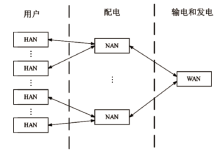
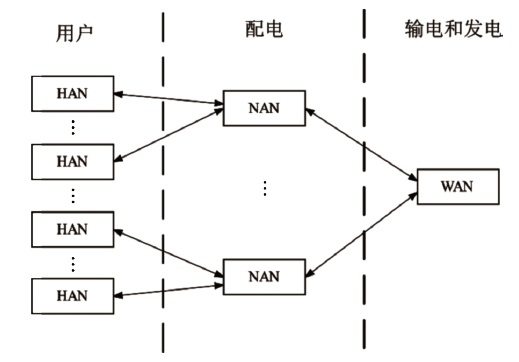
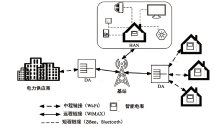
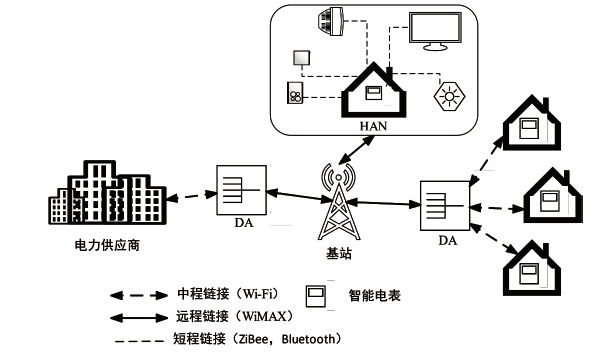
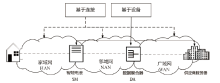
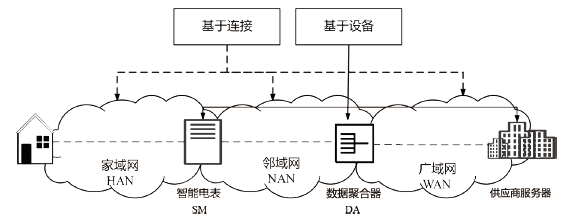
Netinfo Security ›› 2023, Vol. 23 ›› Issue (1): 1-8.doi: 10.3969/j.issn.1671-1122.2023.01.001
Previous Articles Next Articles
A Review of IDS Research in Smart Grid AMI Field
JIN Zhigang( ), LIU Kai, WU Xiaodong
), LIU Kai, WU Xiaodong
- School of Electrical and Information Engineering, Tianjin University, Tianjin 300072, China
-
Received:2022-09-10Online:2023-01-10Published:2023-01-19 -
Contact:JIN Zhigang E-mail:zgjin@tju.edu.cn
CLC Number:
Cite this article
JIN Zhigang, LIU Kai, WU Xiaodong. A Review of IDS Research in Smart Grid AMI Field[J]. Netinfo Security, 2023, 23(1): 1-8.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.01.001
| 面向 层面 | 参考 文献 | 发表 年份 | 使用技术 | 评价 |
|---|---|---|---|---|
| 面向 设备 | 参考 文献[ | 2021 | 一种基于XGBoost的AMI窃电检测方案 | 模型在训练集不平衡时性能表现良好 |
| 参考 文献[ | 2020 | 一种基于异常的IDS,该模型只需要正常的能耗数据检验模型 | 该方法能有效预测异常能源消耗天数 | |
| 参考 文献[ | 2019 | 基于K-means和DNN算法的IDS | 注意到以往研究忽略了环境因素对IDS检测结果的影响,并提出解决办法 | |
| 参考 文献[ | 2019 | 基于长短期记忆网络,提出一种应对概念漂移的异常检测方法 | 注意到消费者消费习惯的变化会造成IDS的假阳性率 | |
| 参考 文献[ | 2021 | SVM 和时间故障传播图 | 提出一个两阶段的网络入侵保护系统 | |
| 参考 文献[ | 2018 | 基于线性规划的异常检测框架 | 有效检测出欺诈性消费者或有缺陷的智能电表 | |
| 面向 连接 | 参考 文献[ | 2021 | 结合特征降维和改进的LSTM的入侵检测系统 | 有效降低由数据不平衡导致的高FAR |
| 参考 文献[ | 2020 | 结合了K-means算法和SVM | 有效降低了模型的检测时间 | |
| 参考 文献[ | 2020 | 提出DBN-OS-RKELM算法,加入核函数与正则化 | 应用OS-ELM对实时入侵数据以块的方式进行在线更新分类以缩短检测时间 | |
| 参考 文献[ | 2021 | 一种特征选择方法,并使用加权粒子群算法来改进 | 实验表明该方法在随机森林和神经网络上训练时间和FAR表现较好 | |
| 参考 文献[ | 2021 | 结合LSTM与极端梯度提升算法 | 实验性能良好,召回率超过95% | |
| 参考 文献[ | 2021 | 基于CNN和LSTM的跨层特征融合的AMI入侵检测模型 | 在KDD99数据集上表现良好 |
| [1] | LIU Jianan, WENG Jian. Survey on Smart Grid Security[J]. Netinfo Security, 2016, 16(5): 78-84. |
| 刘家男, 翁健. 智能电网安全研究综述[J]. 信息网络安全, 2016, 16(5): 78-84. | |
| [2] | CHEN Jiaqi, WANG Qi, TANG Yi, et al. Anomaly Detection Method for Cyber Physical Power System Considering Bilateral Features[J]. Power System Technology, 2022, 46(6): 2339-2348. |
