信息网络安全 ›› 2026, Vol. 26 ›› Issue (1): 139-149.doi: 10.3969/j.issn.1671-1122.2026.01.012
基于非局部机制的可逆神经网络视频隐写研究
- 中国人民武装警察部队工程大学密码工程学院,西安 710086
-
收稿日期:2025-08-06出版日期:2026-01-10发布日期:2026-02-13 -
通讯作者:胡方锰2670884020@qq.com -
作者简介:钮可(1981—),男,浙江,教授,博士,主要研究方向为信息隐藏、多媒体安全|胡方锰(1998—),男,浙江,硕士研究生,主要研究方向为视频隐写|李军(1987—),男,湖南,讲师,博士,主要研究方向为多媒体信息隐藏 -
基金资助:国家自然科学基金(62272478)
Research on Reversible Neural Network Video Steganography Based on Nonlocal Mechanism
- School of Cryptography Engineering, Engineering University of PAP, Xi’an 710086, China
-
Received:2025-08-06Online:2026-01-10Published:2026-02-13
摘要:
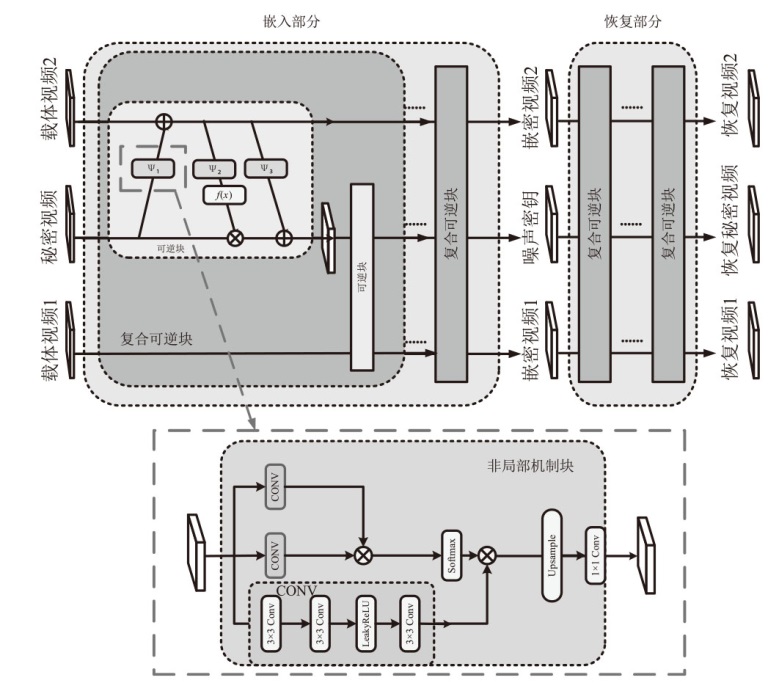
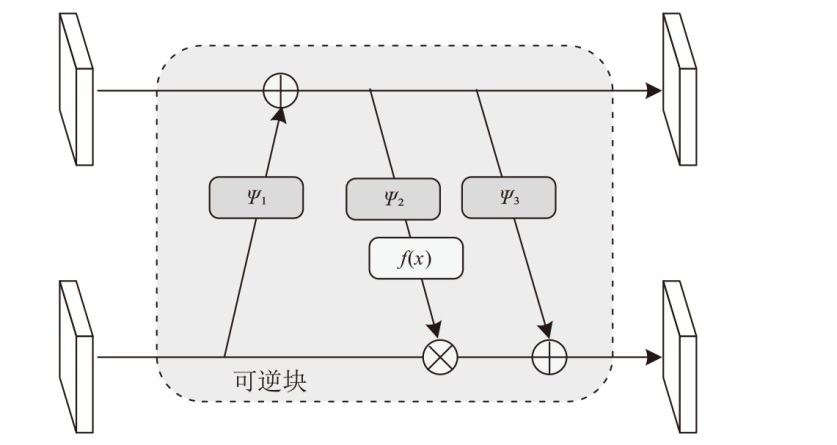
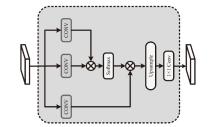
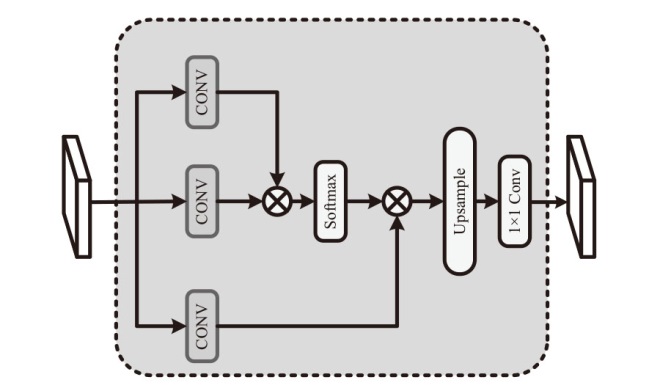
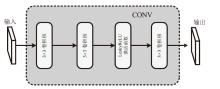
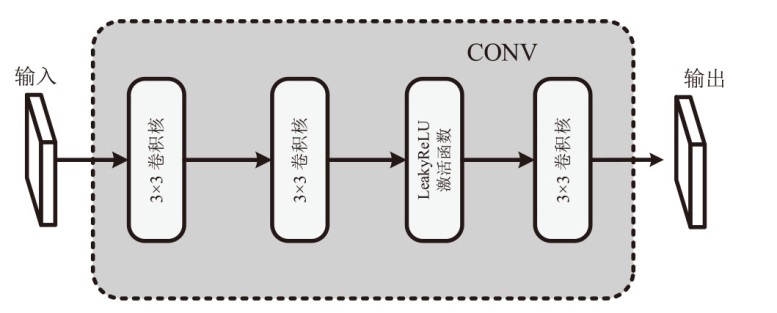
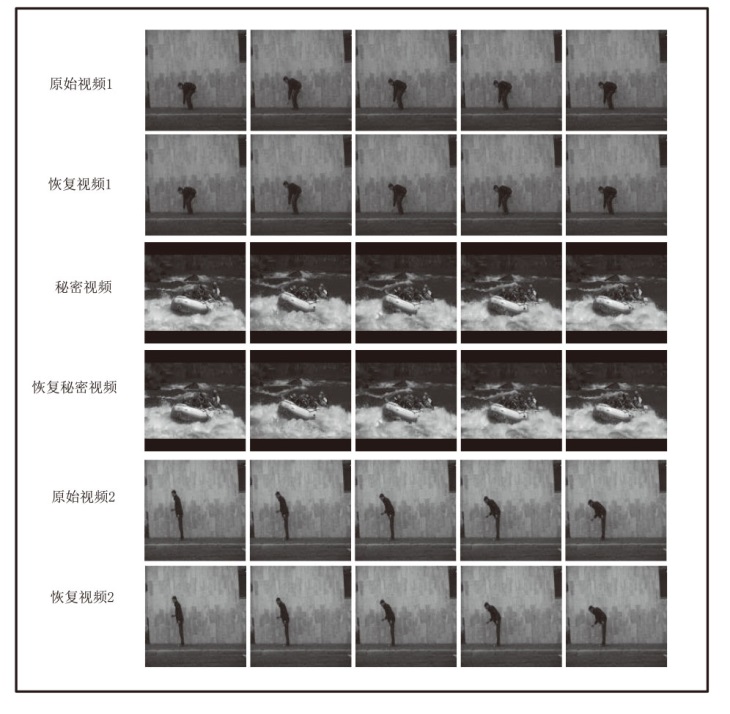
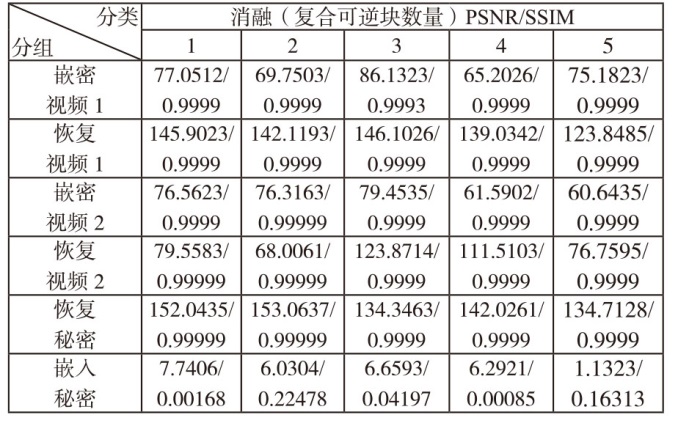
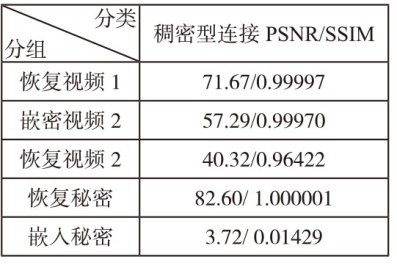
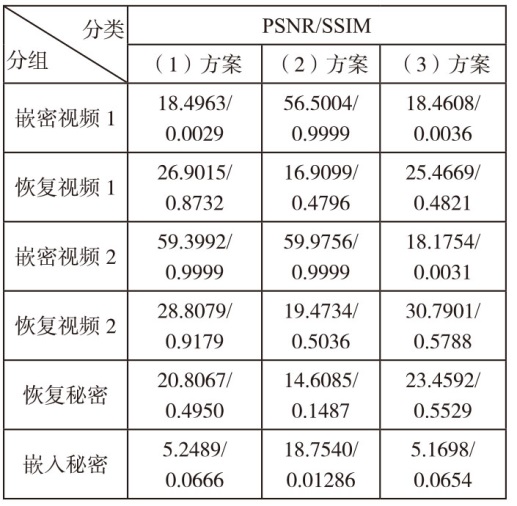
文章设计了一种可逆神经网络视频隐写模型。该模型通过优化设计的非局部机制函数,替代当前可逆神经网络中普遍应用的稠密型连接函数,有效解决了视频载体中提取出的秘密信息质量不高的问题;通过设计叠加态的加密和解密结构,提升了模型的安全性;通过优化可逆神经网络块的数量,提高了网络效率。实验结果表明,在利用可逆神经网络进行视频隐写时,与稠密型网络结构相比,采用非局部机制的可逆神经网络能够恢复更高质量的秘密信息,且嵌入秘密后视频的失真更少。同时,使用叠加态的加解密结构,在应用层面显著提升了可逆神经网络视频隐写的安全性。
中图分类号:
引用本文
钮可, 胡方锰, 李军. 基于非局部机制的可逆神经网络视频隐写研究[J]. 信息网络安全, 2026, 26(1): 139-149.
NIU Ke, HU Fangmeng, LI Jun. Research on Reversible Neural Network Video Steganography Based on Nonlocal Mechanism[J]. Netinfo Security, 2026, 26(1): 139-149.
