Netinfo Security ›› 2019, Vol. 19 ›› Issue (10): 24-31.doi: 10.3969/j.issn.1671-1122.2019.10.004
Previous Articles Next Articles
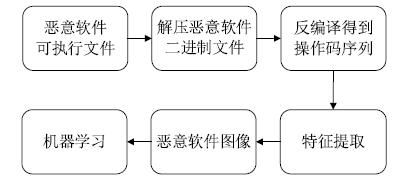
Research on Malware Detection Technology Based on Image Analysis
Jian ZHANG1,2,3( ), Bohan CHEN1, Liangyi GONG1, Zhaojun GU4
), Bohan CHEN1, Liangyi GONG1, Zhaojun GU4
- 1. School of Computer Science and Engineering, Tianjin University of Technology, Tianjin 300384, China
2. College of Cyber Science, Nankai University, Tianjin 300350, China
3. Tianjin Key Laboratory of Network and Data Security Technology, Tianjin 300350, China
4.Information Security Evaluation Center, Civil Aviation University of China, Tianjin 300300, China
-
Received:2019-06-15Online:2019-10-10Published:2020-05-11 -
Contact:Jian ZHANG E-mail:jeffersonzj@qq.com
CLC Number:
Cite this article
Jian ZHANG, Bohan CHEN, Liangyi GONG, Zhaojun GU. Research on Malware Detection Technology Based on Image Analysis[J]. Netinfo Security, 2019, 19(10): 24-31.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2019.10.004
| 文献 | 图像转化源 (均来自恶意软件) | 转换方法 | 图像类型 | 特征选择 | ||
|---|---|---|---|---|---|---|
| 直接 | 操作码 | 灰度 | RGB | |||
| 文献[ | 二进制文件 | √ | √ | 使用GIST纹理特征 | ||
| 文献[ | 二进制文件 | √ | √ | 使用GIST纹理特征 | ||
| 文献[ | 可执行文件 | √ | √ | 基于强度、基于小波和基于Gabor的特征 | ||
| 文献[ | 操作码序列 | √ | √ | 通过动态过分析选出基本块(虑重),从基本块选出主要块 | ||
| 文献[ | 可执行文件 | √ | √ | 使用GLCM纹理特征,纹理分割 | ||
| 文献[ | PE文件 | √ | √ | 为适应各种哈希算法调整图像尺寸 | ||
| 文献[ | PE文件 | √ | √ | 图像特征和其他多个特征进行特征融合 | ||
| 文献[ | DEX文件 | √ | √ | 使用GIST纹理特征 | ||
| 文献[ | 操作码序列 | √ | √ | 使用直方图归一化,扩张和侵蚀处理恶意软件图像 | ||
| 文献[ | AndroidManifest.xml DEX文件 | √ | √ | 将两个文件转化后的图像进行拼接 | ||
| 文献[ | PE文件 | √ | √ | 图像的颜色特征和纹理特征 | ||
| 文献[ | 操作码序列 | √ | √ | 使用多哈希提升图像质量,进行主要块选择 | ||
| 文献[ | classes.dex、函数调用关系 | √ | √ | 对图像进行归一化处理 | ||
| 文献[ | 操作码序列 | √ | √ | 使用PE文件.text段操作码序列转化图像,使用GIST纹理特征 | ||
| 文献 | 时间 | 数据集来源 | 算法 | 精确度/% |
|---|---|---|---|---|
| 文献[ | 2011.7 | Anubis Analysis System | KNN | 99.93 |
| 文献[ | 2011.9 | VX-Heavens | KNN | 97.57 |
| 文献[ | 2013.4 | Offensive Computing Database | SVM | 95.95 |
| 文献[ | 2016.3 | Microsoft Released | XGBoost | 99.76 |
| 文献[ | 2016.6 | Drebin数据集 | RF | >90 |
| 文献[ | 2018.2 | 未说明来源 | RF、KNN、SVM | 97.47、96.23、95.23 |
| 文献[ | 2018.6 | MalGenome | KNN | 94.49 |
| 文献[ | 2019.1 | 安天实验室 | KNN、RF | 94.199、93.511 |
| [1] | 360 Internet Security Center. 2018 China Internet Security Report[EB/OL]. , 2019-5-30. |
| 360互联网安全中心. 2018年中国互联网安全报告[EB/OL]. , 2019-5-30. | |
| [2] | QING Sihan.Research Progress on Android Security[J]. Journal of Software, 2016, 27(1): 45-71. |
| 卿斯汉. Android安全研究进展[J]. 软件学报,2016,27(1):45-71. | |
| [3] | YE Yanfang, LI Tao, ADJEROH D, et al.A Survey on Malware Detection Using Data Mining Techniques[J]. ACM Computing Surveys, 2017, 50(3): 1-40. |
| [4] | WANG Chiheng, CHEN Jing, CHEN Xiangyun, et al.An Android Ransomware Detection Scheme Based on Evidence Chain Generation[J]. Chinese Journal of Computers, 2018, 41(10): 2344-2358. |
| 王持恒,陈晶,陈祥云,等. 基于证据链生成的Android勒索软件检测方法[J]. 计算机学报,2018,41(10):2344-2358. | |
| [5] | UCCI D, ANIELLO L, BALDONI R. Survey of Machine Learning Techniques for Malware Analysis[EB/OL]. , 2019-2-11. |
| [6] | YANG Yimin, CHEN Tieming. Android Malware Family Classification Method Based on the Image of Byte Code Construction of MDS Matrices[EB/OL]. , 2019-2-11. |
