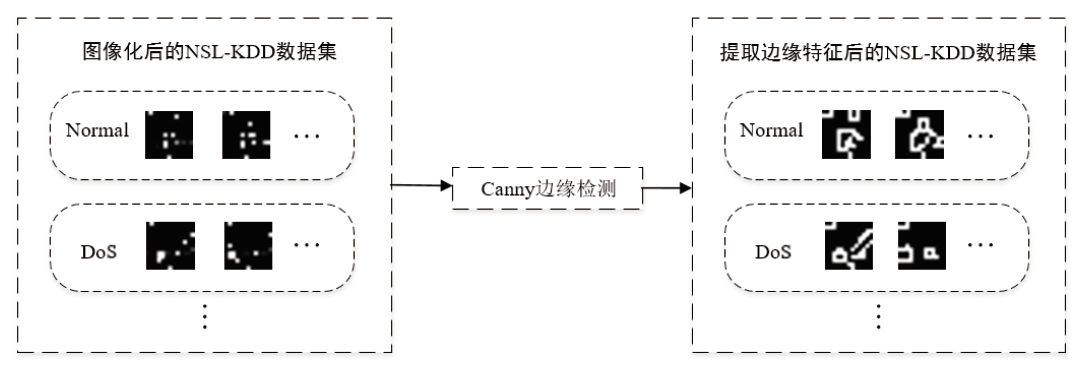
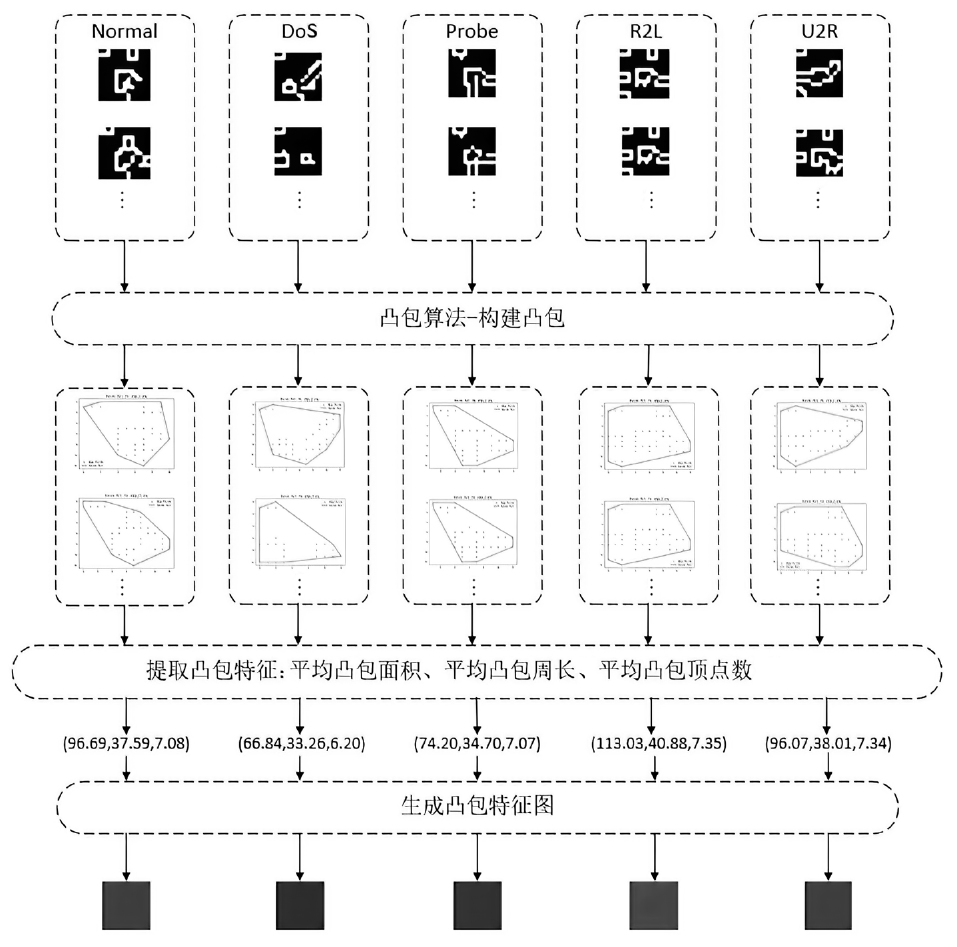
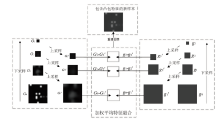
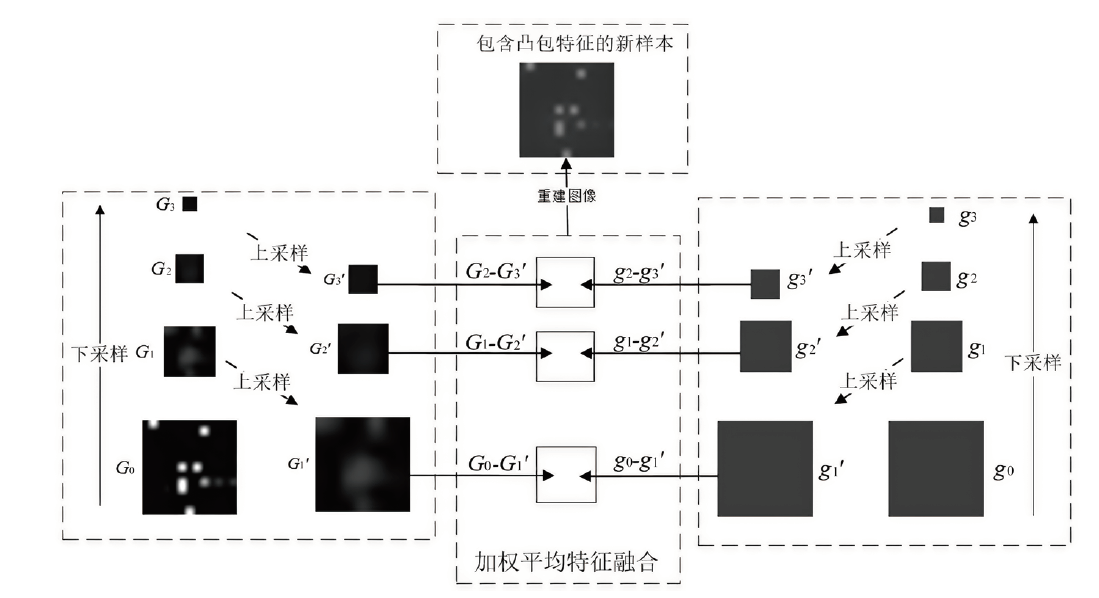
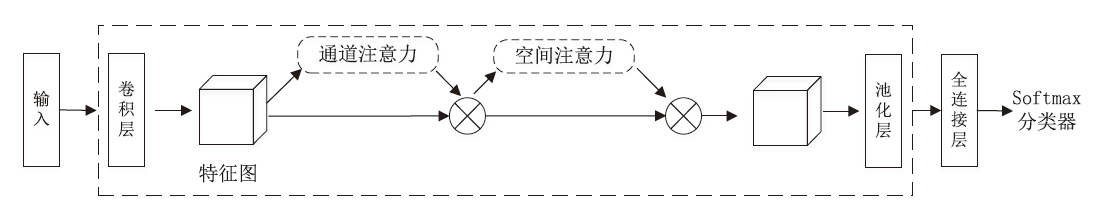
Netinfo Security ›› 2024, Vol. 24 ›› Issue (9): 1422-1431.doi: 10.3969/j.issn.1671-1122.2024.09.010
Previous Articles Next Articles
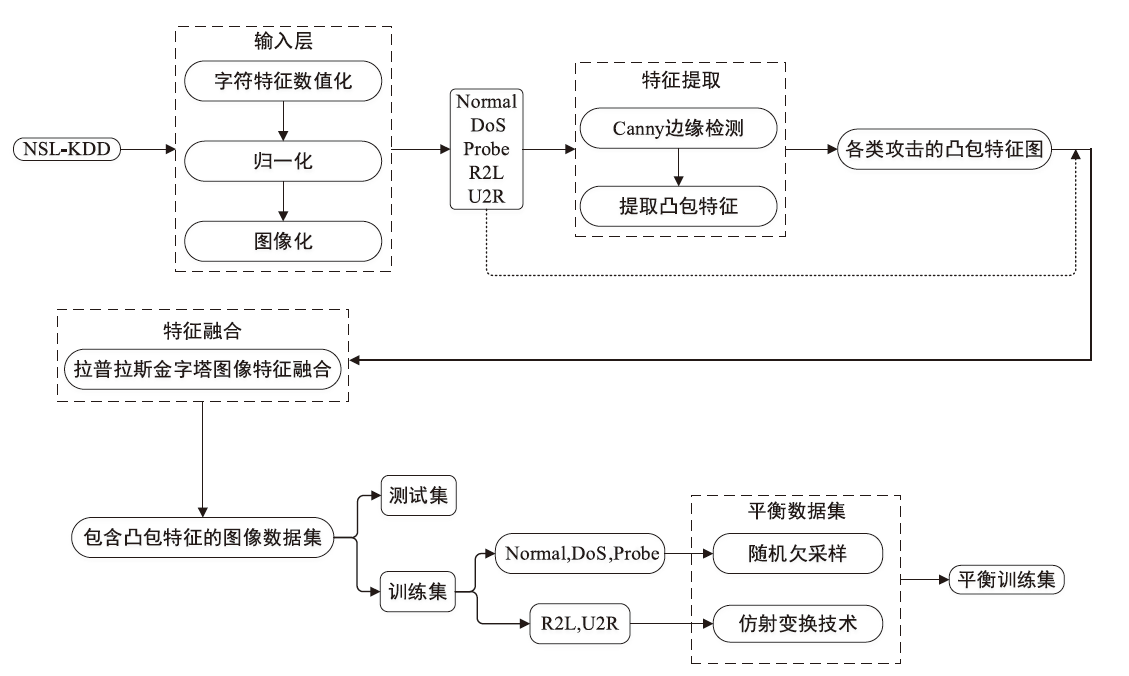
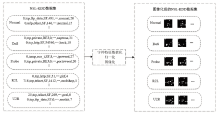
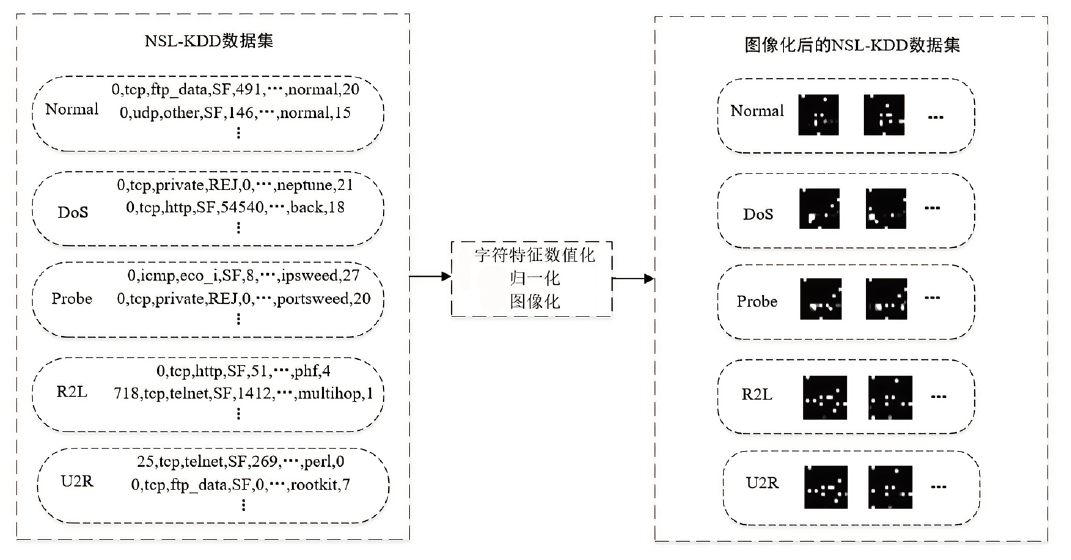
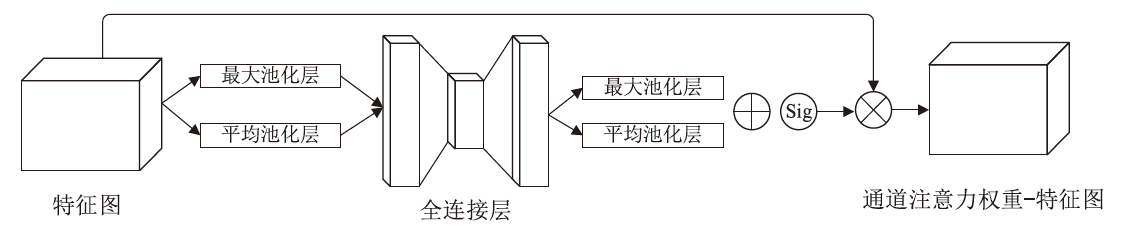
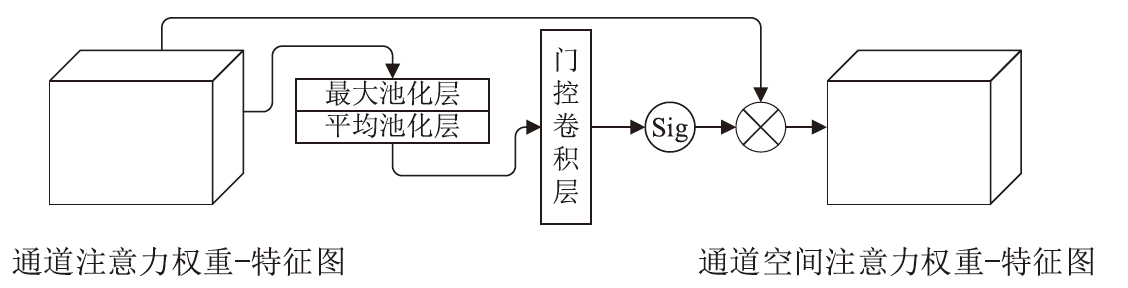
CBAM-CNN Network-Based Intrusion Detection Method Using Image Convex Hull Features
LIU Lianhai, LI Huiye( ), MAO Donghui
), MAO Donghui
- School of Computer Science and Information Security, Guilin University of Electronic Technology, Guilin 541004, China
-
Received:2024-03-09Online:2024-09-10Published:2024-09-27
CLC Number:
Cite this article
LIU Lianhai, LI Huiye, MAO Donghui. CBAM-CNN Network-Based Intrusion Detection Method Using Image Convex Hull Features[J]. Netinfo Security, 2024, 24(9): 1422-1431.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.09.010
| [1] | ALJABRI M, ALJAMEEL S S, MOHAMMAD R M A, et al. Intelligent Techniques for Detecting Network Attacks: Review and Research Directions[EB/OL]. (2021-06-09)[2024-02-25]. https://doi.org/10.3390/s21217070. |
| [2] | AMANOUL S V, ABDULAZEEZ A M. Intrusion Detection System Based on Machine Learning Algorithms: A Review[C]// IEEE.2022 IEEE 18th International Colloquium on Signal Processing & Applications (CSPA). New York: IEEE, 2022: 79-84. |
