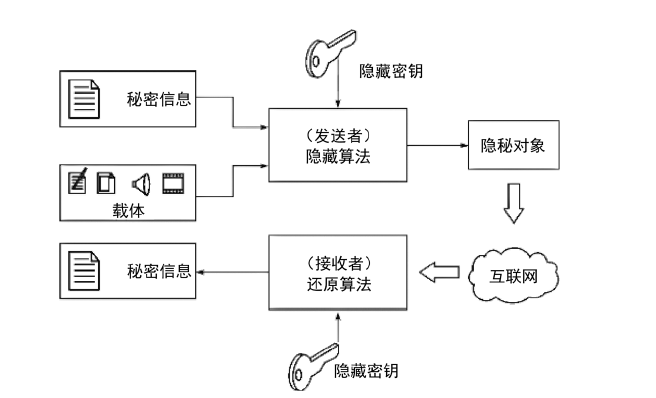
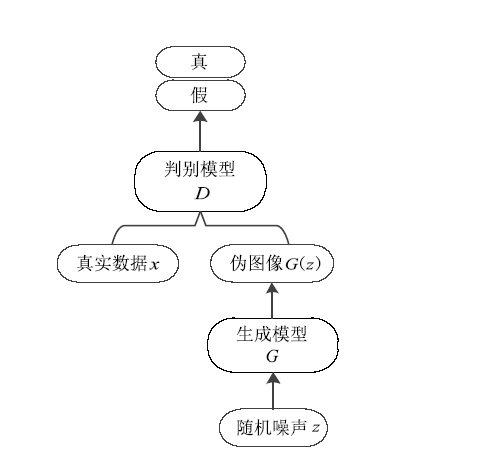
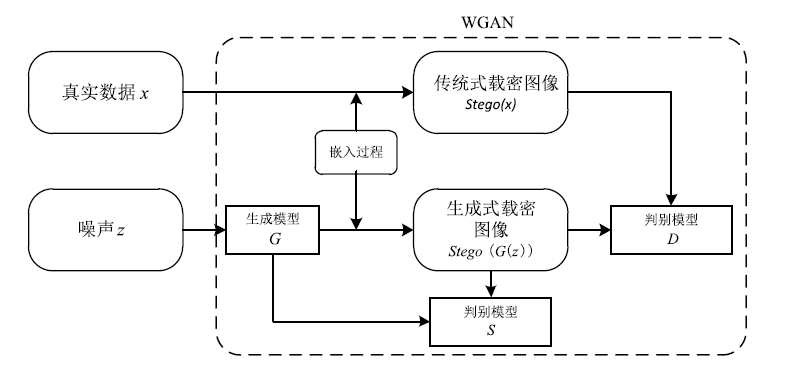
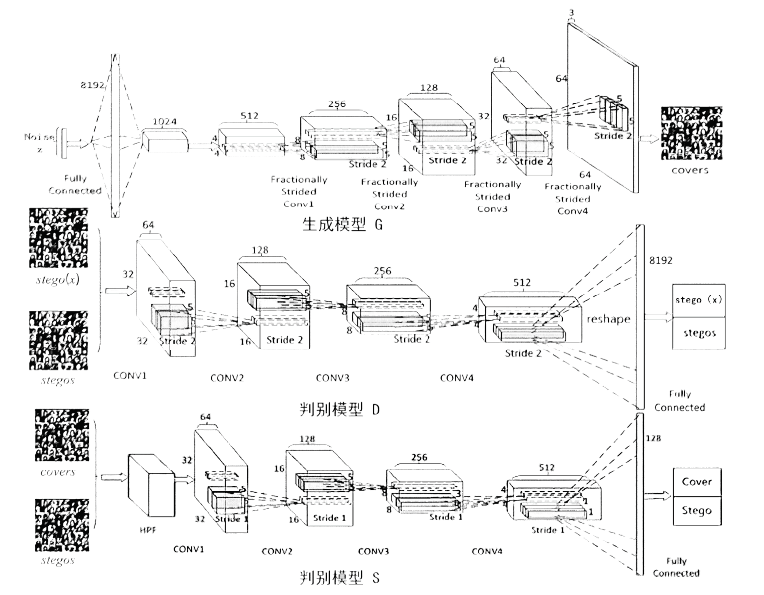
| [1] |
XIONG Jinbo, MA Rong, ZHANG Yuanyuan, et al.Image Information Hiding Method and Implementation for Social Network[J]. Information Network Security, 2017, 17(3): 6-13.
|
|
熊金波,马蓉,张媛媛,等.面向社交网络的图片信息隐藏方法与实现[J].信息网络安全,2017,17(3):6-13.
