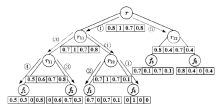
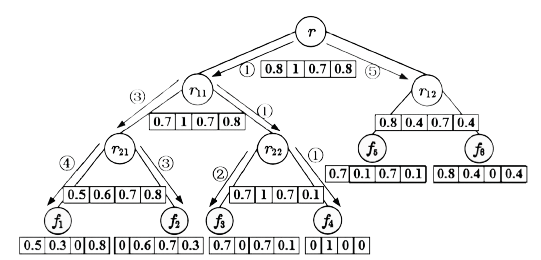
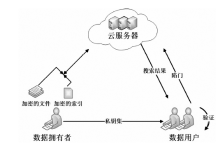
| [1] |
ARMBRUST M, FOX A, GRIFFITH R, et al.A View of Cloud Computing[J]. Communications of the ACM, 2010, 53(4): 50-58.
|
| [2] |
Wikipedia.2011 PlayStation Network Outage[EB/OL]., 2018-12-25.
|
| [3] |
YU Jia, REN Kui, WANG Cong, et al.Enabling Cloud Storage Auditing with Key-Exposure Resistance[J]. IEEE Transactions on Information Forensics and Security, 2015, 10(6): 1167-1179.
|
| [4] |
HOU Huiying, YU Jia, HAO Rong.Research on an Integrity Auditing Scheme Based on Algebraic Signature in Cloud Storage[J].Netinfo Security, 2017, 17(10): 69-74.
|
|
侯慧莹,于佳,郝蓉. 一种基于代数签名的云存储完整性审计方案研究[J]. 信息网络安全,2017,17(10): 69-74.
|
| [5] |
SONG D X, WAGNER D, PERRIG A.Practical Techniques for Searches on Encrypted Data[C]//IEEE. The 2000 IEEE Symposium on Security and Privacy, May 14 - 17, 2000 , Berkeley, CA, USA. NJ: IEEE, 2000: 44-55.
|
| [6] |
GOHE J.Secure Indexes[J]. IACR Cryptology ePrint Archive, 2003, 2003: 216.
|
| [7] |
CURTMOLA R, GARY J, KAMARA S, et al.Searchable Symmetric Encryption: Improved Definitions and Efficient Constructions[C]//ACM. ACM Conference on Computer and Communications Security, October 30-November 3, 2006,Alexandria, Virginia, USA. New York: ACM, 2006: 79-88.
|
| [8] |
LU Haining.Searchable Symmetric Encryption with Hidden Search Pattern[J]. Netinfo Security, 2017, 17(1): 38-42.
|
|
陆海宁. 可隐藏搜索模式的对称可搜索加密方案[J]. 信息网络安全,2017,17(1):38-42.
|
| [9] |
WANG Cong, CAO Ning, LI Jin, et al.Secure Ranked Keyword Search over Encrypted Cloud Data[C]//IEEE. 2010 IEEE 30th International Conference on Distributed Computing Systems, June 21-25, 2010, Genova, Italy. NJ: IEEE, 2010: 253-262.
|
| [10] |
XIA Zhihua, WANG Xinhui, SUN Xingming, et al.A Secure and Dynamic Multi-keyword Ranked Search Scheme over Encrypted Cloud Data[J]. IEEE Transactions on Parallel and Distributed Systems, 2016, 27(2): 340-352.
|
| [11] |
CAO Ning, WANG Cong, LI Ming, et al.Privacy-preserving Multi-keyword Ranked Search over Encrypted Cloud Data[C]//IEEE. 2011 Proceedings IEEE INFOCOM, April 10-15, 2011, Shanghai, China. NJ: IEEE, 2011: 222-233.
|
| [12] |
ZHANG Nan, CHEN Lanxiang.Research on An Efficient Ranked Keywords Searchable Encryption System[J]. Netinfo Security, 2017, 17(2): 43-50.
|
|
张楠,陈兰香. 一种高效的支持排序的关键词可搜索加密系统的研究[J].信息网络安全,2017,17(2):43-50.
|
| [13] |
KUROSAWA K, OHTAKI Y.UC-Secure Searchable Symmetric Encryption[M]//Springer. Financial Cryptography and Data Security. Heidelberg: Springer, Berlin, Heidelberg, 2012: 285-298.
|
| [14] |
ZHANG Wei, LIN Yaping, GU Qi.Catch You if You Misbehave: Ranked Keyword Search Results Verification in Cloud Computing[J]. IEEE Transactions on Cloud Computing, 2005, 6(1): 74-86.
|
| [15] |
SUN Wenhai, WANG Bing, CAO Ning, et al.Verifiable Privacy-Preserving Multi-keyword Text Search in the Cloud Supporting Similarity-based Ranking[J]. IEEE Transactions on Parallel and Distributed Systems, 2013, 25(11): 3025-3035.
|
| [16] |
PAILLIER P.Public-key Cryptosystems Based on Composite Degree Residuosity Classes[C]//EUROCRYPT. The 17th International Conference on Theory and Application of Cryptographic Techniques, May 2-6, 1999, Prague, Czech Republic. Heidelberg : Springer-Verlag Berlin, Heidelberg, 1999: 223-238.
|
| [17] |
WONG W K, CHEUNG D WL,KAO B C M, et al.Secure kNN Computation on Encrypted Databases[C]//ACM. 2009 ACM SIGMOD International Conference on Management of Data, June 29-July 2, 2009, Providence, Rhode Island, USA. New York: ACM, 2009: 139-152.
|
 ), Jia YU1,3
), Jia YU1,3