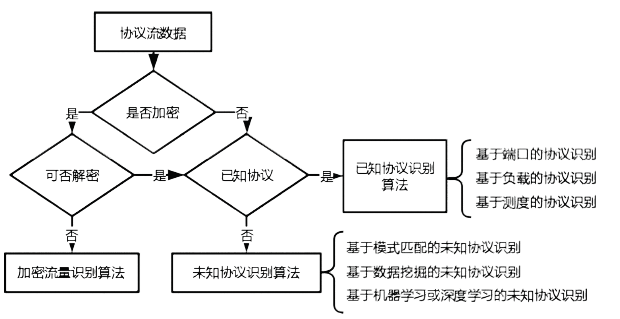
Netinfo Security ›› 2019, Vol. 19 ›› Issue (10): 74-83.doi: 10.3969/j.issn.1671-1122.2019.10.010
Previous Articles Next Articles
Research on Traffic Identification Technology for Unknown Protocols
Xudong WANG( ), Xiangzhan YU, Hongli ZHANG
), Xiangzhan YU, Hongli ZHANG
- School of Computer Science and Technology, Harbin Institute of Technology, Harbin Heilongjiang 150001,China
-
Received:2019-06-06Online:2019-10-10Published:2020-05-11 -
Contact:Xudong WANG E-mail:bluestar.21@qq.com
CLC Number:
Cite this article
Xudong WANG, Xiangzhan YU, Hongli ZHANG. Research on Traffic Identification Technology for Unknown Protocols[J]. Netinfo Security, 2019, 19(10): 74-83.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2019.10.010
| [1] | LEI Dong, WANG Tao, ZHANG Jianpeng, et al.Survey on Bit Stream-oriented Unknown Protocol Identification and Analysis Techniques[J]. Application Research of Computers, 2016, 33(11): 3206-3210, 3250. |
| 雷东,王韬,赵建鹏,等. 面向比特流的未知协议识别与分析技术综述[J]. 计算机应用研究,2016,33(11):3206-3210,3250. | |
| [2] | CHEN Lliang, GONG Jian, XU Xuan.A Survey of Application-Level Protocol Identification Algorithm[J]. Computer Science, 2007, 34(7): 73-75. |
| 陈亮,龚俭,徐选. 应用层协议识别算法综述[J]. 计算机科学, 2007,34(7):73-75. | |
| [3] | HC360.com.2008 Latest P2P Traffic Monitoring and Management Solution[EB/OL]. , 2008-2-27. |
| 慧聪网. 2008最新P2P流量监控与管理解决方案[EB/OL].,2008-2-27. | |
| [4] | IANA. IANA[EB/OL]. https://www.iana.org/about, 2019-5-21. |
| [5] | KARAGIANNIS T, PAPAGIANNAKI K, FALOUTSOS M.BLINC: Multilevel Traffic Classification in the Dark[C]//ACM. The 2005 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications, August 22 - 26, 2005, Philadelphia, Pennsylvania, USA. New York: ACM, 2005: 229-240. |
| [6] | MADHUKAR A, WILLIAMSON C.A Longitudinal Study of P2P Traffic Classification[C]// IEEE. 14th IEEE International Symposium on Modeling, Analysis, and Simulation, September 11-14, 2006, Monterey, CA, USA. NJ: IEEE, 2006: 179-188. |
| [7] | KANG H J, KIM M S, HONG J W K. A Method on Multimedia Service Traffic Monitoring and Analysis[M]//Springer. Self-managing Distributed Systems. Heidelberg: Springer, 2003: 93-105. |
| [8] | MERWE J V D, Ramón Cáceres, CHU Yanghua, et al. Mmdump: A Tool for Monitoring Internet Multimedia Traffic[J]. Acm Sigcomm Computer Communication Review, 2000, 30(5): 48-59. |
| [9] | MA J, LEVCHENKO K, KREIBICH C, et al.Unexpected Means of Protocol Inference[C]//ACM. The 6th ACM SIGCOMM Conference on Internet Measurement, October 25-27, 2006, Rio de Janeriro, Brazil. New York: ACM, 2006: 313. |
| [10] | SEN S, SPATSCHECK O, WANG Dongmei.Accurate, Scalable In-network Identification of p2p Traffic Using Application Signatures[C]//ACM. The 13th International Conference on World Wide Web, May 17 - 20, 2004, New York, NY, USA. New York: ACM, 2004: 512-521. |
| [11] | SONG Jiang, ZHANG Chunrui, ZHANG Nan, et al.Network Traffic Identification Based on Data Finger-print[J]. Application Research of Computers, 2012, 29(12): 4604-4606, 4614. |
| 宋疆,张春瑞,张楠,等. 基于数据报指纹关系的未知协议识别与发现[J]. 计算机应用研究,2012, 29(12):4604-4606,4614. | |