表3
和其他隐写方法的对比
| 方法 | 参数/M | Cover PSNR | SSIM | Secret PSNR | SSIM |
|---|---|---|---|---|---|
| 本文 | 0.235 | 73.02 /139.69 | 0.9999 | 142.02 | 0.9999 |
| DRANet | 16.54 | 31.11 | 0.9726 | 28.45 | 0.9293 |
| LF-VSN | 7.40 | 45.17 | 0.9800 | 48.39 | 0.9960 |
| HCCVS | 0.0387 | 26.77 | 0.9034 | 27.42 | 0.9005 |
| VStegNET | 0.0341 | 27.70 | 0.9441 | 23.16 | 0.8716 |
| BEGAN | — | 40.47 | 0.9794 | 40.66 | 0.9842 |
| Liu et al | — | 67.30 | 0.9999 | 69.21 | 0.9999 |
表3
表4
噪声干扰实验
| 分类 | 小幅度干扰(PSNR/SSIM) | 大幅度干扰(PSNR/SSIM) | |||||||
|---|---|---|---|---|---|---|---|---|---|
| 0~128 | 0~255 | ||||||||
| 分组 | (1) | (2) | (3) | (1) | (2) | (3) | (1) | (2) | (3) |
| 嵌密 视频1 | 56.5935/ 0.9999 | 56.6112/ 0.9999 | 56.5702/ 0.9999 | 5.8293/ 0.0011 | 5.8418/ 0.0010 | 56.5400/ 0.9999 | 5.9454/ 0.0005 | 5.8704/ 0.0005 | 56.6211/ 0.9999 |
| 恢复 视频1 | 133.9142/ 0.9999 | 133.9283/ 0.9999 | 133.9003/ 0.9999 | 24.4425/ 0.6423 | 24.5261/ 0.5180 | 14.4128/ 0.6399 | 20.7117/ 0.6271 | 25.5806/ 0.5502 | 11.5989/ : 0.5572 |
| 嵌密 视频2 | 59.5129/ 0.9999 | 59.7357/ 0.9999 | 59.6422/ 0.9999 | 59.4828/ 0.9999 | 5.8520/ 0.0010 | 59.9031/ 0.9999 | 59.5011/ 0.9999 | 5.8619/ 0.0005 | 59.6208/ 0.9999 |
| 恢复 视频2 | 110.1303/ 0.9999 | 109.9959/ 0.9999 | 109.9754/ 0.9999 | 31.5141/ 0.7704 | 34.3927/ 0.7793 | 15.9045/ 0.2545 | 26.4681/ 0.7535 | 37.2740/ 0.8634 | 12.3413/ 0.2274 |
