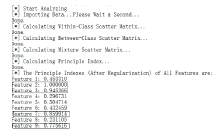
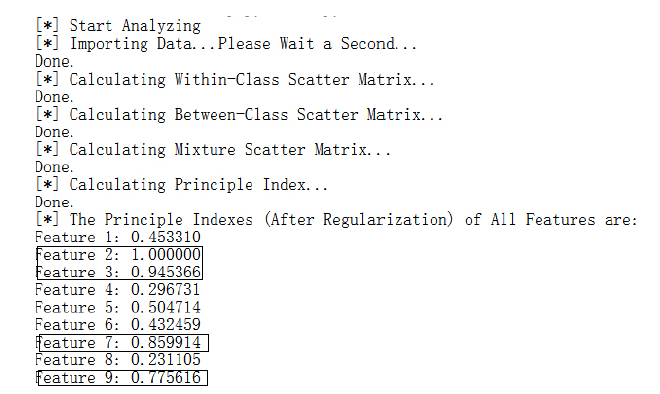
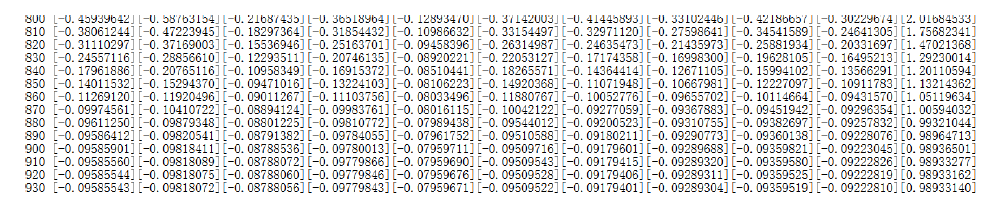
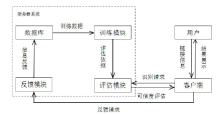
| [1] |
National Internet Information Office. National Cyberspace Security Strategy[R]. Beijing: China Network Security and Information Leading Group, 2016.
|
|
国家互联网信息办公室. 国家网络空间安全战略[R]. 北京:中央网络安全和信息化领导小组,2016.
|
| [2] |
iiMedia Research. Research Report on China's Network Security Market in the First Half of 2017[EB/OL]. .
|
|
艾媒咨询.2017上半年中国网络安全市场研究报告[EB/OL]. .
|
| [3] |
ANONYMOUS. Download Link Where are You? Incomplete Evaluation on Inductive False Download Link[J]. PC Digest, 2010(9):3-6.
|
| [4] |
Wikipedia.Cryptocurrency[EB/OL]..
|
| [5] |
MA J, SAUL L K, SAVAGE S, et al.Identifying Suspicious URLs: An Application of Large-scale Online Learning[C]//ACM. Proceedings of the 26th International Conference on Machine Learning. June 14 - 18, 2009,Montreal, Quebec, Canada.New York:ACM,2009:681-688.
|
| [6] |
BILGE L, KIRDA E, KRUEGEL C, et al. EXPOSURE: Finding Malicious Domains Using Passive DNS Analysis[EB/OL]..
|
| [7] |
LIN Hailun, LI Yan, WANG Weiping, et al.Efficient Segment Pattern Based Method for Malicious URL Detection[J]. Journal on Communications, 2015, 36(S1):141-148.
|
|
林海伦,李焱,王伟平,等. 高效的基于段模式的恶意URL检测方法[J]. 通信学报, 2015,36(S1):141-148.
|
| [8] |
Wikipedia. tf-idf[EB/OL]..
|
| [9] |
ZHANG Yue, HONG J I, CRANOR L F.Cantina: A Content-based Approach to Detecting Phishing Web Sites[C]//ACM.WWW '07 Proceedings of the 16th international conference on World Wide Web,May 8-12, 2007,Banff, Alberta, Canada .New York:ACM,2007:639-648.
|
| [10] |
XU Jie.Design and Testing of Malicious URL Real-Time Detecting System Working in the Mode of Cloud Security[D]. Beijing:Beijing University of Posts and Telecommunications, 2014.
|
|
许杰. 云安全模式下恶意URL实时检测系统的设计与测试[D]. 北京:北京邮电大学, 2014.
|
| [11] |
PROVOS N, MAVROMMATIS P, et al.All Your iFrames Point to Us[C]//USENIX. Proceedings of the 17th Usenix Security Symposium,July 28 - August 1, 2008,San Jose, CA. Berkeley:USENIX,2008:1-16.
|
| [12] |
ZHOU Zhenfei, FANG Binxing, CUI Xiang, et al.A Method of Malicious Code Detection in WordPress Theme Based on Similarity Analysis[J]. Netinfo Security, 2017,17(12):47-53.
|
|
周振飞,方滨兴,崔翔,等 . 基于相似性分析的 WordPress 主题恶意代码检测[J]. 信息网络安全,2017,17(12): 47-53.
|
| [13] |
CHEN Xu, LI Yukun, YUAN Huaping, et al.Phishing Detection System Based on Classification Confidence and Website Features[J]. Netinfo Security, 2017,17(9):111-114.
|
|
陈旭,黎宇坤,袁华平,等. 基于分类置信度和网站特征的钓鱼检测系统[J]. 信息网络安全,2017,17(9):111-114.
|
| [14] |
MA J, SAUL L K, SAVAGE S, et al.Beyond Blacklist: Learning to Detect Malicious Web Site from Suspicious URLs[C]//ACM SIGKDD. International Conference on Knowledge Discovery & Data Mining, June 28-July 1, 2009, Paris, France. New York:ACM, 2009: 1245-1254.
|
| [15] |
LIU Jian, ZHAO Gang, ZHENG Yunpeng, Design and Implementation of a Multi-layer Filtering Detection Model for Malicious URL[J]. Netinfo Security, 2016,16(1) : 75-80.
|
|
刘健,赵刚,郑运鹏. 恶意URL多层过滤检测模型的设计与实现[J]. 信息网络安全,2016,16,16(1):75-80.
|
| [16] |
THEODORIDIS S, KOUTROUMBAS K.Pattern Recognition Fourth Edition[M]. Netherlands:Elsevier Inc. , 2009.
|
| [17] |
GOODFELLOW I, BENGIO Y, COURVILLE A.Deep Learning[M]. US:MIT Press, 2016.
|
| [18] |
LVSE. A List of Software Download Websites[EB/OL]. .
|
 ), Zhuoxiang SHEN, Dongjie SHEN, Zhi LI
), Zhuoxiang SHEN, Dongjie SHEN, Zhi LI