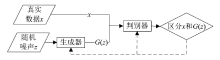
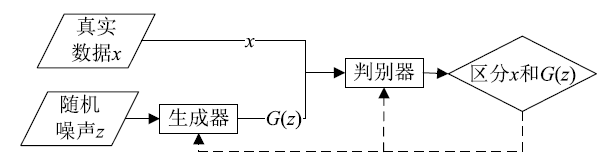
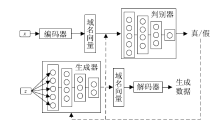
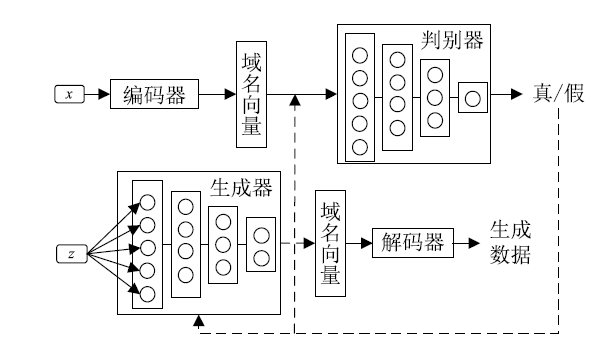
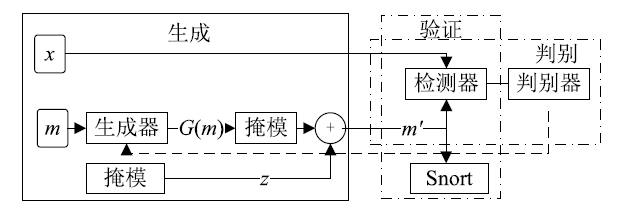
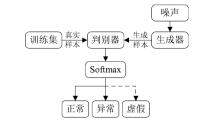
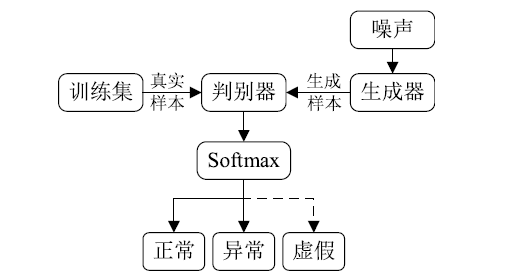
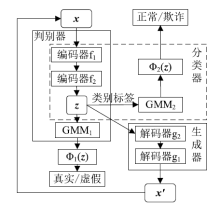
Netinfo Security ›› 2019, Vol. 19 ›› Issue (2): 1-9.doi: 10.3969/j.issn.1671-1122.2019.02.001
Survey of Network Attack Detection Based on GAN
Jianming FU1,2( ), Lin LI1, Rui ZHENG1, Suriguga1
), Lin LI1, Rui ZHENG1, Suriguga1
- 1. School of Cyber Science and Engineering, Wuhan University, Wuhan Hubei 430072, China
2. Key Laboratory of Aerospace Information Security and Trusted Computing, Ministry of Education,Wuhan University, Wuhan Hubei 430072, China
-
Received:2018-09-28Online:2019-02-10Published:2020-05-11
CLC Number:
Cite this article
Jianming FU, Lin LI, Rui ZHENG, Suriguga. Survey of Network Attack Detection Based on GAN[J]. Netinfo Security, 2019, 19(2): 1-9.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2019.02.001
| [1] | GOODFELLOW I. NIPS2016 Tutorial: Generative Adversarial Networks[EB/OL]. |
| [2] | ARJOVSKY M, BOTTOU L. Towards Principled Methods for Training Generative Adversarial Networks[EB/OL]. ,2017-1-17. |
| [3] | AGHAKHANI H, MACHIRY A, NILIZADEH S, et al. Detecting Deceptive Reviews Using Generative Adversarial Networks[EB/OL].,2018-5-25. |
| [4] | GOODFELLOW I, POUGET-ABADIE J, MIRZA M, et al.Generative Adversarial Nets[C]//NIPS. The 2014 Conference on Advances in Neural Information Processing Systems 27, December 8-13, 2014, Montreal, Canada. NY:Curran Associates, 2014. 2672-2680. |
| [5] | SALIMANS T, GOODFELLOW I, ZAREMBA W, et al. Improved Techniques for Training Gans[EB/OL]. ,2016-6-10. |
| [6] | ZHAO Junbo, MATHIEU M, LECUN Y. Energy-based Generative Adversarial Network[EB/OL]. ,2017-3-6. |
| [7] | ARJOVSKY M, CHINTALA S, BOTTOU L. Wasserstein Gan[EB/OL]. ,2017-12-6. |
| [8] | GULRAJANI I, AHMED F, ARJOVSKY M, et al. Improved Training of Wasserstein Gans[EB/OL].,2017-12-25. |
| [9] | LEDIG C, THEIS L, HUSZÁR F, et al. Photo-realistic Single Image Super-resolution Using a Generative Adversarial Network[EB/OL]. ,2017-5-25. |
| [10] | WU Huikai, ZHENG Shuai, ZHANG Junge, et al. GP-GAN: Towards Realistic High-Resolution Image Blending[EB/OL]. ,2017-3-25 . |
| [11] | PATHAK D, KRAHENBUHL P, DONAHUE J, et al.Context Encoders: Feature Learning by Inpainting[C]//IEEE. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, June 27-30,2016, Las Vegas,USA.NJ:IEEE,2016: 2536-2544. |
| [12] | MOGREN O. C-RNN-GAN: Continuous Recurrent Neural Networks with Adversarial Training[EB/OL]. ,2016-11-29. |
| [13] | YU Lantao, ZHANG Weinan, WANG Jun, et al.SeqGAN: Sequence Generative Adversarial Nets with Policy Gradient[C]//AAAI. The Thirty-first AAAI Conference on Artificial Intelligence and the Twenty-ninth Innovative Applications of Artificial Intelligence Conference, February 4-9,2017,San Francisco,California,USA. CA:AAAI, 2017: 2852-2858. |
| [14] | LI Jiwei, MONROE W, SHI Tianlin, et al. Adversarial Learning for Neural Dialogue Generation[EB/OL]. ,2017-9-24. |
