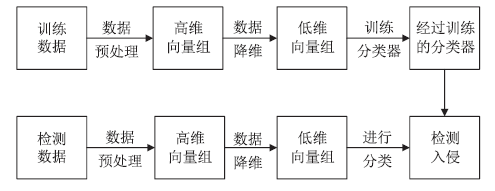
| [1] |
LIU Jifen.Intrusion Detection Classification Method Based on Non-negative Matrix Factorization[J]. Computer Engineering and Applications, 2012, 48(30): 117-121.
|
|
刘积芬. 非负矩阵分解降维的入侵检测方法[J]. 计算机工程与应用,2012,48(30):117-121.
|
| [2] |
TANG Jian, SUN Chunlai, MAO Kefeng, et al.Network Intrusion Anomaly Detection Model Based on Dimension Reduction Strategy Using Principal Component Analysis and Mutual Information[J]. Netinfo Security, 2015, 15(9): 78-83.
|
|
汤健,孙春来,毛克峰,等. 基于主元分析和互信息维数约简策略的网络入侵异常检测[J]. 信息网络安全,2015,15(9):78-83.
|
| [3] |
JYOTHSNA V, PRASAD V V R. A Review of Anomaly Based Intrusion Detection Systems[J]. International Journal of Computer Applications, 2011, 28(7): 26-35.
|
| [4] |
QI Mingyu, LIU Ming, FU Yanming.Research on Network Intrusion Detection Using Support Vector Machines Based on Principal Component Analysis[J]. Netinfo Security, 2015, 15(2): 15-18.
|
|
戚名钰,刘铭,傅彦铭. 基于PCA的SVM网络入侵检测研究[J]. 信息网络安全,2015,15(2):15-18.
|
| [5] |
BI Zhanke, XU Shengli.Actuality and Development Trend of Intrusion Detection Technology[J]. Soft Ware Guide, 2010(11): 152-154.
|
|
毕战科,许胜礼. 入侵检测技术的研究现状及其发展[J]. 软件导刊,2010(11):152-154.
|
| [6] |
FODOR I K.A Survey of Dimension Reduction Techniques LLNL Technical [EB/OL]. , 2017-10-10.
|
| [7] |
LEE D, SEUNG H.Learning the Parts of Objects by Nonnegative Matrix Factorization[J]. Nature, 1999, 401(21): 788-791.
|
| [8] |
JU Yufang.Research of Text Clustering Based on NMF Algorithm[D]. XuZhou: China University of Mining and Technology, 2014.
|
|
巨瑜芳. 基于NMF算法的文本聚类研究[D]. 徐州:中国矿业大学,2014.
|
| [9] |
GAO Xin.The Research of SAR Image Target Recognition Method Based on NMF[D]. ChengDu: University of Electronic Science and Technology of China, 2013.
|
|
高馨. 基于NMF的SAR图识像目标别方法研究[D]. 成都:电子科技大学,2013.
|
| [10] |
HE Songhua, CHEN Qiao, DUAN Jiang, et al.The Spectral Prediction of Original Primary Pigment Based on Constrained Non-negative Matrix Factorization[J]. Spectroscopy and Spectral Analysis, 2016, 36(10): 3274-3279.
|
|
何颂华,陈桥,段江,等. 基于有约束非负矩阵分解的原稿基色色料光谱预测方法[J]. 光谱学与光谱分析,2016,36(10):3274-3279.
|
| [11] |
LV ZhiGao.Research on Non-negative Matrix Factorization Method and Its Application in Blind Source Separation[D]. WuHan: Wuhan University of Science and Technology, 2012.
|
|
吕志高. 一种非负矩阵分解方法研究以及在盲源分离中的应用[D]. 武汉:武汉科技大学,2012.
|
| [12] |
ZHANG Fengbin, GE Haiyang, YANG Ze.Optimization and Application of Non-negative Matrix Factorization in Immune Intrusion Detection[J]. Computer Engineering, 2016, 41(5): 173-178.
|
|
张凤斌,葛海洋,杨泽. 非负矩阵分解在免疫入侵检测中的优化和应用[J]. 计算机工程,2016,41(5):173-178.
|
| [13] |
LI Le, ZHANG Yujin.A Survey on Algorithms of Non-negative Matrix Factorization[J]. Acta Electronica Sinica, 2008, 36(4): 737-743.
|
|
李乐,章毓晋. 非负矩阵分解算法综述[J]. 电子学报,2008,36(4):737-743.
|
| [14] |
BAO Panqing, YANG Mingfu.Intrusion Detection Based on KPCA and SVM[J]. Computer Applications and Software, 2006, 23(2): 125-127.
|
|
包潘晴,杨明福. 基于KPCA和SVM的网络入侵检测[J]. 计算机应用与软件,2006,23(2):125-127.
|
| [15] |
GU Jun.Research on Intrusion Detection System Based on KPCA and SVM[J]. Computer Simulation, 2006, 23(2): 125-127.
|
|
顾钧. 基于KPCA和SVM的网络入侵检测研究[J]. 计算机仿真,2010(7):105-107.
|
| [16] |
KDD. KDD Cup 1999data [EB/OL]. , 2017-10-15.
|
| [17] |
LIN Weining, CHEN Mingzhi, ZHAN Yunqing, et al.Research on an Intrusion Detection Algorithm Based on PCA and Random-forest Classification[J]. Netinfo Security, 2017, 17(11): 50-54.
|
|
林伟宁,陈明志,詹云清,等. 一种基于PCA和随机森林分类的入侵检测算法研究[J]. 信息网络安全,2017,17(11):50-54.
|