| 陈家琪, 王琦, 汤奕, 等. 考虑双侧特征的电力信息物理系统异常检测方法[J]. 电网技术, 2022, 46(6):2339-2348. | |
| [3] | BASTY F B A, LUO Dehan. Development and Challenges of Cyber-Security for Smart Grids[J]. Electrotechnics Electric, 2019(7): 5-8, 54. |
| 巴斯替, 骆德汉. 智能电网网络安全的发展与挑战[J]. 电工电气, 2019(7):5-8, 54. | |
| [4] |
FAISAL M A, AUNG Z, WILLIAMS J R, et al. Data-Stream-Based Intrusion Detection System for Advanced Metering Infrastructure in Smart Grid: A Feasibility Study[J]. IEEE Systems Journal, 2014, 9(1): 31-44.
doi: 10.1109/JSYST.2013.2294120 URL |
| [5] |
MIRZAEE P H, SHOJAFAR M, CRUICKSHANK H, et al. Smart Grid Security and Privacy: from Conventional to Machine Learning Issues (Threats and Countermeasures)[J]. IEEE Access, 2022, 10: 52922-52954.
doi: 10.1109/ACCESS.2022.3174259 URL |
| [6] |
LEON J P A, RICO-NOVELLA F J, LLOPIS L J D. Predictive Traffic Control and Differentiation on Smart Grid Neighborhood Area Networks[J]. IEEE Access, 2020, 8: 216805-216821.
doi: 10.1109/ACCESS.2020.3041690 URL |
| [7] | GHOSAL A, CONTI M. Key Management Systems for Smart Grid Advanced Metering Infrastructure: A Survey[J]. IEEE Communications Surveys & Tutorials, 2019, 21(3): 2831-2848. |
| [8] | LIN Zhenzhi, CUI Xueyuan, JIN Weichao, et al. Key Technologies of Electricity Theft Detection at Consumer Side[J]. Automation of Electric Power Systems, 2022, 46(5): 188-199. |
| 林振智, 崔雪原, 金伟超, 等. 用户侧窃电检测关键技术[J]. 电力系统自动化, 2022, 46(5):188-199. | |
| [9] | SAXENA N, CHOI B J, GRIJALVA S. Secure and Privacy-Preserving Concentration of Metering Data in AMI Networks[C]// IEEE. 2017 IEEE International Conference on Communications (ICC). Paris:IEEE, 2017: 1-7. |
| [10] | NASEER H, BHUTTA M N M, ALOJAIL M A. A Key Transport Protocol for Advance Metering Infrastructure (AMI) Based on Public Key Cryptography[C]//NCCS. 2020 International Conference on Cyber Warfare and Security (ICCWS). New York:IEEE, 2020: 1-5. |
| [11] |
PASETTI M, FERRARI P, BELLAGENTE P, et al. Artificial Neural Network-Based Stealth Attack on Battery Energy Storage Systems[J]. IEEE Transactions on Smart Grid, 2021, 12(6): 5310-5321.