| [12] | PAN Wubin, CHENG Guang, GUO Xiaojun, et al.Review and Perspective on Encrypted Traffic Identification Research[J]. Journal on Communications, 2016, 37(9): 154-167. |
| 潘吴斌,程光,郭晓军,等. 网络加密流量识别研究综述及展望[J]. 通信学报,2016,37(9):154-167. | |
| [13] | HE Yongjun, SHU Hui, XIONG Xiaobing.Network Protocol Reverse Parsing Based on Dynamic Binary Analysis[J]. Computer Engineering, 2010, 36(9): 268-270. |
| 何永君,舒辉,熊小兵. 基于动态二进制分析的网络协议逆向解析[J]. 计算机工程,2010,36(9):268-270. | |
| [14] | HAFFNER P, SEN S, SPATSCHECK O, et al.ACAS: Automated Construction of Application Signatures[C]// ACM. The 2005 ACM SIGCOMM Workshop on Mining Network Data, August 26, 2005, Philadelphia, Pennsylvania, USA. New York: ACM, 2005: 197-202. |
| [15] | LI Xin, BIAN Fang, CROVELLA M, et al.Detection and Identification of Network Anomalies Using Sketch Subspaces[C]// ACM. The 6th ACM SIGCOMM Conference on Internet Measurement, October 25 - 27, 2006, Rio de Janeriro, Brazil. New York: ACM, 2006: 147-152. |
| [16] | YEGANEH S H, EFTEKHAR M, GANJALI Y, et al.CUTE: Traffic Classification Using TErms[C]//IEEE. 2012 21st International Conference on Computer Communications & Networks, July 30- August 2, 2012, Munich, Germany. NJ: IEEE, 2012: 1-9. |
| [17] | FU Wenliang, SONG Tian, ZHOU Zhou.RocketTC: A High Throughput Traffic Classification Architecture on FPGA[J]. Chinese Journal of Computers, 2014, 37(2): 414-422. |
| 付文亮,嵩天,周舟. RocketTC:一个基于FPGA的高性能网络流量分类架构[J]. 计算机学报,2014,37(2):414-422. | |
| [18] | ZHANG Zhuo, ZHANG Zhibin, LEE P P C, et al. Toward Unsupervised Protocol Feature Word Extraction[J]. IEEE Journal on Selected Areas in Communications, 2014, 32(10): 1894-1906. |
| [19] | HU Xiaoyan, GONG Jian.Relevance Analysis of Network Traffic Classification Measure[C]//CERNET. CERNET 16th Annual Academic Conference, December 12-14, 2009, Tianjin, China. Beijing: CERNET, 2012: 221-224. |
| [20] | LI Wei.Overview of Machine Learning[J]. Science&Technology, 2017(12): 149. |
| 李炜. 机器学习概述[J]. 科技视界,2017(12):149. | |
| [21] | LIN Ping, YU Xunyi, LIU Fang, et al.A Network Traffic Classification Algorithm Based on Flow Statistical Characteristics[J]. Journal of Beijing University of Posts and Telecommunications, 2008, 31(2): 15-19. |
| 林平,余循宜,刘芳,等. 基于流统计特性的网络流量分类算法[J]. 北京邮电大学学报,2008,31(2):15-19. | |
| [22] | OKABE T, KITAMURA T, SHIZUNO T.Statistical Traffic Identification Method Based on Flow-level Behavior for Fair VoIP Service[C]// IEEE. 1st IEEE Workshop on VoIP Management and Security, April 3-7, 2006, Vancouver, BC, Canada. NJ: IEEE, 2006: 1-18. |
| [23] | KARAGIANNIS T.Blinc: Multilevel Traffic Classification in the Dark[C]//ACM. The 2005 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications, August 22 - 26, 2005, Philadelphia, Pennsylvania, USA. New York: ACM, 2005: 229-240. |
| [24] | ESTE A, GRINGOLI F, SALGARELLI L.Support Vector Machines for TCP traffic classification[J]. Computer Networks, 2009, 53(14): 2476-2490. |
| [25] | ESTE A, GRINGOLI F, SALGARELLI L.On-line SVM Traffic Classification[C]//IEEE. 2011 7th International Wireless Communications and Mobile Computing Conference, July 4-8, 2011, Istanbul, Turkey. NJ: IEEE, 2011: 1778-1783. |