| [3] | THAKKAR, ANKIT, RITIKA L. Fusion of Statistical Importance for Feature Selection in Deep Neural Network-Based Intrusion Detection System[J]. Network Daily News, 2023: 353-363. |
| [4] | LI Shudong, JIANG Laiyuan, WANG Zhen, et al. A Malicious Mining Code Detection Method Based on Multi-Features Fusion[J]. IEEE Transactions on Network Science and Engineering, 2022: 2731-2739. |
| [5] | ALGHANAM O A, ALMOBAIDEEN W, SAADEH M, et al. An Improved PIO Feature Selection Algorithm for IoT Network Intrusion Detection System Based on Ensemble Learning[EB/OL]. (2023-08-12)[2024-02-25]. https://doi.org/10.1016/j.eswa.2022.118745. |
| [6] | WEN Tingke, XIAO Yuanxing, WANG Anqi, et al. A Novel Hybrid Feature Fusion Model for Detecting Phishing Scam on Ethereum Using Deep Neural Network[J]. Expert Systems with Applications, 2023, 211: 63-74. |
| [7] | AHMAD R S, ALI A H, KAZIM S M, et al. A GAF and CNN Based Wi-Fi Network Intrusion Detection System[C]// IEEE. IEEE INFOCOM 2023-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS). New York: IEEE, 2023: 1-6. |
| [8] | KIM J, KIM J, KIM H, et al. CNN-Based Network Intrusion Detection against Denial-of-Service Attacks[EB/OL]. (2020-06-01)[2024-02-25]. https://doi.org/10.3390/electronics9060916. |
| [9] | SIDDIQI, MURTAZA A, WOOGUIL P. Tier-Based Optimization for Synthesized Network Intrusion Detection System[J]. IEEE Access, 2022: 108530-108544. |
| [10] | LIU Yang, KANG Jian, LI Yiran, et al. A Network Intrusion Detection Method Based on CNN and CBAM[C]// IEEE. 2021-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS). New York: IEEE, 2021: 1-6. |
| [11] | WANG Zhen, FUAD A G. An Attention-Based Convolutional Neural Network for Intrusion Detection Model[J]. IEEE Access, 2023: 43116-43127. |