| 杨益敏,陈铁明.一种基于字节码图像聚类的Android恶意代码家族分类方法[EB/OL]. ,2019-2-11. | |
| [7] | XIA Xiaoling.Research on Android Malware Detection Method Based on Image and Text Feature with Deep Learning[D]. Harbin: Harbin Institute of Technology, 2018. |
| 夏晓玲. 基于深度学习的恶意代码图像及文本特征分类方法研究[D].哈尔滨:哈尔滨工业大学,2018. | |
| [8] | LI Yuanyuan.Detection of Malware Software Based on Data Visualization[D]. Xi’an: Xidian University, 2018. |
| 李媛媛. 基于数据可视化的恶意代码检测[D].西安:西安电子科技大学,2018. | |
| [9] | NATARAJ L, KARTHIKEYAN S, JACOB G, et al.Malware Images: Visualization and Automatic Classification[C]//ACM. 8th International Symposium on Visualization for Cyber Security, July 20, 2011, Pittsburgh, Pennsylvania, USA. New York: ACM, 2011: 4-11. |
| [10] | FU Jianwen, XUE Jingfeng, WANG Yong, et al. Malware Visualization for Fine-grained Classification[EB/OL]. , 2018-2-12. |
| [11] | ZHANG Jixin, QIN Zheng, YIN Hui, et al.IRMD: Malware Variant Detection Using Opcode Image Recognition[C]//IEEE. 22nd International Conference on Parallel and Distributed Systems, December 13-16, 2016, Wu Han, China. New Jersey: IEEE, 2016: 1175-1180. |
| [12] | HAN K S, KANG B J, IM E G. Malware Analysis Using Visualized Image Matrices[EB/OL]. , 2019-2-12. |
| [13] | NATARAJ L, YEGNESWARAN V, PORRAS P, et al.A Comparative Assessment of Malware Classification Using Binary Texture Analysis and Dynamic Analysis[C]//ACM. 4th ACM Workshop on Security and Artificial Intelligence, October 21, 2011, Chicago, Illinois, USA. New York: ACM, 2011: 21-30. |
| [14] | KANCHERLA K, MUKKAMALA S.Image Visualization Based Malware Detection[C]//IEEE. 2013 IEEE Symposium on Computational Intelligence in Cyber Security, April 16-19, 2013, Singapore. New Jersey: IEEE, 2013: 40-44. |
| [15] | HAN Xiaoguang, QU Wu, YAO Xuanxia, et al.Research on Malicious Code Variants Detection Based on Texture Fingerprint[J]. Journal on Communications, 2014, 35(8): 125-136. |
| 韩晓光,曲武,姚宣霞,等.基于纹理指纹的恶意代码变种检测方法研究[J].通信学报,2014,35(8):125-136. | |
| [16] | AREFKHANI M, SORYANI M.Malware Clustering Using Image Processing Hashes[C]//IEEE. 9th Iranian Conference on Machine Vision and Image Processing, Noveber 18-19, 2015, Tehran, Iran. New Jersey: IEEE, 2015: 214-218. |
| [17] | AHMADI M, ULYANOV D, SEMENOV S, et al.Novel Feature Extraction, Selection and Fusion for Effective Malware Family Classification[C]//ACM. 6th ACM Conference on Data and Application Security and Privacy, March 9-11, 2016, New Orleans, Louisiana, USA. New York: ACM, 2016: 183-194. |
| [18] | NI Sang, QIAN Quan, ZHANG Rui. Malware Identification Using Visualization Images and Deep Learning[EB/OL]. https://www.sciencedirect.com/science/article/pii/S0167404818303481, 2019-2-14. |
| [19] | LIU Yashu, WANG Zhihai, HOU Yueran, et al.Malware Visualization and Automatic Classification with Enhanced Information Density[J]. Journal of Tsinghua University(Science and Technology), 2019, 59(1): 9-14. |
| 刘亚姝,王志海,侯跃然,等.信息密度增强的恶意代码可视化与自动分类方法[J].清华大学学报:自然科学版,2019,59(1):11-16. | |
| [20] | GAO Chengcheng, HUI Xiaowei.GLCM-Based Texture Feature Extraction[J]. Computer Systems Applications, 2010, 19(6): 195-198. |
| 高程程,惠晓威.基于灰度共生矩阵的纹理特征提取[J].计算机系统应用,2010,19(6):195-198. | |
