal-lattice and Ring-LWE Homomorphic Encryption[J]. Information Systems Security,2017, 26(2):85-103. |
| [21] | WANG Yongjian, ZHANG Jian, CHENG Shaoyu, et al.An Improved Design of Homomorphic Encryption for Cloud Computing[J]. Netinfo Security, 2017(3):21-26. |
| 王永建, 张健, 程少豫,等. 面向云计算的同态加密改进设计[J]. 信息网络安全, 2017(3):21-26. | |
| [22] | LAUTER K, NAEHRIG M, VAIKUNTANATHAN V.Can Homomorphic Encryption Be Practical?[C]//ACM. Proceedings of 3rd ACM Cloud Computing Security Workshop, CCSW 2011, October 21-21,2011, Chicago, Ilinois, USA.New York: ACM, 2011:113-124. |
| [23] | YASUDA M, SHIMOYAMA T, KOGURE J, et al.Practical Packing Method in Somewhat Homomorphic Encryption[M]. Heidelberg :Springer Berlin Heidelberg, 2014. |
| [24] | OSADCHY M, PINKAS B, JARROUS A, et al.SCiFI- a System for Secure Face Identification[C]//IEEE. Proceedings of the 2010 IEEE Symposium on Security and Privacy. May 16-19, 2010, Washington, DC, USA. NJ:IEEE Computer Society, 2010:239-254. |
| [25] | MITSUHIRO H, NORI M, TAKASHI I, et al.Provably-secure Cancelable Biometric Using 2-DNF Evaluation[J]. Journal of information Processing, 2012,20(2):496-507. |
| [1] | 傅智宙, 王利明, 唐鼎, 张曙光. 基于同态加密的HBase二级密文索引方法研究[J]. 信息网络安全, 2020, 20(4): 55-64. |
| [2] | 刘晓芬, 陈晓峰, 连桂仁, 林崧. 基于d级单粒子的可认证多方量子秘密共享协议[J]. 信息网络安全, 2020, 20(3): 51-55. |
| [3] | 唐春明, 林旭慧. 隐私保护集合交集计算协议[J]. 信息网络安全, 2020, 20(1): 9-15. |
| [4] | 张富友, 王琼霄, 宋利. 基于生物特征识别的统一身份认证系统研究[J]. 信息网络安全, 2019, 19(9): 86-90. |
| [5] | 刘文超, 潘峰, 杨晓元, 周潭平. 基于GPU的全同态加密软件库调试与分析[J]. 信息网络安全, 2019, 19(6): 76-83. |
| [6] | 张顺, 陈张凯, 梁风雨, 石润华. 基于Bell态的量子双向身份认证协议[J]. 信息网络安全, 2019, 19(11): 43-48. |
| [7] | 张敏, 许春香, 黄闽英. 远程医疗环境下面向多服务器的轻量级多因子身份认证协议研究[J]. 信息网络安全, 2019, 19(10): 42-49. |
| [8] | 秦中元, 韩尹, 朱雪金. 基于改进DGHV算法的云存储密文全文检索研究[J]. 信息网络安全, 2019, 19(1): 8-8. |
| [9] | 胡卫, 吴邱涵, 刘胜利, 付伟. 基于国密算法和区块链的移动端安全eID及认证协议设计[J]. 信息网络安全, 2018, 18(7): 7-9. |
| [10] | 魏占祯, 王守融, 李兆斌, 李伟隆. 基于OpenFlow的SDN终端接入控制研究[J]. 信息网络安全, 2018, 0(4): 23-31. |
| [11] | 宋新霞, 马佳敏, 陈智罡, 陈克非. 基于SEAL的虹膜特征密文认证系统[J]. 信息网络安全, 2018, 18(12): 15-22. |
| [12] | 陈付龙, 张紫阳, 王涛春, 谢冬. 一种基于联络信号的物联网安全身份认证方法[J]. 信息网络安全, 2018, 18(11): 40-48. |
| [13] | 王嵘冰, 李雅囡, 徐红艳, 冯勇. 适合云服务环境的实数全同态加密方案[J]. 信息网络安全, 2018, 18(11): 49-56. |
| [14] | 孙子文, 李富. 基于HMM与D-S证据理论的手势身份认证方法[J]. 信息网络安全, 2018, 18(10): 17-23. |
| [15] | 亢保元, 王佳强, 邵栋阳, 李春青. 一种适用于异构Ad Hoc无线传感器网络的身份认证与密钥共识协议[J]. 信息网络安全, 2018, 18(1): 23-30. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||