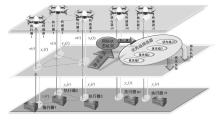
信息网络安全 ›› 2025, Vol. 25 ›› Issue (6): 943-954.doi: 10.3969/j.issn.1671-1122.2025.06.009
基于贪心算法优化工业控制系统数据冲突与DDoS攻击防御机制
陈大1,2,3, 蔡肖1,2( ), 孙彦斌1,2, 董崇武1,2
), 孙彦斌1,2, 董崇武1,2
- 1.广州大学网络空间先进技术研究院,广州 510006
2.广东省工业控制系统攻防对抗重点实验室,广州 510006
3.四川大学电气工程学院,成都 610065
-
收稿日期:2025-02-28出版日期:2025-06-10发布日期:2025-07-11 -
通讯作者:蔡肖 caixiao327327@163.com -
作者简介:陈大(1994—),女,贵州,博士研究生,主要研究方向为工业控制系统、切换系统|蔡肖(1995—),男,广东,博士,主要研究方向为网络化控制系统、工业控制系统及安全|孙彦斌(1987—),男,山东,教授,博士,CCF会员,主要研究方向为网络安全、工业控制系统安全、未来网络|董崇武(1990—),男,广东,博士研究生,主要研究方向为可靠边缘计算、凸优化理论、鞅理论、工业控制系统安全和数字孪生。 -
基金资助:国家自然科学基金(62402129);国家自然科学基金(62272119);国家自然科学基金(62372126);国家自然科学基金(62372129);国家自然科学基金(U2436208);国家自然科学基金(U2468204);中国博士后创新人才支持计划(BX20240095);中国博士后科学基金(2024M750616);广东省基础与应用基础研究基金(2020A1515010450);广东省基础与应用基础研究基金(2021A1515012307);广东省高校珠江学者资助计划(2019);广东省高等教育创新群体项目(2020KCXTD007);广东省工业控制系统攻