doi: 10.1109/TSG.2021.3102833 URL |
| [12] |
ANGELOS E W S, SAAVEDRA O R, CORTES O A C, et al. Detection and Identification of Abnormalities in Customer Consumptions in Power Distribution Systems[J]. IEEE Transactions on Power Delivery, 2011, 26(4): 2436-2442.
doi: 10.1109/TPWRD.2011.2161621 URL |
| [13] | YAN Zhongzong, HE Wen. Electricity Theft Detection Base on Extreme Gradient Boosting in AMI[J]. IEEE Transactions on Instrumentation and Measurement, 2021, 70: 1-9. |
| [14] |
JOKAR P, ARIANPOO N, LEUNG V C M. Electricity Theft Detection in AMI Using Customers’ Consumption Patterns[J]. IEEE Transactions on Smart Grid, 2015, 7(1): 216-226.
doi: 10.1109/TSG.2015.2425222 URL |
| [15] | MAAMAR A, BENAHMED K. A Hybrid Model for Anomalies Detection in AMI System Combining K-means Clustering and Deep Neural Network[J]. Computers Materials & Continua(CMC), 2019, 60(1): 15-39. |
| [16] |
PARK C H, KIM T. Energy Theft Detection in Advanced Metering Infrastructure Based on Anomaly Pattern Detection[J]. Energies, 2020, 13(15): 3832-3841.
doi: 10.3390/en13153832 URL |
| [17] |
YIP S C, TAN W N, TAN C K, et al. An Anomaly Detection Framework for Identifying Energy Theft and Defective Meters in Smart Grids[J]. International Journal of Electrical Power & Energy Systems, 2018, 101: 189-203.
doi: 10.1016/j.ijepes.2018.03.025 URL |
| [18] |
FENZA G, GALLO M, LOIA V. Drift-Aware Methodology for Anomaly Detection in Smart Grid[J]. IEEE Access, 2019, 7: 9645-9657.
doi: 10.1109/ACCESS.2019.2891315 |
| [19] |
SUN C C, CARDENAS D J S, HAHN A, et al. Intrusion Detection for Cybersecurity of Smart Meters[J]. IEEE Transactions on Smart Grid, 2020, 12(1): 612-622.
doi: 10.1109/TSG.2020.3010230 URL |
| [20] | LU Guanyu, TIAN Xiuxia. An Efficient Communication Intrusion Detection Scheme in AMI Combining Feature Dimensionality Reduction and Improved LSTM[EB/OL]. (2021-04-01)[2022-08-11]. https://www.researchgate.net/publication/351052596_An_Efficient_Communication_Intrusion_Detection_Scheme_in_AMI_Combining_Feature_Dimensionality_Reduction_ and_Improved_LSTM. |
| [21] |
ROSE T, KIFAYAT K, ABBAS S, et al. A Hybrid Anomaly-Based Intrusion Detection System to Improve Time Complexity in the Internet of Energy Environment[J]. Journal of Parallel and Distributed Computing, 2020, 145: 124-139.
doi: 10.1016/j.jpdc.2020.06.012 URL |
| [22] | LIU Feifei, WU Zhongdong, DING Longbin, et al. Intrusion Detection Algorithm for AMI Based on Improved Online Sequential Extreme Learning Machine[J]. Computer Engineering, 2020, 46(9): 136-142, 148. |
| 刘菲菲, 伍忠东, 丁龙斌, 等. 基于改进在线序列极限学习机的AMI入侵检测算法[J]. 计算机工程, 2020, 46(9):136-142,148. | |
| [23] | KHAN S, KIFAYAT K, KASHIF B A, et al. Intelligent Intrusion Detection System in Smart Grid Using Computational Intelligence and Machine Learning[J]. Transactions on Emerging Telecommunications Technologies, 2021, 32(6): 1-24. |
| [24] | SONG Chunhe, SUN Yingying, HAN Guangjie, et al. Intrusion Detection Based on Hybrid Classifiers for Smart Grid[EB/OL]. (2021-07-01)[2022-08-11]. https://www.researchgate.net/publication/351655230_Intrusion_detection_based_on_hybrid_classifiers_for_smart_grid. |
| [25] |
YAO Ruizhe, WANG Ning, LIU Zhihui, et al. Intrusion Detection System in the Advanced Metering Infrastructure: A Cross-Layer Feature-Fusion CNN-LSTM-Based Approach[J]. Sensors, 2021, 21(2): 626-642.