| 恢复 秘密 | 138.3023/ 0.9999 | 138.3258/ 0.9999 | 138.3489/ 0.9999 | 18.1464/ 0.4056 | 5.2470/ 0.0665 | 5.1961/ 0.1620 | 16.9346/ 0.2823 | 14.6085/ 0.1487 | 21.8954/ 0.9373 |
| 嵌入 秘密 | 5.2372/ 0.06651 | 5.2269/ 0.06635 | 5.2133/ 0.0661 | 5.2357/ 0.0666 | 17.9618/ 0.3232 | 21.9229/ 0.9363 | 5.2681/ 0.0669 | 5.2508/ 0.06715 | 5.2018/ 0.1634 |
表4
| [1] | BALUJA S. Hiding Images in Plain Sight: Deep Steganography[EB/OL]. (2017-12-04)[2025-07-06]. https://www.semanticscholar.org/paper/Hiding-Images-in-Plain-Sight%3A-Deep-Steganography-Baluja/d511567a87218a555a4cc662c42ee89f044a5852. |
| [2] | HAYES J, DANEZIS G. Generating Steganographic Images via Adversarial Training[EB/OL]. (2017-03-01)[2025-07-06]. https://www.semanticscholar.org/paper/Generating-steganographic-images-via-adversarial-Hayes-Danezis/2da1a80955df1612766ffdf63916a6a374780161. |
| [3] |
KUNHOTH J, SUBRAMANIAN N, AL-MAADEED S, et al. Video Steganography: Recent Advances and Challenges[J]. Multimedia Tools and Applications, 2023, 82(27): 41943-41985.
doi: 10.1007/s11042-023-14844-w |
| [4] |
CHAN C K, CHENG L M. Hiding Data in Images by Simple LSB Substitution[J]. Pattern Recognition, 2004, 37(3): 469-474.
doi: 10.1016/j.patcog.2003.08.007 URL |
| [5] |
WANG C M, WU N I, TSAI C S. A High Quality Steganographic Method with Pixel-Value Differencing and Modulus Function[J]. Journal of Systems and Software, 2008, 81(1): 150-158.
doi: 10.1016/j.jss.2007.01.049 URL |
| [6] |