| [12] | SARHAN M, SIAMAK L, MARIUS P. Towards a Standard Feature Set for Network Intrusion Detection System Datasets[J]. Mobile Networks and Applications, 2022: 1-14. |
| [13] | WU Fangsheng, ZHU Changan, MW B, et al. Research on Image Text Recognition Based on Canny Edge Detection Algorithm and K-Means Algorithm[J]. International Journal of System Assurance Engineering and Management, 2022: 72-80. |
| [14] | LEI Chao, BU Siqi, ZHONG Jun, et al. Distribution Network Reconfiguration: A Disjunctive Convex Hull Approach[J]. IEEE Transactions on Power Systems, 2023: 5926-5929. |
| [15] | LUO Xing, FU Guizhong, YANG Jiangxin, et al. Multi-Modal Image Fusion via Deep Laplacian Pyramid Hybrid Network[J]. IEEE Transactions on Circuits and Systems for Video Technology, 2023: 7354-7369. |
| [16] | GHOSH K, SARKAR A, BANERJEE A, et al. Performance Improvement of Convolutional Neural Network Using Random under Sampling[C]// Springer. Advances in Smart Communication Technology and Information Processing:OPTRONIX 2020. Heidelberg: Springer, 2021: 207-217. |
| [17] | SAYED W S, RADWAN A G, FAHMY H, et al. Trajectory Control and Image Encryption Using Affine Transformation of Lorenz System[J]. Egyptian Informatics Journal, 2021: 155-166. |
| [18] | DHANABAL L, SHANTHARAJAH S P. A Study on NSL-KDD Dataset for Intrusion Detection System Based on Classification Algorithms[J]. International Journal of Advanced Research in Computer and Communication Engineering, 2015, 4(6): 446-452. |
| [19] | MEENA G, CHOUDHARY R R. A Review Paper on IDS Classification Using KDD 99 and NSL KDD Dataset in WEKA[C]// IEEE. 2017 International Conference on Computer, Communications and Electronics (Comptelix). New York: IEEE, 2017: 553-558. |