防对抗重点实验室项目(2024B1212020010);广州市基础与应用基础研究基金(2024A04J9969);广州市高等教育创新群体项目(202032854)
Optimization of Data Conf lict and DDoS Attack Defense Mechanisms in Industrial Control Systems Based on Greedy Algorithm
CHEN Da1,2,3, CAI Xiao1,2( ), SUN Yanbin1,2, DONG Chongwu1,2
), SUN Yanbin1,2, DONG Chongwu1,2
- 1. Cyberspace Institute of Advanced Technology, Guangzhou University, Guangzhou 510006, China
2. Guangdong Key Laboratory of Industrial Control System Security, Guangzhou 510006, China
3. College of Electrical Engineering, Sichuan University, Chengdu 610065, China
-
Received:2025-02-28Online:2025-06-10Published:2025-07-11
摘要:
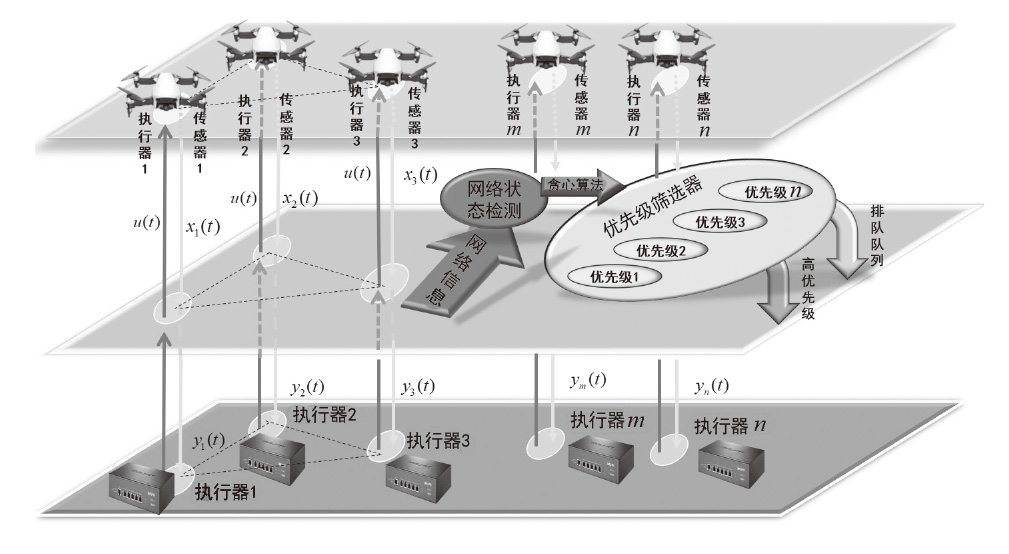
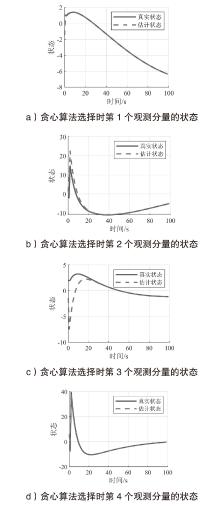
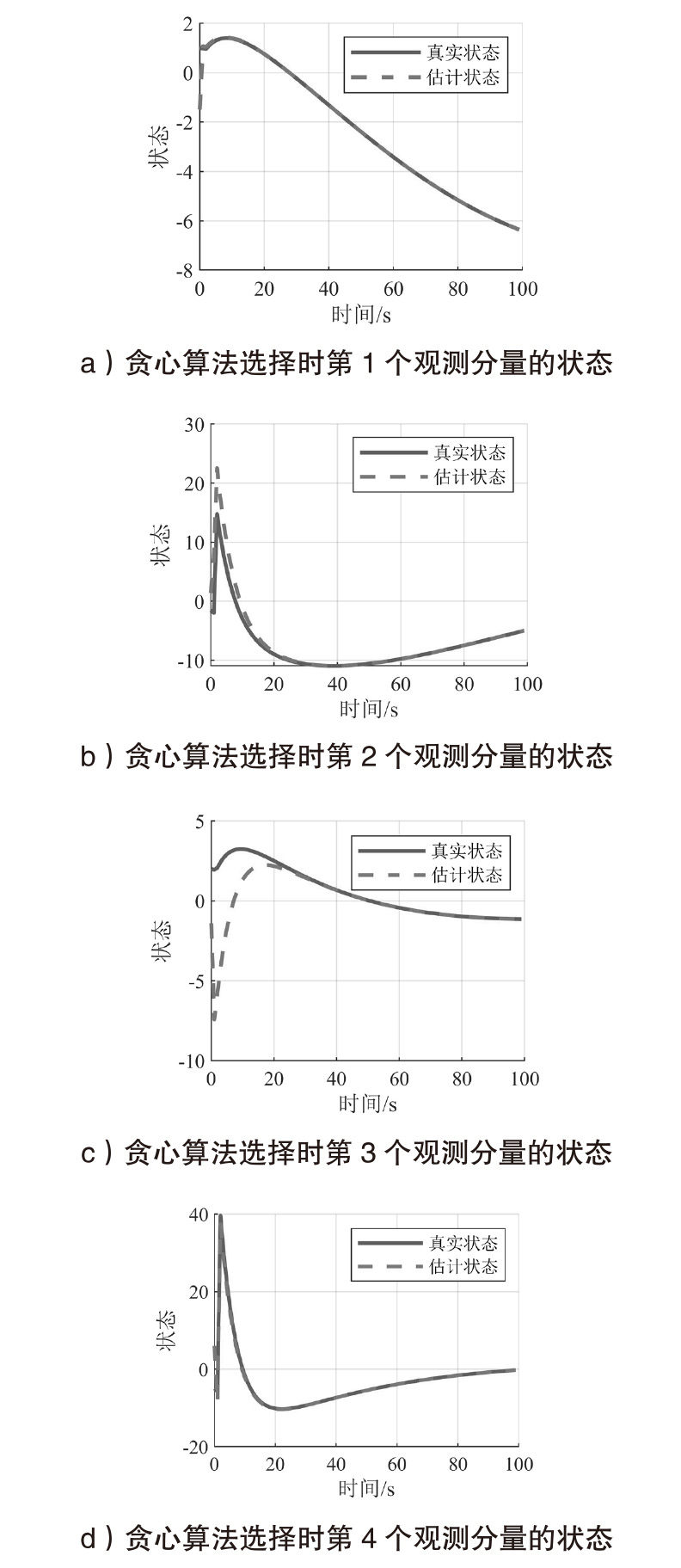
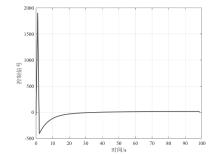
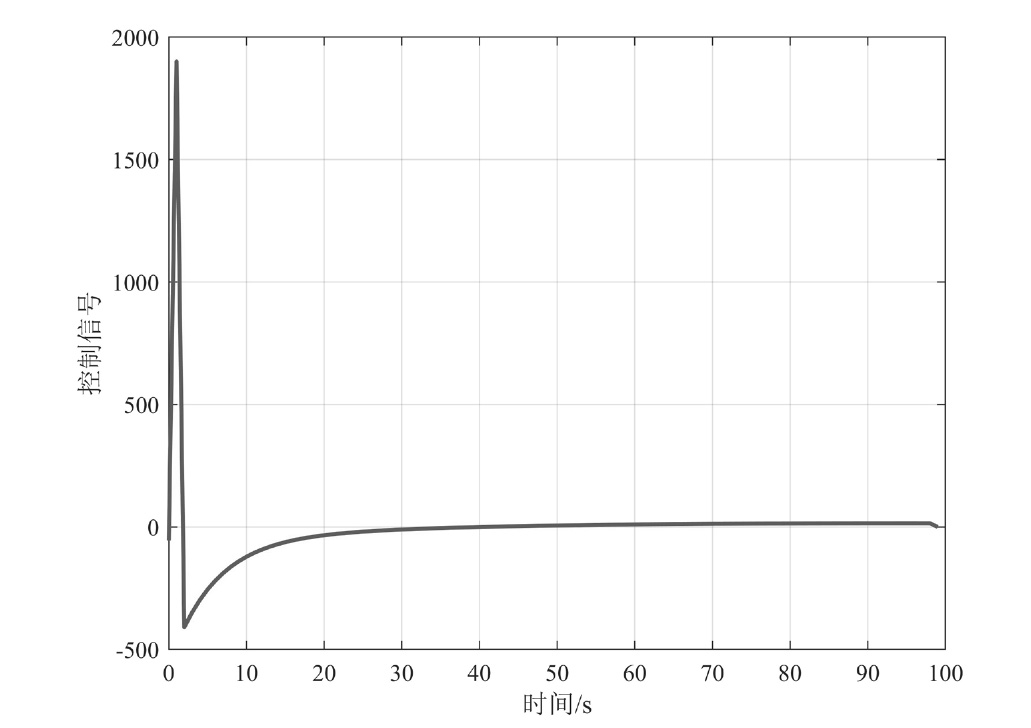
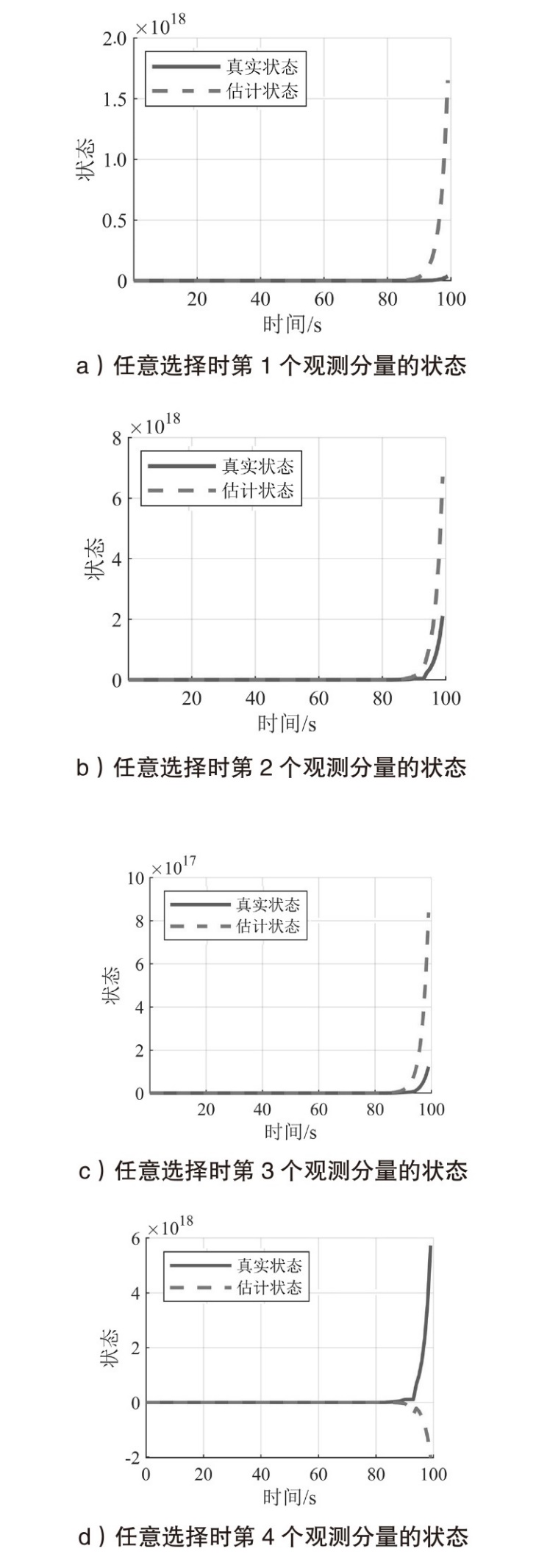