doi: 10.3390/s21020626 URL |
| [26] |
MASSAFERRO P, MARTINO J M D, FERNANDEZ A. Fraud Detection on Power Grids While Transitioning to Smart Meters by Leveraging Multi-Resolution Consumption Data[J]. IEEE Transactions on Smart Grid, 2022, 13(3): 2381-2389.
doi: 10.1109/TSG.2022.3148817 URL |
| [27] |
ZHOU Tailin, XIAHOU Kaishun, ZHANG Luliang, et al. Real-Time Detection of Cyber-Physical False Data Injection Attacks on Power Systems[J]. IEEE Transactions on Industrial Informatics, 2020, 17(10): 6810-6819.
doi: 10.1109/TII.2020.3048386 URL |
| [1] | FENG Jingyu, SHI Yifei, WANG Teng. Crowd Spectrum Sensing Reinforcement Scheme Against Primary-secondary Collusive Attack in Smart Grid [J]. Netinfo Security, 2022, 23(3): 1-9. |
| [2] | CAI Manchun, WANG Tengfei, YUE Ting, LU Tianliang. ARF-based Tor Website Fingerprint Recognition Technology [J]. Netinfo Security, 2021, 21(4): 39-48. |
| [3] | XIA Zhe, LUO Bin, XU Guibin, XIAO Xinxiu. Privacy-preserving Data Aggregation with Fine Grained Access Control for Smart Grid [J]. Netinfo Security, 2021, 21(11): 28-39. |
| [4] | LI Kunchang, SHI Runhua, LI En. Survey on Data Aggregation and Privacy Protection of User Query in Smart Grid [J]. Netinfo Security, 2021, 21(11): 65-74. |
| [5] | LIU Jianwei, HAN Yiran, LIU Bin, YU Beiyuan. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [6] | GUO Qiquan, ZHANG Haixia. Technology System for Security Protection of Critical Information Infrastructures [J]. Netinfo Security, 2020, 20(11): 1-9. |
| [7] | GU Zhaojun, HAO Jintao, ZHOU Jingxian. Classification of Malicious Network Traffic Based on Improved Bilinear Convolutional Neural Network [J]. Netinfo Security, 2020, 20(10): 67-74. |
| [8] | DONG Wei, LI Yonggang. Research on Analysis of Attacks on Smart Grid Network Based on Complex Network [J]. Netinfo Security, 2020, 20(1): 52-60. |
| [9] | Yuling LIU, Yunshan TANG, Qi ZHANG, Feng LI. Power Dispatch Software Security Situation Assessment Method [J]. Netinfo Security, 2019, 19(8): 15-21. |
| [10] | Liangchen CHEN, Baoxu LIU, Shu GAO. Research on Traffic Data Sampling Technology in Network Attack Detection [J]. Netinfo Security, 2019, 19(8): 22-28. |
| [11] | Quan ZHOU, Shumei XU, Ningbin YANG. A Privacy Protection Scheme for Smart Grid Based on Attribute-based Group Signature [J]. Netinfo Security, 2019, 19(7): 25-30. |
| [12] | Yitao NI, Yongjia CHEN, Bogang LIN. Automatic De-obfuscation-based Malicious Webpages Detection [J]. Netinfo Security, 2019, 19(4): 37-46. |
| [13] | Liangchen CHEN, Shu GAO, Baoxu LIU, Zhigang LU. Research Status and Development Trends on Network Encrypted Traffic Identification [J]. Netinfo Security, 2019, 19(3): 19-25. |
| [14] | Meihong LI, Xiaochen QI, Qianqian WU. Smart Grid Wireless Communication Data Encryption Transmission Scheme Based on Dynamic Key [J]. Netinfo Security, 2019, 19(12): 10-21. |
| [15] | Jian ZHANG, Bohan CHEN, Liangyi GONG, Zhaojun GU. Research on Malware Detection Technology Based on Image Analysis [J]. Netinfo Security, 2019, 19(10): 24-31. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||