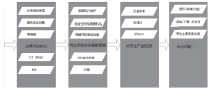
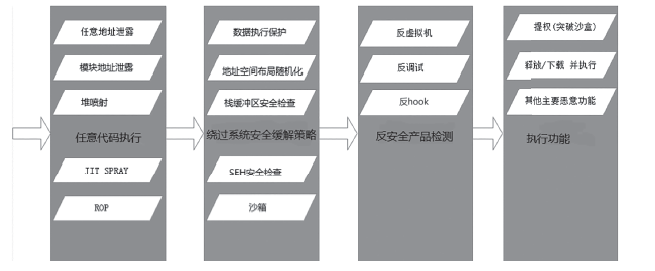
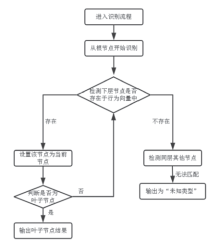
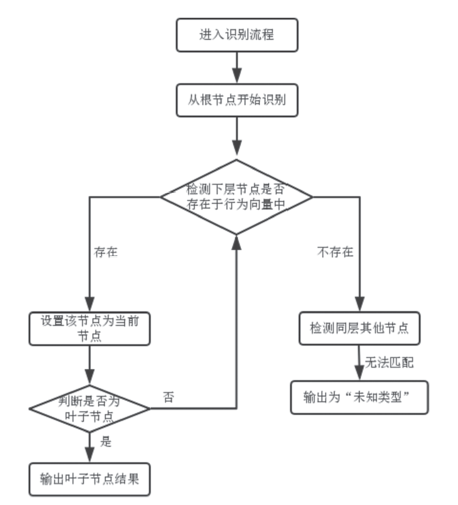
| [1] |
Symantec. Attackers Target Both Large and Small Businesses[EB/OL]. ,2018-3-20.
|
| [2] |
MAO Ningxiang, WEN Weiping,FU Jun.Analysis of Anti-attack Key Technologies in IE Browser[J]. Netinfo Security, 2011, 11(7): 26-29.
|
|
毛宁祥,文伟平,傅军. IE浏览器防攻击关键技术分析[J]. 信息网络安全, 2011, 11(7): 26-29.
|
| [3] |
CHEN Yue.The Survey of Address Space Layout Randomization (ASLR) Enhancement[J]. China Education Network, 2016(8):36-37.
|
|
CHEN Yue.地址空间布局随机化(ASLR)增强研究综述[J]. 中国教育网络, 2016(8):36-37.
|
| [4] |
YANG Chunhui, YAN Chenghua.The Analysis of the Security Strategy Based on Process Management[J]. Netinfo Security, 2014, 14(8): 61-66.
|
|
杨春晖, 严承华. 基于进程管理的安全策略分析[J]. 信息网络安全, 2014, 14(8): 61-66.
|
| [5] |
LIU Lin, ZHAO Xianghui, YAO Yuangang, et al.Composite Document Malicious Code Detection Based on Spectrum Analysis[J]. Journal of Tsinghua University:Science and Technology, 2013, 53(12):1713-1718.
|
|
刘林,赵向辉,姚原岗,等. 基于频谱分析的复合文档恶意代码检测[J]. 清华大学学报:自然科学版, 2013, 53(12):1713-1718.
|
| [6] |
HAO Chenxi, FANG Yong.The Method of Malicious Code Detection for PDF Files Based on Spectrum Analysis[J]. Journal of Information Security Research, 2016, 2(2):166-171.
|
|
郝晨曦,方勇. 基于频谱分析的PDF文件恶意代码检测方法[J]. 信息安全研究, 2016, 2(2):166-171.
|
| [7] |
HU Jiang, ZHOU Anmin.Research on Malicious PDF Document Detection Technology for JavaScript Attack[J]. Modern Computer. 2016(1):36-40.
|
|
胡江, 周安民. 针对JavaScript攻击的恶意PDF文档检测技术研究[J]. 现代计算机, 2016(1):36-40.
|
| [8] |
HUANG H D, CHUANG T Y, TSAI Y L, et al. Ontology-based Intelligent System for Malware Behavioral Analysis[EB/OL]..
|
| [9] |
SUN Benyang, WANG Yijun, XUE Zhi.An Improved Static Monitoring Scheme for Malicious PDF Documents[J]. Computer Applications And Software, 2016, 33(3):308-313.
|
|
孙本阳,王轶骏,薛质. 一种改进的恶意PDF文档静态监测方案[J]. 计算机应用与软件, 2016, 33(3):308-313.
|
| [10] |
FENG Di, YU Min, WANG Yongjian, et al. Detecting Malicious PDF Files Using Semi-Supervised Learning Method[EB/OL]. .
|
| [11] |
Tom Mitchell.Machine Learning[M]. ZENG Huajun, ZHANG Yinkui. Beijing: China Machine Press, 2008.
|
|
Tom Mitchell.机器学习[M].曾华军,张银奎,译. 北京:机械工业出版社,2008.
|
| [12] |
WEN Weiping, ZHANG Puhan, Xu Youfu, et al.Software Security Vulnerability Mining Method Based on Reference Security Patch Comparison[J]. Journal of Tsinghua University:Science and Technology, 2011(10): 1264-1268.
|
|
文伟平, 张普含,徐有福,等. 参考安全补丁比对的软件安全漏洞挖掘方法[J]. 清华大学学报:自然科学版,2011(10):1264-1268.
|
| [13] |
Adobe. PDF Reference[EB/OL]. .
|
| [14] |
ZHANG Xiaokang, SHUAI Jianmei, SHI Lin.Malicious Code Detection Method Based on Weighted Information Gain[J]. Computer Engineering, 2010(6):149-151.
|
|
张小康, 帅建梅, 史林. 基于加权信息增益的恶意代码检测方法[J]. 计算机工程,2010(6) :149-151.
|
| [15] |
Microsoft. File System Minifilter Drivers[EB/OL]. ,2017-4-20.
|
| [16] |
CHENG Sanjun, WANG Yu.Analysis of APT Attack Principle and Protection Technology[J]. Netinfo Security, 2016,16(9): 118-123.
|
|
程三军,王宇. APT 攻击原理及防护技术分析[J]. 信息网络安全,2016,16(9): 118-123.
|
| [17] |
JIN Xin, CHEN Xingshu, ZHAO Cheng, et al.Trusted Attestation Architecture on an Infrastructure-as-a-service[J]. Journal of Tsinghua University, 2017, 22(5):469-477.
|
|
金鑫,陈兴蜀,赵成,等. 基于基础设施即服务的可信认证架构[J].清华大学学报,2017,22(5):469-477.
|
| [18] |
YAO Huachao, WANG Zhenyu.Construction of Virtualization Resource Pool Based on KVM-QEMU and Libvirt[J]. Computer and Modernization, 2013(7):26-33.
|
|
姚华超,王振宇. 基于KVM-QEMU与Libvirt的虚拟化资源池构建[J]. 计算机与现代化,2013(7):26-33.
|
 ), Bozhi WU1, Yingnan JIAO2, Yongqiang HE1
), Bozhi WU1, Yingnan JIAO2, Yongqiang HE1