|
| [2] |
TIEKEL A Z, RANKIN G A, SCHYNDEL R V.Electronic Watermark[C]// IEEE. Digital Image Computing, Technology and Applications, December 10-14, 1993, Sydney, Australia. New York: IEEE, 1993: 666-673.
|
| [3] |
YANG C H, WENG C Y, WANG S J.Adaptive Data Hiding in Edge Areas of Images with Spatial LSB Domain Systems[J]. IEEE Transactions on Information Forensics & Security, 2008, 3(3): 488-497.
|
| [4] |
GAO Hongtao, LU Wei, YANG Yuwang.Image Saliency Region Extraction Method Based on Adaptive Adjustment Kernel Function[J]. Netinfo Security, 2018, 18(2): 54-60.
|
|
高洪涛,陆伟,杨余旺.基于自适应调节核函数的图像显著区域提取方法[J].信息网络安全,2018,18(2):54-60.
|
| [5] |
PEVNY T, FILLER T, BAS P. Using High-Dimensional Image Models to Perform Highly Undetectable Steganography[EB/OL]. , 2017-8-15.
|
| [6] |
HOLUB V, FRIDRICH J.Designing Steganographic Distortion Using Directional Filters[C]//IEEE. International Workshop on Information Forensics and Security, December1-5, 2013, Chicago, USA. New York: IEEE, 2013: 234-239.
|
| [7] |
RUANAIDH J K O, Dowling W J, Boland F M. Phase Watermarking of Digital Images[C]//IEEE. 2013 International Conference on Image Processing, May 11-14, 2013, San Francisco, USA. New York: IEEE, 2013: 1673-1687.
|
| [8] |
COX I J, KILIAN J, LEIGHTON F T.Secure Spread Spectrum Watermarking for Multimedia[J]. IEEE Transactions on Image Processing, 2010, 6(12): 1673-1687.
|
| [9] |
LIN W H, HORNY S J, KAO T W.An Efficient Watermarking Method Based on Significant Difference of Wavelet Coefficient Quantization[J]. IEEE Transactions on Multimedia, 2008, 10(5): 746-757.
|
| [10] |
DENIS V, BORIS B, BUENAIV E.Generative Adversarial Networks for Image Steganography[R]. ICLR 2016 Open Review, 2016.
|
| [11] |
SHI H, DONG J, WANG W, et al. SSGAN: Secure Steganography Based on Generative Adversarial Networks[EB/OL]. , 2017-7-30.
|
| [12] |
GOODFELLOW I, POUGAT A J, MIRZA M. Generative Adversarial Networks[EB/OL]. , 2014-6-10.
|
| [13] |
WANG Kunfeng, YU Chao, DUAN Yanjie, et al.Research Progress and Prospects of Generative Confrontation Network GAN[J]. Acta Automatica Sinica, 2017, 43(3): 321-332.
|
|
王坤峰,苟超,段艳杰,等.生成式对抗网络GAN的研究进展与展望[J].自动化学报,2017,43(3):321-332.
|
| [14] |
RADFORD A, METZ L, CHINTALA S.Unsupervised Representation Learning with Deep Convolutional Generative Adversarial Networks[J]. Computer Science, 2015, 1(11): 132-141.
|
| [15] |
MIRZA M, OSINDRO S. Conditional Generative Adversarial Nets[EB/OL]. , 2014-11-30.
|
| [16] |
CHEN X, DUAN Y, HOUTHOOFT R, et al. InfoGAN: Interpretable Representation Learning by Information MaximiZing Generative Adversarial Nets[EB/OL]. , 2016-6-30.
|
| [17] |
ARJOVSKY M, BOTTOU L. Towards Principled Methods for Training Generative Adversarial Networks[EB/OL]. . 04862, 2017-2-9.
|
| [18] |
CUI S, JIANG Y.Effective Lipschitz Constraint Enforcement for Wasserstein GAN Training[C]//IEEE. 2017 2nd IEEE International Conference on Computational Intelligence and Applications (ICCIA) IEEE, September 8-11, 2017, Beijing, China. New York: IEEE, 2017: 74-78.
|
| [19] |
QIAN Y, DONG J, WANG W, et al. Deep Learning for Steganalysis via Convolutional Neural Networks[EB/OL]. , 2015-4-30.
|
| [20] |
ACHAB M, GUILLOUX A, S G, et al. SGD with Variance Reduction beyond Empirical Risk Minimization[EB/OL]. , 2015-10-30.
|
 ), Ke NIU1,2, Xiaoyuan YANG1,2
), Ke NIU1,2, Xiaoyuan YANG1,2