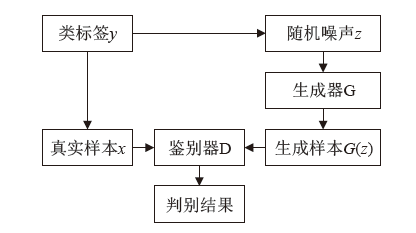
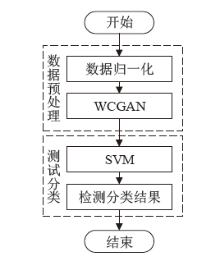
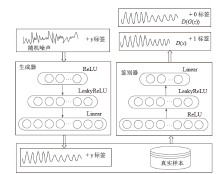
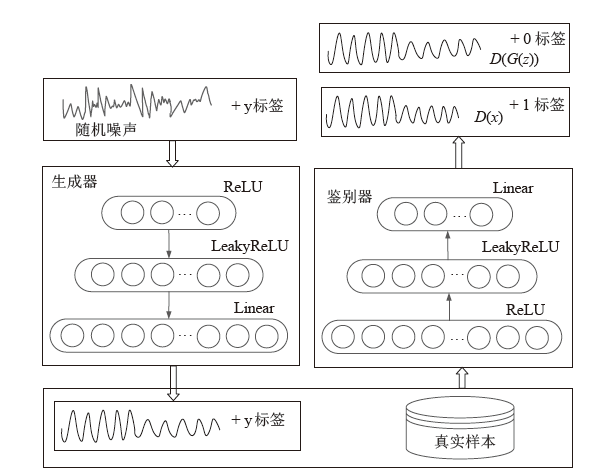
Netinfo Security ›› 2023, Vol. 23 ›› Issue (1): 36-43.doi: 10.3969/j.issn.1671-1122.2023.01.005
Previous Articles Next Articles
Intrusion Detection Method of ICS Based on Improved CGAN Algorithm
- Key Laboratory of Smart Manufacturing in Energy Chemical Processes, Ministry of Education, East China University of Science and Technology, Shanghai 200237, China
-
Received:2022-04-22Online:2023-01-10Published:2023-01-19 -
Contact:WANG Huazhong E-mail:hzwang@ecust.edu.cn
CLC Number:
Cite this article
WANG Huazhong, TIAN Zilei. Intrusion Detection Method of ICS Based on Improved CGAN Algorithm[J]. Netinfo Security, 2023, 23(1): 36-43.
share this article
| 数据集 | 方法 | None | SMOTE | ADASYN | WCGAN |
|---|---|---|---|---|---|
| glass | LR | 0.644 | 0.662 | 0.644 | 0.679 |
| KNN | 0.691 | 0.697 | 0.663 | 0.682 | |
| DT | 0.701 | 0.735 | 0.721 | 0.752 | |
| SVM | 0.698 | 0.781 | 0.762 | 0.788 | |
| carEvaluation | LR | 0.685 | 0.703 | 0.715 | 0.763 |
| KNN | 0.711 | 0.755 | 0.750 | 0.759 | |
| DT | 0.682 | 0.711 | 0.727 | 0.741 | |
| SVM | 0.764 | 0.779 | 0.801 | 0.783 | |
| segment | LR | 0.524 | 0.607 | 0.588 | 0.597 |
| KNN | 0.438 | 0.502 | 0.590 | 0.621 | |
| DT | 0.407 | 0.459 | 0.437 | 0.498 | |
| SVM | 0.600 | 0.645 | 0.619 | 0.717 | |
| ecoli | LR | 0.715 | 0.764 | 0.731 | 0.802 |
| KNN | 0.721 | 0.741 | 0.703 | 0.784 | |
| DT | 0.733 | 0.745 | 0.777 | 0.801 | |
| SVM | 0.784 | 0.797 | 0.791 | 0.812 | |
| hungarian | LR | 0.432 | 0.457 | 0.433 | 0.487 |
| KNN | 0.397 | 0.404 | 0.471 | 0.506 | |
| DT | 0.607 | 0.631 | 0.674 | 0.688 | |
| SVM | 0.579 | 0.654 | 0.669 | 0.696 |
| 数据集 | 方法 | None | SMOTE | ADASYN | WCGAN |
|---|---|---|---|---|---|
| glass | LR | 0.732 | 0.758 | 0.731 | 0.768 |
| KNN | 0.710 | 0.772 | 0.746 | 0.752 | |
| DT | 0.771 | 0.784 | 0.775 | 0.813 | |
| SVM | 0.818 | 0.870 | 0.851 | 0.853 | |
| carEvaluation | LR | 0.779 | 0.818 | 0.819 | 0.854 |
| KNN | 0.873 | 0.886 | 0.881 | 0.889 | |
| DT | 0.792 | 0.821 | 0.835 | 0.847 | |
| SVM | 0.868 | 0.891 | 0.902 | 0.898 | |
| segment | LR | 0.681 | 0.688 | 0.671 | 0.681 |
| KNN | 0.647 | 0.659 | 0.681 | 0.687 | |
| DT | 0.619 | 0.638 | 0.621 | 0.655 | |
| SVM | 0.678 | 0.691 | 0.667 | 0.699 | |
| ecoli | LR | 0.856 | 0.891 | 0.877 | 0.912 |
| KNN | 0.831 | 0.862 | 0.819 | 0.897 | |
| DT | 0.848 | 0.871 | 0.891 | 0.905 | |
| SVM | 0.911 | 0.924 | 0.919 | 0.955 | |
| hungarian | LR | 0.623 | 0.641 | 0.633 | 0.649 |
| KNN | 0.591 | 0.612 | 0.661 | 0.672 | |
| DT | 0.664 | 0.691 | 0.716 | 0.698 | |
| SVM | 0.644 | 0.691 | 0.679 | 0.712 |
| [1] |
THAKKAR A, LOHIYA R. A Survey on Intrusion Detection System: Feature Selection, Model, Performance Measures, Application Perspective, Challenges, and Future Research Directions[J]. Artificial Intelligence Review, 2021, 55(3): 453-563.