| [26] | GROLEAT T, ARZEL M, VATON S.Hardware Acceleration of SVM-based Traffic Classification on FPGA[C]// IEEE. 2012 8th International Wireless Communications and Mobile Computing Conference, August 27-31, 2012, Limassol, Cyprus. NJ: IEEE, 2012: 443-449. |
| [27] | ZHOU Wengang, DONG Leiting, BIC L, et al.Internet Traffic Classification Using Feed-forward Neural Network[C]//IEEE. 2011 International Conference on Computational Problem-solving, October 21-23, Chengdu, China. NJ: IEEE, 2011: 641-646. |
| [28] | ZHAO Weiyu, TANG Wenxiu.P2P Traffic Identification Based on BP Neural Network Clustering Algorithm[J]. Control and Instruments in Chemical Industry, 2013(4): 515-518. |
| 赵魏雨,唐文秀. 基于BP神经网络聚类算法的P2P流量识别[J]. 化工自动化及仪表,2013(4):515-518. | |
| [29] | ZHANG Jun, XIANG Yang, WANG Yu, et al.Network Traffic Classification Using Correlation Information[J]. IEEE Transactions on Parallel and Distributed Systems, 2013, 24(1): 104-117. |
| [30] | ERMAN J, ARLITT M, MAHANTI A.Traffic Classification Using Clustering Algorithms[C]//ACM. the 2006 SIGCOMM Workshop on Mining Network Data, MineNet'06, September 11 - 15, 2006, Pisa, Italy. New York: ACM, 2006: 281-286. |
| [31] | PENG Lizhi.A Survey of Internet Traffic Identification[J]. Journal of University of Jinan(Science and Technology), 2016, 30(2): 95-104. |
| 彭立志. 互联网流量识别研究综述[J]. 济南大学学报(自然科学版),2016,30(2):95-104. | |
| [32] | CAI Le, SHI Rong, XU Du.Identification Method of Unknown Protocol Signatures Based on Association Rules Mining[J]. Electronic Warfare Technology, 2016, 31(6): 18-23, 57. |
| 蔡乐,石荣,许都. 基于关联规则挖掘的未知协议特征提取方法[J]. 电子信息对抗技术,2016,31(6):18-23,57. | |
| [33] | GU Chengjie, ZHUANG Shunyi.A Novel P2P Traffic Classification Approach Using back Propagation Neural Network[C]//IEEE. 2010 IEEE 12th International Conference on Communication Technology, November 11-14, 2010, Nanjing, China. NJ: IEEE, 2011: 52-55. |
| [34] | CHEN Hongwei, HU Zhengbing, YE Zhiwei, et al.Research of P2P Traffic Identification Based on Neural Network[C]//IEEE. 2009 International Symposium on Computer Network & Multimedia Technology, January 18-20, 2009, Wuhan, China. NJ: IEEE, 2009: 1-4. |
| [35] | HE Wei, WANG Ronggui, ZHA Quanmin.A Novel Fast Moving Algorithm for Single Pattern Matching[J]. Journal of Hefei University of Technology(Natural Science), 2010, 33(5): 665-669. |
| 何畏,汪荣贵,查全民. 一种新的快速移动单模式匹配算法[J]. 合肥工业大学学报(自然科学版),2010,33(5):665-669. | |
| [36] | ZHU Jiaojiao, YE Meng.Multi-pattern Matching and Application of Improved Algorithm to Protocol Identification[J]. Video Engineering, 2012, 36(7): 60-63. |
| 朱姣姣,叶猛. 多模式匹配及其改进算法在协议识别中的应用[J]. 电视技术,2012,36(7):60-63. | |
| [37] | AHO A V, CORASICK M J.Efficient String Matching: An Aid to Bibliographic Search[J]. Communications of the ACM, 1975, 18(6): 333-340. |
| [38] | WU Sun, MANBER U.A Fast Algorithm for Multi-pattern Searching[D]. Tucson: University of Arizona, 1994. |
| [39] | JIN Ling.Research on Unknown Header Recognition Technology for Bit Stream[D]. Shanghai: Shanghai Jiao Tong University, 2011. |
| 金凌. 面向比特流的未知帧头识别技术研究[D]. 上海:上海交通大学,2011. | |
| [40] | LU Lina, CHEN Yaping, WEI Hengyi, et al.Research on the Algorithm Apriori of Mining Association Rules[J]. Mini-micro Systems, 2000, 21(9): 940-943. |
| 陆丽娜,陈亚萍,魏恒义,等. 挖掘关联规则中Apriori算法的研究[J]. 小型微型计算机系统,2000,21(9):940-943. | |