| [15] | ZHANG Yizhe, GAN Zhe, CARIN L. Generating Text via Adversarial Training[EB/OL]. ,2018-6-11. |
| [16] | MIYATO T, DAI A M, GOODFELLOW I. Adversarial Training Methods for Semi-Supervised Text Classification[EB/OL].,2017-5-6. |
| [17] | SUTSKEVER I, VINYALS O, LE Q V.Sequence to Sequence Learning with Neural Networks[C]//NIPS. Advances in Neural Information Processing Systems, December 8-13,2014,Montreal,Quebec,Canada.NY:Curran Associates,2016: 3104-3112. |
| [18] | MIKOLOV T, SUTSKEVER I, CHEN K, et al.Distributed Representations of Words and Phrases and Their Compositionality[C]//NIPS.Advances in Neural Information Processing Systems,December 5-10,2013,Lake Tahoe,Nevada,USA.NY:Curran Associates,2013: 3111-3119. |
| [19] | HARER J, OZDEMIR O, LAZOVICH T, et al. Learning to Repair Software Vulnerabilities with Generative Adversarial Networks[EB/OL].,2018-5-28. |
| [20] | YUAN Chen, QIAN Liping, ZHANG Hui, et al. Generation of Malicious Domain Training Data Based on Generative Adversarial Network[EB/OL].. |
| 袁辰, 钱丽萍, 张慧, 等. 基于生成对抗网络的恶意域名训练数据生成[EB/OL].. | |
| [21] | PAN Yiming, LIN Jiajun.Generation and Verification of Malicious Network Flow Based on Generative Adversarial Networks[EB/OL]. |
| 潘一鸣,林家骏.基于生成对抗网络的恶意网络流生成及验证[EB/OL]. | |
| [22] | HU Weiwei, TAN Ying. Generating Adversarial Malware Examples for Black-Box Attacks Based on GAN[EB/OL]. ,2017-2-20. |
| [23] | ZHENG Shengjun, GUO Longhua, CHEN Jian, et al.An Online Detection System for Advanced Malware Based on Virtual Execution Technology[J]. Netinfo Security, 2016,16(1) : 29-33. |
| 郑生军,郭龙华,陈建,等. 基于虚拟执行技术的高级恶意软件攻击在线检测系统[J]. 信息网络安全,2016,16(1) : 29-33. | |
| [24] | KIM J Y, BU S J, CHO S B.Malware Detection Using Deep Transferred Generative Adversarial Networks[C]//ICONIP. the 24th International Conference on Neural Information Processing, November 14-18,2017,Guangzhou,China.HK:Springer,2017: 556-564. |
| [25] | ARNOLD A, NALLAPATI R, COHEN W W.A Comparative Study of Methods for Transductive Transfer Learning[C]//IEEE.ICDM Workshops 2007,October 28,2007,Omaha,USA.NJ:IEEE, 2007: 77-82. |
| [26] | MICROSOFT. Microsoft Malware Classification Challenge (BIG 2015)[EB/OL]. |
| [27] | KIM J Y, BU S J, CHO S B.Zero-day Malware Detection Using Transferred Generative Adversarial Networks Based on Deep Autoencoders[J]. Information Sciences, 2018, 460(9): 83-102. |
| [28] | HEN Hongsong, WANG Gang, SONG Jianlin.Research on Anomaly Behavior Classification Algorithm of Internal Network User Based on Cloud Computing Intrusion Detection Data Set[J]. Netinfo Security, 2018 ,18(3) : 1-7. |
| 陈红松,王钢,宋建林. 基于云计算入侵检测数据集的内网用户异常行为分类算法研究[J]. 信息网络安全,2018,18(3):1-7. | |
| [29] | YIN Chuanlong, ZHU Yuefei, LIU Shengli, et al.An Enhancing Framework for Botnet Detection Using Generative Adversarial Networks[C]//IEEE.2018 International Conference on Artificial Intelligence and Big Data (ICAIBD),May 26-28,2018,Chengdu,China.NJ:IEEE, 2018:228-234. |
| [30] | SHIRAVI A, SHIRAVI H, TAVALLAEE M, et al.Toward Developing a Systematic Approach to Generate Benchmark Datasets for Intrusion Detection[J]. Computers & Security, 2012, 31(3): 357-374. |
