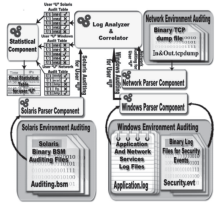
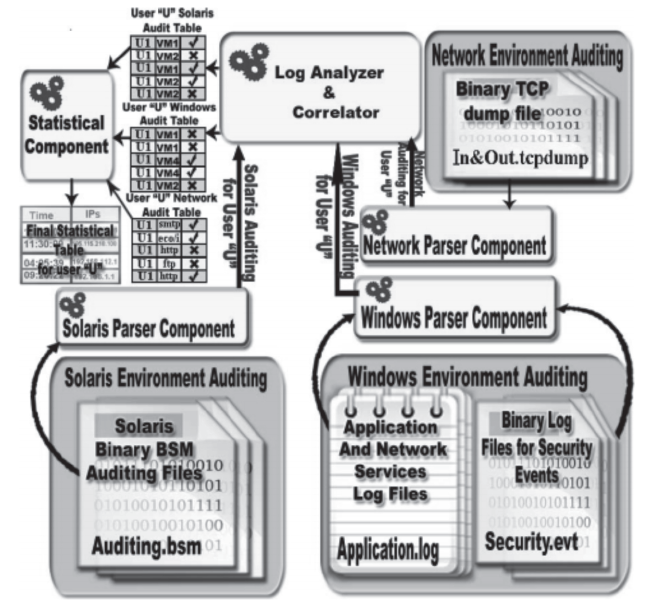
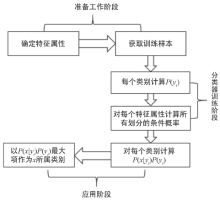
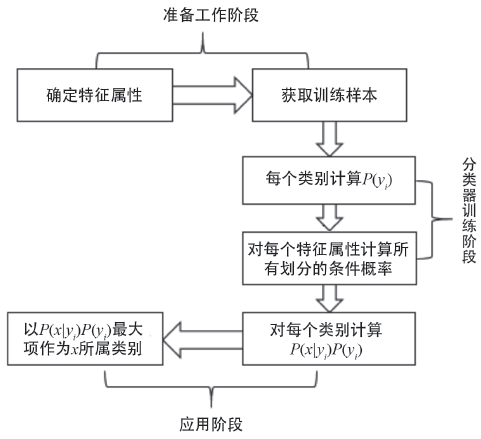
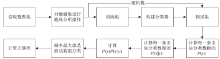
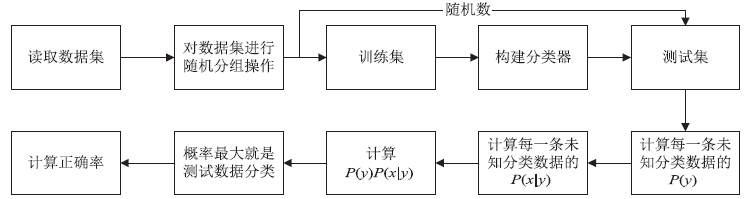
| [1] |
王国峰,刘川意,潘鹤中,等. 云计算模式内部威胁综述[J]. 计算机学报, 2017,40(410):26-46.
|
| [2] |
姬炳帅, 李虎, 韩伟红,等. 面向电子商务的用户异常行为检测研究[J]. 信息网络安全, 2014(9):80-85.
|
| [3] |
GREENBERG S. Using UNIX: Collected Traces of 168 Users[EB/OL].,2017-11-20.
|
| [4] |
LANE T, BRODLEY C E. An Application of Machine Learning to Anomaly Detection[EB/OL].,2017-11-20.
|
| [5] |
IDS. RUU dataset [EB/OL]..
|
| [6] |
KHOLIDY H A, BAIARDI F.CIDD: A Cloud Intrusion Detection Dataset for Cloud Computing and Masquerade Attacks[C]// IEEE. Ninth International Conference on Information Technology: New Generations, April 16-18, 2012, Las Vegas, NV, USA. NJ:IEEE, 2012:397-402.
|
| [7] |
戚犇,王梦迪. 基于信息增益的贝叶斯态势要素提取[J]. 信息网络安全,2017(9): 54-57.
|
| [8] |
CHEN Hongsong, BHARGAVA B, FU Zhongchuan.Multilabels-based Scalable Access Control for Big Data Applications[J].IEEE Cloud Computing, 2015, 1(3):65-71.
|
| [9] |
陈红松,韩至. 智慧城市中大数据安全分析与研究[J]. 信息网络安全,2015(7):1-6.
|
| [10] |
KANNAN A, VENKATESAN K G, STAGKOPOULOU A, et al.A Novel Cloud Intrusion Detection System Using Feature Selection and Classification[J]. International Journal of Intelligent Information Technologies, 2015, 11(4):1-15.
|
| [11] |
PRATIK P J, MADHU B R.Data Mining-based CIDS: Cloud Intrusion Detection System for Masquerade Attacks [DCIDSM][C]//IEEE. Fourth International Conference on Computing, Communications and NETWORKING Technologies, July 4-6, 2013, Tiruchengode, India.NJ: IEEE, 2013:1-5.
|
| [12] |
宋海涛,韦大伟,汤光明,等. 基于模式挖掘的用户行为异常检测算法[J].小型微型计算机系统,2016,37(2):221-226.
|
| [13] |
CHAHAL J K, KAUR A.A Hybrid Approach Based on Classification and Clustering for Intrusion Detection System[J]. International Journal of Mathematical Sciences & Computing, 2016, 2(4):34-40.
|
| [14] |
余慧佳,刘奕群,张敏,等. 基于大规模日志分析的搜索引擎用户行为分析[J]. 中文信息学报,2007,21(1):109-114.
|
| [15] |
WEKA[EB/OL].,2017-11-20.
|
 ), Gang WANG2, Jianlin SONG3
), Gang WANG2, Jianlin SONG3