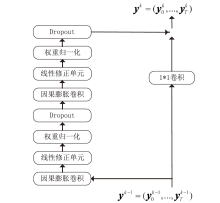
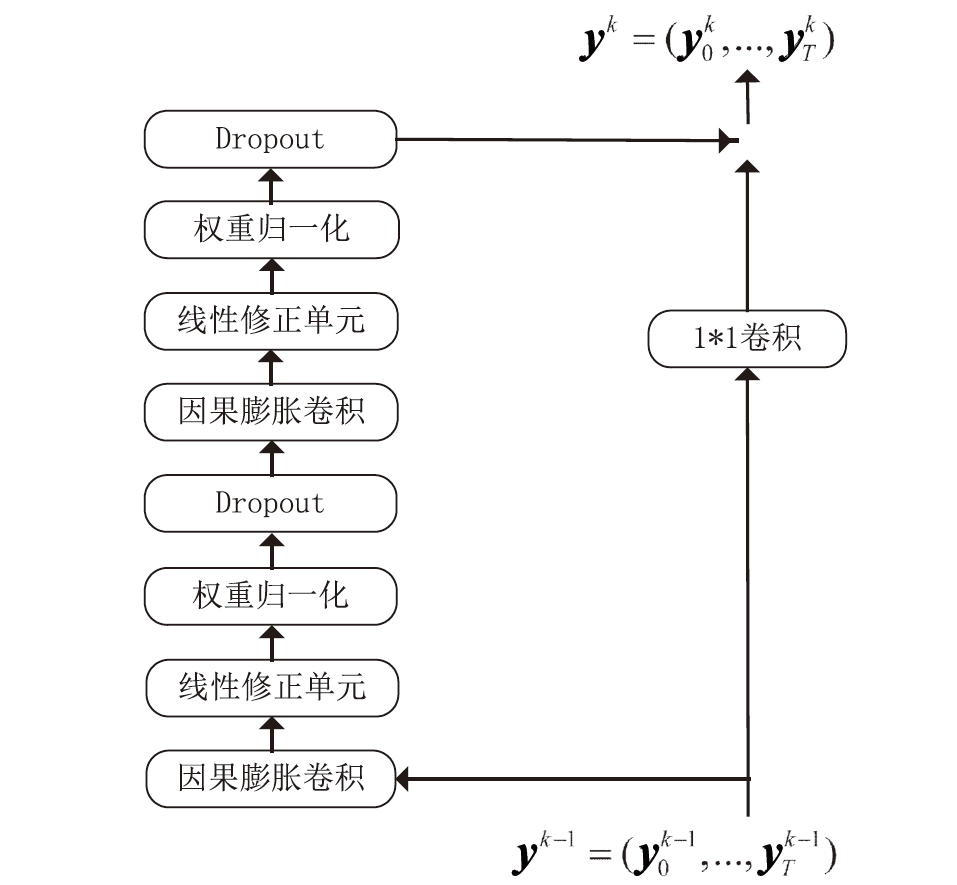
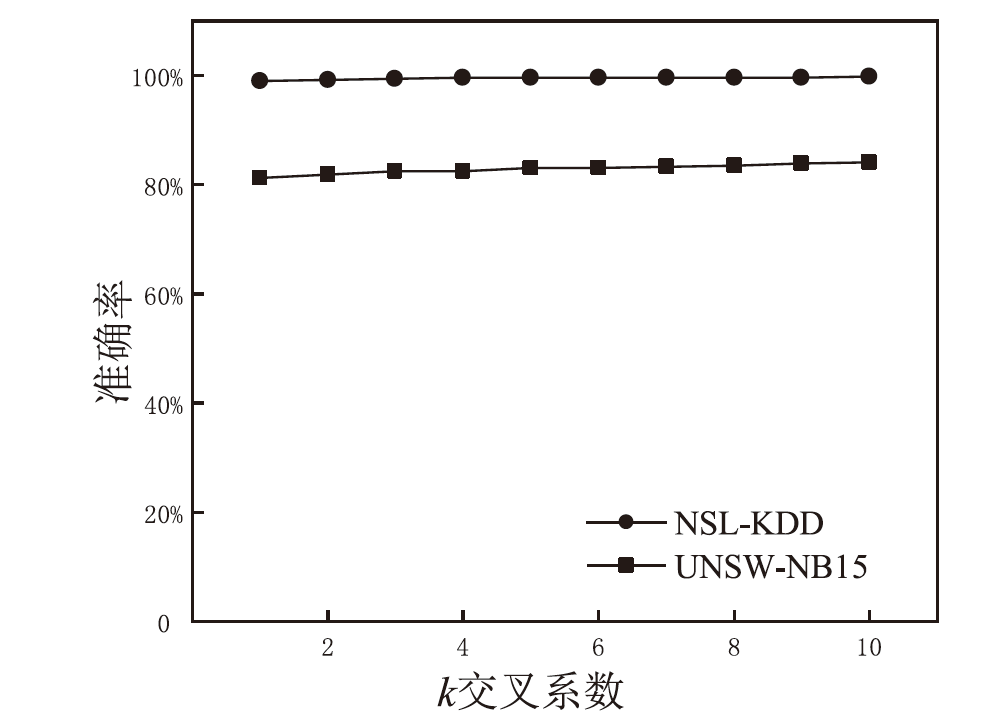
Netinfo Security ›› 2024, Vol. 24 ›› Issue (2): 309-318.doi: 10.3969/j.issn.1671-1122.2024.02.014
Previous Articles Next Articles
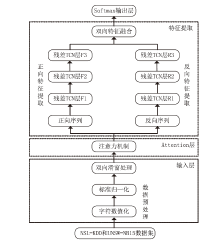
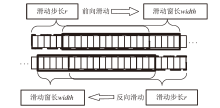
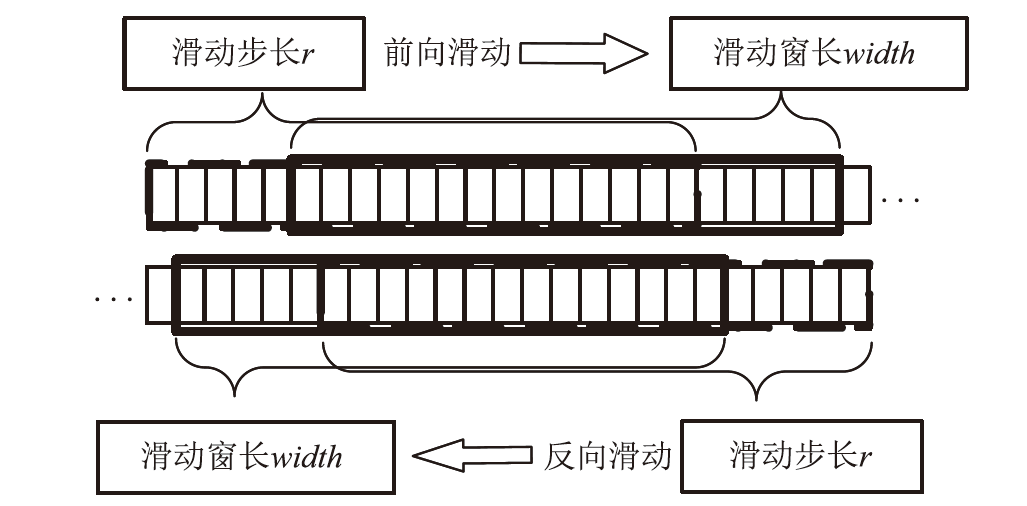
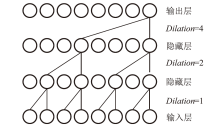
Network Intrusion Detection Method Based on Attention-BiTCN
SUN Hongzhe1,2( ), WANG Jian1, WANG Peng1, AN Yulong2
), WANG Jian1, WANG Peng1, AN Yulong2
- 1. School of Air and Missile Defense, Air Force Engineering University, Xi’an 710051, China
2. Key Laboratory for Fault Diagnosis and Maintenance of Spacecraft in-Orbit, Xi’an 710043, China
-
Received:2023-10-04Online:2024-02-10Published:2024-03-06 -
Contact:SUN Hongzhe E-mail:byxarrk@163.com
CLC Number:
Cite this article
SUN Hongzhe, WANG Jian, WANG Peng, AN Yulong. Network Intrusion Detection Method Based on Attention-BiTCN[J]. Netinfo Security, 2024, 24(2): 309-318.
share this article
| [1] | SHARMA S, GUPTA R K. Intrusion Detection System: A Review[J]. International Journal of Software and Its Applications, 2015, 9(5): 69-76. |
| [2] | JIAN Shijie, LU Zhigang, DU Dan, et al. Overview of Network Intrusion Detection Technology[J]. Journal of Cyber Security, 2020, 5(4): 96-122. |
| 蹇诗婕, 卢志刚, 杜丹, 等. 网络入侵检测技术综述[J]. 信息安全学报, 2020, 5(4): 96-122. | |
| [3] |
SHENG Long, YUAN Lina, WU Nannan, et al. Network Anomaly Detection Model Based on GSA and DE Optimizing Hybrid Kernel ELM[J]. Computer Engineering, 2022, 48(6): 146-153.
