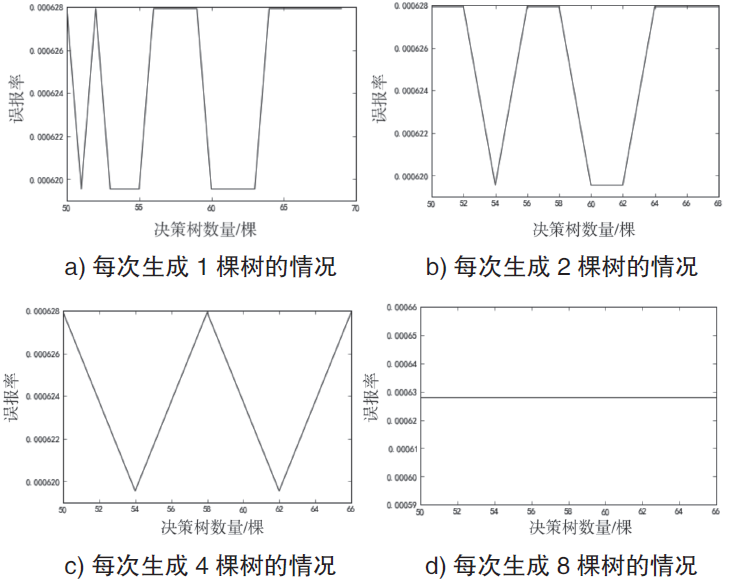
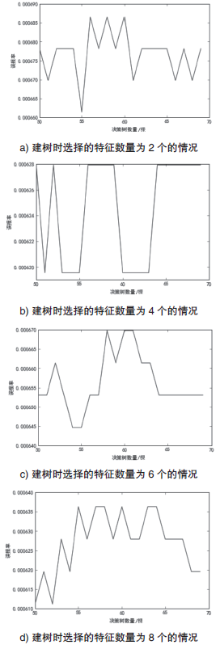
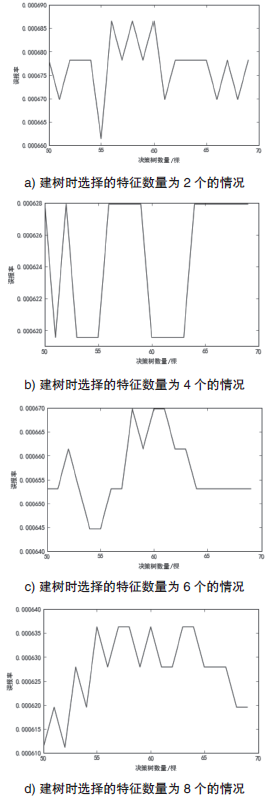
| [1] |
MA Tao, WANG Fen, CHENG Jianjun, et al.A Hybrid Spectral Clustering and Deep Neural Network Ensemble Algorithm for Intrusion Detection in Sensor Networks[J]. Sensors, 2016, 16(10):1701.
|
| [2] |
ALJARRAH O Y, ALHUSSEIN O, YOO P D, et al.Data Randomization and Cluster-based Partitioning for Botnet Intrusion Detection.[J]. IEEE Transactions on Cybernetics, 2016, 46(8): 1796.
|
| [3] |
KANG M J, KANG J W.Intrusion Detection System Using Deep Neural Network for In-Vehicle Network Security[J]. Plos One, 2016, 11(6):0155781-0155798.
|
| [4] |
ALOM M Z, BONTUPALLI V R, TAHA T M.Intrusion Detection Using Deep Belief Networks[C]// IEEE.Aerospace and Electronics Conference, June 15-19, 2015, Dayton, OH, USA.NJ: IEEE, 2016:339-344.
|
| [5] |
YANG Kunpeng.An Intrusion Detection Model Based on Deep Belief Networks[J]. Modern Computer,2015(2):10-14.
|
|
杨昆朋. 基于深度信念网络的入侵检测模型[J]. 现代计算机, 2015(2):10-14.
|
| [6] |
LIU Rujun, JIA Bin, XIN Yang.Network Anomaly Detection Model Based on Information Gain Feature Selection[J]. Journal of Computer Applications, 2016, 36(a02):49-53.
|
|
刘汝隽, 贾斌, 辛阳. 基于信息增益特征选择的网络异常检测模型[J]. 计算机应用, 2016, 36(a02):49-53.
|
| [7] |
QIAN Yanyan, LI Yongzhong, YU Xiya.Intrusion Detection Method Based on Multi-label and Semi-supervised Learning[J]. Computer Science, 2015, 42(2):134-136.
|
|
钱燕燕, 李永忠, 余西亚. 基于多标记与半监督学习的入侵检测方法研究[J]. 计算机科学, 2015, 42(2):134-136.
|
| [8] |
XIA Yuming, HU Shaoyong, ZHU Shaomin, et al.Research on the Method of Network Attack Detection Based on Convolution Neural Network[J].Netinfo Security,2017(11):32-36.
|
|
夏玉明,胡绍勇,朱少民,等. 基于卷积神经网络的网络攻击检测方法研究[J]. 信息网络安全,2017(11):32-36.
|
| [9] |
MITCHELL T, BUCHANAN B, DEJONG G, et al.Machine Learning[J]. Kluwer International, 1997, 4(1):417-433.
|
| [10] |
CHEN Kang, XIANG Yong, YU Chao.New Trend of Machine Learning in the Age of Big Data[J]. Telecommunications Science, 2012, 28(12):88-95.
|
|
陈康, 向勇, 喻超. 大数据时代机器学习的新趋势[J]. 电信科学, 2012, 28(12):88-95.
|
| [11] |
HU Yangrui, CHEN Xingshu, WANG Junfeng, et al.Anomalous Traffic Detection Based on Traffic Behavior Characteristics[J].Netinfo Security,2016(11):45-51.
|
|
胡洋瑞,陈兴蜀,王俊峰,等.基于流量行为特征的异常流量检测[J].信息网络安全,2016(11):45-51.
|
| [12] |
LUO Yuhua, ZUO Jun, LI Yan.SVM and Its Application in Text Classification[J].Science& Technology Information, 2010(3):49-50.
|
|
罗玉华, 左军, 李岩. SVM及其在文本分类中的应用[J]. 科技信息, 2010(3):49-50.
|
| [13] |
ZHANG Xiaohui, LIN Bogang.Research on Internet of Things Security Based on Support Vector Machines with Balanced Binary Decision Tree[J].Netinfo Security,2015(8):20-25.
|
|
张晓惠,林柏钢.基于平衡二叉决策树SVM算法的物联网安全研究[J].信息网络安全,2015(8):20-25.
|
| [14] |
LEE W, STOLFO S J, MOK K W. A Data Mining Framework for Building Intrusion Detection Models[EB/OL]. ,2018-2-25.
|
| [15] |
LIU Qian.Research on Target Detection and Tracking Algorithm Based on Machine Learning[D]. Wuhan:South Central University for Nationalities, 2013.
|
|
刘倩. 基于机器学习的目标检测与跟踪算法研究[D]. 武汉:中南民族大学, 2013.
|
| [16] |
MCCULLOCH W S,PITTS W.A Logical Calculus of the Ideas Immanent in Nervous Activity[J].Bulletin of Mathematical Biophysics, 1943,5(4):115-133.
|
| [17] |
ROSENBLATT F. The Perceptron-A Perceiving and Recognizing Automaton [EB/OL].,2018-2-25.
|
 ), Jiguo JIANG2
), Jiguo JIANG2