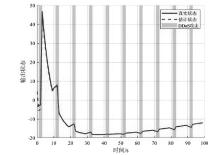
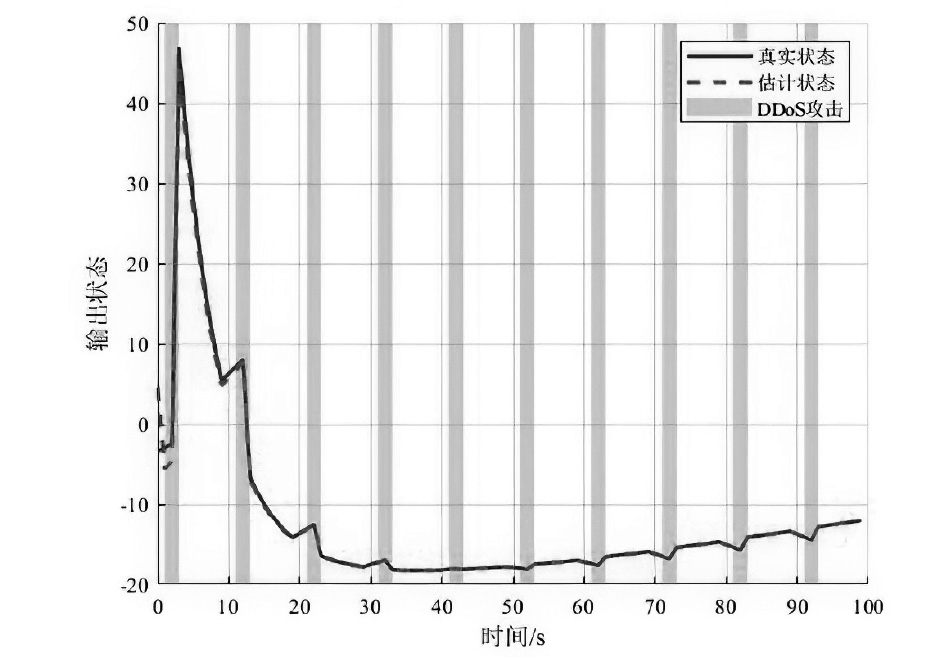
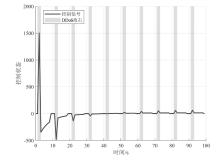
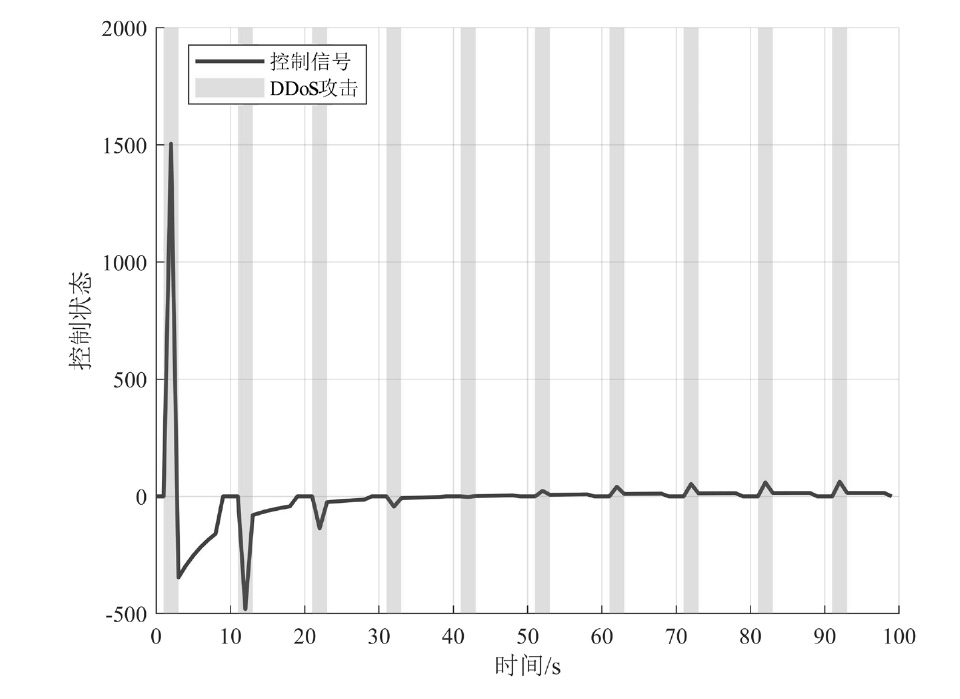
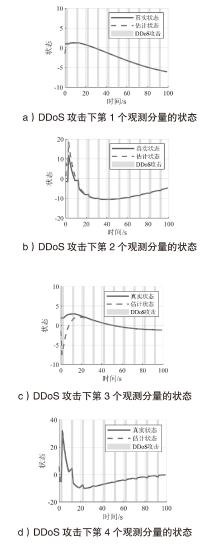
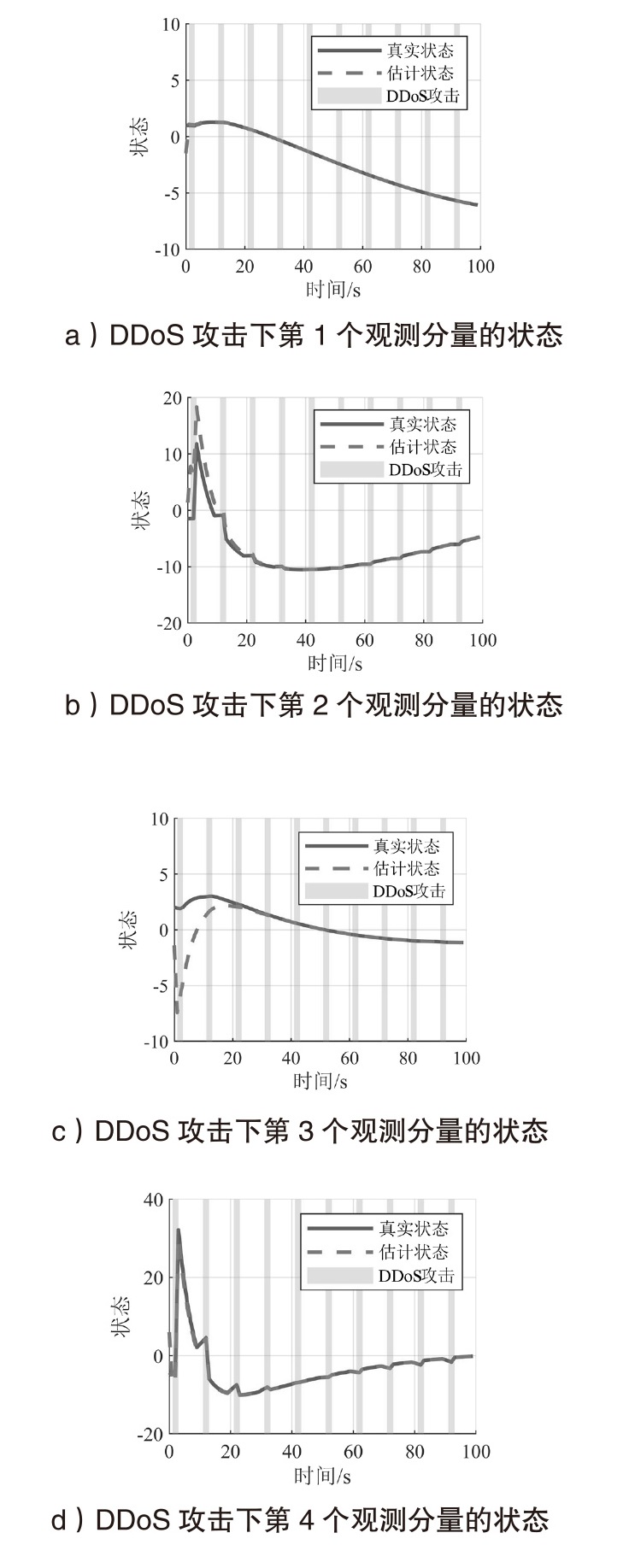
在现代数字网络工业控制系统中,数据冲突和DDoS攻击严重威胁系统的安全与稳定。文章提出基于贪心算法优化工业控制系统数据冲突与DDoS攻击防御机制,用于同时解决数据冲突与DDoS攻击问题。首先,构建基于贪心算法的自适应资源分配模型,通过实时监测网络流量和系统状态,动态调整优先级分配策略,从而有效避免数据冲突并防御DDoS攻击。其次,基于Lyapunov定理设计控制器与观测器,进一步提升系统对数据冲突和DDoS攻击的应对能力。分析结果表明,文章所提方法能显著降低数据冲突的发生频率,并有效增强系统抵御DDoS攻击的能力。此外,通过无人机倒立摆系统的仿真实验进一步验证了该方法的有效性,为数字网络工业控制系统的安全防护提供了一种解决方案。
中图分类号:
引用本文
陈大, 蔡肖, 孙彦斌, 董崇武. 基于贪心算法优化工业控制系统数据冲突与DDoS攻击防御机制[J]. 信息网络安全, 2025, 25(6): 943-954.
CHEN Da, CAI Xiao, SUN Yanbin, DONG Chongwu. Optimization of Data Conf lict and DDoS Attack Defense Mechanisms in Industrial Control Systems Based on Greedy Algorithm[J]. Netinfo Security, 2025, 25(6): 943-954.