| [31] | FIORE U, DE S A, PERLA F, et al. Using Generative Adversarial Networks for Improving Classification Effectiveness in Credit Card Fraud Detection[EB/OL]. ,2017-12-30. |
| [32] | DAL P A, CAELEN O, JOHNSON R A, et al.Calibrating Probability with Undersampling for Unbalanced Classification[C]//IEEE. 2015 IEEE Symposium Series on Computational Intelligence, December 7-10,2015,Cape Town,South Africa.NJ:IEEE,2015: 159-166. |
| [33] | ZHENG Yujun, ZHOU Xiaohan, SHENG Weiguo, et al.Generative Adversarial Network-based Telecom Fraud Detection at the Receiving Bank[J]. Neural Networks, 2018, 102(6): 78-86. |
| [1] | Zhiyan ZHAO, Xiaomo JI. Research on the Intelligent Fusion Model of Network Security Situation Awareness [J]. Netinfo Security, 2020, 20(4): 87-93. |
| [2] | Tengfei WANG, Manchun CAI, Tianliang LU, Ting YUE. IPv6 Network Attack Source Tracing Method Based on iTrace_v6 [J]. Netinfo Security, 2020, 20(3): 83-89. |
| [3] | Tao JING, Wei WAN. Research on a P2P Network Communication Behavior Analytical Method for Status Migration Attribute-oriented [J]. Netinfo Security, 2020, 20(1): 16-25. |
| [4] | Wei DONG, Yonggang LI. Research on Analysis of Attacks on Smart Grid Network Based on Complex Network [J]. Netinfo Security, 2020, 20(1): 52-60. |
| [5] | XU Guotian. A Method of Office Data Fragmentation Recognition, Sorting, Reorganization and Repair [J]. Netinfo Security, 2019, 19(9): 26-30. |
| [6] | QIU Yue. Network Security Risk Analysis and Assessment of Large-scale Sports Events [J]. Netinfo Security, 2019, 19(9): 61-65. |
| [7] | TANG Hongqiong, NIU Ke, ZHANG Yingnan, YANG Xiaoyuan. Reversible Data Hiding in Videos Based on Adaptive Two-dimensional Histogram Modification [J]. Netinfo Security, 2019, 19(9): 106-110. |
| [8] | GAO Mengru, XIE Fangjun, DONG Hongqin, LIN Xiang. Research on Network Security Evaluation System Oriented to Critical Information Infrastructure [J]. Netinfo Security, 2019, 19(9): 111-114. |
| [9] | CHEN Liangchen, LIU Baoxu, GAO Shu. Research on Traffic Data Sampling Technology in Network Attack Detection [J]. Netinfo Security, 2019, 19(8): 22-28. |
| [10] | SHANG Wenli, YIN Long, LIU Xianda, ZHAO Jianming. Construction Technology and Application of Industrial Control System Security and Trusted Environment [J]. Netinfo Security, 2019, 19(6): 1-10. |
| [11] | CHEN Guanheng, SU Jinshu. Abnormal Traffic Detection Algorithm Based on Deep Neural Network [J]. Netinfo Security, 2019, 19(6): 68-75. |
| [12] | ZHANG Ke, WANG Youjie, CHENG Shaoyin, WANG Lidong. Intrusion Collaborative Disposal Method of Spoofed IP Address in DDoS Attacks [J]. 信息网络安全, 2019, 19(5): 22-29. |
| [13] | WANG Yaojie, NIU Ke, YANG Xiaoyuan. Image Steganography Scheme Based on GANs [J]. 信息网络安全, 2019, 19(5): 54-60. |
| [14] | Li WEI, Qin DUAN, Zhiwei LIU. A Summary of Medical Information Security Management in Internet Era [J]. Netinfo Security, 2019, 19(12): 88-92. |
| [15] | Ran ZI, Jia LIU. Research on Construction of Risk and Trust Architecture Based on Lean Trust [J]. Netinfo Security, 2019, 19(10): 32-41. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||