LAM E Y, GOODMAN J W. A Mathematical Analysis of the DCT Coefficient Distributions for Images[J]. IEEE Transactions on Image Processing, 2000, 9(10): 1661-1666.
doi: 10.1109/83.869177 pmid: 18262905 |
| [7] |
MSTAFA R J, ELLEITHY K M. Compressed and Raw Video Steganography Techniques: A Comprehensive Survey and Analysis[J]. Multimedia Tools and Applications, 2017, 76(20): 21749-21786.
doi: 10.1007/s11042-016-4055-1 URL |
| [8] | VOULODIMOS A, DOULAMIS N, DOULAMIS A, et al. Deep Learning for Computer Vision: A Brief Review[J]. Computational Intelligence and Neuroscience, 2018, 18(1): 41-49. |
| [9] |
OTTER D W, MEDINA J R, KALITA J K. A Survey of the Usages of Deep Learning for Natural Language Processing[J]. IEEE Transactions on Neural Networks and Learning Systems, 2021, 32(2): 604-624.
doi: 10.1109/TNNLS.5962385 URL |
| [10] | ZHANG Zixing, GEIGER J, POHJALAINEN J, et al. Deep Learning for Environmentally Robust Speech Recognition: An Overview of Recent Developments[J]. ACM Transactions on Intelligent Systems & Technology, 2018, 9(5): 1-28. |
| [11] | YANG Ziyun, WANG Zichi, ZHANG Xinpeng. A General Steganographic Framework for Neural Network Models[J]. Information Sciences, 2023, 643(9): 119-125. |
| [12] |
YANG Zhongliang, GUO Xiaoqin, CHEN Zimin, et al. RNN-Stega: Linguistic Steganography Based on Recurrent Neural Networks[J]. IEEE Transactions on Information Forensics and Security, 2019, 14(5): 1280-1295.