| [20] | MOHAMMADPOUR L, LING T C, LIEW C S, et al. A Survey of CNN-Based Network Intrusion Detection[EB/OL]. (2022-05-23)[2024-02-27]. https://doi.org/10.3390/app12168162. |
| [21] | PFLUGFELDER D, SCHARR H. Practically Lossless Affine Image Transformation[J]. IEEE Transactions on Image Processing, 2020: 5367-5373. |
| [22] | HU Jianwei, LIU Chenshuo, CUI Yanpeng. An Improved CNN Approach for Network Intrusion Detection System[J]. International Journal of Network Security, 2021: 569-575. |
| [23] | ZHENG Shiji. Network Intrusion Detection Model Based on Convolutional Neural Network[C]// IEEE. 2021 IEEE 5th Advanced Information Technology, Electronic and Automation Control Conference (IAEAC). New York: IEEE, 2021: 634-637. |
| [24] | ZHANG Xiaoqing, YANG Fei, HU Yue, et al. RANet: Network Intrusion Detection with Group-Gating Convolutional Neural Network[EB/OL]. (2022-07-03)[2024-02-27]. https://doi.org/10.1016/j.jnca.2021.103266. |
| [25] | ABDULGANIYU O H, TCHAKOUCHT T A, SAHEED Y K. A Systematic Literature Review for Network Intrusion Detection System (IDS)[J]. International Journal of Information Security, 2023: 1125-1162. |
| [26] | JIANG Kaiyuan, WANG Wenya, WANG Aili, et al. Network Intrusion Detection Combined Hybrid Sampling with Deep Hierarchical Network[J]. IEEE Access, 2020: 32464-32476. |
| [27] | KANAKARAJAN N K, MUNIASAMY K. Improving the Accuracy of Intrusion Detection Using GAR-Forest with Feature Selection[C]// Springer. The 4th International Conference on Frontiers in Intelligent Computing:Theory and Applications (FICTA) 2015. Heidelberg: Springer, 2016: 539-547. |