| [41] | LIU Xiping.Research and Application of Association Rule Mining Algorithms Based on Fp-growth Algorithms[D]. Changsha: Hunan University, 2006. |
| 刘喜苹. 基于Fp-growth算法的关联规则挖掘算法研究和应用[D]. 长沙:湖南大学,2006. | |
| [42] | HAN Jiawei, PEI Jian, MORTAZAVI-ASL B, et al.FreeSpan: Frequent Pattern-projected Sequential Pattern Mining[C]//ACM. The sixth ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, August 20 - 23, 2000, Boston, Massachusetts, USA. New York: ACM, 2000: 355-359. |
| [43] | YAN Jie, QI Wenjuan.Research Based on Aprior & FP-growth Algorithm[J]. Computer Systems & Applications, 2013, 22(5): 122-125. |
| 晏杰,亓文娟. 基于Aprior&FP-growth算法的研究[J]. 计算机系统应用,2013,22(5):122-125. | |
| [44] | WANG Yong, WU Yanmei, LI Fen, et al.Protocol Identification Association Analysis in Mobile Network Environment[J]. Application Research of Computers, 2015, 32(1): 243-248. |
| 王勇,吴艳梅,李芬,等. 面向比特流数据的未知协议关联分析与识别[J]. 计算机应用研究,2015,32(1):243-248. | |
| [45] | XUE Kaiping, LIU Bin, WANG Jinsong, et al.Data Link Bit Stream Oriented Association Analysis on Unknown Frame[J]. Journal of Electronics & Information Technology, 2017, 39(2): 374-380. |
| 薛开平,柳彬,王劲松,等. 面向链路比特流的未知帧关联分析[J]. 电子与信息学报,2017,39(2):374-380. |
| [1] | SONG Xin, ZHAO Kai, ZHANG Linlin, FANG Wenbo. Research on Android Malware Detection Based on Random Forest [J]. Netinfo Security, 2019, 19(9): 1-5. |
| [2] | KANG Jian, WANG Jie, LI Zhengxu, ZHANG Guangda. A Model for Anomaly Intrusion Detection with Different Feature Extraction Strategies in IoT [J]. Netinfo Security, 2019, 19(9): 21-25. |
| [3] | LI Hui, NI Shice, XIAO Jia, ZHAO Tianzhong. Emotion Classification Technology for Online Video Comments on the Internet [J]. 信息网络安全, 2019, 19(5): 61-68. |
| [4] | CHEN Liangchen, GAO Shu, LIU Baoxu, LU Zhigang. Research Status and Development Trends on Network Encrypted Traffic Identification [J]. 信息网络安全, 2019, 19(3): 19-25. |
| [5] | Weiping WEN, Jingwei LI, Yingnan JIAO, Hailin LI. A Vulnerability Detection Method Based on Random Detection Algorithm and Information Aggregation [J]. Netinfo Security, 2019, 19(1): 1-7. |
| [6] | LU Gang, GUO Ronghua, ZHOU Ying, WANG Jun. Review of Malicious Traffic Feature Extraction [J]. 信息网络安全, 2018, 18(9): 1-9. |
| [7] | DUAN Guihua, SHEN Zhuoxiang, SHEN Dongjie, LI Zhi. Research on a Download Link Recognition Scheme Based on Feature Extraction [J]. 信息网络安全, 2018, 18(10): 31-36. |
| [8] | FANG Yuejian, ZHU Jinzhong, ZHOU Wen, LI Tongliang. A Survey on Data Mining Privacy Protection Algorithms [J]. 信息网络安全, 2017, 17(2): 6-11. |
| [9] | QIU Yue. Research on the Hidden Web Technology for the Network Content Security [J]. 信息网络安全, 2015, 15(9): 106-108. |
| [10] | MU Zheng, WU Jin, XU Shu-juan. Research on P2P Traffic Identification Under the High Speed Network [J]. 信息网络安全, 2015, 15(5): 69-76. |
| [11] | HU Xue, FENG Hua-min,LI Ming-wei, DING Zhao. Analysis of An Enhanced Apriori Algorithms in Data Mining [J]. 信息网络安全, 2015, 15(11): 77-83. |
| [12] | ZHAO Zheng, LIU Ji-qiang. Research and Realization of Indentification Technology of Mobile Internet Audio-Video Protocol [J]. 信息网络安全, 2014, 14(12): 61-64. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||