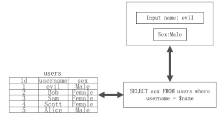
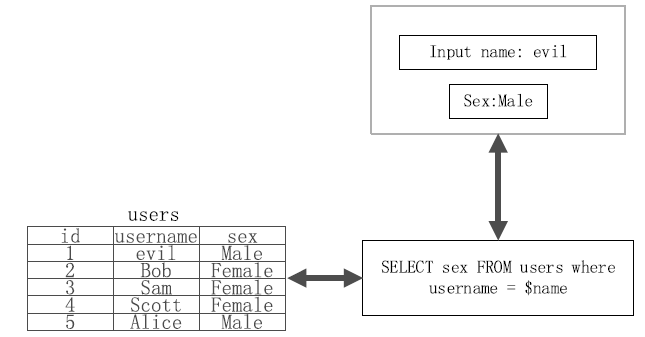
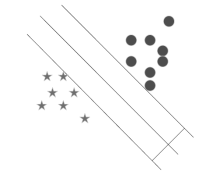
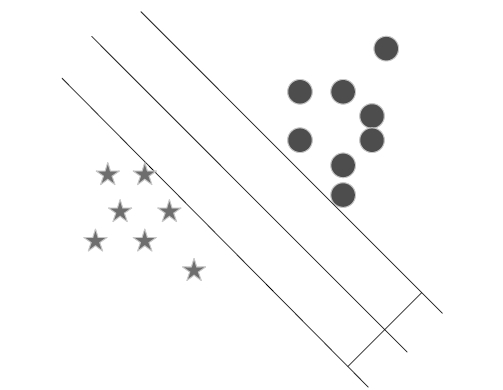
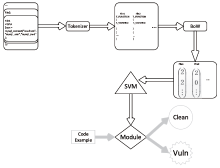
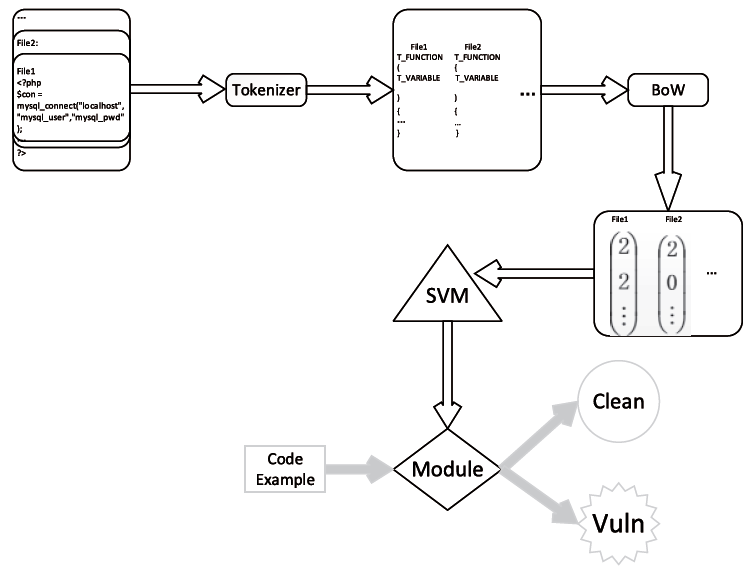
| [1] |
SINGH N, DAYAL M, RAW R S, et al. SQL Injection: Types, Methodology, Attack Queries and Prevention[EB/OL]., 2019-4-10.
|
| [2] |
ABIRAMI J, DEVAKUNCHARI R, VALLIYAMMAI C. A Top Web Security Vulnerability SQL Injection Attack Survey[EB/OL]. , 2019-4-10.
|
| [3] |
QIAN L, ZHU Z, HU J, et al. Research of SQL Injection Attack and Prevention Technology[EB/OL]. , 2019-4-10.
|
| [4] |
KUMAR P, PATERIYA R K. A Survey on SQL Injection Attacks, Detection and Prevention Techniques[EB/OL]. , 2019-4-10.
|
| [5] |
SHAR L K, TAN H B K. Defeating SQL Injection[J]. Computer, 46(3): 69-77.
|
| [6] |
JOHARI R, SHARMA P.A Survey on Web Application Vulnerabilities(SQLIA, XSS) Exploitation and Security Engine for SQL Injection[C]// IEEE. 2012 International Conference on Communication Systems and Network Technologies, May 11-13, 2012, Rajkot, India. New York: IEEE, 2012: 453-458.