doi: 10.19678/j.issn.1000-3428.0061509 |
|
生龙, 袁丽娜, 武南南, 等. 基于GSA与DE优化混合核ELM的网络异常检测模型[J]. 计算机工程, 2022, 48(6): 146-153.
doi: 10.19678/j.issn.1000-3428.0061509 |
|
| [4] |
SULTANA N, CHILAMKURTI N, PENG W, et al. Survey on SDN Based Network Intrusion Detection System Using Machine Learning Approaches[J]. Peer-to-Peer Networking and Applications, 2019, 12(2): 493-501.
doi: 10.1007/s12083-017-0630-0 |
| [5] |
MISHRA P, VARADHARAJAN V, TUPAKULA U, et al. A Detailed Investigation and Analysis of Using Machine Learning Techniques for Intrusion Detection[J]. IEEE Communications Surveys and Tutorials, 2019, 21(1): 686-728.
doi: 10.1109/COMST.2018.2847722 URL |
| [6] | ARHAN B I, JASIM A D. A Survey of Intrusion Detection Using Deep Learning in INTERNET of Things[J]. Iraqi Journal for Computer Science and Mathematics, 2022(31): 83-93. |
| [7] |
ZHANG Hao, ZHANG Xiaoyu, ZHANG Zhenyou, et al. Summary of Intrusion Detection Models Based on Deep Learning[J]. Computer Engineering and Applications, 2022, 58(6): 17-28.
doi: 10.3778/j.issn.1002-8331.2107-0084 |
|
张昊, 张小雨, 张振友, 等. 基于深度学习的入侵检测模型综述[J]. 计算机工程与应用, 2022, 58(6): 17-28.
doi: 10.3778/j.issn.1002-8331.2107-0084 |
|
| [8] |
LE T T H, KIM Y, KIM H. Network Intrusion Detection Based on Novel Feature Selection Model and Various Recurrent Neural Networks[J]. Applied Sciences, 2019, 9(7): 1-29.
doi: 10.3390/app9010001 URL |
| [9] | LI Xiangang, WU Xihong. Constructing Long Short-Term Memory Based Deep Recurrent Neural Networks for Large Vocabulary Speech Recognition[C]// IEEE. 2015 IEEE International Conference on Acoustics, Speech and Signal Processing(ICASSP). New York:IEEE, 2015: 4520-4524. |
| [10] | SINGH N B, SINGH M M, SARKAR A, et al. A Novel Wide & Deep Transfer Learning Stacked GRU Framework for Network Intrusion Detection[EB/OL]. (2021-09-10)[2023-09-26]. https://www.researchgate.net/publication/353138019_A_novel_wide_deep_transfer_learning_stacked_GRU_framework_for_network_intrusion_detection. |
| [11] | ZHANG Anlin, ZHANG Qikun, HUANG Daoying, et al. Intrusion Detection Model Based on CNN and BiGRU Fused Neural Network[J]. Journal of Zhengzhou University (Engineering Science), 2022, 43(3): 37-43. |
| 张安琳, 张启坤, 黄道颖, 等. 基于CNN与BiGRU融合神经网络的入侵检测模型[J]. 郑州大学学报(工学版), 2022, 43(3): 37-43. | |
| [12] | LIU Zhihui. Research on Network Intrusion Detection of Advanced Metering Infrastructure Based on Parallel CNN-GRU[D]. Dalian: Dalian University of Technology, 2022. |
| 刘智慧. 基于并行CNN-GRU的高级量测体系网络入侵检测研究[D]. 大连: 大连理工大学, 2022. | |
| [13] | IMRANA Y, XIANG Yanping, ALI L, et al. A Bidirectional LSTM Deep Learning Approach for Intrusion Detection[EB/OL]. (2021-12-05)[2023-09-26]. https://doi.org/10.1016/j.eswa.2021.115524. |
| [14] | YANG Shuaichuang, TAN Minsheng, XIA Shiying, et al. A Method of Intrusion Detection Based on Attention-LSTM Neural Network[C]// ACM. The 2020 5th International Conference on Machine Learning Technologies. New York: ACM, 2020: 46-50. |
| [15] | TAO Zhiyong, YAN Minghao, LIU Ying. Channel Coding Closed Set Recognition Based on Temporal Convolutional Networks[J]. Journal of Huazhong University of Science and Technology (Natural Science Edition), 2022, 50(3): 12-17. |
| 陶志勇, 闫明豪, 刘影. 基于时序卷积网络的信道编码闭集识别[J]. 华中科技大学学报(自然科学版), 2022, 50(3): 12-17. | |