doi: 10.1007/s10462-021-10037-9 URL |
| [2] | CASE D U. Analysis of the Cyber Attack on the Ukrainian Power Grid[J]. Electricity Information Sharing and Analysis Center(E-ISAC), 2016, 388: 1-29. |
| [3] | HOBBS A. The Colonial Pipeline Hack: Exposing Vulnerabilities in Us Cybersecurity[M]. London: SAGE Publications, 2021. |
| [4] | ZHANG Wenan, HONG Zhen, ZHU Junwei, et al. A Survey of Network Intrusion Detection Methods for Industrial Control Systems[J]. Control and Decision, 2019, 34(11): 2277-2288. |
| 张文安, 洪榛, 朱俊威, 等. 工业控制系统网络入侵检测方法综述[J]. 控制与决策, 2019, 34(11): 2277-2288. | |
| [5] | INOUE J, YAMAGATA Y, CHEN Yuqi, et al. Anomaly Detection for a Water Treatment System Using Unsupervised Machine Learning[C]// IEEE. 17th IEEE International Conference on Data Mining(ICDMW). New York: IEEE, 2017: 1058-1065. |
| [6] | MOIZUDDIN M D, JOSE M V. A Bio-Inspired Hybrid Deep Learning Model for Network Intrusion Detection[EB/OL]. (2022-02-28)[2022-03-28]. https://doi.org/10.1016/j.knosys.2021.107894. |
| [7] | THASEEN I S, BANU J S, LAVANYA K, et al. An Integrated Intrusion Detection System Using Correlation-Based Attribute Selection and Artificial Neural Network[EB/OL]. (2020-08-08)[2022-01-13]. https://doi.org/10.1002/ett.4014. |
| [8] | LIU Shuo, ZHANG Xinglan. Intrusion Detection Based on Dual Attention[J]. Netinfo Security, 2022, 22(1): 80-86. |
| 刘烁, 张兴兰. 基于双重注意力的入侵检测系统[J]. 信息网络安全, 2022, 22(1):80-86. | |
| [9] | MBOW M, KOIDE H, SAKURAI K. An Intrusion Detection System for Imbalanced Dataset Based on Deep Learning[C]//IEEE. 9th International Symposium on Computing and Networking(CANDAR). New York: IEEE, 2021: 38-47. |
| [10] |
DOUZAS G, BACAO F, LAST F. Improving Imbalanced Learning through a Heuristic Oversampling Method Based on K-Means and SMOTE[J]. Information Sciences, 2018, 465: 1-20.
doi: 10.1016/j.ins.2018.06.056 URL |
| [11] |
ZHOU Xiaokang, HU Yiyong, LIANG Wei, et al. Variational LSTM Enhanced Anomaly Detection for Industrial Big Data[J]. IEEE Transactions on Industrial Informatics, 2021, 17(5): 3469-3477.
doi: 10.1109/TII.2020.3022432 URL |
| [12] |
MOAYEDIKIA A, ONG K L, BOO Y L, et al. Feature Selection for High Dimensional Imbalanced Class Data Using Harmony Search[J]. Engineering Applications of Artificial Intelligence, 2017, 57: 38-49.