doi: 10.1109/TIFS.2018.2871746 URL |
| [13] | XU Chenyi, HUANG Lin, QIN Chuan, et al. Steganography with Constructing Neural Networks[J]. IEEE Transactions on Circuits and Systems for Video Technology, 2025: 1-11. |
| [14] | WENG Xinyu, LI Yongzhi, CHI Lu. Convolutional Video Steganography with Temporal Residual Modeling[EB/OL]. (2018-02-13)[2025-05-19]. http://arxiv.org/abs/1806.02941. |
| [15] | VStegNET. Video Steganography Networkusing Spatio-Temporal Features and Micro-Bottleneck[EB/OL]. [2025-05-19]. https://paperswithcode.com/paper/vstegnet-video-steganography-networkusing. |
| [16] | JAISWAL A, KUMAR S, NIGAM A. En-VStegNET: Video Steganography Using Spatio-Temporal Feature Enhancement with 3D-CNN and Hourglass[C]// IEEE. 2020 International Joint Conference on Neural Networks (IJCNN). New York: IEEE, 2020: 1-8. |
| [17] | BARMAN A, DUTTA P. Facial Expression Recognition Using Reversible Neural Network[J]. Applied Soft Computing, 2024, 162: 15-26. |
| [18] |
HAN Qinhui, JUNG C. Cross Spectral Disparity Estimation from VIS and NIR Paired Images Using Disentangled Representation and Reversible Neural Networks[J]. IEEE Transactions on Intelligent Transportation Systems, 2023, 24(5): 5326-5336.
doi: 10.1109/TITS.2023.3238800 URL |
| [19] | LIU Ming, YE Guodong, ZHOU Junwei. Asymmetric Image Encryption-Hiding Scheme Based on Reversible Neural Network[J]. Science China(Technological Sciences), 2025, 68(9): 24-31. |
| [20] | MOU Chong, XU Youmin, SONG Jiecong, et al. Large-Capacity and Flexible Video Steganography via Invertible Neural Network[C]// IEEE. The IEEE/CVF Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2023: 22606-22615. |
| [21] | DINH L, KRUEGER D, BENGIO Y. NICE: Non-Linear Independent Components Estimation[EB/OL]. (2015-02-16)[2025-05-19]. http://arxiv.org/abs/1410.8516. |
| [22] | DINH L, SOHL-DICKSTEIN J, BENGIO S. Density Estimation Using Real NVP[EB/OL]. (2017-03-19)[2025-05-19]. http://arxiv.org/abs/1605.08803. |
| [23] | XU Wanni, FU Youlei, ZHU Dongmei. ResNet and Its Application to Medical Image Processing: Research Progress and Challenges[J]. Computer Methods and Programs in Biomedicine, 2023, 240: 60-76. |
| [24] | KOONCE B. Convolutional Neural Networks with Swift for Tensorflow: Image Recognition and Dataset Categorization[M]. Berkeley: Apress, 2021. |
| [25] |
GIRDHAR N, SINHA A, GUPTA S. DenseNet-II: An Improved Deep Convolutional Neural Network for Melanoma Cancer Detection[J]. Soft Computing, 2023, 27(18): 13285-13304.
doi: 10.1007/s00500-022-07406-z |
| [26] |
HOU Yuntao, WU Zequan, CAI Xiaohua, et al. The Application of Improved Densenet Algorithm in Accurate Image Recognition[J]. Scientific Reports, 2024, 14(1): 24-35.
doi: 10.1038/s41598-023-50497-3 |
| [27] | WANG Xiaolong, GIRSHICK R, GUPTA A, et al. Non-Local Neural Networks[C]// IEEE. IEEE Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2018: 7794-7803. |
| [28] | LI Zhiyuan, WU Anhao, TAN Lin, et al. Stream Sequence Feature Fusion and Attention Mechanism Based Method for Encrypted Traffic Classification[J]. Journal of Chinese Computer Systems, 2025, 46(7): 1718-1726. |
| 李志远, 吴安昊, 谭林, 等. 基于流序列特征融合与注意力机制的加密流量分类方法[J]. 小型微型计算机系统, 2025, 46(7): 1718-1726. | |
| [29] | HUANG Gao, LIU Zhuang, VAN D M L, et al. Densely Connected Convolutional Networks[C]// IEEE. IEEE Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2017: 2261-2269. |
| [30] |
GORELICK L, BLANK M, SHECHTMAN E, et al. Actions as Space-Time Shapes[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2007, 29(12): 2247-2253.
pmid: 17934233 |
| [31] | SOOMRO K, ZAMIR A R, SHAH M. UCF101: A Dataset of 101 Human Actions Classes from Videos in the Wild[EB/OL]. (2012-03-04)[2025-05-19]. http://arxiv.org/abs/1212.0402. |
| [32] |
DAMEN D, DOUGHTY H, FARINELLA G M, et al. Rescaling Egocentric Vision: Collection, Pipeline and Challenges for EPIC-KITCHENS-100[J]. International Journal of Computer Vision, 2022, 130(1): 33-55.
doi: 10.1007/s11263-021-01531-2 |
| [1] | 唐洪琼, 钮可, 张英男, 杨晓元. 自适应二维直方图迁移的视频可逆隐写算法[J]. 信息网络安全, 2019, 19(9): 106-110. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||