| [16] | SARIKA C K, NISHTHA K. Analysis of KDD-Cup’99, NSL-KDD and UNSW-NB15 Datasets Using Deep Learning in IoT[J]. Procedia Computer Science, 2020(167): 1561-1573. |
| [17] | GEETA K, GULSHAN K. Analysis of Machine Learning Algorithms with Feature Selection for Intrusion Detection Using UNSW-NB15 Dataset[J]. International Journal of Network Security & Its Applications, 2021, 13(1): 21-31. |
| [18] | ACHARYA T, KHATRI I, ANNAMALAI A, et al. Efficacy of Machine Learning-Based Classifiers for Binary and Multi-Class Network Intrusion Detection[C]// IEEE. 2021 IEEE International Conference on Automatic Control & Intelligent Systems. New York: IEEE, 2021: 402-407. |
| [19] | WANG Xiaodan, WANG Peng, SONG Yafei, et al. HRRP Recognition of Midcourse Ballistic Targets Based on AF-BiTCN[EB/OL]. (2023-03-07)[2023-05-10]. https://doi.org/10.13700/j.bh.1001-5965.2023.0025. |
| 王晓丹, 王鹏, 宋亚飞, 等. 基于AF-BiTCN的弹道目标HRRP识别[EB/OL]. (2023-03-07)[2023-05-10]. https://doi.org/10.13700/j.bh.1001-5965.2023.0025. | |
| [20] | ZHU Mingkang. Human Action Recognition Algorithm Based on BiLSTM-Attention Model[J]. Advances in Laser and Optoelectronics, 2019, 56(15): 153-161. |
| 朱铭康. 基于Bi-LSTM-Attention模型的人体行为识别算法[J]. 激光与光电子学进展, 2019, 56(15): 153-161. | |
| [21] | XIE Xiaoyu. Research on Intrusion Detection Model Based on Convolutional Neural Network[D]. Nanjing: Nanjing University of Posts and Telecommunications, 2019. |
| 谢潇雨. 基于卷积神经网络的入侵检测模型研究[D]. 南京: 南京邮电大学, 2019. | |
| [22] | WANG Hui, CAO Zijian, HONG Bo. A Network Intrusion Detection System Based on Convolutional Neural Network[J]. Journal of Intelligent & Fuzzy Systems, 2020, 38(6): 7623-7637. |
| [23] | BAI Shaojie, KOLTER J Z, KOLTUN V. Trellis Networks for Sequence Modeling[EB/OL]. (2018-12-21)[2023-09-26]. https://github.com/locuslab/trellisnet. |
| [24] | ZHOU Haoyi, ZHANG Shanghang, PENG Jieqi, et al. Informer: Beyond Efficient Transformer for Long Sequence Time-Series Forecasting[EB/OL]. (2021-05-28)[2023-09-26]. https://www.xueshufan.com/publication/3111507638. |
| [25] | ZHAO Wentian, GAO Yanyun, JI Tingxiang, et al. Deep Temporal Convolutional Networks for Short-Term Traffic Flow Forecasting[J]. IEEE Access, 2019(7): 114496-114507. |
| [26] | BAI Shaojie, KOLTER J Z, KOLTUN V. An Empirical Evaluation of Generic Convolutional and Recurrent Networks for Sequence Modeling[EB/OL]. (2018-04-19)[2023-09-26]. https://arxiv.org/pdf/1803.01271.pdf. |
| [27] | SALIMANS T, KINGMA D P. Weight Normalization: A Simple Reparameterization to Accelerate Training of Deep Neural Networks[J]. Advances in Neural Information Processing Systems, 2016(29): 901-909. |
| [28] | SRIVASTAVA N, HINTON G E, KRIZHEVSKY A, et al. Dropout: A Simple Way to Prevent Neural Networks from Overfitting[J]. Journal of Machine Learning Research, 2014, 15(1): 1929-1958. |
| [29] | RAI K, DEVI M S, GULERIA A. Decision Tree Based Algorithm for Intrusion Detection[J]. International Journal of Advanced Networking and Applications, 2016, 7(4): 2828-2834. |
| [30] | XIA Jingming, LI Chong, TAN Ling, et al. Improved Intrusion Detection Method of Random Forest Classifier Network[J]. Computer Engineering and Design, 2019, 40(8): 2146-2150. |