| [28] | IERACITANO C, ADEEL A, MORABITO F C, et al. A Novel Statistical Analysis and Autoencoder Driven Intelligent Intrusion Detection Approach[J]. Neurocomputing, 2020: 51-62. |
| [29] | WISANWANICHTHAN T, THAMMAWICHAI M. A Double-Layered Hybrid Approach for Network Intrusion Detection System Using Combined Naive Bayes and SVM[J]. IEEE Access, 2021: 138432-138450. |
| [30] | FU Yanfang, DU Yishuai, CAO Zijian, et al. A Deep Learning Model for Network Intrusion Detection with Imbalanced Data[EB/OL]. (2022-06-12)[2024-02-27]. https://doi.org/10.3390/electronics11060898. |
| [1] | XU Kaiwen, ZHOU Yichao, GU Wenquan, CHEN Chen, HU Xiyuan. A Multi-Scale Feature Fusion Deepfake Detection Algorithm Based on Reconstruction Learning [J]. Netinfo Security, 2024, 24(8): 1173-1183. |
| [2] | ZHANG Hao, XIE Dazhi, HU Yunsheng, YE Junwei. A Review of Network Anomaly Detection Based on Semi-Supervised Learning [J]. Netinfo Security, 2024, 24(4): 491-508. |
| [3] | JIANG Rong, LIU Haitian, LIU Cong. Unsupervised Network Intrusion Detection Method Based on Ensemble Learning [J]. Netinfo Security, 2024, 24(3): 411-426. |
| [4] | FENG Guangsheng, JIANG Shunpeng, HU Xianlang, MA Mingyu. New Research Progress on Intrusion Detection Techniques for the Internet of Things [J]. Netinfo Security, 2024, 24(2): 167-178. |
| [5] | JIN Zhigang, DING Yu, WU Xiaodong. Federated Intrusion Detection Algorithm with Bilateral Correction Merging Gradient Difference [J]. Netinfo Security, 2024, 24(2): 293-302. |
| [6] | SUN Hongzhe, WANG Jian, WANG Peng, AN Yulong. Network Intrusion Detection Method Based on Attention-BiTCN [J]. Netinfo Security, 2024, 24(2): 309-318. |