| [1] | AHMED I, JEON G, PICCIALLI F. From Artificial Intelligence to Explainable Artificial Intelligence in Industry 4.0: A Survey on What, How, and Where[J]. IEEE Transactions on Industrial Informatics, 2022, 18(8): 5031-5042. |
| [2] | NTAMO D, LOPEZ-MONTERO E, MACK J, et al. Industry 4.0 in Action:Digitalisation of a Continuous Process Manufacturing for Formulated Products[EB/OL]. (2022-06-01)[2025-01-10]. https://doi.org/10.1016/j.dche.2022.100025. |
| [3] | ESWARAN M, BAHUBALENDRUNI M V A R. Challenges and Opportunities on AR/VR Technologies for Manufacturing Systems in the Context of Industry 4.0: A State of the Art Review[J]. Journal of Manufacturing Systems, 2022, 65: 260-278. |
| [4] | KNAPP E D, LANGILL J. Industrial Network Security: Securing Critical Infrastructure Networks for Smart Grid, SCADA, and Other Industrial Control Systems[M]. New York: ACM, 2024. |
| [5] | TURNER C J, OYEKAN J, STERGIOULAS L, et al. Utilizing Industry 4.0 on the Construction Site: Challenges and Opportunities[J]. IEEE Transactions on Industrial Informatics, 2021, 17(2): 746-756. |
| [6] | ARISHI A, KRISHNAN K, ARISHI M. Machine Learning Approach for Truck-Drones Based Last-Mile Delivery in the Era of Industry 4.0[EB/OL]. (2022-12-01)[2025-01-10]. https://doi.org/10.1016/j.engappai.2022.105439. |
| [7] | KOSHTA N, DEVI Y, CHAUHAN C. Evaluating Barriers to the Adoption of Delivery Drones in Rural Healthcare Supply Chains: Preparing the Healthcare System for the Future[J]. IEEE Transactions on Engineering Management, 2022(71): 13096-13108. |
| [8] | ZHANG Peiying, WANG Chao, QIN Zeyu, et al. A Multidomain Virtual Network Embedding Algorithm Based on Multiobjective Optimization for Internet of Drones Architecture in Industry 4.0[J]. Software: Practice and Experience, 2022, 52(3): 710-728. |
| [9] | SUN Nianyi, ZHAO Jin, SHI Qing, et al. Moving Target Tracking by Unmanned Aerial Vehicle: A Survey and Taxonomy[J]. IEEE Transactions on Industrial Informatics, 2024, 20(5): 7056-7068. |
| [10] | WANG Xin, SUN Jian, WANG Gang, et al. Data-Driven Control of Distributed Event-Triggered Network Systems[J]. IEEE/CAA Journal of Automatica Sinica, 2023, 10(2): 351-364. |
| [11] | YUAN Fang, ZHANG Shuting, XING Guibin, et al. Parameter Control Methods for Discrete Memristive Maps with Network Structure[J]. IEEE Transactions on Industrial Informatics, 2024, 20(5): 7194-7204. |
| [12] | LI Fanghui, HOU Zhongsheng. Learning-Based Model-Free Adaptive Control for Nonlinear Discrete-Time Networked Control Systems under Hybrid Cyber Attacks[J]. IEEE Transactions on Cybernetics, 2024, 54(3): 1560-1570. |
| [13] | VLADIMIROV S S, VYBORNOVA A, MUTHANNA A, et al. Network Coding Datagram Protocol for TCP/IP Networks[J]. IEEE Access, 2023(11): 43485-43498. |
| [14] | REN Wei. Research on Software Defined Network Control Technology for Internet of Things[D]. Beijing: Beijing University of Posts and Telecommunications, 2021. |
| 任玮. 面向物联网的软件定义网络控制技术研究[D]. 北京: 北京邮电大学, 2021. | |
| [15] | YANG Shenghao, YEUNG R W. Network Communication Protocol Design from the Perspective of Batched Network Coding[J]. IEEE Communications Magazine, 2022, 60(1): 89-93. |
| [16] | KIM D M, SORENSEN R B, MAHMOOD K, et al. Data Aggregation and Packet Bundling of Uplink Small Packets for Monitoring Applications in LTE[J]. IEEE Network, 2017, 31(6): 32-38. |