| 夏景明, 李冲, 谈玲, 等. 改进的随机森林分类器网络入侵检测方法[J]. 计算机工程与设计, 2019, 40(8): 2146-2150. | |
| [31] | LI Jun, XIA Songzhu, LAN Haiyan, et al. Network Intrusion Detection Method Based on GRU-RNN[J]. Journal of Harbin Engineering University, 2021, 42(6): 879-884. |
| 李俊, 夏松竹, 兰海燕, 等. 基于GRU-RNN的网络入侵检测方法[J]. 哈尔滨工程大学学报, 2021, 42(6): 879-884. | |
| [32] | SHEN Jiquan, WEI Kun. CR-BiGRU Intrusion Detection Model Based on Residual Network[J]. Journal of Jilin University(Science Edition), 2023, 61(2): 353-361. |
| 沈记全, 魏坤. 融合残差网络的CR-BiGRU入侵检测模型[J]. 吉林大学学报(理学版), 2023, 61(2): 353-361. |
| [1] | FENG Guangsheng, JIANG Shunpeng, HU Xianlang, MA Mingyu. New Research Progress on Intrusion Detection Techniques for the Internet of Things [J]. Netinfo Security, 2024, 24(2): 167-178. |
| [2] | JIN Zhigang, DING Yu, WU Xiaodong. Federated Intrusion Detection Algorithm with Bilateral Correction Merging Gradient Difference [J]. Netinfo Security, 2024, 24(2): 293-302. |
| [3] | SHEN Hua, TIAN Chen, GUO Sensen, MU Zhiying. Research on Adversarial Machine Learning-Based Network Intrusion Detection Method [J]. Netinfo Security, 2023, 23(8): 66-75. |
| [4] | PENG Hanzhong, ZHANG Zhujun, YAN Liyue, HU Chenglin. Research on Intrusion Detection Mechanism Optimization Based on Federated Learning Aggregation Algorithm under Consortium Chain [J]. Netinfo Security, 2023, 23(8): 76-85. |
| [5] | LIU Gang, YANG Wenli, WANG Tongli, LI Yang. Differential Privacy-Preserving Dynamic Recommendation Model Based on Cloud Federation [J]. Netinfo Security, 2023, 23(7): 31-43. |
| [6] | JIANG Yingzhao, CHEN Lei, YAN Qiao. Distributed Denial of Service Attack Detection Algorithm Based on Two-Channel Feature Fusion [J]. Netinfo Security, 2023, 23(7): 86-97. |
| [7] | LIU Changjie, SHI Runhua. A Smart Grid Intrusion Detection Model for Secure and Efficient Federated Learning [J]. Netinfo Security, 2023, 23(4): 90-101. |
| [8] | GAO Qingguan, ZHANG Bo, FU Anmin. An Advanced Persistent Threat Detection Method Based on Attack Graph [J]. Netinfo Security, 2023, 23(12): 59-68. |
| [9] | LI Sicong, WANG Jian, SONG Yafei, HUANG Wei. Malicious Code Classification Method Based on BiTCN-DLP [J]. Netinfo Security, 2023, 23(11): 104-117. |
| [10] | JIN Zhigang, LIU Kai, WU Xiaodong. A Review of IDS Research in Smart Grid AMI Field [J]. Netinfo Security, 2023, 23(1): 1-8. |
| [11] | WANG Huazhong, TIAN Zilei. Intrusion Detection Method of ICS Based on Improved CGAN Algorithm [J]. Netinfo Security, 2023, 23(1): 36-43. |
| [12] | LIU Xiangyu, LU Tianliang, DU Yanhui, WANG Jingxiang. Lightweight IoT Intrusion Detection Method Based on Feature Selection [J]. Netinfo Security, 2023, 23(1): 66-72. |
| [13] | LI Jiyu, FU Zhangjie, ZHANG Yubin. An Image Information Hiding Algorithm Based on Cross-Domain Adversarial Adaptation [J]. Netinfo Security, 2023, 23(1): 93-102. |
| [14] | ZHANG Guanghua, LIU Yongsheng, WANG He, YU Naiwen. Smart Contract Vulnerability Detection Scheme Based on BiLSTM and Attention Mechanism [J]. Netinfo Security, 2022, 22(9): 46-54. |
| [15] | ZHANG Xinglan, FU Juanjuan. Auxiliary Entropy Reduction Based Intrusion Detection Model for Ordinary Differential Equations [J]. Netinfo Security, 2022, 22(6): 1-8. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||