doi: 10.1016/j.engappai.2016.10.008 URL |
| [13] | GOODFELLOW I J, POUGET-ABADIE J, MIRZA M, et al. Generative Adversarial Nets[C]// ACM. 27th International Conference on Neural Information Processing Systems. New York: ACM, 2014: 2672-2680. |
| [14] | GAUTHIER J. Conditional Generative Adversarial Nets for Convolutional Face Generation[EB/OL]. [2022-02-20]. http://cs231n.stanford.edu/reports/2015/pdfs/jgauthie_final_report.pdf. |
| [15] | TANG Xianlun, DU Yiming, LIU Yuwei, et al. Image Recognition with Conditional Deep Convolutional Generative Adversarial Networks[J]. Acta Automatica Sinica, 2018, 44(5): 855-864. |
| 唐贤伦, 杜一铭, 刘雨微, 等. 基于条件深度卷积生成对抗网络的图像识别方法[J]. 自动化学报, 2018, 44(5):855-864. | |
| [16] | MIRZA M, OSINDERO S. Conditional Generative Adversarial Nets[EB/OL]. (2014-11-06)[2022-01-29]. https://arxiv.org/abs/1411.1784. |
| [17] | LI Yanxia, CHAI Yi, HU Youqiang, et al. Review of Imbalanced Data Classification Method[J]. Control and Decision, 2019, 34(4): 673-688. |
| 李艳霞, 柴毅, 胡友强, 等. 不平衡数据分类方法综述[J]. 控制与决策, 2019, 34(4):673-688. | |
| [18] | MATHUR A P, TIPPENHAUER N O. SWaT: A Water Treatment Testbed for Research and Training on ICS Security[C]// IEEE. International Workshop on Cyber-Physical Systems for Smart Water Networks(CySWater). New York: IEEE, 2016: 31-36. |
| [1] | JIN Zhigang, LIU Kai, WU Xiaodong. A Review of IDS Research in Smart Grid AMI Field [J]. Netinfo Security, 2023, 23(1): 1-8. |
| [2] | MA Xiangjun, HE Jingsha, WU Tiejun, FAN Dunqiu. An Approach to Identifying Key Hackers in Social Networks [J]. Netinfo Security, 2023, 23(1): 57-65. |
| [3] | LIU Xiangyu, LU Tianliang, DU Yanhui, WANG Jingxiang. Lightweight IoT Intrusion Detection Method Based on Feature Selection [J]. Netinfo Security, 2023, 23(1): 66-72. |
| [4] | ZHANG Xinglan, FU Juanjuan. Auxiliary Entropy Reduction Based Intrusion Detection Model for Ordinary Differential Equations [J]. Netinfo Security, 2022, 22(6): 1-8. |
| [5] | WANG Haoyang, LI Wei, PENG Siwei, QIN Yuanqing. An Intrusion Detection Method of Train Control System Based on Ensemble Learning [J]. Netinfo Security, 2022, 22(5): 46-53. |
| [6] | YIN Ying, ZHOU Zhihong, YAO Lihong. Research on LSTM-Based CAN Intrusion Detection Model [J]. Netinfo Security, 2022, 22(12): 57-66. |
| [7] | LIANG Guangjun, XIN Jianfang, NI Xueli, MA Zhuo. Research on Smart Speaker Security and Forensics [J]. Netinfo Security, 2022, 22(10): 108-113. |
| [8] | GAO Changfeng, XIAO Yanhui, TIAN Huawei. Image Camera Fingerprint Extraction Algorithm Based on MPRNet [J]. Netinfo Security, 2022, 22(10): 15-23. |
| [9] | BAI Hongpeng, DENG Dongxu, XU Guangquan, ZHOU Dexiang. Research on Intrusion Detection Mechanism Based on Federated Learning [J]. Netinfo Security, 2022, 22(1): 46-54. |
| [10] | HE Hongyan, HUANG Guoyan, ZHANG Bing, JIA Damiao. Intrusion Detection Model Based on Extra Trees-recursive Feature Elimination and LightGBM [J]. Netinfo Security, 2022, 22(1): 64-71. |
| [11] | LIU Shuo, ZHANG Xinglan. Intrusion Detection System Based on Dual Attention [J]. Netinfo Security, 2022, 22(1): 80-86. |
| [12] | CHEN Qinggang, DU Yanhui, HAN Yi, LIU Xiangyu. IoT Device Recognition Model Based on Depthwise Separable Convolution [J]. Netinfo Security, 2021, 21(9): 67-73. |
| [13] | LI Qun, DONG Jiahan, GUAN Zhitao, WANG Chao. A Clustering and Classification-based Malicious Attack Detection Method for Internet of Things [J]. Netinfo Security, 2021, 21(8): 82-90. |
| [14] | REN Tao, JIN Ruochen, LUO Yongmei. Network Intrusion Detection Algorithm Integrating Blockchain and Federated Learning [J]. Netinfo Security, 2021, 21(7): 27-34. |
| [15] | HUANG Ziyi, QIN Yuhai. Malicious Mining Web Page Detection and Forensics Based on Multi-feature Recognition [J]. Netinfo Security, 2021, 21(7): 87-94. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||