| [17] | XIE Ronggui, YIN Huarui, CHEN Xiaohui, et al. Many Access for Small Packets Based on Precoding and Sparsity-Aware Recovery[J]. IEEE Transactions on Communications, 2016, 64(11): 4680-4694. |
| [18] | HUA Lanfeng, ZHU Hong, ZHONG Shouming, et al. Fixed-Time Stability of Nonlinear Impulsive Systems and Its Application to Inertial Neural Networks[J]. IEEE Transactions on Neural Networks and Learning Systems, 2024, 35(2): 1872-1883. |
| [19] | LIU Bin, LIU Tao, DOU Chunxia. Stability of Discrete-Time Delayed Impulsive Linear Systems with Application to Multi-Tracking[J]. International Journal of Control, 2014, 87(5): 911-924. |
| [20] | CHEN Yongxuan, WANG Dianhui. An Improved Deep Kernel Partial Least Squares and Its Application to Industrial Data Modeling[J]. IEEE Transactions on Industrial Informatics, 2024, 20(5): 7894-7903. |
| [21] | XIANG Wei, YU Kan, HAN Fengling, et al. Advanced Manufacturing in Industry 5.0: A Survey of Key Enabling Technologies and Future Trends[J]. IEEE Transactions on Industrial Informatics, 2024, 20(2): 1055-1068. |
| [22] | CAI Xiao, SHI Kaibo, SHE Kun, et al. Performance Degradation Estimation Mechanisms for Networked Control Systems under DoS Attacks and Its Application to Autonomous Ground Vehicle[J]. IEEE Transactions on Cybernetics, 2024, 54(5): 2992-3002. |
| [23] | LI Bin, ZHOU Xinglian, NING Zhaoke, et al. Dynamic Event-Triggered Security Control for Networked Control Systems with Cyber-Attacks: A Model Predictive Control Approach[J]. Information Sciences, 2022(612): 384-398. |
| [24] | QIAO Libing, DONG Enhuan, YIN Huanpu, et al. Intelligent Network Device Identification Based on Active TCP/IP Stack Probing[J]. IEEE Network, 2024, 38(6): 187-193. |
| [25] | ZHANG Nannan, WANG Wei, XIN Xiaofeng, et al. Low-Delay Ultra-Small Packet Transmission with in-Network Aggregation via Distributed Stochastic Learning[J]. IEEE Transactions on Communications, 2024, 72(5): 2655-2669. |
| [26] | CHEN Da, LIU Xingwen, SHI Kaibo, et al. Exponential Stability of Discrete-Time Systems with Slowly Time-Varying Delays[EB/OL]. (2022-11-01)[2025-01-10]. https://doi.org/10.1016/j.nahs.2022.101246. |
| [27] | LIU Kun, FRIDMAN E, XIA Yuanqing. Networked Control Under Communication Constraints: A Time-Delay Approach[M]. Heidelberg: Springer, 2020. |
| [1] | 申秀雨, 姬伟峰. 考虑安全的边—云协同计算卸载成本优化[J]. 信息网络安全, 2024, 24(7): 1110-1121. |
| [2] | 王健, 陈琳, 王凯崙, 刘吉强. 基于时空图神经网络的应用层DDoS攻击检测方法[J]. 信息网络安全, 2024, 24(4): 509-519. |
| [3] | 印杰, 陈浦, 杨桂年, 谢文伟, 梁广俊. 基于人工智能的物联网DDoS攻击检测[J]. 信息网络安全, 2024, 24(11): 1615-1623. |
| [4] | 蒋英肇, 陈雷, 闫巧. 基于双通道特征融合的分布式拒绝服务攻击检测算法[J]. 信息网络安全, 2023, 23(7): 86-97. |
| [5] | 范明钰, 李珂. 一种基于RNN区分DDoS攻击类型的方法[J]. 信息网络安全, 2022, 22(7): 1-8. |
| [6] | 罗文华, 程家兴. 基于Hadoop架构的混合型DDoS攻击分布式检测系统[J]. 信息网络安全, 2021, 21(2): 61-69. |
| [7] | 王健, 王语杰, 韩磊. 基于突变模型的SDN环境中DDoS攻击检测方法[J]. 信息网络安全, 2020, 20(5): 11-20. |
| [8] | 张可, 汪有杰, 程绍银, 王理冬. DDoS攻击中的IP源地址伪造协同处置方法[J]. 信息网络安全, 2019, 19(5): 22-29. |
| [9] | 喻志彬, 马程, 李思其, 王淼. 基于Web应用层的DDoS攻击模型研究[J]. 信息网络安全, 2019, 19(5): 84-90. |
| [10] | 张雪博, 刘敬浩, 付晓梅. 基于改进Logistic回归算法的抗Web DDoS攻击模型的设计与实现[J]. 信息网络安全, 2017, 17(6): 62-67. |
| [11] | 李洁, 许鑫, 陈宇, 张丁文. 模拟DDoS攻击场景下的云取证模型的研究[J]. 信息网络安全, 2015, 15(6): 67-72. |
| [12] | 姜颖军;张淑芝. 网吧DDoS攻击应急处置方案解析[J]. , 2009, 9(9): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||