|
| [7] |
SHAR L K, TAN H B K. Mining Input Sanitization Patterns for Predicting SQL Injection and Cross Site Scripting Vulnerabilities[C]// IEEE. 34th International Conference on Software Engineering(ICSE), June 2-9, 2012, Zurich, Switzerland. New York: IEEE, 2012: 1293-1296.
|
| [8] |
SHAR L K, TAN H B K, BRIAND L C. Mining SQL Injection and Cross Site Scripting Vulnerabilities Using Hybrid Program Analysis[C]// IEEE. ICSE'13 Proceedings of the 2013 International Conference on Software Engineering, May 18 - 26, 2013, San Francisco, CA, USA. New York: IEEE, 2013: 642-651.
|
| [9] |
BUJA G, JALIL K B A, ALI F B H M, et al. Detection Model for SQL Injection Attack: An Approach for Preventing a Web Application from the SQL Injection Attack[EB/OL]. , 2019-4-10.
|
| [10] |
BOYD S W, KEROMYTIS A D. SQLrand: Preventing SQL Injection Attacks[EB/OL]. , 2019-4-10.
|
| [11] |
MEI J J.An Approach for SQL Injection Vulnerability Detection[C]// IEEE. 2009 Sixth International Conference on Information Technology: New Generations. IEEE, April 27-29, 2009, Las Vegas, NV, USA. New York: IEEE, 2009: 1411-1414.
|
| [12] |
BISHT P, MADHUSUDAN P, VENKATAKRISHNAN V N.CANDID: Dynamic Candidate Evaluations for Automatic Prevention of SQL Injection Attacks[J]. ACM Transactions on Information and System Security(TISSEC), 2010, 13(2): 14.
|
| [13] |
ANITHA V, LAKSHMI S, REVATHI M, et al.Detecting Various SQL Injection Vulnerabilities Using String Matching and LCS method[C]// IEEE.2014 Sixth International Conference on Advanced Computing(ICoAC), December 17-19, 2014, Chennai, India. New York: IEEE, 2014: 237-241.
|
| [14] |
JOSHI A, GEETHA V.SQL Injection Detection Using Machine Learning[C]//IEEE. 2014 International Conference on Control, Instrumentation, Communication and Computational Technologies(ICCICCT), July 10-11, 2014, Kanyakumari, India. New York: IEEE, 2014: 1111-1115.
|
| [15] |
XIAO Z, ZHOU Z, YANG W, et al. An Approach for SQL Injection Detection Based on Behavior and Response Analysis[EB/OL]. , 2019-4-10.
|
| [16] |
JOHNSON B, SONG Y, MURPHY H E, et al.Why Don't Software Developers Use Static Analysis Tools to Find Bugs?[C]// IEEE. 2013 International Conference on Software Engineering, May 18-26, 2013, San Francisco, CA, USA. New York: IEEE, 2013: 672-681.
|
| [17] |
WALDEN J, STUCKMAN J, SCANDARIATO R.Predicting Vulnerable Components: Software Metrics vs Text Mining[C]// IEEE. 25th International Symposium on Software Reliability Engineering, November 3-6, 2014, Naples, Italy. New York: IEEE, 2014: 23-33.
|
| [18] |
STIVALET B, FONG E.Large Scale Generation of Complex and Faulty PHP Test Cases[C]// IEEE. 2016 IEEE International Conference on Software Testing, Verification and Validation(ICST), April 11-15, 2016, Chicago, IL, USA. New York: IEEE, 2016: 409-415.
|
| [19] |
YAN X X, WANG Q X, MA H T. Path Sensitive Static Analysis of Taint-style Vulnerabilities in PHP Code[EB/OL]. , 2019-4-10.
|
| [20] |
GHAFFARIAN S M, SHAHRIARI H R.Software Vulnerability Analysis and Discovery Using Machine-learning and Data-mining Techniques: A survey[J]. ACM Computing Surveys(CSUR), 2017, 50(4): 56.
|
| [21] |
PAN S J, YANG Q.A Survey on Transfer Learning[J]. IEEE Transactions on Knowledge and Data Engineering, 2009, 22(10): 1345-1359.
|
 ), Zheng YAN, Rui ZHANG
), Zheng YAN, Rui ZHANG