| [21] | ZHANG Chenbin, ZHANG Yunchun, ZHENG Yang, et al.Malware Classification Based on Texture Fingerprint of Gray-scale Images[J]. Computer Science, 2018, 45( Z1): 383-386. |
| 张晨斌,张云春,郑杨,等.基于灰度图纹理指纹的恶意软件分类[J].计算机科学,2018,45(Z1):383-386. | |
| [22] | LIU Li, KUANG Gangyao.Overview of Image Textural Feature Extraction Methods[J]. Journal of Image and Graphics, 2009, 14(4): 622-635. |
| 刘丽,匡纲要.图像纹理特征提取方法综述[J].中国图象图形学报,2009,14(4):622-635. | |
| [23] | RANDEN T, HUSOY J H.Filtering for Texture Classification: a Comparative Study[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 1999, 21(4): 291-310. |
| [24] | OLIVA A, TORRALBA A.Modeling the Shape of the Scene: A Holistic Representation of the Spatial Envelope[J]. International Journal of Computer Vision, 2001, 42(3): 145-175. |
| [25] | TORRALBA A, MURPHY K P, FREEMAN W T, et al.Context-based Vision System for Place and Object Recognition[C]//IEEE. 9th IEEE International Conference on Computer Vision, October 13-16, 2003, Nice, France. New Jersey: IEEE, 2003: 273. |
| [1] | Jianwei LIU, Yiran HAN, Bin LIU, Beiyuan YU. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [2] | Chun GUO, Changqing CHEN, Guowei SHEN, Chaohui JIANG. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [3] | Yifeng DU, Yuanbo GUO. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [4] | SONG Xin, ZHAO Kai, ZHANG Linlin, FANG Wenbo. Research on Android Malware Detection Based on Random Forest [J]. Netinfo Security, 2019, 19(9): 1-5. |
| [5] | MA Zewen, LIU Yang, XU Hongping, YI Hang. DoS Traffic Identification Technology Based on Integrated Learning [J]. Netinfo Security, 2019, 19(9): 115-119. |
| [6] | CHEN Liangchen, LIU Baoxu, GAO Shu. Research on Traffic Data Sampling Technology in Network Attack Detection [J]. Netinfo Security, 2019, 19(8): 22-28. |
| [7] | CHEN Guanheng, SU Jinshu. Abnormal Traffic Detection Algorithm Based on Deep Neural Network [J]. Netinfo Security, 2019, 19(6): 68-75. |
| [8] | TIAN Chunqi, LI Jing, WANG Wei, ZHANG Liqing. A Method for Improving the Performance of Spark on Container Cluster Based on Machine Learning [J]. 信息网络安全, 2019, 19(4): 11-19. |
| [9] | NI Yitao, CHEN Yongjia, LIN Bogang. Automatic De-obfuscation-based Malicious Webpages Detection [J]. 信息网络安全, 2019, 19(4): 37-46. |
| [10] | CHEN Liangchen, GAO Shu, LIU Baoxu, LU Zhigang. Research Status and Development Trends on Network Encrypted Traffic Identification [J]. 信息网络安全, 2019, 19(3): 19-25. |
| [11] | HU Jianwei, ZHAO Wei, YAN Zheng, ZHANG Rui. Analysis and Implementation of SQL Injection Vulnerability Mining Technology Based on Machine Learning [J]. Netinfo Security, 2019, 19(11): 36-42. |
| [12] | Weiping WEN, Jingwei LI, Yingnan JIAO, Hailin LI. A Vulnerability Detection Method Based on Random Detection Algorithm and Information Aggregation [J]. Netinfo Security, 2019, 19(1): 1-7. |
| [13] | YU Yingchao, DING Lin, CHEN Zuoning. Research on Attacks and Defenses towards Machine Learning Systems [J]. 信息网络安全, 2018, 18(9): 10-18. |
| [14] | ZHANG Yang, YAO Yuangang. Research on Network Intrusion Detection Based on Xgboost [J]. 信息网络安全, 2018, 18(9): 102-105. |
| [15] | WEN Weiping, WU Bozhi, JIAO Yingnan, HE Yongqiang. Design and Implementation on Malicious Documents Detection Tool Based on Machine Learning [J]. 信息网络安全, 2018, 18(8): 1-7. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||