| [7] | SHEN Hua, TIAN Chen, GUO Sensen, MU Zhiying. Research on Adversarial Machine Learning-Based Network Intrusion Detection Method [J]. Netinfo Security, 2023, 23(8): 66-75. |
| [8] | PENG Hanzhong, ZHANG Zhujun, YAN Liyue, HU Chenglin. Research on Intrusion Detection Mechanism Optimization Based on Federated Learning Aggregation Algorithm under Consortium Chain [J]. Netinfo Security, 2023, 23(8): 76-85. |
| [9] | LIU Changjie, SHI Runhua. A Smart Grid Intrusion Detection Model for Secure and Efficient Federated Learning [J]. Netinfo Security, 2023, 23(4): 90-101. |
| [10] | GAO Qingguan, ZHANG Bo, FU Anmin. An Advanced Persistent Threat Detection Method Based on Attack Graph [J]. Netinfo Security, 2023, 23(12): 59-68. |
| [11] | YAO Yuan, FAN Zhaoshan, WANG Qing, TAO Yuan. Malicious Domain Detection Method Based on Multivariate Time-Series Features [J]. Netinfo Security, 2023, 23(11): 1-8. |
| [12] | LI Sicong, WANG Jian, SONG Yafei, HUANG Wei. Malicious Code Classification Method Based on BiTCN-DLP [J]. Netinfo Security, 2023, 23(11): 104-117. |
| [13] | JIN Zhigang, LIU Kai, WU Xiaodong. A Review of IDS Research in Smart Grid AMI Field [J]. Netinfo Security, 2023, 23(1): 1-8. |
| [14] | WANG Huazhong, TIAN Zilei. Intrusion Detection Method of ICS Based on Improved CGAN Algorithm [J]. Netinfo Security, 2023, 23(1): 36-43. |
| [15] | LIU Xiangyu, LU Tianliang, DU Yanhui, WANG Jingxiang. Lightweight IoT Intrusion Detection Method Based on Feature Selection [J]. Netinfo Security, 2023, 23(1): 66-72. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||