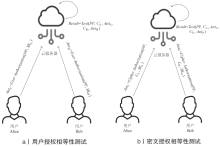
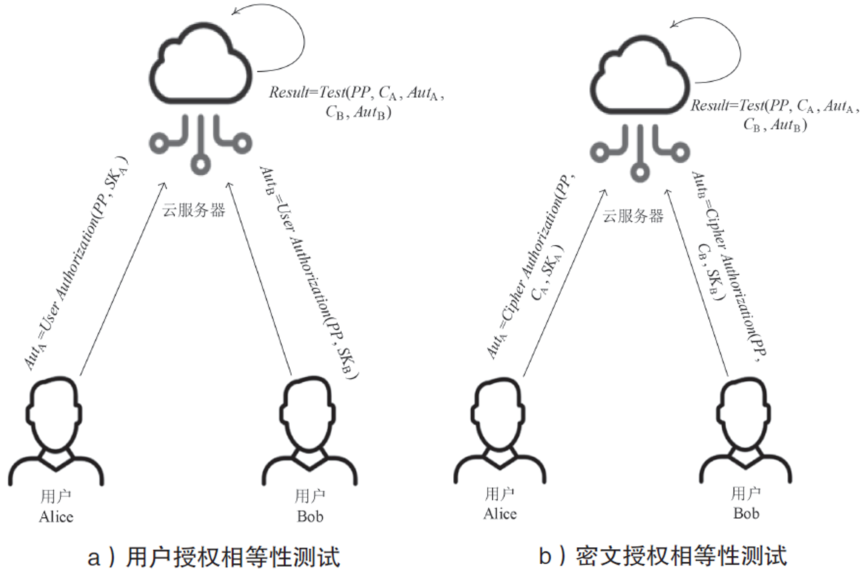
| [1] |
BAO Guohua, WANG Shengyu, LI Yunfa.Research on Data Security Protection Method Based on Privacy Awareness in Cloud Computing[J]. Netinfo Security, 2017, 17(1): 84-89.
|
|
包国华,王生玉,李运发. 云计算中基于隐私感知的数据安全保护方法研究[J]. 信息网络安全,2017,17(1):84-89.
|
| [2] |
YANG Guomin, TAN C H, HUANG Qiong, et al.Probabilistic Public Key Encryption with Equality Test[C]//Springer. 2010 International Conference on Topics in Cryptology, March 1-5, 2010, San Francisco, California, USA. Heidelberg: Springer, 2010: 119-131.
|
| [3] |
WANG Yongjian, ZHANG Jian, CHENG Shaoyu, et al.An Improved Design of Homomorphic Encryption for Cloud Computing[J]. Netinfo Security, 2017, 17(3): 21-26.
|
|
王永建,张健,程少豫,等. 面向云计算的同态加密改进设计[J]. 信息网络安全,2017,17(3):21-26.
|
| [4] |
TANG Qiang.Towards Public Key Encryption Scheme Supporting Equality Test with Fine-grained Authorization[C]//Springer. 16th Australasian Conference on Information Security and Privacy, July 11-13, 2011, Melbourne, Australia. Heidelberg: Springer, 2011: 389-406.
|
| [5] |
TANG Qiang.Public Key Encryption Supporting Plaintext Equality Test and User-specified Authorization[J]. Security & Communication Networks. 2012, 5(12): 1351-1362.
|
| [6] |
TANG Qiang.Public Key Encryption Schemes Supporting Equality Test with Authorisation of Different Granularity[J]. International Journal of Applied Cryptography, 2012, 2(4): 304-321.
|
| [7] |
MA Sha, ZHANG Mingwu, HUANG Qiong, et al. Public Key Encryption with Delegated Equality Test in a Multi-user Setting[EB/OL]. , 2017-12-10.
|
| [8] |
HUANG Kaibin, TSO R, CHEN Yuchi, et al.PKE-AET: Public Key Encryption with Authorized Equality Test[J]. Computer Journal, 2015, 58(10): 2686-2697.
|
| [9] |
MA Sha, HUANG Qiong, ZHANG Mingwu, et al.Efficient Public Key Encryption With Equality Test Supporting Flexible Authorization[J]. IEEE Transactions on Information Forensics & Security, 2015, 10(3): 458-470.
|
| [10] |
HUANG Kaibin, TSO R, CHEN Yuchi, et al.A New Public Key Encryption with Equality Test[C]//Springer. 8th International Conference on Network and System Security, October 15-17, 2014, Xi’an, China. Heidelberg: Springer, 2014: 550-557.
|
| [11] |
LU Yao, ZHANG Rui, LIN Dongdai.Stronger Security Model for Public-key Encryption with Equality Test[C]//Springer. 5th International Conference on Pairing-based Cryptography, May 16-18, 2012, Cologne, Germany. Heidelberg: Springer, 2012: 65-82.
|
| [12] |
JI Haiping, XU Lei, YU Xiaoling, et al.Research on Hierarchical Identity-based Encryption Management System in Cloud Computing[J]. Netinfo Security, 2016, 16(5): 30-36.
|
|
计海萍,徐磊,蔚晓玲,等. 云计算环境下基于身份的分层加密管理系统研究[J]. 信息网络安全,2016,16(5):30-36.
|
| [13] |
MCCULLAGH N.Securing E-mail with Identity-based Encryption[J]. It Professional, 2005, 7(3): 63-64.
|
| [14] |
BAI Qinghai.Comparative Research on Two Kinds of Certification Systems of the Public Key Infrastructure (PKI) and the Identity Based Encryption (IBE)[C]//IEEE. 2012 Cross Strait Quad-Regional Radio Science and Wireless Technology Conference, July 23-27, 2012, Taiwan, China. New Jersey: IEEE, 2012: 147-150.
|
| [15] |
MA Sha.Identity-based Encryption with Outsourced Equality Test in Cloud Computing[J]. Information Sciences an International Journal, 2016, 328(C): 389-402.
|
| [16] |
LEE H T, LING S, SEO J H, et al.Semi-generic Construction of Public Key Encryption and Identity-based Encryption with Equality Test[J]. Information Sciences An International Journal, 2016, 373(C): 419-440.
|
| [17] |
WU Libing, ZHANG Yubo, CHOO K K R, et al. Efficient Identity-based Encryption Scheme with Equality Test in Smart City[J]. IEEE Transactions on Sustainable Computing, 2018, 3(1): 44-55.
|
| [18] |
CHEN Yu, CHEN Liqun, ZHANG Zongyang.CCA Secure IB-KEM from the Computational Bilinear Diffie-Hellman Assumption in the Standard Model[C]//Springer. 14th International Conference on Information Security and Cryptology, November 30-December 2, 2011, Seoul, Korea. Heidelberg: Springer, 2012: 275-301.
|
 )
)